Contents
1.Antivirus software Clamav installed
Install Clam AntiVirus, a free anti-virus software for Linux, as an anti-virus measure.
By installing this anti-virus software, you can not only scan the entire server for viruses, but also scan incoming and outgoing mail for viruses if you build and configure a mail server.
1.1 Install
|
1 |
# apt install clamav clamav-daemon |
The clamav-related configuration files are installed in the /etc/clamav/ folder.
1.2 Virus Definition Update
|
1 2 3 4 5 6 |
# systemctl stop clamav-freshclam # freshclam Sat Jun 17 15:42:41 2023 -> ClamAV update process started at Sat Jun 17 15:42:41 2023 Sat Jun 17 15:42:41 2023 -> daily.cvd database is up-to-date (version: 26941, sigs: 2037175, f-level: 90, builder: raynman) Sat Jun 17 15:42:41 2023 -> main.cvd database is up-to-date (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) Sat Jun 17 15:42:41 2023 -> bytecode.cvd database is up-to-date (version: 334, sigs: 91, f-level: 90, builder: anvilleg) |
|
1 |
# systemctl start clamav-freshclam |
Edit configuration file
|
1 2 3 4 |
# vi /etc/logrotate.d/clamav-freshclam create 640 clamav adm ↓ create 640 clamav clamav |
Automatic virus definition update confirmation
Ensure that the service is registered for automatic virus definition updates.
|
1 |
# service clamav-freshclam status |
It appears as follows
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
● clamav-freshclam.service - ClamAV virus database updater Loaded: loaded (/lib/systemd/system/clamav-freshclam.service; enabled; preset: enabled) Active: active (running) since Sat 2023-06-17 15:39:18 JST; 5min ago Docs: man:freshclam(1) man:freshclam.conf(5) https://docs.clamav.net/ Main PID: 18789 (freshclam) Tasks: 1 (limit: 2265) Memory: 234.4M CPU: 26.406s CGroup: /system.slice/clamav-freshclam.service mq18789 /usr/bin/freshclam -d --foreground=true Jun 17 15:39:35 Lepard freshclam[18789]: Sat Jun 17 15:39:35 2023 -> daily.cvd updated (version: 26941, sigs: 2037175> Jun 17 15:39:35 Lepard freshclam[18789]: Sat Jun 17 15:39:35 2023 -> main database available for download (remote ver> Jun 17 15:39:39 Lepard freshclam[18789]: Sat Jun 17 15:39:39 2023 -> Testing database: '/var/lib/clamav/tmp.0c18cec89> Jun 17 15:39:47 Lepard freshclam[18789]: Sat Jun 17 15:39:47 2023 -> Database test passed. Jun 17 15:39:47 Lepard freshclam[18789]: Sat Jun 17 15:39:47 2023 -> main.cvd updated (version: 62, sigs: 6647427, f-> Jun 17 15:39:47 Lepard freshclam[18789]: Sat Jun 17 15:39:47 2023 -> bytecode database available for download (remote> Jun 17 15:39:47 Lepard freshclam[18789]: Sat Jun 17 15:39:47 2023 -> Testing database: '/var/lib/clamav/tmp.0c18cec89> Jun 17 15:39:47 Lepard freshclam[18789]: Sat Jun 17 15:39:47 2023 -> Database test passed. Jun 17 15:39:47 Lepard freshclam[18789]: Sat Jun 17 15:39:47 2023 -> bytecode.cvd updated (version: 334, sigs: 91, f-> |
Logs are recorded in the file /var/log/clamav/freshclam.log.
1.3 Virus Check Confirmation
①Running manual virus checks
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# clamscan --infected --remove --recursive /home ----------- SCAN SUMMARY ----------- Known viruses: 8669076 Engine version: 1.0.1 Scanned directories: 3 Scanned files: 7 Infected files: 0 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 16.099 sec (0 m 16 s) Start Date: 2023:06:17 15:46:00 End Date: 2023:06:17 15:46:16 |
Infected files: 0, so no virus
②Virus detection by downloading test viruses
Download a harmless virus and test it for detection.
Log in as a general user and check
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
# su - <user name> $ wget http://www.eicar.org/download/eicar.com $ clamscan --infected --remove --recursive /home /home/huong/eicar.com: Win.Test.EICAR_HDB-1 FOUND /home/huong/eicar.com: Removed. ----------- SCAN SUMMARY ----------- Known viruses: 8669076 Engine version: 1.0.1 Scanned directories: 3 Scanned files: 8 Infected files: 1 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 13.475 sec (0 m 13 s) Start Date: 2023:06:17 15:47:25 End Date: 2023:06:17 15:47:39 |
As you can see, the virus is notified with the message "FOUND" and "Infected files: 1". The "--remove" option was also added, so the test virus was removed.
1.4 Create a script file to do a full scan
①Create a script file storage directory (/opt/script) in advance.
|
1 2 3 |
$ su - Password: # mkdir /opt/script |
②Create script file
|
1 |
# vi /opt/script/clam-full.sh |
Contents of clam-full.sh (new)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
#!/bin/sh echo ========================================= date hostname clamscan / \ --infected \ --recursive \ --log=/var/log/clamav/clamscan.log \ --move=/var/log/clamav/virus \ --exclude-dir=^/boot \ --exclude-dir=^/sys \ --exclude-dir=^/proc \ --exclude-dir=^/dev \ --exclude-dir=^/var/log/clamav/virus if [ $? = 0 ]; then echo “virus undetected.” else echo “virus detection!!” fi |
③execute authorization
|
1 |
# chmod +x /opt/script/clam-full.sh |
④Create a folder for virus quarantine
If not, a runtime error will occur because the above script specifies it as an excluded directory.
|
1 |
# mkdir /var/log/clamav/virus |
⑤Script Execution
|
1 |
# /opt/script/clam-full.sh |
|
1 2 3 4 5 6 7 8 9 10 11 12 |
----------- SCAN SUMMARY ----------- Known viruses: 8669076 Engine version: 1.0.1 Scanned directories: 3856 Scanned files: 30053 Infected files: 0 Data scanned: 2091.72 MB Data read: 1483.83 MB (ratio 1.41:1) Time: 233.338 sec (3 m 53 s) Start Date: 2023:06:17 15:57:40 End Date: 2023:06:17 16:01:33 “virus undetected.” |
Takes quite a long time to complete.
