1.SSL 用証明書の作成
1.1事前準備
RHEL8系にはCAが含まれていないためRHEL7のCA利用する。
① CAをWINSCP等を利用、またはwindowsマウントし、/etc/pki/tls/misc/にコピーする
➁SSL コマンドにPATH を通す
|
1 |
# export PATH=/etc/pki/tls/misc:$PATH |
➂openssl.cnf ファイルの編集
|
1 |
# cd /etc/pki/tls/ |
|
1 2 3 4 5 6 7 8 9 10 |
tls]# vi openssl.cnf ■197 行目あたりに追加 # This is OK for an SSL server. # nsCertType = server nsCertType = server ■265 行目あたりに追加 # Some might want this also # nsCertType = sslCA, emailCA nsCertType = sslCA, emailCA |
④各種証明書等を作成する作業用ディレクトリに移動
|
1 |
# cd /etc/pki/tls/certs |
1-2.CA 関連証明書の作成
① CA 用秘密鍵(cakey.pem)とCA 用証明書(cacert.pem)の作成
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 |
certs]# CA -newca CA certificate filename (or enter to create) <Enter>を入力 Making CA certificate ... Generating a 2048 bit RSA private key...............+++ .................................................................................................................+++ writing new private key to '/etc/pki/CA/private/./cakey.pem Enter PEM pass phrase: ←任意のCA 用パスワードを入力 Verifying - Enter PEM pass phrase: ←再度、任意のCA 用パスワードを入力 ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:JP State or Province Name (full name) []:<都道府県名> Locality Name (eg, city) [Default City]:<市町村名> Organization Name (eg, company) [Default Company Ltd]:<組織名> Organizational Unit Name (eg, section) []:<組織内ユニット名> Common Name (eg, your name or your server's hostname) []:<組織/サーバー名> Email Address []:<管理者メールアドレス> Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: <Enter> An optional company name []: <Enter> Using configuration from /etc/pki/tls/openssl.cnf Enter pass phrase for /etc/pki/CA/private/./cakey.pem: ←設定したCA 用パスワードを入力 Check that the request matches the signature Signature ok Certificate Details: Serial Number: c3:af:88:a0:37:c6:c9:6e Validity Not Before: Feb 20 04:47:20 2019 GMT Not After : Feb 19 04:47:20 2022 GMT Subject: countryName = JP stateOrProvinceName = <上で設定した都道府県名が表示される> organizationName = <上で設定した市町村名が表示される> organizationalUnitName = <上で設定した組織名が表示される> commonName = <上で設定した組織/サーバー名が表示される> emailAddress = <上で設定した管理者メールアドレスが表示される> X509v3 extensions: X509v3 Subject Key Identifier: 9F:64:6A:89:54:AF:A1:A3:08:D7:6B:B4:CB:3A:3E:DB:C9:0A:B8:70 X509v3 Authority Key Identifier: keyid:9F:64:6A:89:54:AF:A1:A3:08:D7:6B:B4:CB:3A:3E:DB:C9:0A:B8:70 X509v3 Basic Constraints: CA:TRUE Netscape Cert Type: SSL CA, S/MIME CA Certificate is to be certified until Feb 19 04:47:20 2022 GMT (1095 days) Write out database with 1 new entries Data Base Updated |
