Tripwire
Implement a system to detect file tampering on Linux servers by crackers.
This time, Tripwire, a host-based IDS (IDS=Intrusion Detection System), will be installed as the file tampering detection system.
Tripwire detects file additions/changes/deletions by creating a database of file status at the time of installation and comparing the database with the current status of the file.
1. Installation and configuration.
|
1 |
# apt install tripwire |
①Create Site Key
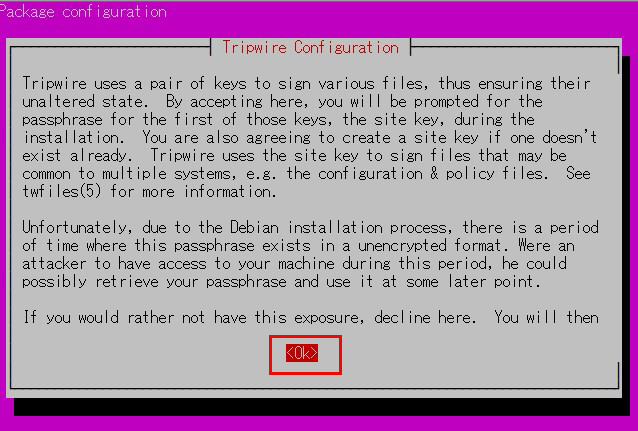
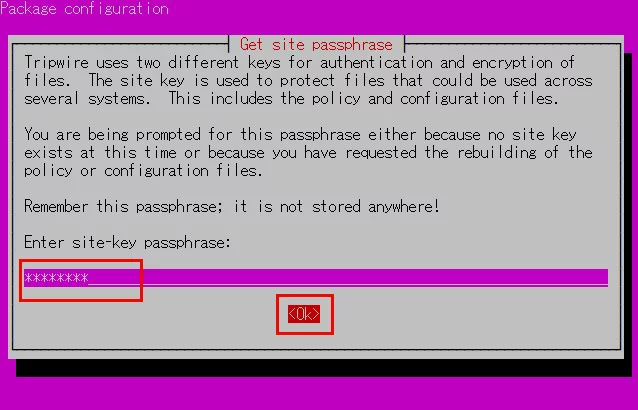
Tripwire requires a site passphrase to secure the "tw.cfg" tripwire configuration file and the "tw.pol" tripwire policy file.
The specified passphrase is used to encrypt both files.
The site passphrase is also required for a single instance of tripwire.
②local key passphrase
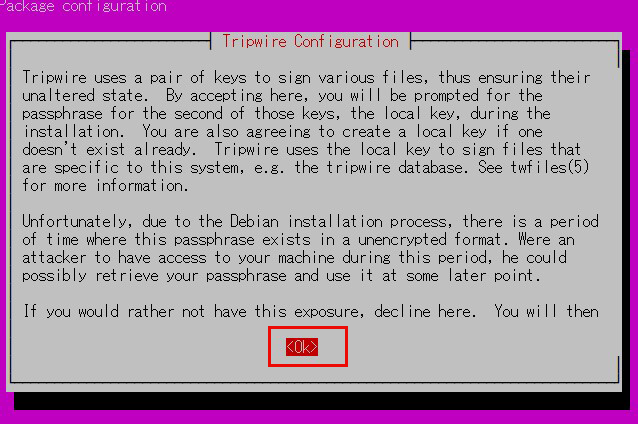
A local passphrase is required to protect the tripwire database and report files.
A local key used by tripwire to avoid unauthorized modification of the tripwire baseline database.
③tripwire configuration path
The tripwire configuration is stored in the file /etc/tripwire/twcfg.txt.
It is used to generate the encrypted configuration file tw.cfg.