Logs are recorded in the /var/log/clamav/clamscan.log file.
⑤Scheduled virus scan execution with cron
|
1 2 |
# crontab -e 0 2 * * mon /opt/script/clam-full.sh >> /var/log/clamav/clamascan.log |
In the above example, it runs regularly every Monday at 2:00 AM.
2. Mail server installation
Postfix was developed as a Mail Transport Agent (MTA) to replace sendmail, and is a mail server that is highly compatible with sendmail, secure, easy to maintain, and fast.
In addition, since Postfix only functions as an SMTP server for sending mail, the POP server Dovecot for receiving mail will be installed separately in the latter half.
2.1 Postfix : Installation Configuration
①Install Postfix
Install Postfix and build an SMTP server; SMTP uses 25/TCP.
To prevent unauthorized mail relay, use the SASL function of Dovecot, described below, and configure Postfix so that authentication is also required for sending.
|
1 |
# apt -y install postfix sasl2-bin |
You will be asked to select general configuration settings, select "No configuration " to set them manually later
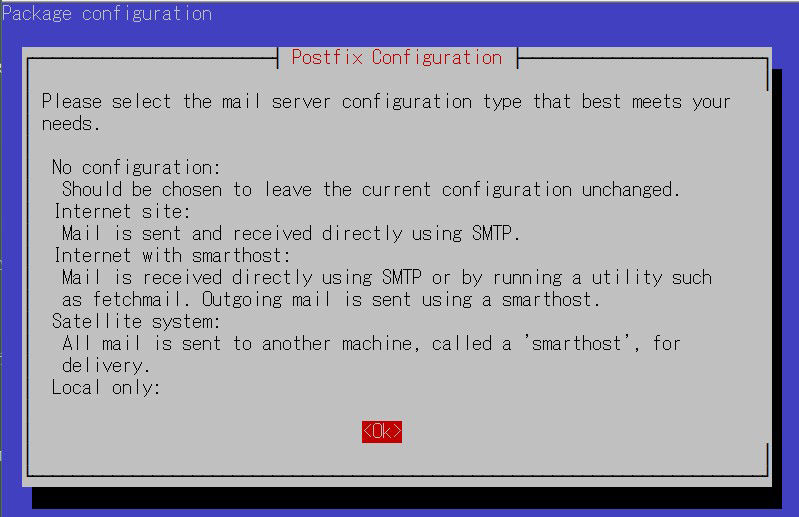
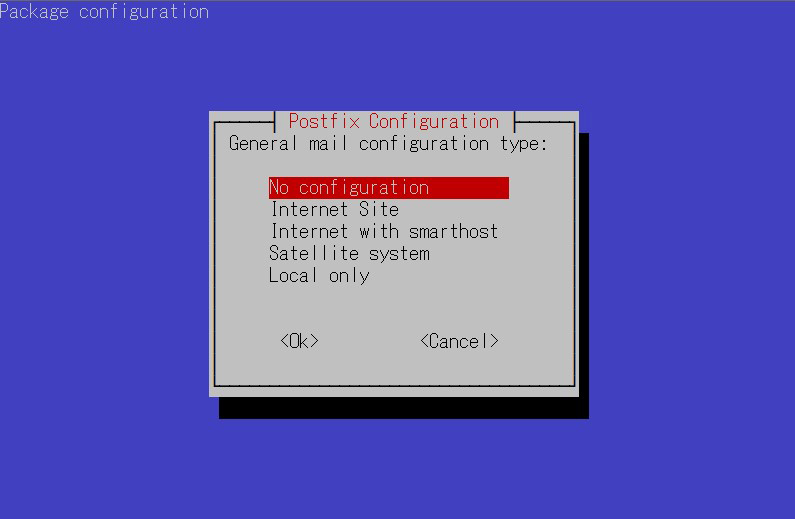
②Edit configuration file (main.cf)
|
1 2 |
# cp /usr/share/postfix/main.cf.dist /etc/postfix/main.cf # vi /etc/postfix/main.cf |
Editorial content
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 |
# Line 82:Uncomment mail_owner = postfix # Line 100:Uncomment and specify host name myhostname = mail.<domain name> # Per Line 107:domain add mydomain = <domain name> # Per Line 127:Uncomment myorigin = $mydomain # Per Line 141:Uncomment inet_interfaces = all # Per Line 189:Uncomment mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain # Per Line 232:Uncomment local_recipient_maps = unix:passwd.byname $alias_maps # Per Line 277:Uncomment mynetworks_style = subnet # Per Line 294:Own network addition mynetworks = 127.0.0.0/8, 192.168.11.0/24 # Per Line 416:Uncomment alias_maps = hash:/etc/aliases # Per Line 427:Uncomment alias_database = hash:/etc/aliases # Per Line 449:Uncomment home_mailbox = Maildir/ # Per Line 585:Make it a comment and add below it #smtpd_banner = $myhostname ESMTP $mail_name (Debian/GNU) smtpd_banner = $myhostname ESMTP # Per Line 659:add sendmail_path = /usr/sbin/postfix # Per Line 664:add newaliases_path = /usr/bin/newaliases # Per Line 669:add mailq_path = /usr/bin/mailq # Per Line 675:add setgid_group = postdrop # Per Line 679:Comment #html_directory = # Per Line 683:Comment #manpage_directory = # Per Line 688:Comment #sample_directory = # Per Line 692:Comment #readme_directory = # Add to last line # SMTP VRFY command is disabled disable_vrfy_command = yes # Requests a HELO command from the client smtpd_helo_required = yes # Limit sent/received mail size to 10M message_size_limit = 10485760 # Limit mailbox size to 1G mailbox_size_limit = 1073741824 # SMTP-Auth Settings smtpd_sasl_type = dovecot smtpd_sasl_path = private/auth smtpd_sasl_auth_enable = yes smtpd_sasl_security_options = noanonymous smtpd_sasl_local_domain = $myhostname smtpd_recipient_restrictions = permit_mynetworks, permit_auth_destination, permit_sasl_authenticated, reject |
③Edit configuration file (master.cf)
