Contents
Snort3 + SnortSnarfインストール
不正アクセス検知システムにネットワーク型IDSのSnortを導入する。
また、Snortが抽出した不正アクセスログをWebブラウザ上で確認できるようにするためにSnortSnarfも導入する。
RockyLinux8はSnortリポジトリがありませんので、ソースコードからSnort3をビルド、コンパイルしてインストールします
事前準備
①ビルドとインストールに必要なビルドツールと依存関係のあるライブラリーをインストール。
EPELをインストールし、Powertoolsリポジトリを有効にします。
|
1 2 |
# dnf install epel-release # dnf config-manager --set-enabled powertools |
|
1 |
# dnf install bison flex libtool nghttp2 libnghttp2-devel libpcap-devel pcre-devel openssl-devel libdnet-devel libtirpc-devel git gcc-c++ libunwind-devel cmake hwloc-devel luajit-devel xz-devel libnfnetlink-devel libmnl-devel libnetfilter_queue-devel uuid-devel libsafec-devel -y |
②SNORT3のインストール作業ディレクトリー作成
|
1 |
# mkdir snort_src && cd snort_src |
③DAQのダウンロード、インストール
|
1 2 3 4 5 6 |
# git clone https://github.com/snort3/libdaq.git # cd libdaq # ./bootstrap # ./configure # make # make install |
④メモリ使用量の増加時の速度が向上のためgperftoolsインストール
|
1 2 3 4 5 6 7 |
# cd ~/snort_src # wget https://github.com/gperftools/gperftools/releases/download/gperftools-2.9.1/gperftools-2.9.1.tar.gz # tar xzf gperftools-2.9.1.tar.gz # cd gperftools-2.9.1/ # ./configure # make # make install |
Snort3 ダウンロード、インストール
①Snort3をダウンロードしてインストール
|
1 2 3 4 5 6 7 8 |
# cd ~/snort_src # wget https://github.com/snort3/snort3/archive/refs/tags/3.1.31.0.tar.gz # tar xzf 3.1.31.0.tar.gz # cd snort3-3.1.31.0 # ./configure_cmake.sh --prefix=/usr/local --enable-tcmalloc # cd build # make # make install |
②共有ライブラリを更新
|
1 2 3 |
# ln -s /usr/local/lib/libtcmalloc.so.4 /lib/ # ln -s /usr/local/lib/libdaq.so.3 /lib/ # ldconfig |
Snort3を構成する
①ネットワークインターフェイスカードを構成
|
1 2 3 4 5 6 |
# ip link set dev ens160 promisc on # ip add sh ens160 2: ens160: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 00:0c:29:3f:48:ad brd ff:ff:ff:ff:ff:ff inet 192.168.11.83/24 brd 192.168.11.255 scope global noprefixroute ens160 valid_lft forever preferred_lft forever |
Snortが1518バイトを超える大きなパケットを切り捨てないよう、インターフェイスオフロードを無効にする
現状の確認
|
1 2 3 |
# ethtool -k ens160 | grep receive-offload generic-receive-offload: on large-receive-offload: on |
GRO,LROがonになっているのてこれを無効にする
|
1 |
# ethtool -K ens160 gro off lro off |
システムの再起動後も変更が反映するように、systemdサービスを作成して有効にする
|
1 |
# vi /etc/systemd/system/snort3-promisc.service |
snort3-promisc.serviceの内容
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
[Unit] Description=Set Snort 3 NIC in promiscuous mode and Disable GRO, LRO on boot After=network.target [Service] Type=oneshot ExecStart=/usr/sbin/ip link set dev ens160 promisc on ExecStart=/usr/sbin/ethtool -K ens160 gro off lro off TimeoutStartSec=0 RemainAfterExit=yes [Install] WantedBy=default.target |
|
1 2 |
# systemctl daemon-reload # systemctl enable --now snort3-promisc.service |
②ルールセットを構成
今回はコミュニティールールをセットします
ルールディレクトリを作成
|
1 |
# mkdir /usr/local/etc/rules |
③Snort3コミュニティルールをダウンロードしてルールディレクトリに保存
|
1 2 3 4 5 6 7 |
# wget -qO- https://www.snort.org/downloads/community/snort3-community-rules.tar.gz | tar xz -C /usr/local/etc/rules/ # ls -1 /usr/local/etc/rules/snort3-community-rules/ AUTHORS LICENSE sid-msg.map snort3-community.rules VRT-License.txt |
④構成ファイルを編集
