Contents
Web server Apache2 installation
Allow http:80 and https:443 ports in UFW before installation
|
1 2 3 |
# ufw allow http # ufw allow https # ufw reload |
1 Apache2 Installation and Configuration
Apache2 Install
|
1 |
# apt -y install apache2 |
2.Basic Apache2 Configuration
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
# vi /etc/apache2/conf-enabled/security.conf # Line 25:change ServerTokens Prod # vi /etc/apache2/mods-enabled/dir.conf # Line 2:Check file names accessible by directory name only DirectoryIndex index.html index.cgi index.pl index.php index.xhtml i ndex.htm # vi /etc/apache2/apache2.conf # Line 70:Server name added ServerName <own domain name> # Line 172:change AllowOverride ALL # vi /etc/apache2/sites-available/000-default.conf # Line 11:Administrator address change ServerAdmin <your mailaddress> Restart Apache # systemctl restart apache2 |
3. Apache2; Using Perl Scripts
Enable CGI to make Perl scripts available
①Install Perl
|
1 |
# apt -y install perl |
②Enable CGI module and restart
|
1 2 |
# a2enmod cgid # systemctl restart apache2 |
③Check the validity of CGI modules
Create test scripts
|
1 2 3 4 |
# vi /usr/lib/cgi-bin/test_script #!/usr/bin/perl print "Content-type: text/html\n\n" ; print "Hello CGI\n" |
Authorize script files
|
1 |
# chmod 705 /usr/lib/cgi-bin/test_script |
operation check
|
1 2 3 4 5 6 |
# curl http://localhost/cgi-bin/test_script If you get a "curl: command not found" message # apt install curl again # curl http://localhost/cgi-bin/test_script Hello CGI |
4 Apache2 : Using PHP Scripts
①Install PHP
|
1 |
# apt -y install php php-cgi libapache2-mod-php php-common php-pear php-mbstring |
②Apache2 Configuration
|
1 2 3 4 |
# a2enconf php7.4-cgi Enabling conf php7.4-cgi. To activate the new configuration, you need to run: systemctl reload apache2 |
|
1 2 3 4 5 6 |
# vi /etc/php/7.4/apache2/php.ini # Line 846 change #upload_max_filesize = 2M upload_max_filesize = 200M # Line 962:Uncomment and set time zone date.timezone = “Asia/Tokyo” |
③Create a PHP test page and check its operation
|
1 2 |
# vi /var/www/html/index.php <?php phpinfo(); ?> |
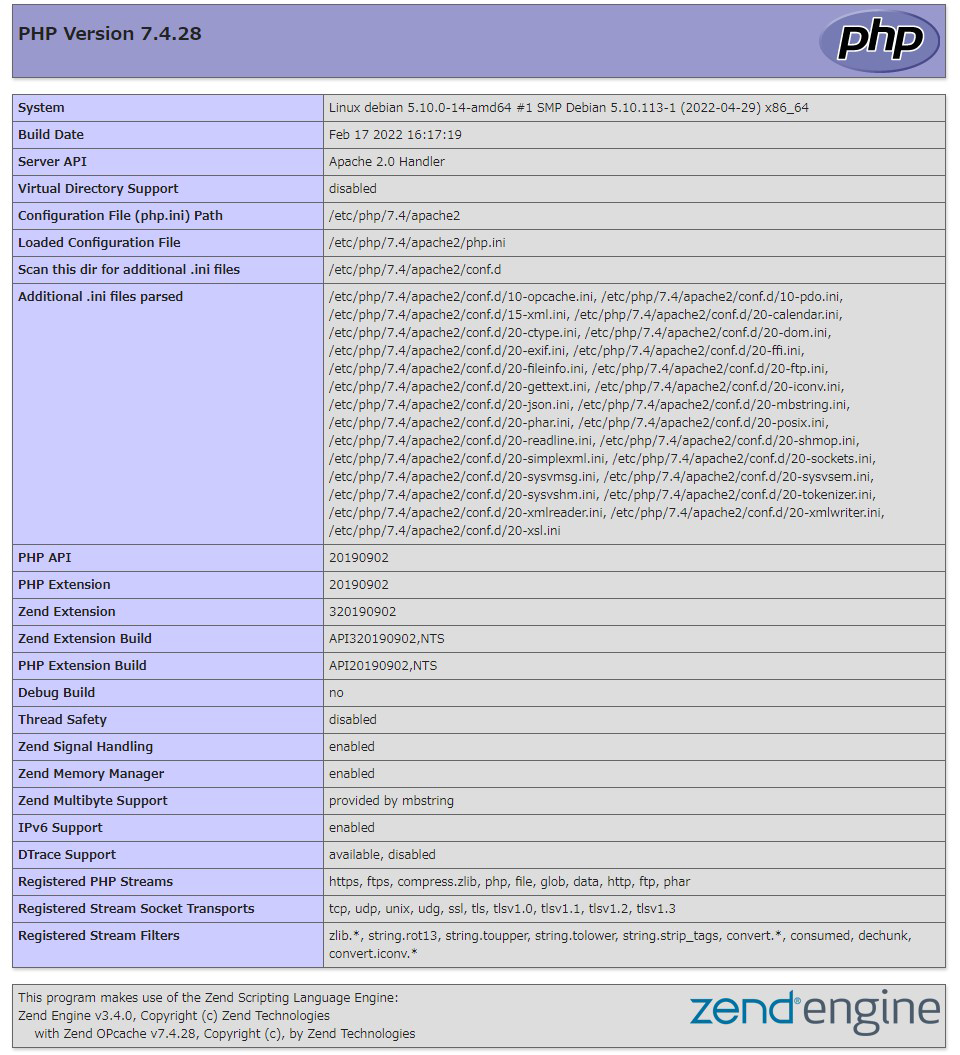
Access http://<server IP address>/index.php with a browser and if the following screen appears, OK
5. Virtual Host Settings
Copy the default configuration file (file name is arbitrary, in this case vhost-yourdomain.conf as an example) and configure the virtual host
|
1 2 |
# cd /etc/apache2/sites-available/ # cp 000-default.conf vhost-yourdomain.conf |
Edit configuration file
|
1 2 3 4 5 6 7 8 9 10 11 |
