1.Obtain SSL Certificate ( Let's Encrypt )
Install the latest open ssl
|
1 |
# dnf install openssl-devel |
1.1 Certificate Installation
|
1 2 |
# dnf -y install certbot # certbot certonly --webroot -w /var/www/html/[FQDN] -d [FQDN] |
# Registration of e-mail address and agreement to terms of use are required for the first time only.
# Specify an email address to receive
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 |
Saving debug log to /var/log/letsencrypt/letsencrypt.log Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): <mail address> - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server. Do you agree? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: y - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing, once your first certificate is successfully issued, to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: y Account registered. Requesting a certificate for <FQDN> Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/<FQDN>/fullchain.pem Key is saved at: /etc/letsencrypt/live/<FQDN>/privkey.pem This certificate expires on 2022-10-14. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
Success when displaye ""Successfully received certificate"
# The following certificate is obtained under [/etc/letsencrypt/live/<FQDN>/] as described in the message
# cert.pem ⇒ SSL server certificate (including public key)
# chain.pem ⇒ intermediate certificate
# fullchain.pem ⇒ File containing cert.pem and chain.pem combined
# privkey.pem ⇒ private key
※ Obtaining a Let's Encrypt certificate when the web server is not running
It is a prerequisite that the server on which the work is to be performed is accessible from the Internet at port 80.
#Use the simple Web server function by specifying [--standalone].
#-d [FQDN for which you want to get a certificate] # FQDN (Fully Qualified Domain Name) : Host Name. Fully Qualified Domain Name
#If there are multiple FQDNs for which you want to obtain certificates, specify multiple -d [FQDNs for which you want to obtain certificates
|
1 |
# certbot certonly --standalone -d <FQDN> |
Renewing certificates already obtained
# Renew all certificates with an expiration date of less than 30 days
# If you want to renew regardless of the number of days remaining on the expiration date, specify [--force-renewal] as well
|
1 |
# certbot [--force-renewal] renew |
1.2 Automatic renewal of certificates (Let's Encrypt)
①Pre-registration testing
Test the automatic renewal with the following --dry-run option. With this option, the certificate is not renewed and only the operation is tested, so there is no need to worry about getting caught in the limit of the number of times a certificate can be obtained.
|
1 |
# certbot renew --dry-run |
②Using Systemd Timer
|
1 2 3 4 5 6 7 8 9 10 |
# systemctl cat certbot-renew.timer # /usr/lib/systemd/system/certbot-renew.timer [Unit] Description=This is the timer to set the schedule for automated renewals [Timer] OnCalendar=*-*-* 00/12:00:00 RandomizedDelaySec=12hours Persistent=true [Install] WantedBy=timers.target |
|
1 |
# systemctl enable --now certbot-renew.timer |
|
1 2 3 4 5 |
# systemctl list-timers certbot-renew.timer NEXT LEFT LAST PASSED UNIT ACTIVATES Fri 2022-06-10 15:17:07 JST 4h 39min left n/a n/a certbot-renew.timer certbot-renew.service 1 timers listed. Pass --all to see loaded but inactive timers, too. |
2. Apache SSL
Install the following just in case
|
1 |
# dnf -y install mod_ssl |
2.1 Edit ssl.conf file
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# vi /etc/httpd/conf.d/ssl.conf ●Line 43 : Uncomment and change DocumentRoot "/var/www/html/<FQDN>" ●Line 44 : Uncomment and change ServerName <FQDN>:443 ●Line 85 : Comment-out and add it below # SSLCertificateFile /etc/pki/tls/certs/localhost.crt SSLCertificateFile /etc/letsencrypt/live/<FQDN>/cert.pem ●Lin 93 : Comment-out and add it below # SSLCertificateKeyFile /etc/pki/tls/private/localhost.key SSLCertificateKeyFile /etc/letsencrypt/live/<FQDN>/privkey.pem ●Line 103 : add SSLCertificateChainFile /etc/letsencrypt/live/<FQDN>/chain.pem |
|
1 |
# systemctl restart httpd |
|
1 2 3 4 |
# firewall-cmd --add-service=https --permanent success # firewall-cmd --reload success |
2.2 Redirect HTTP communications to HTTPS
|
1 2 3 |
RewriteEngine On RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L] |
3. Mail SSL/TLS(Let's Encrypt)
3.1 Obtaining a certificate for the mail server
Obtain a certificate for the mail server, but it cannot be obtained in the same way as above, so the following with the "--standalone" option fails.