|
1 2 3 4 5 |
# vi /usr/local/etc/snort/snort.lua # 24行目 : 自ネットワークに変更 HOME_NET = '192.168.11.0/24' # 28行目 : 変更 EXTERNAL_NET = '!$HOME_NET' |
⑤ルールへのパスを更新
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# vi /usr/local/etc/snort/snort.lua # 193行目あたり : 追記 ips = { -- use this to enable decoder and inspector alerts --enable_builtin_rules = true,-- use include for rules files; be sure to set your path -- note that rules files can include other rules files -- (see also related path vars at the top of snort_defaults.lua) variables = default_variables, rules = [[ include $RULE_PATH/snort3-community-rules/snort3-community.rules ]] } |
⑥SnortOpenAppIDのインストール(バージョンは最新のものに書き換えてください)
|
1 2 3 |
# wget https://www.snort.org/downloads/openappid/23020 -O OpenAppId-23020.tgz # tar -xzvf OpenAppId-23020.tgz # cp -R odp /usr/local/lib/ |
|
1 2 3 4 5 6 7 8 9 10 |
# vi /usr/local/etc/snort/snort.lua # 101行目あたり : 追記 appid = { -- appid requires this to use appids in rules --app_detector_dir = 'directory to load appid detectors from' app_detector_dir = '/usr/local/lib', log_stats = true, } |
⑦ログディレクトリー作成
|
1 |
# mkdir /var/log/snort |
⑧構成のチェック
|
1 |
# snort -c /usr/local/etc/snort/snort.lua --daq-dir /usr/local/lib/daq |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 |
-------------------------------------------------- o")~ Snort++ 3.1.28.0 -------------------------------------------------- Loading /usr/local/etc/snort/snort.lua: Loading snort_defaults.lua: Finished snort_defaults.lua: Loading file_magic.lua: Finished file_magic.lua: ssh hosts host_cache pop so_proxy stream_tcp mms smtp gtp_inspect packets dce_http_proxy stream_icmp normalizer ips network binder wizard appid file_id stream_udp http2_inspect http_inspect ftp_data search_engine ftp_server port_scan dce_http_server dce_smb dce_tcp netflow iec104 cip telnet ssl sip rpc_decode modbus host_tracker stream_user stream_ip process back_orifice classifications dnp3 active trace ftp_client decode alerts stream daq references arp_spoof output dns dce_udp imap file_policy s7commplus stream_file Finished /usr/local/etc/snort/snort.lua: Loading ips.rules: Loading ../rules/snort3-community-rules/snort3-community.rules: Finished ../rules/snort3-community-rules/snort3-community.rules: Finished ips.rules: -------------------------------------------------- ips policies rule stats id loaded shared enabled file 0 4024 0 4024 /usr/local/etc/snort/snort.lua -------------------------------------------------- rule counts total rules loaded: 4024 text rules: 4024 option chains: 4024 chain headers: 324 flowbits: 48 flowbits not checked: 23 -------------------------------------------------- port rule counts tcp udp icmp ip any 473 58 147 22 src 177 17 0 0 dst 787 154 0 0 both 6 11 0 0 total 1443 240 147 22 -------------------------------------------------- service rule counts to-srv to-cli dcerpc: 7 4 dhcp: 2 2 dns: 28 7 ftp: 90 4 ftp-data: 1 97 http: 2077 256 http2: 2077 256 imap: 35 118 irc: 5 2 kerberos: 7 0 ldap: 0 1 mysql: 3 0 netbios-dgm: 1 1 netbios-ns: 4 3 netbios-ssn: 73 17 nntp: 2 0 pop3: 23 118 rdp: 