|
1 |
# vi /etc/postfix/master.cf |
Editorial content
|
1 2 3 4 5 6 7 8 9 10 |
smtp inet n - y - - smtpd #smtp inet n - y - 1 postscreen #smtpd pass - - y - - smtpd #dnsblog unix - - y - 0 dnsblog #tlsproxy unix - - y - 0 tlsproxy submission inet n - y - - smtpd # -o syslog_name=postfix/submission # -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes # -o smtpd_tls_auth_only=yes |
Reflect settings, reboot
|
1 2 |
# newaliases # systemctl restart postfix |
2.2 Dovecot : Installation Configuration
①Install Dovecot
Install Dovecot and build a POP/IMAP server, using 110/TCP for POP and 143/TCP for IMAP.
|
1 |
# apt -y install dovecot-core dovecot-pop3d dovecot-imapd |
②Configure Dovecot to provide SASL functionality for Postfix
|
1 2 3 |
# vi /etc/dovecot/dovecot.conf Line 30:Uncomment listen = *, :: |
|
1 2 3 4 5 |
# vi /etc/dovecot/conf.d/10-auth.conf Line 10:Uncomment and change (also allow plain text authentication) disable_plaintext_auth = no Line 100:add auth_mechanisms = plain login |
|
1 2 3 |
# vi /etc/dovecot/conf.d/10-mail.conf Line 30:Change to Maildir format mail_location = maildir:~/Maildir |
|
1 2 3 4 5 6 7 8 |
# vi /etc/dovecot/conf.d/10-master.conf Line 107-109:Uncommented and added # Postfix smtp-authi unix_listener /var/spool/postfix/private/auth { mode = 0666 user = postfix group = postfix } |
③Reflect settings, reboot
|
1 |
# systemctl restart dovecot |
2.3 Email User Account Registration
Register a user account for e-mail.
This setting is for when a user account on the OS is also used for e-mail.
If you want to use mail with a user account on the OS, no additional configuration is required, just register the OS user
①Mail client installed
|
1 |
# apt -y install mailutils |
②Mailboxes are set to refer to Maildir
|
1 |
# echo 'export MAIL=$HOME/Maildir/' >> /etc/profile.d/mail.sh |
2.4 Opening Ports
|
1 2 3 4 |
# ufw allow pop3 # ufw allow imap # ufw allow smtp # ufw reload |
2.5 operation check ①
①Send test mail to yourself [mail (user name)@(host name)].
user name : huong
|
1 2 3 4 5 6 7 8 |
# su - huong $ mail huong@localhost # Cc Cc: # Subject: Test Mail # This is the first mail. |
Ctrl + D key to exit the main text
Check incoming mail
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
$ mail "/home/huong/Maildir/": 1 message 1 new >N 1 huong Sat Jun 17 07:56 13/429 Test Mail ? 1 Return-Path: <huong@Lepard> X-Original-To: huong@localhost Delivered-To: huong@localhost Received: by mail.korodes.com (Postfix, from userid 1000) id 45E5623F817; Sat, 17 Jun 2023 16:56:40 +0900 (JST) To: <huong@localhost> Subject: Test Mail User-Agent: mail (GNU Mailutils 3.15) Date: Sat, 17 Jun 2023 16:56:40 +0900 Message-Id: <20230617075640.45E5623F817@mail.korodes.com> From: huong <huong@Lepard> This is the first mail. |
2.6 operation check ②
Set up and confirm your account in Mozilla Thunderbird
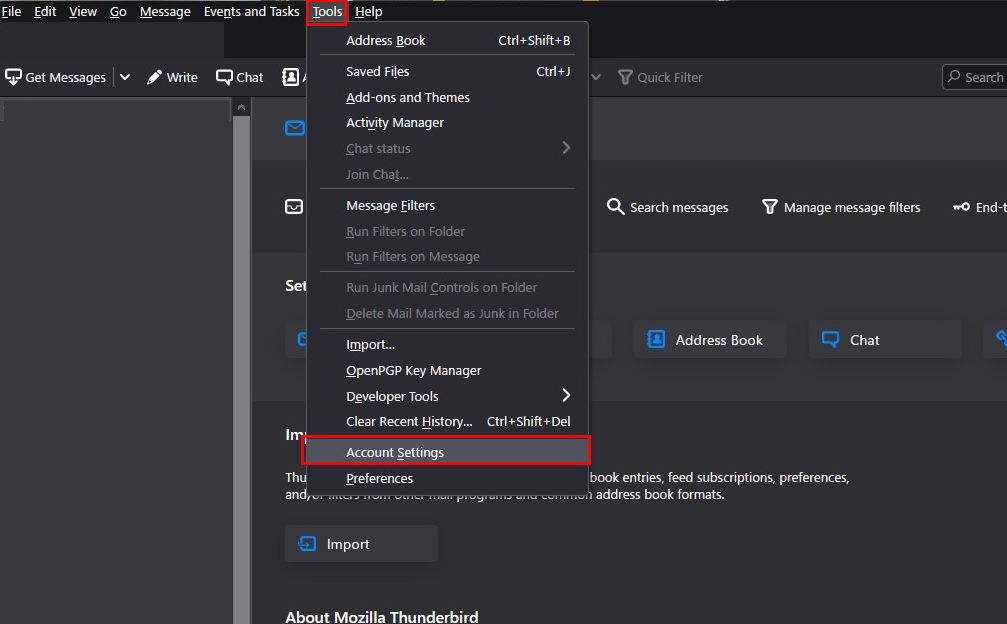
①Start Thunderbird, and click "Tools", "Account Settings".