➁CA 証明書をブラウザにインポートするca.der ファイルの作成
|
1 |
certs]# openssl x509 -inform pem -in /etc/pki/CA/cacert.pem -outform der -out /etc/pki/CA/ca.der |
1-3.サーバー関連証明書の作成
①サーバー用秘密鍵(newkey.pem)を作成
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
certs]# CA -newreq Generating a 2048 bit RSA private key .................................................+++ .......................+++ writing new private key to 'newkey.pem' Enter PEM pass phrase: ←任意のサーバー証明書用のパスワードを入力) Verifying - Enter PEM pass phrase: ←再度、任意のサーバー証明書用のパスワードを入力 ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:JP State or Province Name (full name) []:<都道府県名> Locality Name (eg, city) [Default City]:<市町村名> Organization Name (eg, company) [Default Company Ltd]:<組織名> Organizational Unit Name (eg, section) []:<組織内ユニット名> Common Name (eg, your name or your server's hostname) []:<組織/サーバー名> Email Address []:<管理者メールアドレス> Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: <Enter> An optional company name []: <Enter> Request is in newreq.pem, private key is in newkey.pem |
② サーバー秘密鍵のパスワードを削除
このパスワードを設定したままにしておくと、SSL を起動するたびにパスワード入力が必要になり、自
動再起動時などに起動できなくなる。
|
1 2 3 |
certs]# openssl rsa -in newkey.pem -out newkey.pem Enter pass phrase for newkey.pem: ←サーバー証明書用のパスワードを入力 writing RSA key |
③ サーバー用証明書(newcert.pem/server.crt)を作成
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 |
certs]# CA -sign Using configuration from /etc/pki/tls/openssl.cnf Enter pass phrase for ./demoCA/private/cakey.pem: ←設定したCA 用パスワードを入力 Check that the request matches the signature Signature ok Certificate Details: Serial Number: c3:af:88:a0:37:c6:c9:6f Validity Not Before: Feb 20 04:51:26 2021 GMT Not After : Feb 20 04:51:26 20221 GMT Subject: countryName = xxxx stateOrProvinceName = xxxx localityName = xxxxx organizationName = xxxxx ・・・・・ 中略 ・・・・ DA:DD:DB:FF:DA:5B:28:8C:44:21:7E:DF:CC:C9:6C:31:03:23:BE:B6 X509v3 Authority Key Identifier: keyid:9F:64:6A:89:54:AF:A1:A3:08:D7:6B:B4:CB:3A:3E:DB:C9:0A:B8:70 Certificate is to be certified until Feb 20 04:51:26 2020 GMT (365 days) Sign the certificate? [y/n]:y ←「y」を入力 Write out database with 1 new entries Data Base Updated ・・・・・ 中略 ・・・・ -----BEGIN CERTIFICATE----- MIIEHDCCAwSgAwIBAgIJAMOviKA3xslvMA0GCSqGSIb3DQEBCwUAMH4xCzAJBgNV