Contents
Snort3+Snortsnarf Install
Implement Snort, a network-based IDS, in the unauthorized access detection system.
SnortSnarf will also be installed to enable the unauthorized access logs extracted by Snort to be checked on a Web browser.
RockyLinux8 does not have a Snort3 repository, so build, compile and install Snort3 from source code
Advance preparation
①Install required build tools and libraries
Install the EPEL repository and enable the Powertools repository.
|
1 2 |
# dnf install epel-release # dnf config-manager --set-enabled powertools |
|
1 |
# dnf install bison flex libtool nghttp2 libnghttp2-devel libpcap-devel pcre-devel openssl-devel libdnet-devel libtirpc-devel git gcc-c++ libunwind-devel cmake hwloc-devel luajit-devel xz-devel libnfnetlink-devel libmnl-devel libnetfilter_queue-devel uuid-devel libsafec-devel -y |
②SNORT3 installation working directory creation
|
1 |
# mkdir snort_src && cd snort_src |
③DAQ Download Install
|
1 2 3 4 5 6 |
# git clone https://github.com/snort3/libdaq.git # cd libdaq # ./bootstrap # ./configure # make # make install |
④Tcmalloc Install
Installed gperftools to improve speed when memory usage increases
|
1 2 3 4 5 6 7 |
# cd ~/snort_src # wget https://github.com/gperftools/gperftools/releases/download/gperftools-2.9.1/gperftools-2.9.1.tar.gz # tar xzf gperftools-2.9.1.tar.gz # cd gperftools-2.9.1/ # ./configure # make # make install |
Snort3 Download Install
①Download, compile, and install Snort3
|
1 2 3 4 5 6 7 8 |
# cd ~/snort_src # wget https://github.com/snort3/snort3/archive/refs/tags/3.1.31.0.tar.gz # tar xzf 3.1.31.0.tar.gz # cd snort3-3.1.31.0 # ./configure_cmake.sh --prefix=/usr/local --enable-tcmalloc # cd build # make # make install |
②Update shared libraries
|
1 2 3 |
# ln -s /usr/local/lib/libtcmalloc.so.4 /lib/ # ln -s /usr/local/lib/libdaq.so.3 /lib/ # ldconfig |
Configure Snort3
①Network Interface Card Configuration
|
1 2 3 4 5 6 7 8 9 |
# ip link set dev ens160 promisc on # ip add sh ens160 2: ens160: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000 link/ether 00:0c:29:54:b7:1b brd ff:ff:ff:ff:ff:ff altname enp3s0 inet 192.168.11.83/24 brd 192.168.11.255 scope global noprefixroute ens160 valid_lft forever preferred_lft forever inet6 fe80::20c:29ff:fe54:b71b/64 scope link noprefixroute valid_lft forever preferred_lft forever |
Disable interface offloading so that Snort does not truncate packets larger than 1518 bytes
Confirmation of current status
|
1 2 3 |
# ethtool -k ens160 | grep receive-offload generic-receive-offload: on large-receive-offload: on |
Disable GRO and LRO as they are turned on.
