1.Introduced Clamav antivirus software
1.1 Install
|
1 |
# apt install clamav clamav-daemon |
1.2 Virus Definition Update
|
1 2 |
# systemctl stop clamav-freshclam # freshclam |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
Sat May 21 20:44:38 2022 -> ClamAV update process started at Sat May 21 20:44:38 2022 Sat May 21 20:44:38 2022 -> daily database available for update (local version: 26547, remote version: 26548) Current database is 1 version behind. Downloading database patch # 26548... Time: 0.1s, ETA: 0.0s [========================>] 4.54KiB/4.54KiB Sat May 21 20:44:39 2022 -> Testing database: '/var/lib/clamav/tmp.981f495cb5/clamav-8326c463cad95e3bdb0c82777fabee39.tmp-daily.cld' ... Sat May 21 20:44:43 2022 -> Database test passed. Sat May 21 20:44:43 2022 -> daily.cld updated (version: 26548, sigs: 1984525, f-level: 90, builder: raynman) Sat May 21 20:44:43 2022 -> main database available for download (remote version: 62) Time: 1.7s, ETA: 0.0s [========================>] 162.58MiB/162.58MiB Sat May 21 20:44:47 2022 -> Testing database: '/var/lib/clamav/tmp.981f495cb5/clamav-c2c43c703192aba0e8620feef8c408f4.tmp-main.cvd' ... Sat May 21 20:44:53 2022 -> Database test passed. Sat May 21 20:44:53 2022 -> main.cvd updated (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) Sat May 21 20:44:53 2022 -> bytecode database available for download (remote version: 333) Time: 0.1s, ETA: 0.0s [========================>] 286.79KiB/286.79KiB Sat May 21 20:44:53 2022 -> Testing database: '/var/lib/clamav/tmp.981f495cb5/clamav-9e09fff258e546a9ca671b3f4fc7c3da.tmp-bytecode.cvd' ... Sat May 21 20:44:53 2022 -> Database test passed. Sat May 21 20:44:53 2022 -> bytecode.cvd updated (version: 333, sigs: 92, f-level: 63, builder: awillia2) |
|
1 |
# systemctl start clamav-freshclam |
|
1 2 3 4 |
# vi /etc/logrotate.d/clamav-freshclam create 640 clamav adm ↓ create 640 clamav clamav |
1.3 Virus Check Confirmation
①Run virus check manually
|
1 2 3 4 5 6 7 8 9 10 11 12 |
# clamscan --infected --remove --recursive /home ----------- SCAN SUMMARY ----------- Known viruses: 8616546 Engine version: 0.103.6 Scanned directories: 4 Scanned files: 7 Infected files: 0 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 12.697 sec (0 m 12 s) Start Date: 2022:05:20 15:24:29 End Date: 2022:05:20 15:24:41 |
Infected files: 0 No virus.
②Virus detection by downloading test viruses
Download a harmless virus and test it for detection.
Log in as a general user and check
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# su - <user name> $ wget http://www.eicar.org/download/eicar.com $ clamscan --infected --remove --recursive /home /home/<user name>/eicar.com: Win.Test.EICAR_HDB-1 FOUND /home/<user name>/eicar.com: Removed. ----------- SCAN SUMMARY ----------- Known viruses: 8616546 Engine version: 0.103.6 Scanned directories: 4 Scanned files: 8 Infected files: 1 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 12.858 sec (0 m 12 s) Start Date: 2022:05:20 15:23:05 End Date: 2022:05:20 15:23:18 |
The virus is notified with the message "FOUND" and "Infected files: 1". Also, since the "--remove" option is attached, the test virus has been removed.