5 0 sip: 5 5 smtp: 130 2 snmp: 18 7 ssdp: 3 0 ssl: 18 40 sunrpc: 68 4 telnet: 12 6 tftp: 1 0 wins: 1 0 total: 4696 950 -------------------------------------------------- fast pattern groups src: 59 dst: 158 any: 4 to_server: 47 to_client: 34 -------------------------------------------------- search engine instances: 302 patterns: 7518 pattern chars: 121768 num states: 82296 num match states: 7149 memory scale: MB total memory: 2.58334 pattern memory: 0.402628 match list memory: 0.914368 transition memory: 1.22948 fast pattern only: 4963 -------------------------------------------------- pcap DAQ configured to passive. Snort successfully validated the configuration (with 0 warnings). o")~ Snort exiting |
⑨ローカルルールを作成
|
1 2 3 |
# vi /usr/local/etc/rules/local.rules 以下を記入 alert icmp any any -> $HOME_NET any (msg:"ICMP connection test"; sid:1000001; rev:1;) |
テスト実行
|
1 |
# snort -c /usr/local/etc/snort/snort.lua -R /usr/local/etc/rules/local.rules -i ens160 -A alert_fast -s 65535 -k none --daq-dir /usr/local/lib/daq |
同じネットワーク内の別のPCからサーバーにpingすると、コンソール画面に以下のように表示される
|
1 2 3 4 5 6 7 8 9 |
++ [0] ens160 06/20-17:58:56.092420 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.20 -> 192.168.11.83 06/20-17:58:56.092462 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.83 -> 192.168.11.20 06/20-17:58:57.104416 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.20 -> 192.168.11.83 06/20-17:58:57.104442 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.83 -> 192.168.11.20 06/20-17:58:58.109416 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.20 -> 192.168.11.83 06/20-17:58:58.109443 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.83 -> 192.168.11.20 06/20-17:58:59.115335 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.20 -> 192.168.11.83 06/20-17:58:59.115376 [**] [1:1000001:1] "ICMP connection test" [**] [Priority: 0] [AppID: ICMP] {ICMP} 192.168.11.83 -> 192.168.11.20 |
⑩アラートをログに書き込む
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
# vi /usr/local/etc/snort/snort.lua # 255行目 : コメント解除して追記 -- event logging -- you can enable with defaults from the command line with -A -- uncomment below to set non-default configs --alert_csv = { } alert_fast = { file = true, packet = false, limit = 10, } --alert_full = { } --alert_sfsocket = { } --alert_syslog = { } --unified2 = { } |
ログディレクトリーにalert_fast.txt ファイルが作成される
構成をチェック
|
1 |
# snort -c /usr/local/etc/snort/snort.lua -R /usr/local/etc/rules/local.rules -i ens160 -s 65535 -k none -l /var/log/snort/ --daq-dir /usr/local/lib/daq |
再度、同じネットワーク内の別のPCからサーバーにpingすると今度はコンソール画面には何も表示されないが
ログディレクトリを確認すると、 alert_fast.txt ファイルが作成されました
alert_fast.txt ファイルを確認するには
|
1 |
# tail -f /var/log/snort/alert_fast.txt |
⑪ローカルルールをsnort.luaに含める
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
# vi /usr/local/etc/snort/snort.lua # 197行目 : 追記 ips = { -- use this to enable decoder and inspector alerts --enable_builtin_rules = true,-- use include for rules files; be sure to set your path -- note that rules files can include other rules files -- (see also related path vars at the top of snort_defaults.lua) variables = default_variables, rules = [[ include $RULE_PATH/snort3-community-rules/snort3-community.rules include $RULE_PATH/local.rules ]] } |
バックグラウンドでSnortを実行