BAYTAkpQMQ4wDAYDVQQIDAVUb2t5bzETMBEGA1UECgwKQ0FfUHJpdmF0ZTEOMAwG A1UECwwFQWRtaW4xEzARBgNVBAMMCkNBX1ByaXZhdGUxJTAjBgkqhkiG9w0BCQEW FnN0dWR5QGxpbnV4LXRvcGljcy5jb20wHhcNMTkwMjIwMDQ1MTI2WhcNMjAwMjIw MDQ1MTI2WjCBijELMAkGA1UEBhMCSlAxDjAMBgNVBAgMBVRva3lvMQ0wCwYDVQQH DARUYW1hMQ4wDAYDVQQKDAVUaWdlcjEOMAwGA1UECwwFQWRtaW4xFTATBgNVBAMM DDE5Mi4xNjguMC4zNjElMCMGCSqGSIb3DQEJARYWc3R1ZHlAbGludXgtdG9waWNz LmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAN/3xLxDDO9AdyCx q8MoiXAGU2JID6UXPUSwUvZURuNZsxoxOOJoGlgPr6H8fOKshNlfL50QMXDCRqYn P8ACUIoRbS4mrsGlriNDTVatai7CdhODz+NoYHMKDbbr42lHSM1ycm+JVZzsCcF3 M72WaoYZpNtB6oedg78NG/bwWz4fLhBm/YTaItfpYdNk0lPFuQQushzI8Z/ZmDGM 5iNd86WNtsDvtmZQEM01aA6uvBUVaT8bBn8y8efwvFqX+WRbO1DoygJOKJ89npXX uRUMQVNDsW5jrSTLi4qQgGKmc23o/q2P46q9TZ9Bbp9xyc/5EOq1NUv5AE5lFoLV /AmkFKcCAwEAAaOBjzCBjDAJBgNVHRMEAjAAMBEGCWCGSAGG+EIBAQQEAwIGQDAs BglghkgBhvhCAQ0EHxYdT3BlblNTTCBHZW5lcmF0ZWQgQ2VydGlmaWNhdGUwHQYD VR0OBBYEFNrd2//aWyiMRCF+38zJbDEDI762MB8GA1UdIwQYMBaAFJ9kaolUr6Gj CNdrtMs6PtvJCrhwMA0GCSqGSIb3DQEBCwUAA4IBAQCK0Xvx2ppyKxVv1FswuTXC Vy/WLeAVVdLR4LFzQ41g2CsISRU6pkvnqCKJQsNsejlfh9oeMMpvBTqJMdSAe9mV CX0X4xtmGqKFzTsS3Xd2E8QvX8MJrATPvLzKl9wAOP45RpKStDgvt9e85mpFtOdU