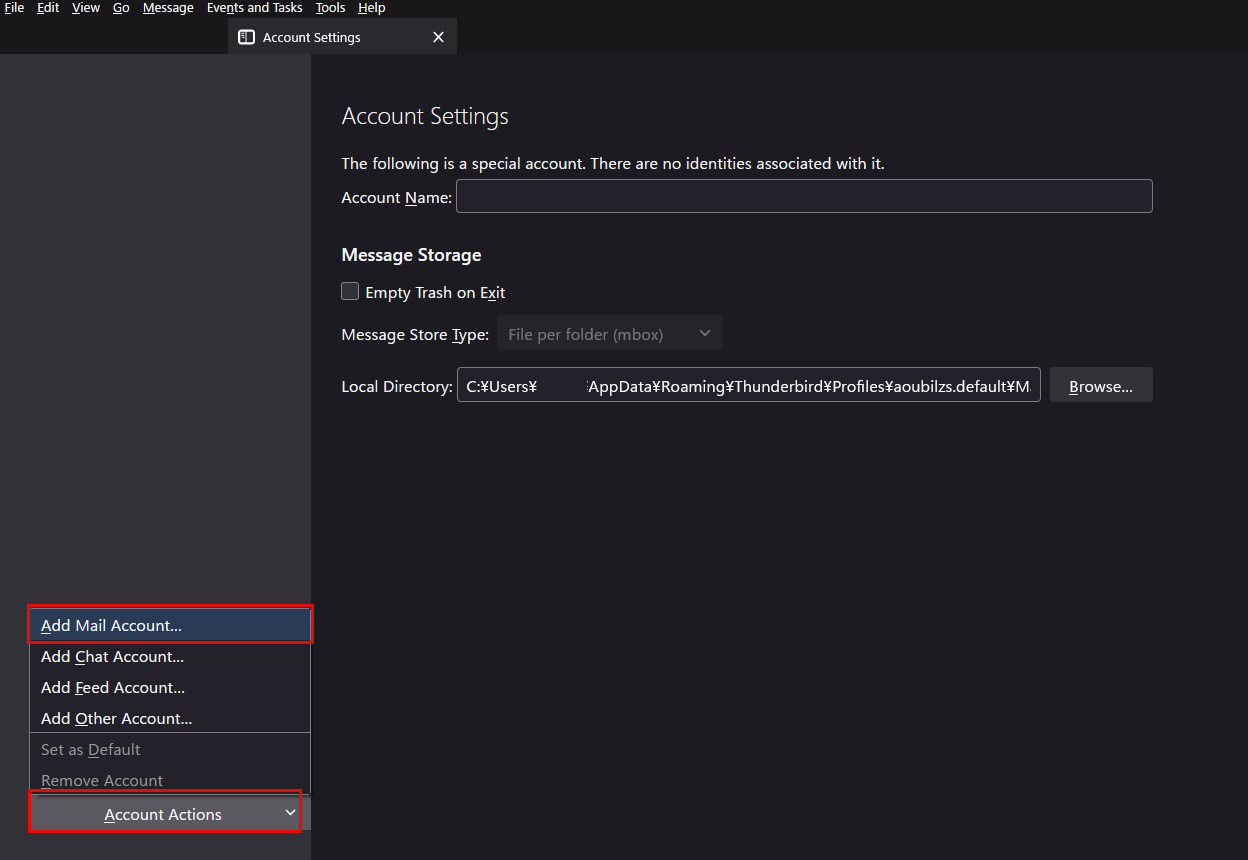
②「Account Actions」「Add Mail Account」
③Your full name" is an optional name
Email addtess" is "huong@korodes.com" added earlier
Password" is the password for user huong
Click on "Configure manually"