|
1 |
# certbot certonly --standalone -d mail.<domain name> |
If I stop the web server once and then do it, it succeeds as follows
|
1 2 |
# systemctl stop httpd.service # certbot certonly --standalone -d mail.<domain name> |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
Saving debug log to /var/log/letsencrypt/letsencrypt.log Requesting a certificate for mail.<domain name> Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/mail.<domain name>/fullchain.pem Key is saved at: /etc/letsencrypt/live/mail.<domain name>/privkey.pem This certificate expires on 2022-10-11. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
3.2 Postfix Configuration
|
1 2 3 4 5 6 7 8 9 10 11 |
# vi /etc/postfix/main.cf ● Per line 709, 715 : comment #smtpd_tls_cert_file = /etc/pki/tls/certs/postfix.pem #smtpd_tls_key_file = /etc/pki/tls/private/postfix.key ● Add to the last line smtpd_use_tls = yes smtp_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_cert_file = /etc/letsencrypt/live/mail.<domain name>/fullchain.pem smtpd_tls_key_file = /etc/letsencrypt/live/mail.<domain name>/privkey.pem smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache |
|
1 2 3 4 5 6 7 8 9 10 11 |
# vi /etc/postfix/master.cf ● Line 19-22 : Uncomment submission inet n - n - - smtpd -o syslog_name=postfix/submission -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes ● Line 31-34 : Uncomment smtps inet n - n - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes |
3.3 Dovecot Settings
|
1 2 3 4 5 6 7 8 |
# vi /etc/dovecot/conf.d/10-ssl.conf ● Line 8:confirmation ssl = yes ● Line 14,15: comment and add it below #ssl_cert = </etc/pki/dovecot/certs/dovecot.pem #ssl_key = </etc/pki/dovecot/private/dovecot.pem ssl_cert = </etc/letsencrypt/live/mail.<domain name>/fullchain.pem ssl_key = </etc/letsencrypt/live/mail.<domain name>/privkey.pem |
|
1 2 |
# firewall-cmd --add-port=587/tcp --permanent # firewall-cmd --reload |
|
1 |
# systemctl restart postfix dovecot |
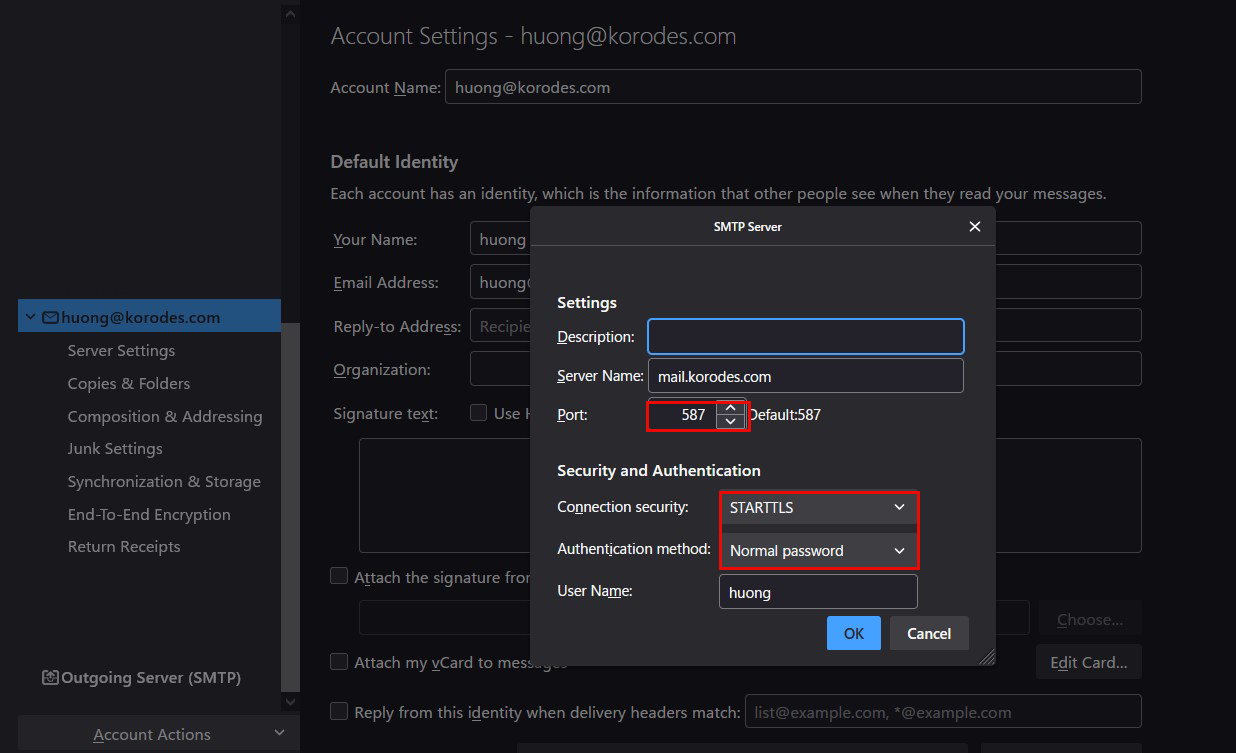
3.4 Thunderbird Settings
Connection security : STARTTLS
Authentication method : Normal password
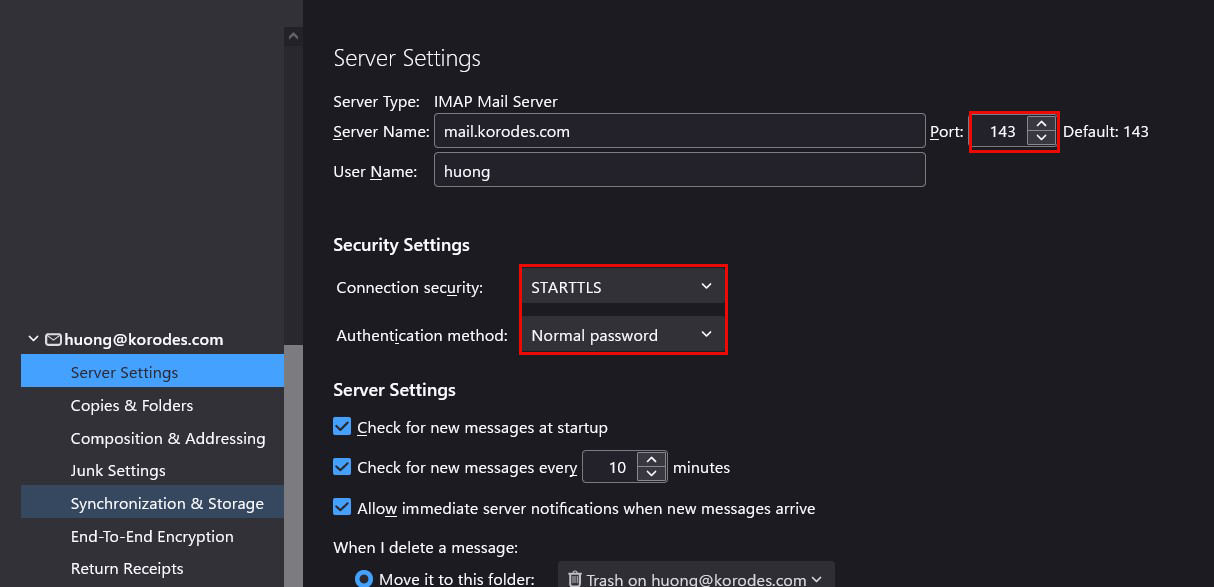
Connection security : STARTTLS
Authentication method : Normal password