GfriZBlAxU2MnAbhLpTInefKneZh+v+KwgBoRL3NPZHVL/JGV4L0vnrG2r6SnNuS nBHZnkW4A6T3T/28f/ogbjq+kmvXjoakZw7axTGO53TariaRO6eVusNe+i66Ectj 2SFTGsOd6sHJW5KPWuqFamncAjFqxo67KNIMWzgmUDqQTwji+bql+lKNUakZJf9u -----END CERTIFICATE----- Signed certificate is in newcert.pem |
④ サーバー証明書(server.crt)を作成
|
1 |
certs]# openssl x509 -in newcert.pem -out server.crt |
2.SSH の公開鍵暗号方式設定
① RSA でキーペアを作成
一般ユーザー(例ではjimmy)になり、RSA でキーペアを作成
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
certs]# su - jimmy ~]$ ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/tama/.ssh/id_rsa): <Enter> Created directory '/home/pakira/.ssh'. Enter passphrase (empty for no passphrase): ←CA 用パスワードを入力 Enter same passphrase again: ←再度同じパスワードを入力 Your identification has been saved in /home/pakira/.ssh/id_rsa. Your public key has been saved in /home/pakira/.ssh/id_rsa.pub The key fingerprint is: SHA256:/C+8j0Ykpbqq80ABB/kkbwB8L76MUxmrkBvAsT6OVwg pakira@Tiger The key's randomart image is: +---[RSA 2048]----+ |*o. | |+=.. . | |.*= . o | |Eo++ . .o . | |o+o.= .So | |++.=. . .. | |+oB.. . o. | |o=o+ . +o | | .o+o. .o+o | +----[SHA256]-----+ |
|
1 2 |
~]$ mv ~/.ssh/id_rsa.pub ~/.ssh/authorized_keys ~]$ chmod 600 ~/.ssh/authorized_keys |