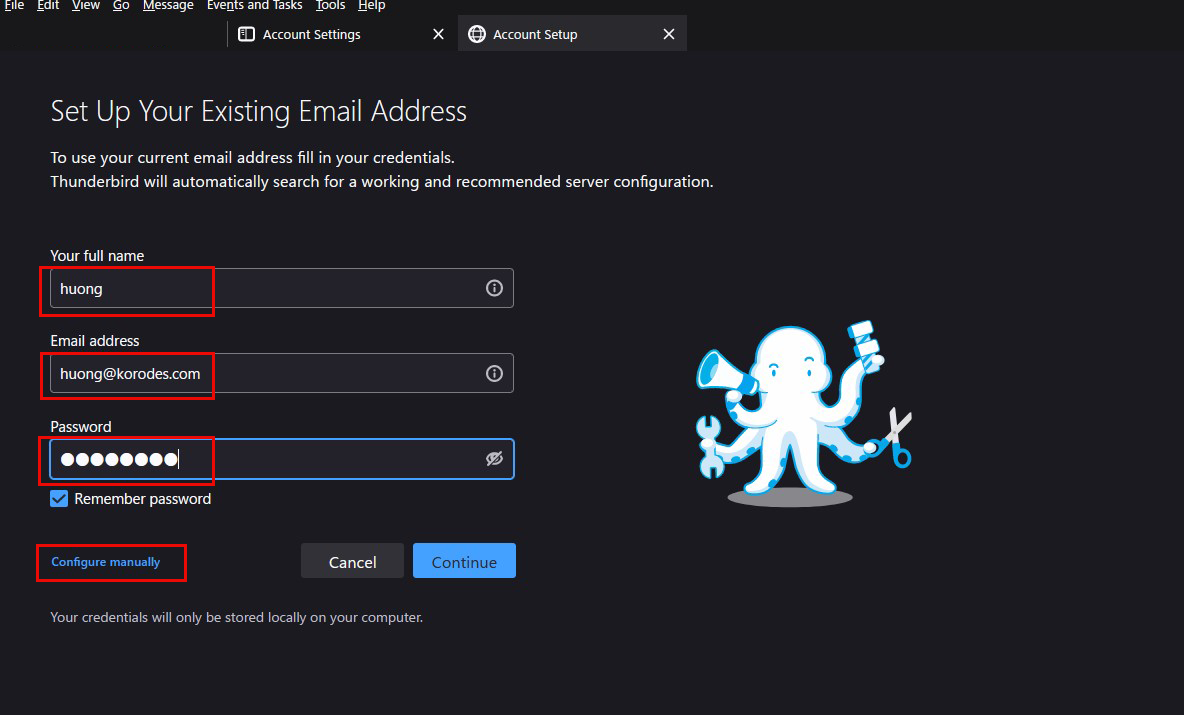
④Set "INCOMMING SERVER" and "OUTGOING SERVER" as shown below and click "Re-test".
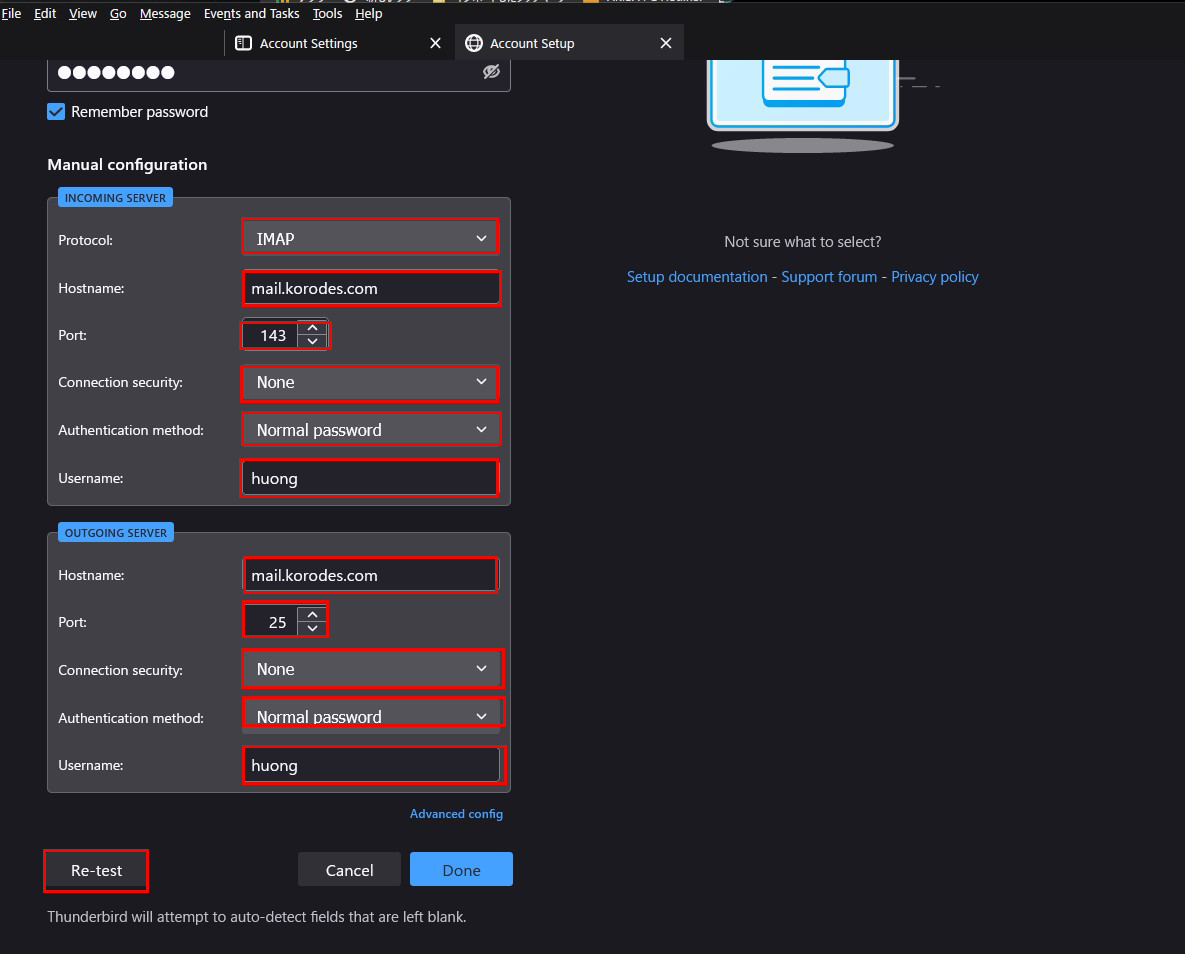
⑤The "Server Found" message appears.(The following settings were found by probinfg the given server)