|
1 |
# ethtool -K ens160 gro off lro off |
Create and enable systemd service so that changes will take effect after system reboot
|
1 |
# vi /etc/systemd/system/snort3-promisc.service |
Contents of snort3-promisc.service
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
[Unit] Description=Set Snort 3 NIC in promiscuous mode and Disable GRO, LRO on boot After=network.target [Service] Type=oneshot ExecStart=/usr/sbin/ip link set dev ens160 promisc on ExecStart=/usr/sbin/ethtool -K ens160 gro off lro off TimeoutStartSec=0 RemainAfterExit=yes [Install] WantedBy=default.target |
|
1 2 |
# systemctl daemon-reload # systemctl enable --now snort3-promisc.service |
②Configure rule sets
Set community rules this time
Create Snort Rules directory
|
1 |
# mkdir /usr/local/etc/rules |
③Download Snort 3 Community Rules from the Snort 3 Download Page
Extract the rules and copy them to the configuration folder
|
1 2 3 4 5 6 7 |
# wget -qO- https://www.snort.org/downloads/community/snort3-community-rules.tar.gz | tar xz -C /usr/local/etc/rules/ # ls -1 /usr/local/etc/rules/snort3-community-rules/ AUTHORS LICENSE sid-msg.map snort3-community.rules VRT-License.txt |
④Edit Main Configuration File
|
1 2 3 4 5 |
# vi /usr/local/etc/snort/snort.lua # Line 24: Change to own server IP address HOME_NET = '192.168.11.0/24' # Line 28 : Change EXTERNAL_NET = '!$HOME_NET' |
⑤Update path to rules
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# vi /usr/local/etc/snort/snort.lua # Per Line193 : Update rule paths in the ips section ips = { -- use this to enable decoder and inspector alerts --enable_builtin_rules = true,-- use include for rules files; be sure to set your path -- note that rules files can include other rules files -- (see also related path vars at the top of snort_defaults.lua) variables = default_variables, rules = [[ include $RULE_PATH/snort3-community-rules/snort3-community.rules ]] } |
⑥OpenAppID install
Download and install Snort OpenAppID from the Snort 3 download page
Please change to the latest version.
|
1 2 3 |
# wget https://www.snort.org/downloads/openappid/33380 -O OpenAppId-33380.tgz # tar -xzvf OpenAppId-33380.tgz # cp -R odp /usr/local/lib/ |
|
1 2 3 4 5 6 7 8 9 10 |
# vi /usr/local/etc/snort/snort.lua # Per Line 101 : Add appid = { -- appid requires this to use appids in rules --app_detector_dir = 'directory to load appid detectors from' app_detector_dir = '/usr/local/lib', log_stats = true, } |
⑦Snorts log directory creation
|
1 |
# mkdir /var/log/snort |
⑧Check configuration files
|
1 |
# snort -c /usr/local/etc/snort/snort.lua --daq-dir /usr/local/lib/daq |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 |
-------------------------------------------------- o")~ Snort++ 3.1.31.0 -------------------------------------------------- Loading /usr/local/etc/snort/snort.lua: Loading snort_defaults.lua: Finished snort_defaults.lua: Loading file_magic.lua: Finished file_magic.lua: ssh host_cache pop so_proxy stream_tcp mms smtp gtp_inspect packets dce_http_proxy stream_icmp ips normalizer binder wizard appid file_id http2_inspect stream_udp http_inspect ftp_data search_engine ftp_server port_scan dce_http_server dce_tcp dce_smb iec104 cip telnet ssl sip rpc_decode netflow modbus trace host_tracker stream_user stream_ip back_orifice classifications dnp3 active process ftp_client decode daq alerts stream network references arp_spoof output hosts dns dce_udp imap file_policy s7commplus stream_file Finished /usr/local/etc/snort/snort.lua: Loading ips.rules: Loading ../rules/snort3-community-rules/snort3-community.rules: Finished ../rules/snort3-community-rules/snort3-community.rules: Finished