1.4 Create a script file to do a full scan
|
1 2 3 4 5 |
$ su - Password: # mkdir /opt/script (If /opt/script is missing) # cd /opt/script # vi clam-full.sh |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
#!/bin/sh echo ========================================= date hostname clamscan / \ --infected \ --recursive \ --log=/var/log/clamav/clamscan.log \ --move=/var/log/clamav/virus \ --exclude-dir=^/boot \ --exclude-dir=^/sys \ --exclude-dir=^/proc \ --exclude-dir=^/dev \ --exclude-dir=^/var/log/clamav/virus if [ $? = 0 ]; then echo "virus undetected." else echo "Virus detected!" fi |
|
1 |
# chmod +x /opt/script/clam-full.sh |
|
1 |
# mkdir /var/log/clamav/virus |
|
1 |
# /opt/script/clam-full.sh |
If you see the above
Run with the options "--max-filesize=200M" "--max-scansize=200M"
|
1 2 |
# crontab -e 0 2 * * mon /opt/script/clam-full.sh >> /var/log/clamav/clamascan.log |
2.Email software installation
2.1 Postfix : Installation/Configuration
Install Postfix and build an SMTP server; SMTP uses 25/TCP.
To prevent unauthorized mail relay, use the SASL function of Dovecot, described below, and configure Postfix so that authentication is also required for sending mail.
①Install
|
1 |
# apt -y install postfix sasl2-bin |
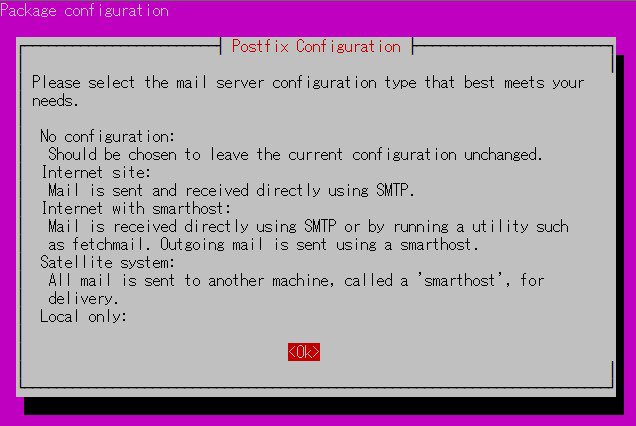
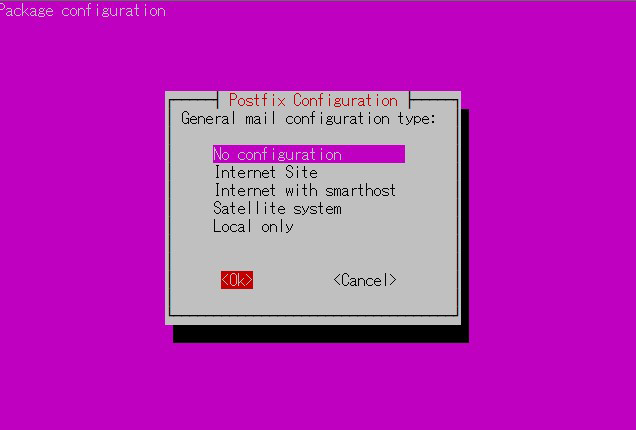
Installation Status Screen
You will be asked to select a general configuration setting, select "No Configuration" to set it manually later
②Configuration File Editing
|
1 2 |
# cp /usr/share/postfix/main.cf.dist /etc/postfix/main.cf # vi /etc/postfix/main.cf |
Editorial content
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 |
# Line 78:Uncomment mail_owner = postfix # Line 94:Uncomment host name specification myhostname = mail.<domain name> # Line 102:Uncomment domain name specification mydomain = <domain name> # Line 123:Uncomment myorigin = $mydomain # Line 137:Uncomment inet_interfaces = all # Line 185:Uncomment mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain # Line 228:Uncomment local_recipient_maps = unix:passwd.byname $alias_maps # Line 270:Uncomment mynetworks_style = subnet # Line 287:self-network addition mynetworks = 127.0.0.0/8, 192.168.11.0/24 # Line 407:Uncomment alias_maps = hash:/etc/aliases # Line 418:Uncomment alias_database = hash:/etc/aliases # Line 440:Uncomment home_mailbox = Maildir/ # Line 576:Make it a comment and add below it #smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu) smtpd_banner = $myhostname ESMTP # Line 650:add sendmail_path = /usr/sbin/postfix # Line 655:add newaliases_path = /usr/bin/newaliases # Line 660:add mailq_path = /usr/bin/mailq # Line 666:add setgid_group = postdrop # Line 670:comment #html_directory = # Line 674:comment #manpage_directory = # Line 679:comment #sample_directory = # Line 683:comment #readme_directory = # Added to the last line: Limit sent/received mail size to 10M message_size_limit = 10485760 # Limit mailbox size to 1G mailbox_size_limit = 1073741824 # SMTP-Auth Settings smtpd_sasl_type = dovecot smtpd_sasl_path = private/auth smtpd_sasl_auth_enable = yes smtpd_sasl_security_options = noanonymous smtpd_sasl_local_domain = $myhostname smtpd_recipient_restrictions = permit_mynetworks, permit_auth_destination, permit_sasl_authenticated, reject |
|
1 |
# vi /etc/postfix/master.cf |
Editorial content
|
1 2 3 4 5 6 7 8 9 10 |
smtp inet n - y - - smtpd #smtp inet n - y - 1 postscreen #smtpd pass - - y - - smtpd #dnsblog unix - - y - 0 dnsblog #tlsproxy unix - - y - 0 tlsproxy submission inet n - y - - smtpd # -o syslog_name=postfix/submission # -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes # -o smtpd_tls_auth_only=yes |
|
1 2 |
# newaliases # systemctl restart postfix |
2.2 Dovecot : Installation/Configuration
Install Dovecot and build a POP/IMAP server, using 110/TCP for POP and 143/TCP for IMAP
①Configure Dovecot to provide SASL functionality for Postfix
|
1 2 3 4 |
# apt -y install dovecot-core dovecot-pop3d dovecot-imapd # vi /etc/dovecot/dovecot.conf # Line 30:Uncomment listen = *, :: |
|
1 2 3 4 5 |
# vi /etc/dovecot/conf.d/10-auth.conf # Line 10:Uncomment change(Plain text authentication is also allowed) disable_plaintext_auth = no # Line 100:add auth_mechanisms = plain login |
|
1 2 3 |
# vi /etc/dovecot/conf.d/10-mail.conf # Line 30:Change to Maildir format mail_location = maildir:~/Maildir |
|
1 2 3 4 5 6 7 8 |
# vi /etc/dovecot/conf.d/10-master.conf # Line 107-109:Uncomment add # Postfix smtp-authi unix_listener /var/spool/postfix/private/auth { mode = 0666 user = postfix group = postfix } |
②Settings reflect
|
1 |
# systemctl restart dovecot |
2.3 Email User Account Registration
Register a user account for e-mail.
This setting is for when a user account on the OS is also used for e-mail.
①Mail client installed
|
1 |
# apt -y install mailutils |
②Mailboxes are set to refer to Maildir
|
1 |
# echo 'export MAIL=$HOME/Maildir/' >> /etc/profile.d/mail.sh |
③Test sending mail
Send test mail to yourself [mail (user name)@(host name)].
|
1 2 3 4 5 |
# su - <user name> $ mail <user name>@localhost Cc: Subject: Test Mail This is the first mail. |
Ctrl + D key to exit the main text
④Check incoming mail
|
1 2 3 |
$ mail "/home/<user name>/Maildir/": 1 message 1 new >N 1 <user name> 13/450 Test Mail |
2.4 Applied ClamAV to mail server Postfix
Set up Postfix and Clamav to work together to scan incoming and outgoing mail in real time.