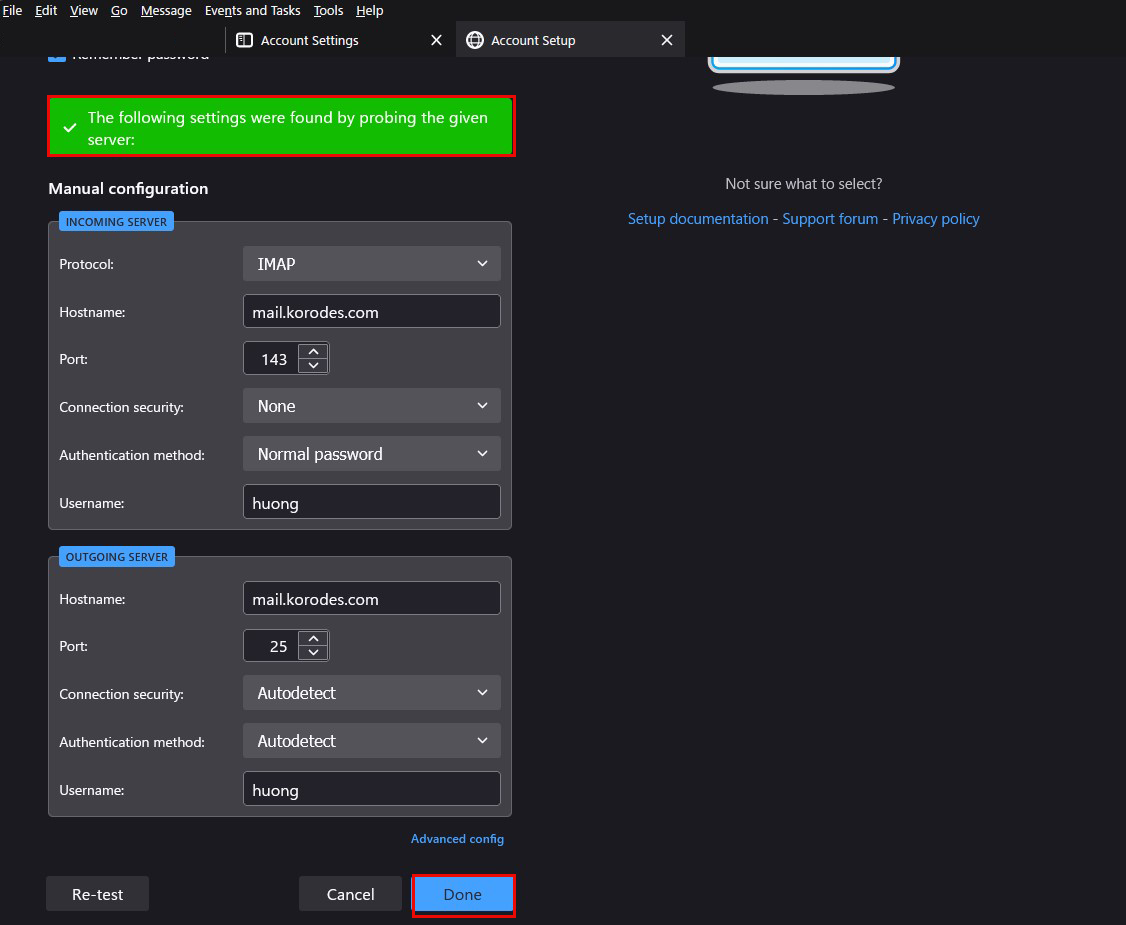
After clicking "Done," the following "Warning" appears, but there is no problem, so click "Confirm.
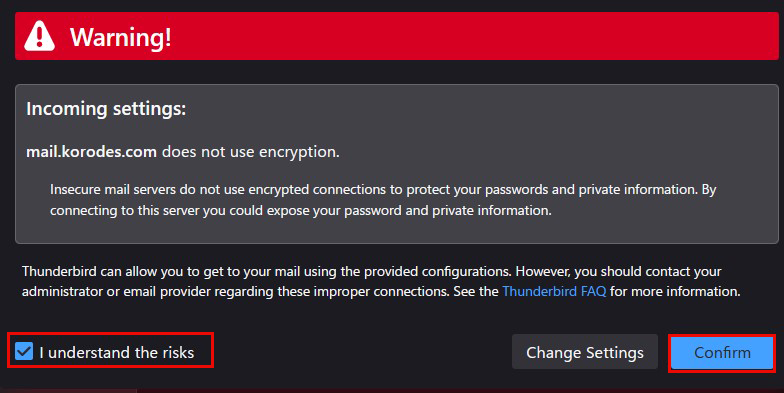
⑥Click "Finish" when "Account syccessfuly created" is displayed.