ips.rules: -------------------------------------------------- ips policies rule stats id loaded shared enabled file 0 4024 0 4024 /usr/local/etc/snort/snort.lua -------------------------------------------------- rule counts total rules loaded: 4024 text rules: 4024 option chains: 4024 chain headers: 323 flowbits: 48 flowbits not checked: 23 -------------------------------------------------- port rule counts tcp udp icmp ip any 473 58 147 22 src 177 17 0 0 dst 778 153 0 0 both 6 11 0 0 total 1434 239 147 22 -------------------------------------------------- service rule counts to-srv to-cli dcerpc: 7 4 dhcp: 2 2 dns: 28 7 ftp: 90 4 ftp-data: 1 97 http: 2085 256 http2: 2085 256 imap: 35 118 irc: 5 2 kerberos: 5 0 ldap: 0 1 mysql: 3 0 netbios-dgm: 1 1 netbios-ns: 4 3 netbios-ssn: 69 17 nntp: 2 0 pop3: 23 118 rdp: 5 0 sip: 5 5 smtp: 130 2 snmp: 18 7 ssdp: 3 0 ssl: 20 42 sunrpc: 68 4 telnet: 12 6 tftp: 1 0 wins: 1 0 total: 4708 952 -------------------------------------------------- fast pattern groups src: 59 dst: 158 any: 4 to_server: 47 to_client: 34 -------------------------------------------------- search engine instances: 302 patterns: 7522 pattern chars: 122098 num states: 82566 num match states: 7154 memory scale: MB total memory: 2.58907 pattern memory: 0.403095 match list memory: 0.91655 transition memory: 1.23256 fast pattern only: 4971 -------------------------------------------------- pcap DAQ configured to passive. Snort successfully validated the configuration (with 0 warnings). o")~ Snort exiting |
⑨Create custom local rules
|
1 2 3 |
# vi /usr/local/etc/rules/local.rules Fill in the following alert icmp any any -> $HOME_NET any (msg:"ICMP connection test"; sid:1000001; rev:1;) |
Next, run the test by executing the following command
|
1 |
# snort -c /usr/local/etc/snort/snort.lua -R /usr/local/etc/rules/local.rules -i ens160 -A alert_fast -s 65535 -k none --daq-dir /usr/local/lib/daq |
When pinging this server from another PC in the same local network, an alert line is written on the console screen of this server as shown below.
|
1 2 3 4 5 6 7 8 9 10 11 |
Commencing packet processing ++ [0] ens160 10/26-18:45:32.295852 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.22 -> 192.168.11.83 10/26-18:45:32.295882 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.83 -> 192.168.11.22 10/26-18:45:32.295948 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.22 -> 192.168.11.83 10/26-18:45:32.295957 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.83 -> 192.168.11.22 10/26-18:45:33.311468 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.22 -> 192.168.11.83 10/26-18:45:33.311528 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.83 -> 192.168.11.22 10/26-18:45:33.311595 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.22 -> 192.168.11.83 10/26-18:45:33.311602 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.83 -> 192.168.11.22 |
⑩Settings for writing to log files
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
# vi /usr/local/etc/snort/snort.lua # Line 251 : Uncomment and add in the "-- 7. configure outputs" section -- event logging -- you can enable with defaults from the command line with -A -- uncomment below to set non-default configs --alert_csv = { } alert_fast = { file = true, packet = false, limit = 10, } --alert_full = { } --alert_sfsocket = { } --alert_syslog = { } --unified2 = { } |
An alert_fast.txt file is created in the log directory
Perform syntax check
|
1 |
# snort -c /usr/local/etc/snort/snort.lua -R /usr/local/etc/rules/local.rules -i ens160 -s 65535 -k none -l /var/log/snort/ --daq-dir /usr/local/lib/daq |
When I pinged the server again from another PC in the same network, this time nothing appeared on the console screen, but