①Install Amavisd and Clamav Daemon and start Clamav Daemon
|
1 2 3 |
$ su - Password: # apt -y install clamav-daemon amavisd-new |
If the server is not using a fully qualified domain name (FQDN) as the hostname, Amavis may fail to start. Also, since the OS hostname may change, set a valid hostname directly in the Amavis configuration file
|
1 2 3 4 5 6 |
# vi /etc/amavis/conf.d/05-node_id use strict;# $myhostname is used by amavisd-new for node identification, and it is # important to get it right (e.g. for ESMTP EHLO, loop detection, and so on) .chomp($myhostname = `hostname --fqdn`);# To manually set $myhostname, edit the following line with the correct Full y # Qualified Domain Name (FQDN) and remove the # at the beginning of the line . # $myhostname = "mail.<domain name>";1; # ensure a defined return |
②15-content_filter_mode edit
|
1 2 3 4 |
# vi /etc/amavis/conf.d/15-content_filter_mode # Uncomment and enable virus scan @bypass_virus_checks_maps = ( \%bypass_virus_checks, \@bypass_virus_checks_acl, \$bypass_virus_checks_re); |
③Register your own domain name
|
1 |
# echo '<yourDomain>' > /etc/mailname |
④Main.cf edit
|
1 2 3 |
# vi /etc/postfix/main.cf # Add to last line content_filter=smtp-amavis:[127.0.0.1]:10024 |
⑤master.cf edit
|
1 |
# vi /etc/postfix/master.cf |
Editorial content
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# Add all the following lines to the last line smtp-amavis unix - - n - 2 smtp -o smtp_data_done_timeout=1200 -o smtp_send_xforward_command=yes -o disable_dns_lookups=yes 127.0.0.1:10025 inet n - n - - smtpd -o content_filter= -o local_recipient_maps= -o relay_recipient_maps= -o smtpd_restriction_classes= -o smtpd_client_restrictions= -o smtpd_helo_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o mynetworks=127.0.0.0/8 -o strict_rfc821_envelopes=yes -o smtpd_error_sleep_time=0 -o smtpd_soft_error_limit=1001 -o smtpd_hard_error_limit=1000 |
|
1 2 3 |
# usermod -G clamav amavis # usermod -G amavis clamav # systemctl restart clamav-daemon amavis postfix |
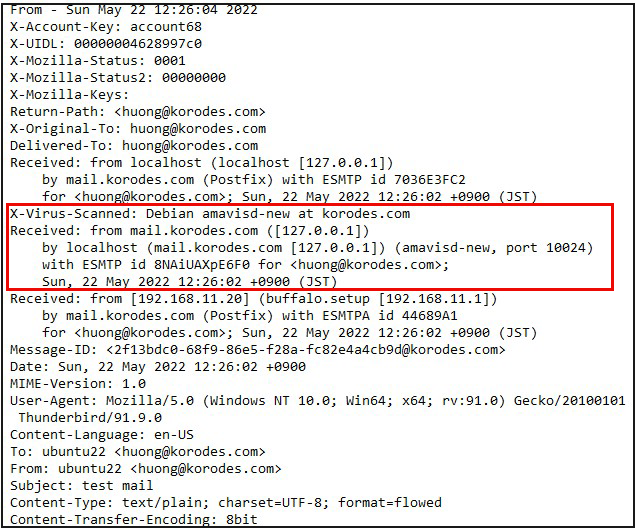
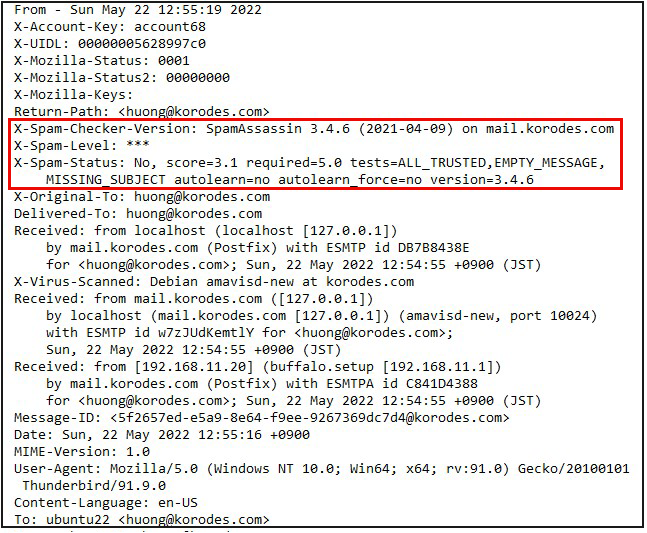
2.5 Applied spamassassin to mail server Postfix
2.5.1 Install spamassassin
①Install
|
1 2 3 |
# apt update # apt upgrade # apt install spamassassin |
②SpamAssassin Settings
The configuration file is "/etc/mail/spamassassin/local.cf".