# vi vhost-yourdomain.conf <VirtualHost *:80> ~omission~ ServerName <FQDN> ServerAdmin <Administrator's email address> DocumentRoot /var/www/html/<FQDN>/ ~omission~ ErrorLog ${APACHE_LOG_DIR}/<FQDN>.error.log CustomLog ${APACHE_LOG_DIR}/<FQDN>.access.log combined ~omission~ </VirtualHost> |
Symbolic link to the configuration file to disable the default configuration file
|
1 2 3 4 5 6 |
# cd /etc/apache2/sites-available/ # a2ensite vhost-yourdomain.conf Default Disable Apache Restart # a2dissite 000-default.conf # systemctl restart apache2 |
Edit hosts file
|
1 2 |
# vi /etc/hosts 127.0.0.1 <FQDN> |
directory creation
|
1 |
# mkdir /var/www/html/<FQDN> |
Create test pages and check operation
|
1 2 3 4 5 6 7 8 |
# vi /var/www/html/<FQDN>/index.html <html> <body> <div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;"> Virtual Host Test Page </div> </body> </html> |
Access "http://<own domain name>/index.html" with a browser to check
6.Digest authentication with Apache2
Since Basic Authentication, a well-known authentication authorization method for http, sends authentication information in plain text, there is a risk of ID and password leakage if the packet is intercepted.
On the other hand, Digest Authentication encrypts and transmits authentication information, so there is almost no risk of information leakage.
6.1 Create password file for Digest authentication
Specify an authenticated area called realm. This realm allows the same directory to be accessed as authenticated.
As an example, we will create a user named "secretuser" with "DigestAuth" as the realm. Execute the following command and enter the password for "secretuser" when prompted.
|
1 |
# /usr/bin/htdigest -c /etc/apache2/.digestauth "DigestAuth" secretuser |
Confirmation
|
1 2 |
# cat /etc/apache2/.digestauth secretuser:DigestAuth:64939177c7b7c6eac3687925b27e771d |
As above, secretuser and encrypted password are created
6.2 Edit Apache configuration file
Specify the directory to which Digest authentication will be applied. (In this case, specify the secret directory.)
|
1 |
# vi /etc/apache2/apache2.conf |
Add the following at the end
|
1 2 3 4 5 6 7 |
<Directory /var/www/html/[FQDN]/secret> AuthType Digest AuthName "DigestAuth" AuthDigestDomain /secret/ AuthUserFile /etc/apache2/.digestauth Require valid-user </Directory> |
Create a directory for Digest authentication
|
1 |
# mkdir /var/www/html/[FQDN]/secret |
Enable Digest authentication and reboot
|
1 2 |
# a2enmod auth_digest # systemctl restart apache2 |
When accessing http://[FQDN]/secret with a browser, a screen appears asking for "user name" and "password".