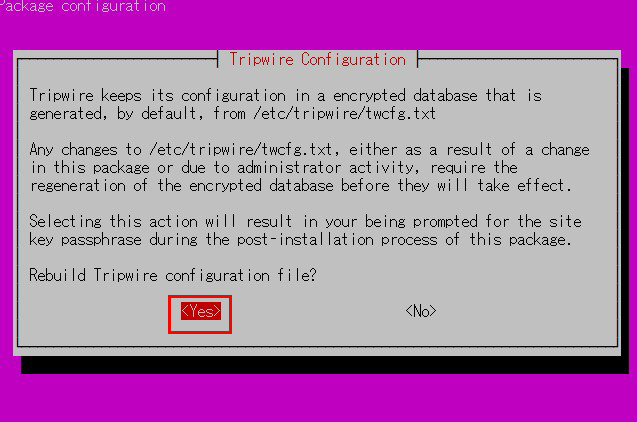
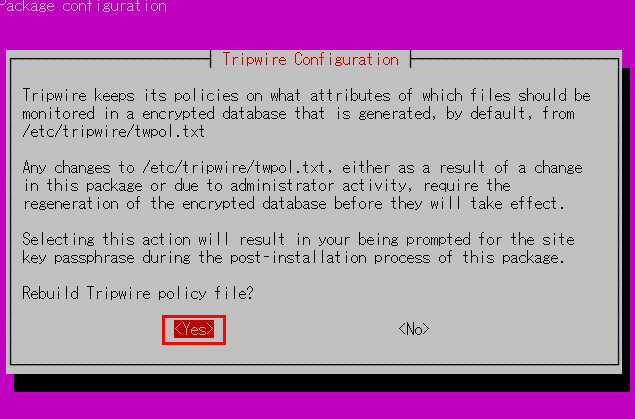
④tripwire policy path
tripwire stores policies in the file /etc/tripwire/twpol.txt.
This is used to generate the encrypted policy file tw.pol used by tripwire.
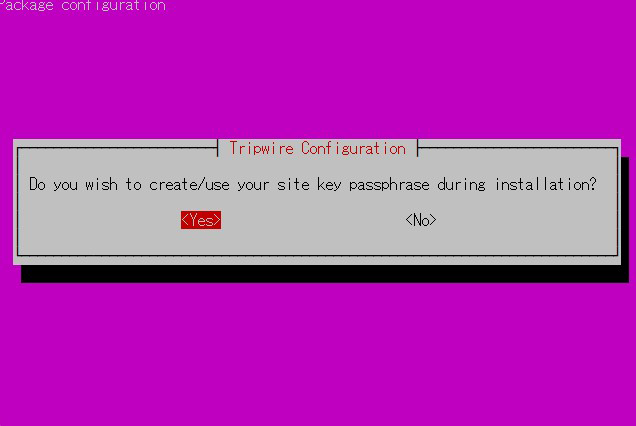
⑤Enter site key passphrase
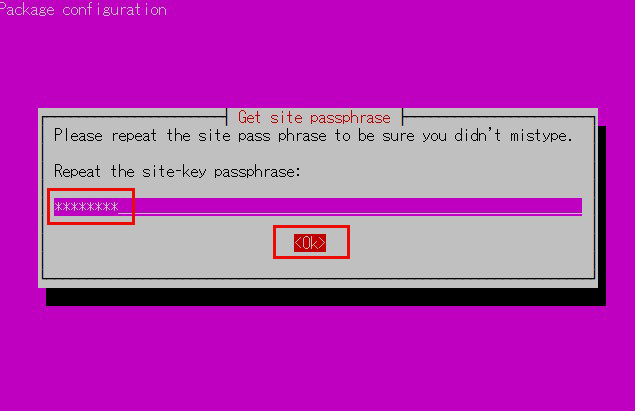
You will be asked to enter the site key passphrase again.