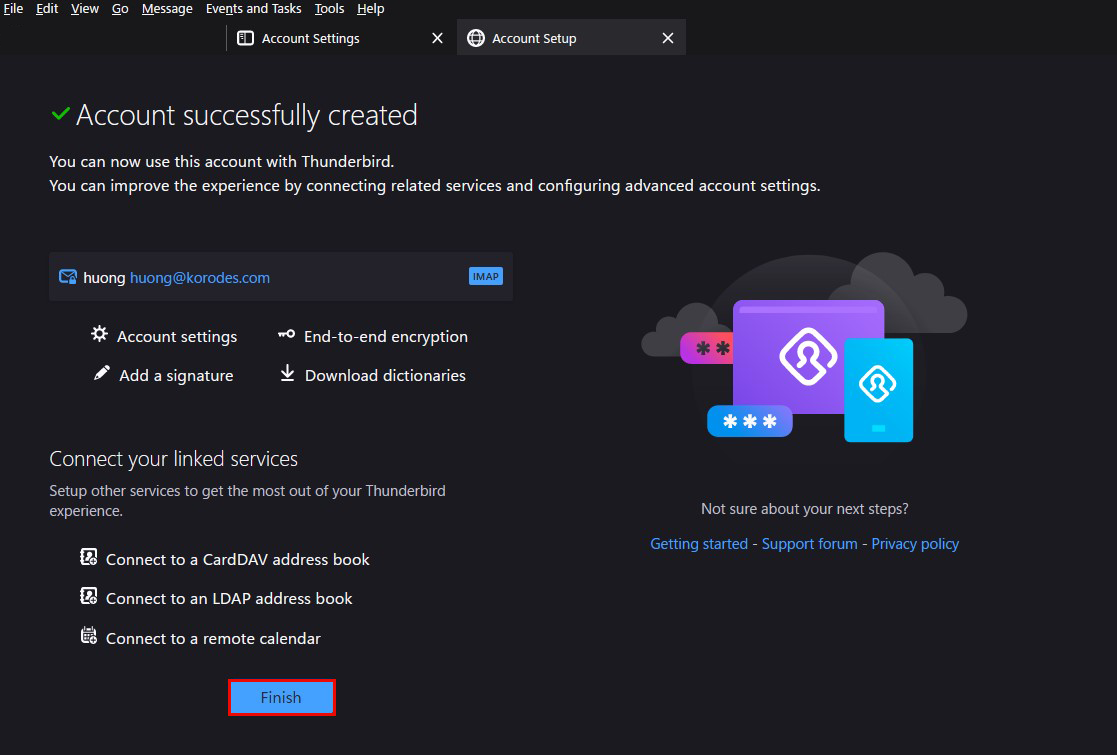
3 Applied ClamAV to mail server Postfix
Set up Postfix and Clamav to work together to scan incoming and outgoing mail in real time.
①Install Amavisd and Clamav Daemon and start Clamav Daemon
|
1 |
# apt -y install clamav-daemon amavisd-new |
If the server is not using a fully qualified domain name (FQDN) as the hostname, Amavis may fail to start. Also, since the OS hostname may change, set a valid hostname directly in the Amavis configuration file
|
1 2 3 4 5 6 7 8 9 10 |
# vi /etc/amavis/conf.d/05-node_id use strict; # $myhostname is used by amavisd-new for node identification, and it is # important to get it right (e.g. for ESMTP EHLO, loop detection, and so on) . chomp($myhostname = `hostname --fqdn`); # To manually set $myhostname, edit the following line with the correct Full y # Qualified Domain Name (FQDN) and remove the # at the beginning of the line . # $myhostname = "mail.<domain name>"; 1; # ensure a defined return |
②Virus Scan Enable
|
1 2 3 4 5 |
# vi /etc/amavis/conf.d/15-content_filter_mode # Line 14 : Uncomment and enable virus scan @bypass_virus_checks_maps = ( \%bypass_virus_checks, \@bypass_virus_checks_acl, \$bypass_virus_checks_re); |
③Register your own domain name
|
1 |
# echo '<yourDomain>' > /etc/mailname |
④Edit configuration file (Main.cf)
|
1 2 3 |
# vi /etc/postfix/main.cf Add to last line content_filter=smtp-amavis:[127.0.0.1]:10024 |
⑤Edit configuration file (master.cf)
|
1 |
# vi /etc/postfix/master.cf |
Editorial content
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# Add all the following lines to the last line smtp-amavis unix - - n - 2 smtp -o smtp_data_done_timeout=1200 -o smtp_send_xforward_command=yes -o disable_dns_lookups=yes 127.0.0.1:10025 inet n - n - - smtpd -o content_filter= -o local_recipient_maps= -o relay_recipient_maps= -o smtpd_restriction_classes= -o smtpd_client_restrictions= -o smtpd_helo_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o mynetworks=127.0.0.0/8 -o strict_rfc821_envelopes=yes -o smtpd_error_sleep_time=0 -o smtpd_soft_error_limit=1001 -o smtpd_hard_error_limit=1000 |
⑥Settings reflect
|
1 2 3 |
# usermod -G clamav amavis # usermod -G amavis clamav # systemctl restart clamav-daemon amavis postfix |
When you send an e-mail to yourself on Thuderbird, etc., it is successful if you see the following message in the header of the incoming e-mail.
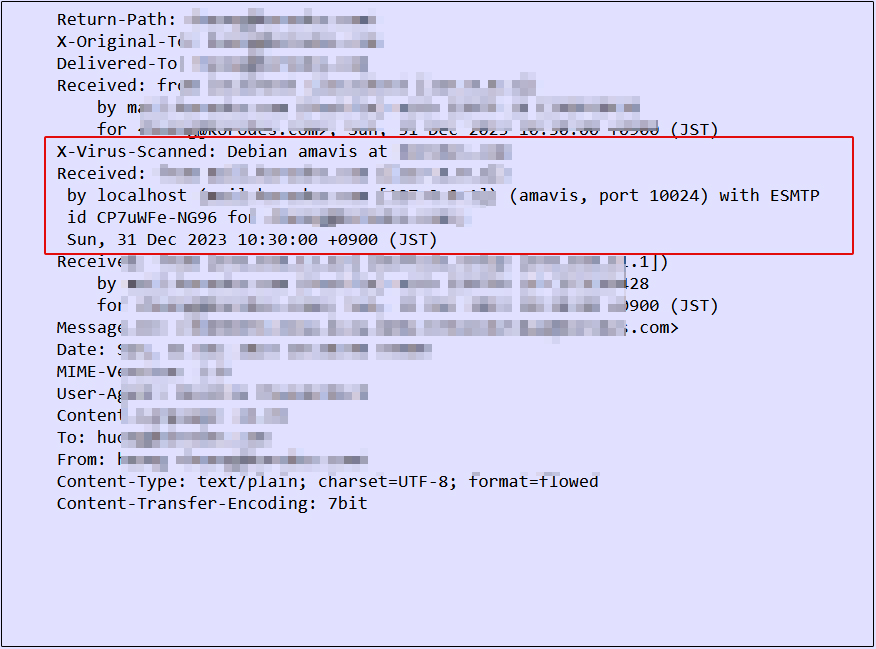
4 Apply spam checks to the mail server
4.1 Spam checking using spamassassin and procmail
①spamassassin and procmail installation
|
1 |
# apt install procmail spamassassin |
➁Configure procmail
If you want to apply the settings to all users
Create /etc/procmailrc
To configure for each individual, create a ~/.procmailrc in each user's home directory.