- Use default without additional settings
- Creation of Maildir for storing spam mails
- Create a directory in Maildir format to store spam emails
- Create a directory ".Spam" in Maildir format for storing spam mails.
- Creation is done by the target user.
|
1 2 3 4 5 6 7 |
# su – <user name> $ cd ~ Create a directory named ".Spam" $ cd Maildir $ /usr/bin/maildirmake.dovecot .Spam $ su – Password: |
①Install Procmail
|
1 |
# apt install procmail |
If installed, the following results are returned
|
1 2 |
# which procmail /usr/bin/procmail |
②Procmail Settings
If you put it in "/etc/procmailrc", which is in charge of the entire mail filter, it will be applied to all users.
The filter will be applied only to that user if it is written in "/home/username/.procmailrc", which is an individual mail filter file for each user.
This time, to apply to all users, we will write the following in "/etc/procmailrc".
|
1 |
# vi /etc/procmailrc |
procmailrc description (newly created)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# Set path PATH=/bin:/usr/bin:/usr/local/bin # Mailbox Settings MAILDIR=$HOME/Maildir DEFAULT=$MAILDIR/ # Specify where to output Procmail log files LOGFILE=$MAILDIR/procmaillog #Specify lock file path LOCKFILE=$HOME/.lockmail # If there is no "X-Spam-***" in the mail header, spamassassassin will be started. :0fw *!^X-Spam.* |spamassassin # If the mail header contains "X-Spam-Status: Yes", the mail will be stored in the ".Spam" directory. :0 * ^X-Spam-Status: Yes $MAILDIR/.Spam/ |
① Edit main.cf
|
1 2 3 |
# vi /etc/postfix/main.cf # Add to the last line mailbox_command = /usr/bin/procmail |
②Reflecting and activating settings
|
1 2 |
# systemctl start spamassassin # systemctl restart postfix |
2.5.4 Spam Email Learning
Allows all users to learn the entire contents of their ".Spam" directory as spam mail
①Spam Email Learning
|
1 2 |
# /usr/bin/sa-learn --spam /home/*/Maildir/.Spam/cur Learned tokens from 0 message(s) (0 message(s) examined). <-- Learned 0 emails as spam mails |
②Normal mail learning
|
1 2 |
# /usr/bin/sa-learn --ham /home/*/Maildir/cur Learned tokens from 4 message(s) (4 message(s) examined). <-- Learned 4 emails as normal emails |
③Create a script and register it with Cron
Name the file "spam-learns.sh" and place it under /opt/script/.
After saving the script, give it executable access as "chmod 750 spam-learns.sh".
|
1 |
# vi /opt/script/spam-learns.sh |
spam-learns.sh Contents
|
1 2 3 4 5 6 7 |
#! /bin/sh # Spam Email Learning /usr/bin/sa-learn --spam /home/*/Maildir/.Spam/cur # Learning normal mail /usr/bin/sa-learn --ham /home/*/Maildir/cur # If you want to force the deletion of the contents of the spam mail storage directory, add the following statement /bin/rm -f /home/*/Maildir/.Spam/cur |
|
1 |
# chmod 750 /opt/script/spam-learns.sh |
Type is defined by simple
|
1 2 |
# cd /lib/systemd/system # vi spam-learns.service |
|
1 2 3 4 5 6 7 8 9 10 |
[Unit] Description=demo sample node.js program [Service] Type=simple ExecStart= /opt/script/spam-learns.sh Restart=always [Install] WantedBy=multi-user.target |
|
1 2 |
# crontab -e 0 4 * * * /opt/script/spam-learns.sh |
|
1 |
# systemctl enable spam-learns |