Checking the log directory, an alert_fast.txt file has been created
To check the alert_fast.txt file
|
1 |
# tail -f /var/log/snort/alert_fast.txt |
⑪Include local rules in snort.lua
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
# vi /usr/local/etc/snort/snort.lua # Line 197 : Add ips = { -- use this to enable decoder and inspector alerts --enable_builtin_rules = true,-- use include for rules files; be sure to set your path -- note that rules files can include other rules files -- (see also related path vars at the top of snort_defaults.lua) variables = default_variables, rules = [[ include $RULE_PATH/snort3-community-rules/snort3-community.rules include $RULE_PATH/local.rules ]] } |
Run Snort in the background
①Create a non-login system user account for Snort
|
1 |
# useradd -r -s /usr/sbin/nologin -M -c SNORT_IDS snort |
②Create systemd service unit for Snort
|
1 |
# vi /etc/systemd/system/snort3.service |
Describe the following
|
1 2 3 4 5 6 7 8 9 10 11 |
[Unit] Description=Snort Daemon After=syslog.target network.target [Service] Type=simple ExecStart=/usr/local/bin/snort -c /usr/local/etc/snort/snort.lua -s 65535 -k none -l /var/log/snort -D -i ens160 -m 0x1b -u snort -g snort --daq-dir /usr/local/lib/daq ExecStop=/bin/kill -9 $MAINPID [Install] WantedBy=multi-user.target |
Reload systemd configuration
|
1 |
# systemctl daemon-reload |
Set ownership and permissions for log files
|
1 2 |
# chmod -R 5775 /var/log/snort # chown -R snort:snort /var/log/snort |
③Enable Snort to start and run at system startup
|
1 2 |
# systemctl enable --now snort3 Created symlink /etc/systemd/system/multi-user.target.wants/snort3.service → /etc/systemd/system/snort3.service. |
|
1 2 3 4 5 6 7 8 9 10 11 |
# systemctl status snort3 ● snort3.service - Snort Daemon Loaded: loaded (/etc/systemd/system/snort3.service; enabled; vendor preset: disabled) Active: active (running) since Thu 2023-10-26 18:53:53 JST; 9s ago Main PID: 37570 (snort) Tasks: 2 (limit: 23021) Memory: 270.5M CGroup: /system.slice/snort3.service mq37570 /usr/local/bin/snort -c /usr/local/etc/snort/snort.lua -s 65535 -k none -l /var/log/snort -D -i ens160 -m 0x1b -u snort -g snort -> Oct 26 18:53:53 Lepard systemd[1]: Started Snort Daemon. |
Place log rotation configuration file
①Configuration File Creation
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# vi /etc/logrotate.d/snort Describe the following /var/log/snort/alert_fast.txt /var/log/snort/*log { weekly rotate 4 create 0600 snort snort dateext missingok compress notifempty sharedscripts postrotate /usr/bin/systemctl restart snort3 1>/dev/null || true endscript } |
➁Test # Force execution with -f option
|
1 |
# logrotate -f /etc/logrotate.d/snort |
Log file confirmation
|
1 2 3 |
# ls -l /var/log/snort alert_fast.txt-20240115.gz appid_stats.log-20240115.gz |
|
1 2 3 4 |
# cat /var/lib/logrotate/logrotate.status "/var/log/snort/appid_stats.log" 2024-1-15-14:50:18 "/var/log/snort/alert_fast.txt" 2024-1-15-14:50:18 "/var/log/snort/file.log" 2024-1-15-13:0:0 |
Snortsnarf Install
①advance preparation
Install Perl Time-modules
|
1 |
# dnf -y install perl-Time-modules |
Cpan Installation
|
1 |
# dnf install cpan |
|
1 2 |
# cpan Time::ParseDate # mkdir /usr/local/snortsnarf |
➁Download and install Snortsnarf
|
1 2 3 4 |
# wget https://sourceforge.net/projects/snortsnarf/files/latest/download/SnortSnarf-1.0.tar.gz # tar xvfz SnortSnarf-1.0.tar.gz # cp -v SnortSnarf-1.0/snortsnarf.pl /usr/local/snortsnarf # cp -vrf SnortSnarf-1.0/include/ /usr/local/snortsnarf |
➂Edit configuration files, etc.
