Contents
1.Obtain a certificate (Let's Encrypt)
1.1 advance preparation
1.Enable mod_ssl
|
1 |
# a2enmod ssl |
2.Package management system Snappy installed
Let's Encrypt's SSL certificate issuing tool "certbot" is recommended to be installed using "snap" after 2021, so install Snapd first.
|
1 |
# apt install snapd |
Bring snapd version up to date
|
1 2 3 4 5 |
# snap install core core 16-2.60.3 from Canonical? installed # snap refresh core snap "core" has no updates available |
Version Check
|
1 2 3 4 5 6 |
# snap --version snap 2.60.3 snapd 2.60.3 series 16 ubuntu 23.04 kernel 6.2.0-34-generic |
1.2.certbot package install
|
1 2 |
# snap install --classic certbot certbot 2.7.0 from Certbot Project (certbot-eff?) installed |
Create symbolic link to /snap/bin/certbot
|
1 |
# ln -s /snap/bin/certbot /usr/bin/certbot |
Confirmation
|
1 2 3 4 5 |
# ls -la /usr/bin/certbot lrwxrwxrwx 1 root root 17 Oct 5 09:39 /usr/bin/certbot -> /snap/bin/certbot # ls -la /snap/bin/certbot lrwxrwxrwx 1 root root 13 Oct 5 09:34 /snap/bin/certbot -> /usr/bin/snap |
1.3 Obtain a Let's Encrypt Certificate
It is assumed that a web server such as Apache httpd or Nginx is running.
If the web server is not running on the server where the work is to be performed, follow the procedure below under "Obtaining a Let's Encrypt certificate when the web server is not running".
It is also assumed that the server on which the work is to be performed (the server with the FQDN of the server from which you want to obtain the certificate) is accessible from the Internet at port 80.
|
1 |
# certbot certonly --webroot -w /var/www/html/[FQDN] -d [FQDN] |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 |
Saving debug log to /var/log/letsencrypt/letsencrypt.log Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [Administrator's email address ] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf. You must agree in order to register with the ACME server. Do you agree? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing, once your first certificate is successfully issued, to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y Account registered. Requesting a certificate for [FQDN] Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/[FQDN]/fullchain.pem Key is saved at: /etc/letsencrypt/live/[FQDN]/privkey.pem This certificate expires on 2024-01-02. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
「Successfully received certificate.」
# The following certificate is obtained under [/etc/letsencrypt/live//] as described in the message
cert.pem ⇒ SSL server certificate (including public key)
chain.pem ⇒ intermediate certificate
fullchain.pem ⇒ a combined file of cert.pem and chain.pem
privkey.pem ⇒ private key for public key
Obtaining a Let's Encrypt certificate when the web server is not running
It is a prerequisite that the server on which this work is performed can be accessed from the Internet at port 80.
|
1 |
# certbot certonly --standalone -d <FQDN> |
1.4 Automatic renewal of certificates (Let's Encrypt)
①Pre-registration testing
First, test the automatic renewal using the following --dry-run option. With this option, the certificate is not renewed, but only the operation is tested, so there is no need to worry about being caught by the limit on the number of times a certificate can be obtained.