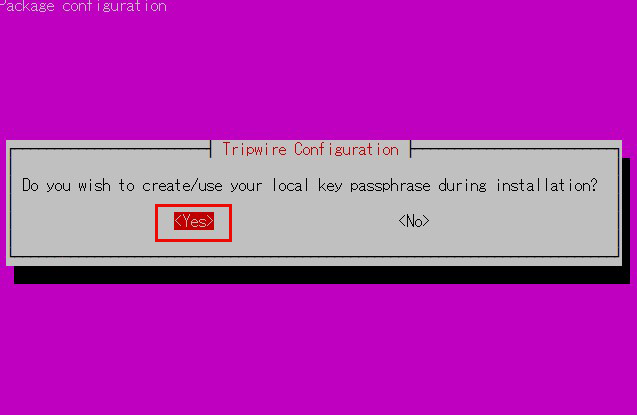
⑥Enter local key passphrase
⑦You will be asked to enter the local key passphrase again.
⑧Installation will proceed and complete.
2. Configuration File Settings
①Tripwire configuration file (twcfg.txt)
The tripwire configuration file (twcfg.txt) is detailed below.
The paths to the encrypted policy file (tw.pol), site key (site.key), and local key (hostname local.key), etc. are as follows
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
ROOT =/usr/sbin executable file POLFILE =/etc/tripwire/tw.pol DBFILE =/var/lib/tripwire/$(HOSTNAME).twd database file REPORTFILE =/var/lib/tripwire/report/$(HOSTNAME)-$(DATE).twr SITEKEYFILE =/etc/tripwire/site.key LOCALKEYFILE =/etc/tripwire/$(HOSTNAME)-local.key EDITOR =/usr/bin/editor LATEPROMPTING =false LOOSEDIRECTORYCHECKING =false MAILNOVIOLATIONS =true EMAILREPORTLEVEL =3 REPORTLEVEL =3 SYSLOGREPORTING =true MAILMETHOD =SMTP SMTPHOST =localhost SMTPPORT =25 TEMPDIRECTORY =/tmp |
3. Initial setup such as key creation, database creation, etc.
①Edit twcfg.txt
|
1 2 3 4 5 6 7 8 |
# cd /etc/tripwire # vi twcfg.txt Line9 Add "#" at the beginning of the line and "LOOSEDIRECTORYCHECKING =true" on the line below it #LOOSEDIRECTORYCHECKING =false LOOSEDIRECTORYCHECKING =true Line 12:Change as needed (maximum report level: 4) REPORTLEVEL =4 |
②configuration file generation
|
1 2 3 |
# twadmin -m F -c tw.cfg -S site.key twcfg.txt Please enter your site passphrase: <Site Key Passphrase> Wrote configuration file: /etc/tripwire/tw.cfg |
③ Optimize Policy
Use the following policy optimization scripts to optimize your policy
|
1 |
# vi twpolmake.pl |
Policy Optimization Script Contents
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 |
#!/usr/bin/perl $POLFILE=$ARGV[0]; open(POL,"$POLFILE") or die "open error: $POLFILE" ; my($myhost,$thost) ; my($sharp,$tpath,$cond) ; my($INRULE) = 0 ; while (<POL>) { chomp; if (($thost) = /^HOSTNAME\s*=\s*(.*)\s*;/) { $myhost = `hostname` ; chomp($myhost) ; if ($thost ne $myhost) { $_="HOSTNAME=\"$myhost\";" ; } } elsif ( /^{/ ) { $INRULE=1 ; } elsif ( /^}/ ) { $INRULE=0 ; } elsif ($INRULE == 1 and ($sharp,$tpath,$cond) = /^(\s*\#?\s*)(\/\S+)\b(\s+->\s+.+)$/) { $ret = ($sharp =~ s/\#//g) ; if ($tpath eq '/sbin/e2fsadm' ) { $cond =~ s/;\s+(tune2fs.*)$/; \#$1/ ; } if (! -s $tpath) { $_ = "$sharp#$tpath$cond" if ($ret == 0) ; } else { $_ = "$sharp$tpath$cond" ; } } print "$_\n" ; } close(POL) ; |
|
1 2 3 4 |
# perl twpolmake.pl twpol.txt > twpol.txt.new # twadmin -m P -c tw.cfg -p tw.pol -S site.key twpol.txt.new Please enter your site passphrase: <Site Key Passphrase> Wrote policy file: /etc/tripwire/tw.pol |
④Database Creation
|
1 2 |
# tripwire -m i -s -c tw.cfg Please enter your local passphrase: <Local Key Passphrase> |
If it stops with an error on the way, re-run with the "--verbose" option.
|
1 2 |
# tripwire -m i -c tw.cfg --verbose Please enter your local passphrase: <Local Key Passphrase> |
View the progress and check the files that stop with errors.