Create /etc/procmailrc this time
|
1 |
# vi /etc/procmailrc |
Contents of procmailrc
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
SHELL=/bin/bash PATH=/usr/bin:/bin:/usr/local/bin DROPPRIVS=yes MAILDIR=$HOME/Maildir DEFAULT=$MAILDIR/ SPAM=$MAILDIR/.Spam/ LOGFILE=$HOME/.procmail.log # Log output destination VERBOSE=ON # Detailed log output # If there is no "X-Spam-***" in the mail header, spamassassassin will be started. :0fw *!^X-Spam.* |spamassassin # If there is an "X-Spam-Status: Yes" in the mail header, the mail is stored in the ". .Spam" directory. :0 * ^X-Spam-Status: Yes $SPAM |
➂Create a .Spam directory in each user's ~/Maildir directory
|
1 2 |
# su - user $ mkdir Maildir/.Spam |
④Edit postfix configuration file
|
1 2 3 4 |
# vi /etc/postfix/main.cf Per Line 479 : Uncomment mailbox_command = /usr/bin/procmail -a "$EXTENSION" |
⑤Restart postfix and spamassassin
|
1 2 |
# systemctl restart postfix spamd # systemctl enable spamassassin-maintenance.timer |
⑥Confirmed by Thudrtbird
If you send an e-mail to yourself and the header displays the following, it is normal.
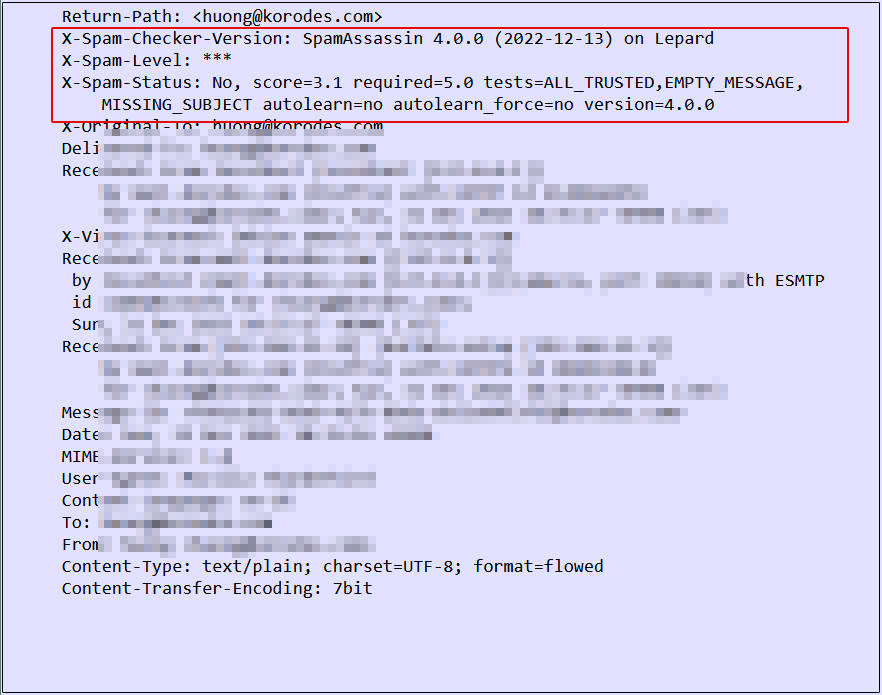
4.2 Spam Email Learning
SpamAssassin's email learning functionality improves the accuracy of its judgments
①Learns all contents of ".Spam" directory as spam mail
|
1 2 |
# /usr/bin/sa-learn --spam /home/*/Maildir/.Spam/cur Learned tokens from 0 message(s) (0 message(s) examined) |
➁Learning of non-spam mail (normal mail)
|
1 2 |
# /usr/bin/sa-learn --ham /home/*/Maildir/cur Learned tokens from 7 message(s) (7 message(s) examined) |
➂Creating scripts for automatic learning
|
1 |
# vi /opt/script/spam-learns.sh |
|
1 2 3 4 5 6 7 8 |
#! /bin/sh # Spam Email Learning /usr/bin/sa-learn --spam /home/*/Maildir/.Spam/cur # Learning normal mail /usr/bin/sa-learn --ham /home/*/Maildir/cur # If you want to force the deletion of the contents of the spam mail storage directory, add the following statement /bin/rm -f /home/*/Maildir/.Spam/cur |
|
1 |
# chmod 750 /opt/script/spam-learns.sh |
④SpamAssassin automatically starts at system startup
|
1 |
# systemctl enable spamd |