|
1 2 3 4 5 6 |
# vi /usr/local/snortsnarf/snortsnarf.pl Line 78 use lib qw(./include); ↓change use lib qw(/usr/local/snortsnarf/include); |
|
1 2 3 |
# vi /usr/local/snortsnarf/include/SnortSnarf/HTMLMemStorage.pm Line 290 return @arr->[($first-1)..$end]; Delete "->" return @arr[($first-1)..$end]; |
|
1 2 3 |
# vi /usr/local/snortsnarf/include/SnortSnarf/HTMLAnomMemStorage.pm Line 266 return @arr->[($first-1)..$end]; Delete "->" return @arr[($first-1)..$end]; |
④Creation of analysis result output directory
|
1 2 |
# mkdir /var/www/html/snortsnarf # chown apache:apache /var/www/html/snortsnarf |
⑤Access control to analysis results
|
1 2 3 4 5 6 7 8 |
# vi /etc/httpd/conf/httpd.conf For Apache 2.4, add per line 161 <Directory "/var/www/html/snortsnarf"> DirectoryIndex index.html Options +ExecCGI require ip 127.0.0.1 192.168.11.0/24 </Directory> |
⑥Execution and Confirmation
|
1 |
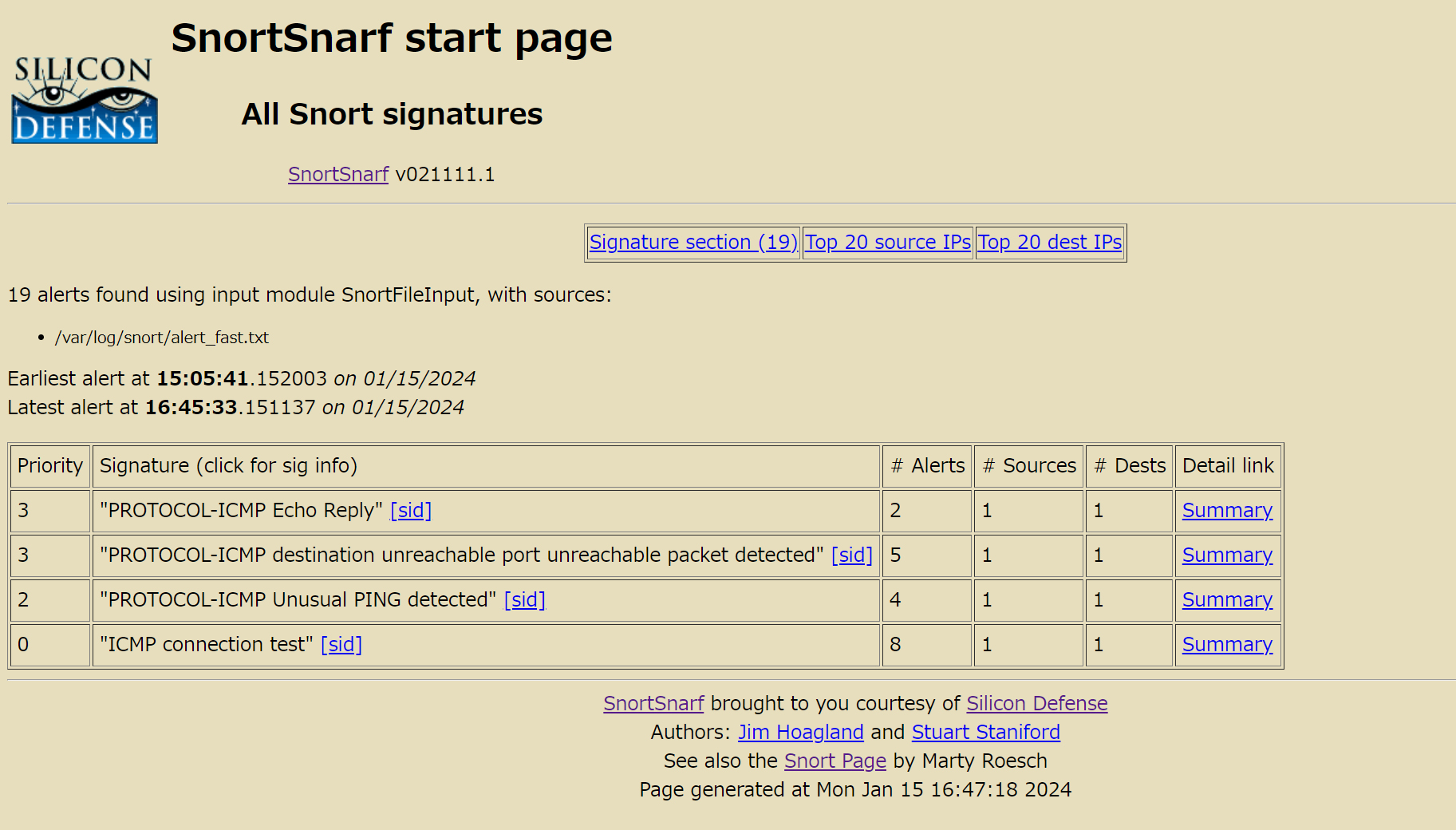
# /usr/local/snortsnarf/snortsnarf.pl /var/log/snort/alert_fast.txt -d /var/www/html/snortsnarf |
Access http://[server IP]/snortsnarf/ with a browser, and you should see the following screen
chkrootkit Install
①Download and install chkrootkit
|
1 2 3 |
# cd /usr/local/src # wget https://launchpad.net/chkrootkit/main/0.55/+download/chkrootkit-0.55.tar.gz # tar xvf chkrootkit-0.55.tar.gz |
➁Create /root/bin directory and move chkrootkit command to that directory
|
1 2 |
# mkdir -p /root/bin # mv chkrootkit-0.55/chkrootkit /root/bin |
➂Check chkrootkit.
|
1 |
# chkrootkit | grep INFECTED |
Searching for Linux.Xor.DDoS … INFECTED: Possible Malicious Linux.Xor.DDoS installed
If the above message appears, there may be an executable file under /tmp.
When I checked the files under /tmp, I found a file "ks-script-xxx", so I deleted it and reexecuted the file.
INFECTED disappeared.
④Create chkrootkit periodic execution script and change permissions