In our environment, it stopped at Snort-related files.
|
1 2 |
# chmod -R 5775 <Specify the file to stop at by absolute path> # chown -R snort:snort <Specify the file to stop at by absolute path> |
Paths and files expected to stop
/etc/snort/etc
/etc/snort/preproc_rules
/etc/snort/rules
/etc/snort/so_rules
/root/community-rules
After granting ownership and permissions to the above file, run the following again
|
1 2 |
# tripwire -m i -s -c tw.cfg Please enter your local passphrase: <Local Key Passphrase> |
When completed, the following will appear
|
1 2 3 4 5 6 7 8 |
Processing: /var/tmp --- Generating information for: /var/tmp Processing: /home --- Generating information for: /home Processing: /tmp --- Generating information for: /tmp Wrote database file: /var/lib/tripwire/Lepard.twd The database was successfully generated. |
4. Perform checks
①Create test file
|
1 |
# echo test > /root/test.txt |
②Check Tripwire operation
|
1 |
# tripwire -m c -s -c /etc/tripwire/tw.cfg |
If successful, the following display appears
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 |
Open Source Tripwire(R) 2.4.3.7 Integrity Check Report Report generated by: root Report created on: Sun 05 May 2024 07:51:15 JST Database last updated on: Never =============================================================================== Report Summary: =============================================================================== Host name: Lepard Host IP address: 127.0.1.1 Host ID: None Policy file used: /etc/tripwire/tw.pol Configuration file used: /etc/tripwire/tw.cfg Database file used: /var/lib/tripwire/Lepard.twd Command line used: tripwire -m c -s -c /etc/tripwire/tw.cfg =============================================================================== Rule Summary: =============================================================================== ------------------------------------------------------------------------------- Section: Unix File System ------------------------------------------------------------------------------- Rule Name Severity Level Added Removed Modified --------- -------------- ----- ------- -------- Other binaries 66 0 0 0 Tripwire Binaries 100 0 0 0 Other libraries 66 0 0 0 Root file-system executables 100 0 0 0 Tripwire Data Files 100 0 0 0 System boot changes 100 0 0 0 Root file-system libraries 100 0 0 0 (/lib) Critical system boot files 100 0 0 0 Other configuration files 66 0 0 0 (/etc) Boot Scripts 100 0 0 0 Security Control 66 0 0 0 * Root config files 100 1 0 0 Devices & Kernel information 100 0 0 0 (/dev) Invariant Directories 66 0 0 0 Total objects scanned: 43117 Total violations found: 1 =============================================================================== Object Summary: =============================================================================== ------------------------------------------------------------------------------- # Section: Unix File System ------------------------------------------------------------------------------- ------------------------------------------------------------------------------- Rule Name: Root config files (/root) Severity Level: 100 ------------------------------------------------------------------------------- Added: "/root/test.txt" =============================================================================== Error Report: =============================================================================== No Errors ------------------------------------------------------------------------------- *** End of report *** Open Source Tripwire 2.4 Portions copyright 2000-2018 Tripwire, Inc. Tripwire is a registered trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY; for details use --version. This is free software which may be redistributed or modified only under certain conditions; see COPYING for details. All rights reserved. |
Delete the test file.