|
1 |
# certbot renew --dry-run |
②When you install the snap version of certbot, the automatic certificate renewal function is also installed.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# systemctl list-timers | less NEXT LEFT LAST PASSED UNIT ACTIVATES Thu 2023-10-05 10:09:00 JST 9s left Thu 2023-10-05 09:39:32 JST 29min ago phpsessionclean.timer phpsessionclean.service Thu 2023-10-05 11:38:18 JST 1h 29min left Wed 2023-10-04 15:52:32 JST 18h ago motd-news.timer motd-news.service Thu 2023-10-05 14:39:00 JST 4h 30min left - - snap.certbot.renew.timer snap.certbot.renew.service Thu 2023-10-05 14:56:29 JST 4h 47min left Thu 2023-10-05 08:47:45 JST 1h 21min ago ua-timer.timer ua-timer.service Thu 2023-10-05 20:03:19 JST 9h left Wed 2023-10-04 14:17:55 JST 19h ago fwupd-refresh.timer fwupd-refresh.service Fri 2023-10-06 00:00:00 JST 13h left - - dpkg-db-backup.timer dpkg-db-backup.service Fri 2023-10-06 00:00:00 JST 13h left Thu 2023-10-05 08:37:14 JST 1h 31min ago logrotate.timer logrotate.service Fri 2023-10-06 04:31:02 JST 18h left Thu 2023-10-05 09:17:45 JST 51min ago apt-daily.timer apt-daily.service Fri 2023-10-06 06:36:48 JST 20h left - - plocate-updatedb.timer plocate-updatedb.service Fri 2023-10-06 06:42:43 JST 20h left Thu 2023-10-05 08:38:55 JST 1h 29min ago apt-daily-upgrade.timer apt-daily-upgrade.service Fri 2023-10-06 08:42:02 JST 22h left Thu 2023-10-05 08:42:02 JST 1h 26min a: |
snap.certbot.renew.timer is registered
Check the unit file for snap.certbot.renew.timer
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
# vi /etc/systemd/system/snap.certbot.renew.timer [Unit] # Auto-generated, DO NOT EDIT Description=Timer renew for snap application certbot.renew Requires=snap-certbot-3369.mount After=snap-certbot-3369.mount X-Snappy=yes [Timer] Unit=snap.certbot.renew.service OnCalendar=*-*-* 03:51 OnCalendar=*-*-* 14:39 [Install] WantedBy=timers.target |
According to the above settings, it will attempt to update at 3:51 and 14:39 every day as specified in the OnCalender parameter (however, the set time will change randomly for each update).
Check the unit file snap.certbot.renew.service
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
# vi /etc/systemd/system/snap.certbot.renew.service [Unit] # Auto-generated, DO NOT EDIT Description=Service for snap application certbot.renew Requires=snap-certbot-3369.mount Wants=network.target After=snap-certbot-3369.mount network.target snapd.apparmor.service X-Snappy=yes [Service] EnvironmentFile=-/etc/environment ExecStart=/usr/bin/snap run --timer="00:00~24:00/2" certbot.renew SyslogIdentifier=certbot.renew Restart=no WorkingDirectory=/var/snap/certbot/3369 TimeoutStopSec=30 Type=oneshot |
However, the web server that uses the certificate will not be restarted, so set up a script that will run automatically after the update
|
1 2 3 4 |
# vi /etc/letsencrypt/renewal-hooks/post/web_restart.sh #!/bin/bash systemctl reload httpd |
|
1 |
# chmod 755 /etc/letsencrypt/renewal-hooks/post/web_restart.sh |
2. SSL/TLS (Let's Encrypt) configuration for Apache2
①Edit Apache2 SSL-related configuration files
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# cd /etc/apache2/sites-available/ # cp default-ssl.conf hoge.com-ssl.conf # vi hoge.com-ssl.conf # Line 2:Administrator address change ServerAdmin [Administrator Email Address] # Line 4:change DocumentRoot /var/www/html/[FQDN]/ # Line 12,13:change ErrorLog ${APACHE_LOG_DIR}/[FQDN].error.log CustomLog ${APACHE_LOG_DIR}/[FQDN].access.log combined # Line 31,32:Change to the certificate obtained in [1]. SSLCertificateFile /etc/letsencrypt/live/[FQDN]/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/[FQDN]/privkey.pem # Line 43:Uncomment and change to the chain file obtained in [1]. SSLCertificateChainFile /etc/letsencrypt/live/[FQDN]/chain.pem |
②Reflecting and activating the configuration file
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
# a2enmod ssl Considering dependency setenvif for ssl: Module setenvif already enabled Considering dependency mime for ssl: Module mime already enabled Considering dependency socache_shmcb for ssl: Enabling module socache_shmcb. Enabling module ssl. See /usr/share/doc/apache2/README.Debian.gz on how to configure SSL and create self-signed certificates. To activate the new configuration, you need to run: systemctl restart apache2 # a2ensite hoge.com-ssl.conf Enabling site hoge.com-ssl.conf. To activate the new configuration, you need to run: systemctl reload apache2 # systemctl restart apache2 # Default Disable # a2dissite default-ssl.conf # systemctl restart apache2 |
③http to https redirect
|
1 2 3 4 |
# a2enmod rewrite Enabling module rewrite. To activate the new configuration, you need to run: systemctl restart apache2 |
One of the following methods
|
1 2 3 4 5 6 7 8 9 10 |
1How to create a .htaccess file Create .htaccess in /var/www/html/[FQDN]/ and fill in the following RewriteEngine on RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L] 2.How to fill in /vhost-yourdomain.conf RewriteEngine on RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L] |
④Reflection of settings and startup
|
1 |
# a2ensite vhost-yourdomain.conf |
|
1 |
# a2enmod ssl |
Apache Restart
|
1 |
# systemctl restart apache2 |
3. SSL/TLS (Let's Encrypt) settings on the mail server
3.1 Obtaining a certificate for the mail server
Obtain a certificate for the mail server, but it cannot be obtained in the same way as above, so the following with the "--standalone" option fails.