Create chkrootkit execution script in a directory where it is automatically executed daily
|
1 |
# vi /etc/cron.daily/chkrootkit |
chkrootkit contents
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
#!/bin/bash PATH=/usr/bin:/bin:/root/bin LOG=/tmp/$(basename ${0}) # Run chkrootkit chkrootkit > $LOG 2>&1 # log output cat $LOG | logger -t $(basename ${0}) # SMTPS bindshell false positive response if [ ! -z "$(grep 465 $LOG)" ] && \ [ -z $(/usr/sbin/lsof -i:465|grep bindshell) ]; then sed -i '/465/d' $LOG fi # Support for Suckit false positives when updating upstart package if [ ! -z "$(grep Suckit $LOG)" ] && \ [ -z "$(rpm -V `rpm -qf /sbin/init`)" ]; then sed -i '/Suckit/d' $LOG fi # Send mail to root only when rootkit is detected [ ! -z "$(grep INFECTED $LOG)" ] && \ grep INFECTED $LOG | mail -s "chkrootkit report in `hostname`" root |
Add execution permission to chkrootkit execution script
|
1 |
# chmod 700 /etc/cron.daily/chkrootkit |
④Securing commands used by chkrootkit
If the commands used by chkrootkit are tampered with, rootkit will not be detected.
Back up these commands.
If necessary, run chkrootkit with the backed up command
chkrootkit use command save destination directory creation
|
1 |
# mkdir chkrootkitcmd |
Copy chkrootkit commands to the destination directory
|
1 |
# cp `which --skip-alias awk cut echo egrep find head id ls netstat ps strings sed ssh uname` chkrootkitcmd/ |
Execute chkrootkit using the saved chkrootkit use command
|
1 |
# chkrootkit -p /root/chkrootkitcmd|grep INFECTED |
chkrootkit use command save destination directory compressed and deleted
|
1 |
# zip -r chkrootkitcmd.zip chkrootkitcmd/ && rm -rf chkrootkitcmd |
Send chkrootkit use command (compressed version) to root by e-mail
|
1 2 |
# dnf install mailx # echo|mail -a chkrootkitcmd.zip -s chkrootkitcmd.zip root |
chkrootkit use command (compressed version) removed
|
1 |
# rm -f chkrootkitcmd.zip |