➁秘密鍵ログイン設定
|
1 |
~]$ su - |
|
1 2 3 4 5 6 7 |
# vi /etc/ssh/sshd_config ■49 行目あたり行頭の「#」を削除 変更前) #PubkeyAuthentication yes 変更後) PubkeyAuthentication yes |
③ SSH を再起動
|
1 |
# systemctl restart sshd.service |
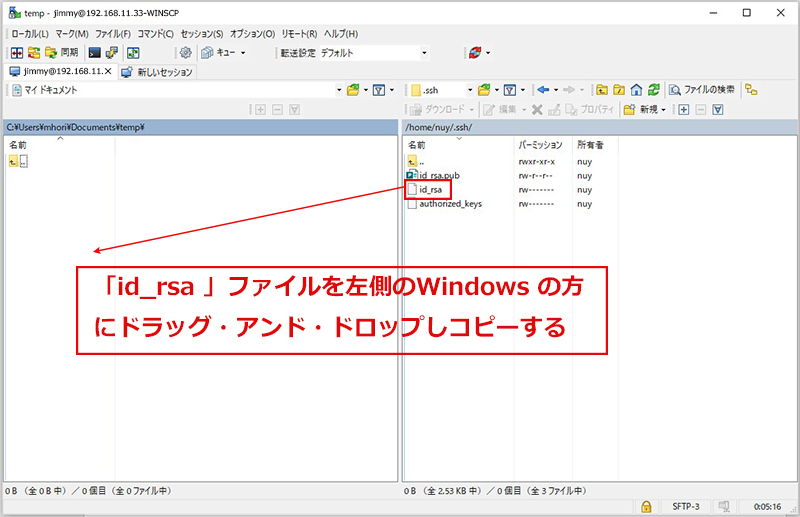
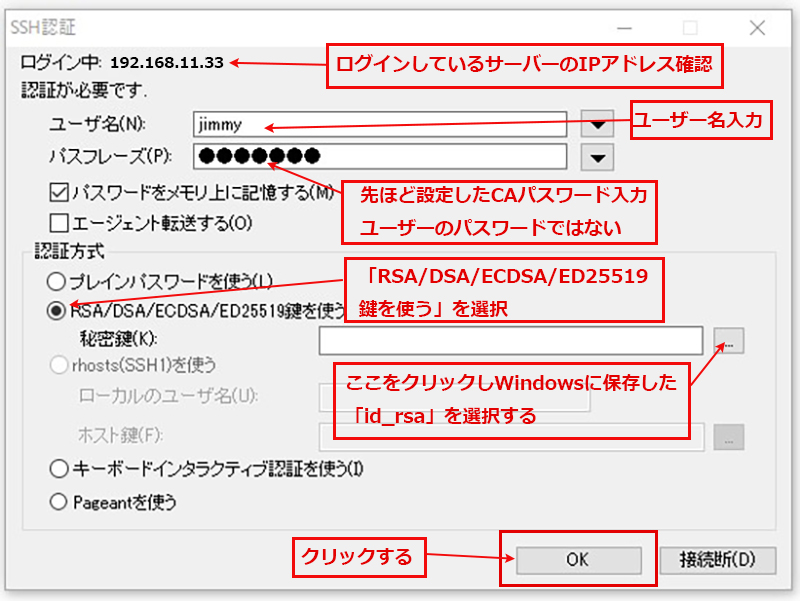
④秘密鍵をクライントPC にコピー(WinSCP使う)
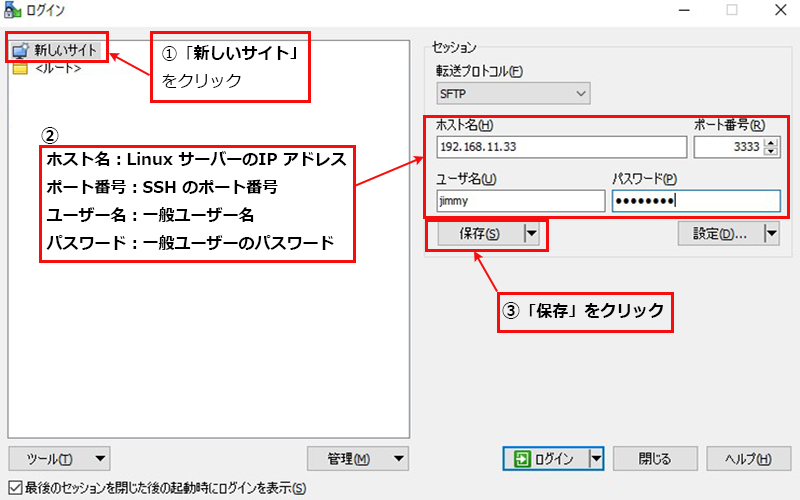
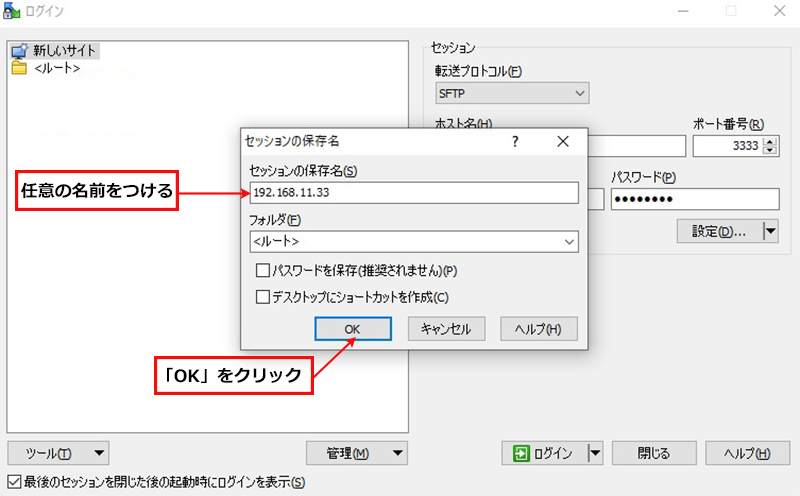
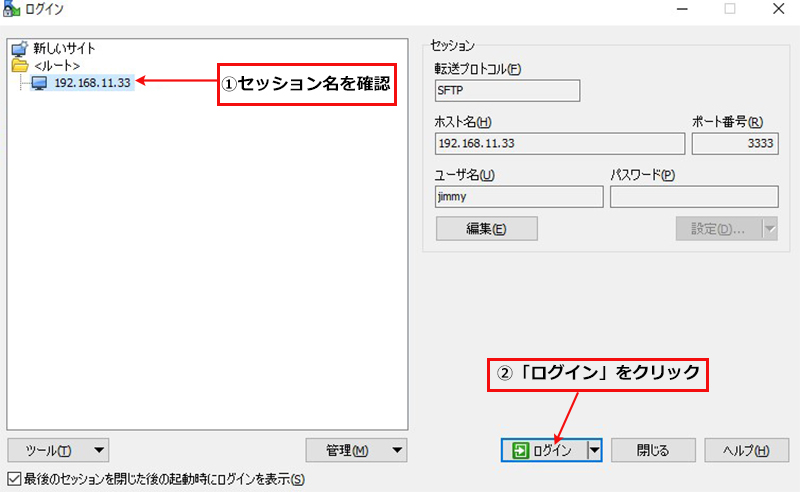
WinSCP を起動し、今回作成のサーバー(IP:192.168.11.33, SSHポート3333)に接続するための設定をする
(入手先 https://winscp.net/eng/download.php)
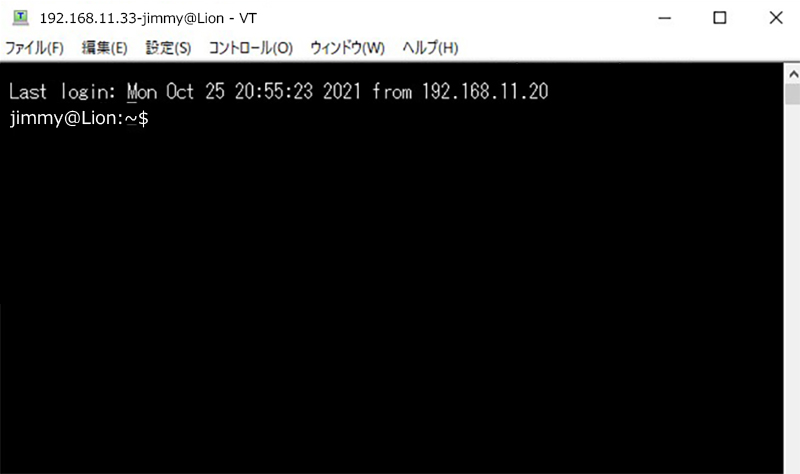
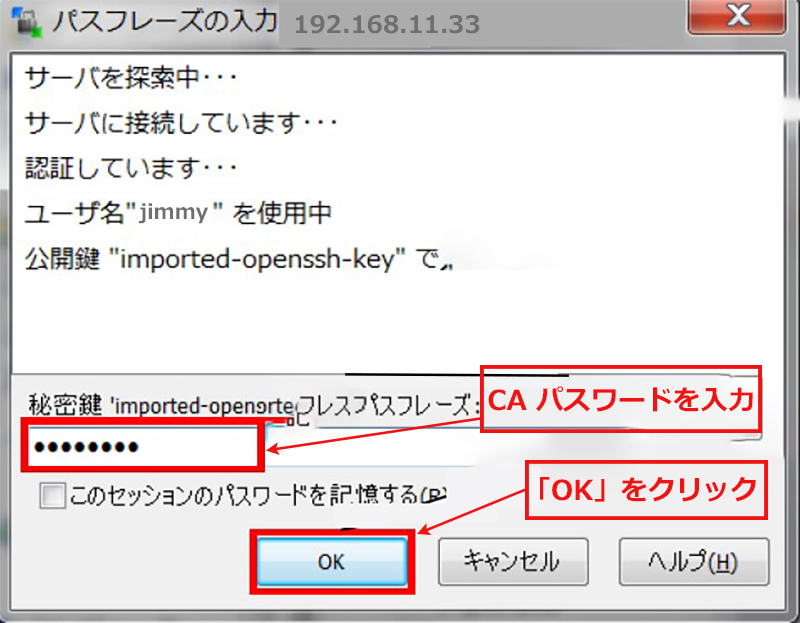
正常に接続されると次のようになる
⑤秘密鍵でのみログインするよう変更
| [root@Lepard ~]# vi /etc/ssh/sshd_config ■69 行目あたり 「#PasswordAuthentication yes」の下に「PasswordAuthentication no」を追加 #PasswordAuthentication yes PasswordAuthentication noSSH を再起動 [root@Lepard ~]# systemctl restart sshd.service |
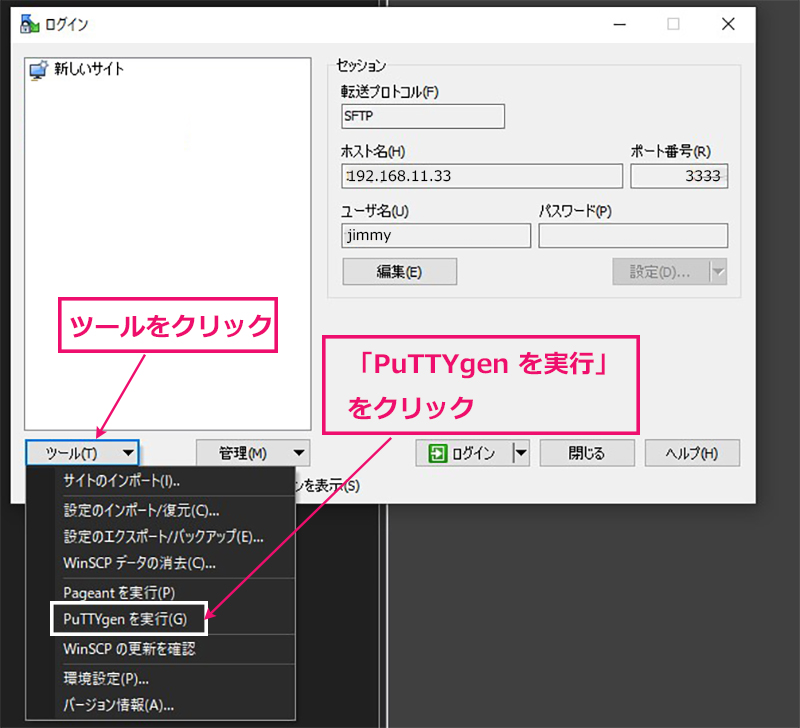
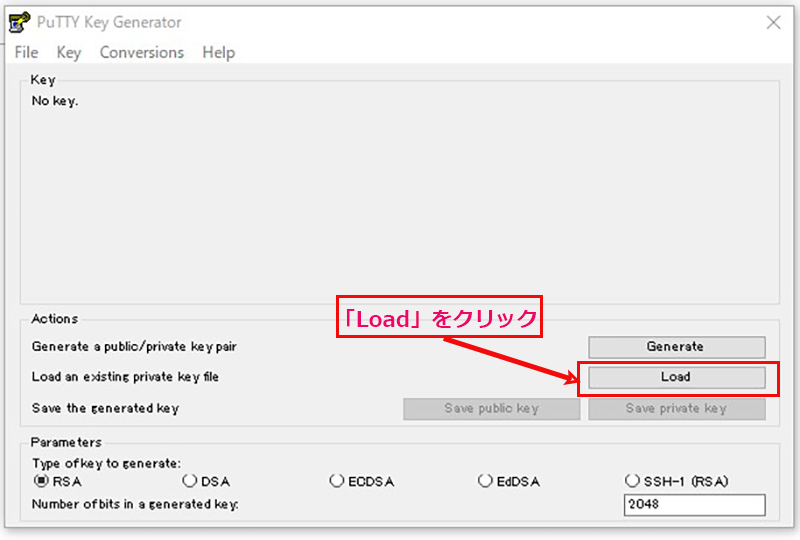
⑥WinSCP の設定変更(WinSCP に付属しているPuTTYgen を使用する)
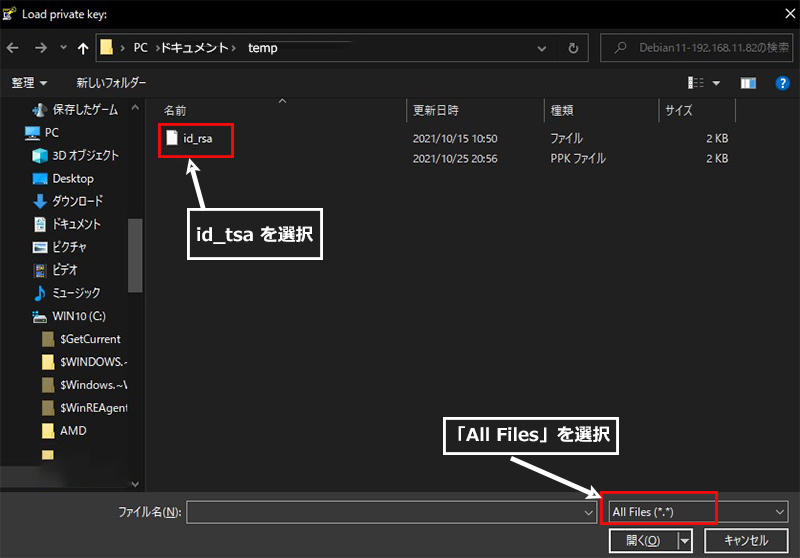
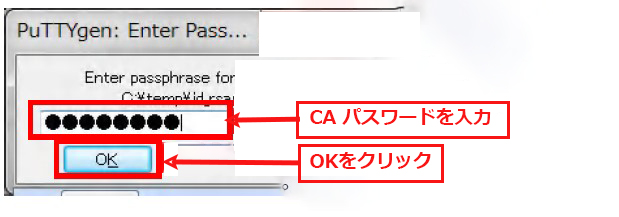
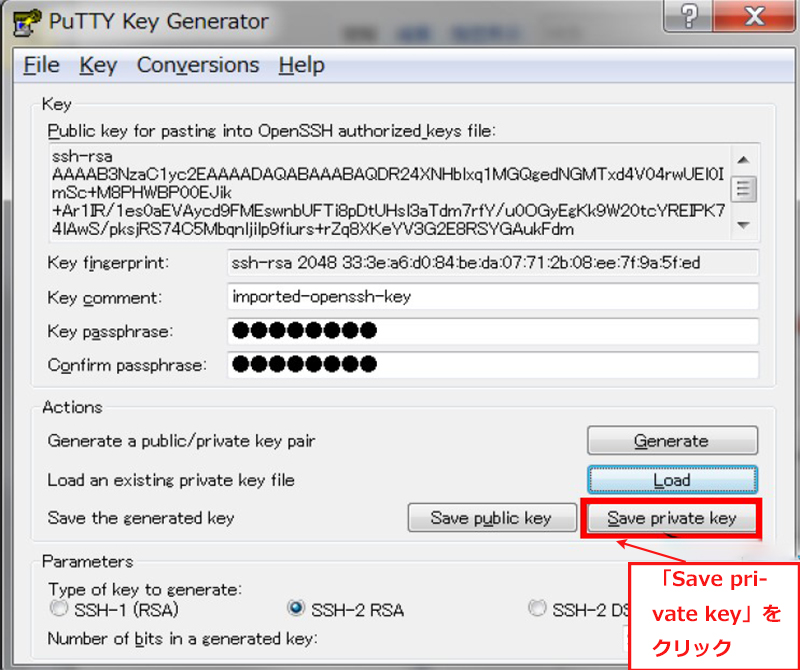
WinSCP を起動し、「ツール」をクリック