|
1 |
# rm -f /root/test.txt |
5. Tripwire Autorun
①Create an auto-execution script (tripwire.sh) and have it run automatically
|
1 2 |
# cd /opt/script # vi tripwire.sh |
Contents of auto-execute script (tripwire.sh)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
#!/bin/bash PATH=/usr/sbin:/usr/bin:/bin:/usr/local/tripwire/sbin # Passphrase setting LOCALPASS=xxxxx # local key passphrase SITEPASS=xxxxx # Site Key Passphrase #Designation of e-mail address for notification MAIL="<your mailaddress> " cd /etc/tripwire # Tripwire check run tripwire -m c -s -c tw.cfg|mail -s "Tripwire(R) Integrity Check Report in `hostname`" $MAIL # Policy File Update twadmin -m p -c tw.cfg -p tw.pol -S site.key > twpol.txt perl twpolmake.pl twpol.txt > twpol.txt.new twadmin -m P -c tw.cfg -p tw.pol -S site.key -Q $SITEPASS twpol.txt.new > /dev/null rm -f twpol.txt* *.bak # Database Update rm -f /usr/local/tripwire/lib/tripwire/*.twd* tripwire -m i -s -c tw.cfg -P $LOCALPASS |
②Give execute permission and execute periodically by Cron.
|
1 2 3 |
# chmod 700 tripwire.sh # crontab -e 0 5 * * * /opt/script/tripwire.sh |
Execute the following command to confirm that notifications are delivered to the address set above
|
1 |
# /opt/script/tripwire.sh |
Introduce disk usage check script
1. Script Creation
|
1 2 |
# cd /opt/script/ # vi disk_capacity_check.sh |
Contents of disk_capacity_check.sh
|
1 2 3 4 5 6 7 8 9 10 |
#!/bin/bash # Designation of e-mail address for notification MAIL="<your mailaddress> " DVAL=`/bin/df / | /usr/bin/tail -1 | /bin/sed 's/^.* \([0-9]*\)%.*$/\1/'` if [ $DVAL -gt 80 ]; then echo "Disk usage alert: $DVAL %" | mail -s "Disk Space Alert in `hostname`" $MAIL fi |
|
1 |
# chmod 700 disk_capacity_check.sh |
2. Execution Confirmation
①Check current usage
|
1 |
# df -h |
It appears as follows
|
1 2 3 4 5 6 7 |
Filesystem Size Used Avail Use% Mounted on tmpfs 387M 4.7M 383M 2% /run /dev/mapper/ubuntu--vg-ubuntu--lv 14G 6.6G 6.4G 51% / tmpfs 1.9G 0 1.9G 0% /dev/shm tmpfs 5.0M 0 5.0M 0% /run/lock /dev/sda2 2.0G 95M 1.7G 6% /boot tmpfs 387M 12K 387M 1% /run/user/1000 |
Create a dummy file so that it is 80% or more (in this case, create about 5G).
|
1 |
# dd if=/dev/zero of=dummyfile bs=1M count=5000 |
③again Confirmation
|
1 |
# df -h |
Confirmation that it is above 80%.
④Run disk space check script
|
1 |
# /opt/script/disk_capacity_check.sh |
You will receive an email to the email address you set up with the body of the message as "Disk usage alert: 89 %".
⑤Delete the "dummyfile" you created.
|
1 |
# rm dummyfile |
⑥Periodic Execution Setting
|
1 2 |
# crontab -e 30 2 * * * /opt/script/disk_capacity_check.sh |
Log analysis tool Logwatch installed
1. Install logwatch
|
1 |
# apt -y install logwatch |
2. Edit logwatch configuration file
①Copy the default configuration file
# cp /usr/share/logwatch/default.conf/logwatch.conf /etc/logwatch/conf/
②Change email address, etc.
|
1 2 3 4 5 |
# vi /etc/logwatch/conf/logwatch.conf Line 52 MailTo =<your mailaddress> # < = Mailing address Line 84 Detail = High |
3. Creating Directories
There is no directory used by the cache, so create one.
|
1 |
# mkdir /var/cache/logwatch |
4. operation check
When logwatch is installed, cron is registered by default, so you will receive daily report emails.
If you want to check it immediately, do the following
|
1 |
# /etc/cron.daily/00logwatch |