|
1 |
# certbot certonly --standalone -d mail.<domain name> |
If I stop the web server once and then do it, it succeeds as follows
|
1 2 |
# systemctl stop apache2 # certbot certonly --standalone -d mail.<domain name> |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
Saving debug log to /var/log/letsencrypt/letsencrypt.log Requesting a certificate for mail.[domain name] Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/mail.[domain name]/fullchain.pem Key is saved at: /etc/letsencrypt/live/mail.[domain name]/privkey.pem This certificate expires on 2024-01-03. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
3.2 Postfix Configuration
|
1 2 3 4 5 6 7 8 9 |
# vi /etc/postfix/main.cf ● Add to the last line smtpd_use_tls = yes smtp_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_cert_file = /etc/letsencrypt/live/mail.[domain name]/fullchain.pem smtpd_tls_key_file = /etc/letsencrypt/live/mail.[domain name]/privkey.pem smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache |
SMTP-Submission is [587/TCP], SMTPS is [465/TCP].
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# vi /etc/postfix/master.cf Line 19-22 : Uncomment submission inet n - y - - smtpd -o syslog_name=postfix/submission -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes # Add to the last line smtps inet n - y - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes |
3.3 Dovecot Configuration
|
1 2 3 4 5 6 7 |
# vi /etc/dovecot/conf.d/10-ssl.conf Line 6:confirmation ssl = yes Line 12,13:Comment and add the following certificate/key file specification ssl_cert = </etc/letsencrypt/live/mail.[domain name]/fullchain.pem ssl_key = </etc/letsencrypt/live/mail.[domain name]/privkey.pem |
Allow Port 587
|
1 2 |
# ufw allow 587/tcp # ufw reload |
|
1 |
# systemctl restart postfix dovecot |
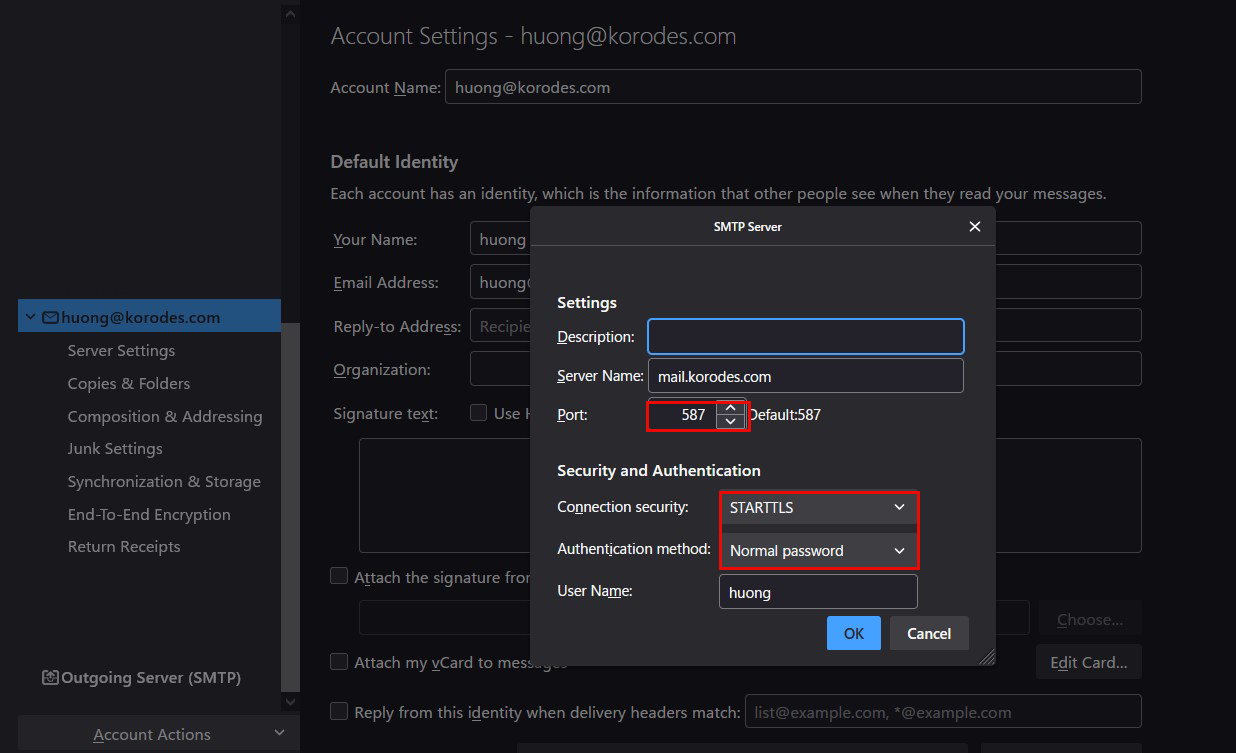
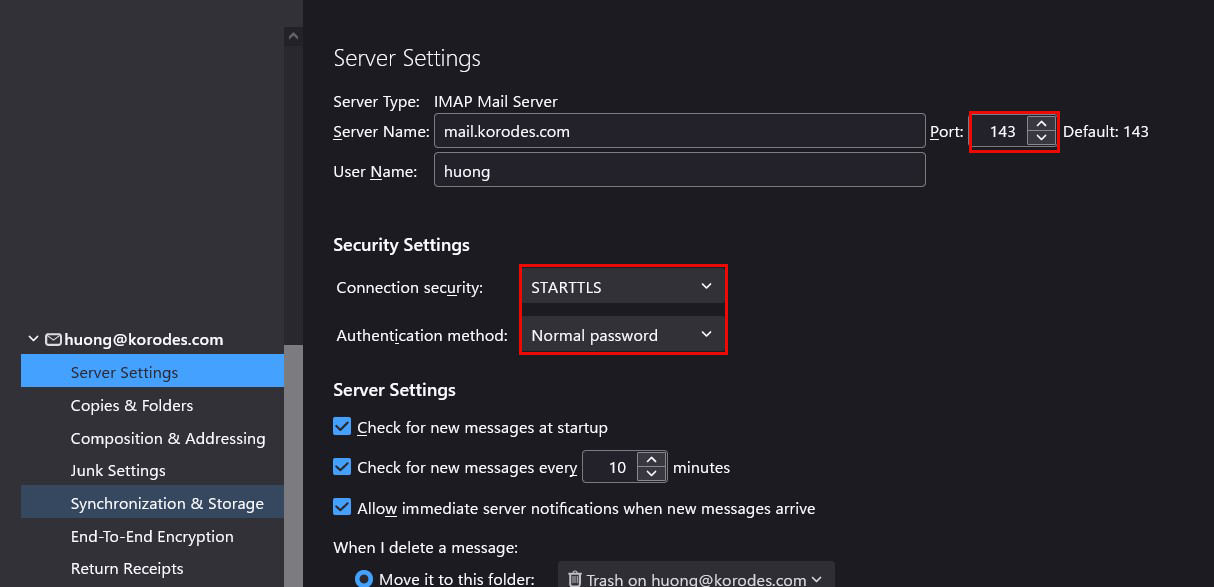
3.4 Thunderbird Settings
Incoming server
Port : 143
Connection security : STARTTLS
Authentication method : Normal password
Sending server
Port : 587
Connection security : STARTTLS
Authentication method : Normal password