①Snortの非ログインシステムユーザーアカウントを作成
|
1 |
# useradd -r -s /usr/sbin/nologin -M -c SNORT_IDS snort |
②systemdサービスユニットを作成
|
1 |
# vi /etc/systemd/system/snort3.service |
snort3.serviceの内容
|
1 2 3 4 5 6 7 8 9 10 11 |
[Unit] Description=Snort Daemon After=syslog.target network.target [Service] Type=simple ExecStart=/usr/local/bin/snort -c /usr/local/etc/snort/snort.lua -s 65535 -k none -l /var/log/snort -D -i ens160 -m 0x1b -u snort -g snort --daq-dir /usr/local/lib/daq ExecStop=/bin/kill -9 $MAINPID [Install] WantedBy=multi-user.target |
再起動
|
1 |
# systemctl daemon-reload |
ログファイルの所有権と権限を設定
|
1 2 |
# chmod -R 5775 /var/log/snort # chown -R snort:snort /var/log/snort |
③Snortを起動し、システム起動時に実行できるようにする
|
1 2 |
# systemctl enable --now snort3 Created symlink /etc/systemd/system/multi-user.target.wants/snort3.service → /etc/systemd/system/snort3.service. |
|
1 2 3 4 5 6 7 8 9 10 |
# systemctl status snort3 ● snort3.service - Snort Daemon Loaded: loaded (/etc/systemd/system/snort3.service; enabled; vendor preset> Active: active (running) since Mon 2022-06-20 11:05:53 JST; 26s ago Main PID: 3220 (snort) Tasks: 2 (limit: 4538) Memory: 234.6M CPU: 910ms CGroup: /system.slice/snort3.service mq3220 /usr/local/bin/snort -c /usr/local/etc/snort/snort.lua -s 6>Jun 20 11:05:53 ubuntu22 systemd[1]: Started Snort Daemon. |
ログローテーション設定ファイルを配置
①設定ファイル作成
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# vi /etc/logrotate.d/snort 下記を記述 /var/log/snort/alert_fast.txt /var/log/snort/*log { weekly # 毎週ローテート rotate 4 # ログを4世代残す create 0600 snort snort # ローテーション後、新規ログファイル作成 dateext # ローテーション後のファイル末尾に、日付を付ける missingok # ログファイルが無くてもエラーにしない compress # ローテーション後のファイルを圧縮(.gz) notifempty # ログファイルが空ならローテーションしない sharedscripts # 以下に記述された処理を1度だけ実行する宣言 postrotate # postrotate ~ endscript に処理を記述 /usr/bin/systemctl restart snort3 1>/dev/null || true endscript } |
➁テスト # -fオプションで強制実行する
|
1 |
# logrotate -f /etc/logrotate.d/snort |
ログファイル確認
|
1 2 3 |
# ls -l /var/log/snort alert_fast.txt-20240115.gz appid_stats.log-20240115.gz |
|
1 2 3 4 |
# cat /var/lib/logrotate/logrotate.status "/var/log/snort/appid_stats.log" 2024-1-15-14:50:18 "/var/log/snort/alert_fast.txt" 2024-1-15-14:50:18 "/var/log/snort/file.log" 2024-1-15-13:0:0 |
Snortsnarf インストール
①事前準備
PerlのTime-modulesをインストール
|
1 |
# dnf -y install perl-Time-modules |
Cpanインストール
|
1 |
# dnf install cpan |
|
1 2 |
# cpan Time::ParseDate # mkdir /usr/local/snortsnarf |
➁Snortsnarfダウンロード、インストール
|
1 2 3 4 |
# wget https://sourceforge.net/projects/snortsnarf/files/latest/download/SnortSnarf-1.0.tar.gz # tar xvfz SnortSnarf-1.0.tar.gz # cp -v SnortSnarf-1.0/snortsnarf.pl /usr/local/snortsnarf # cp -vrf SnortSnarf-1.0/include/ /usr/local/snortsnarf |
➂設定ファイル等編集
|
1 2 3 4 5 |
# vi /usr/local/snortsnarf/snortsnarf.pl 78行目 use lib qw(./include); を use lib qw(/usr/local/snortsnarf/include); に変更 |
|
1 2 3 |
# vi /usr/local/snortsnarf/include/SnortSnarf/HTMLMemStorage.pm 290行目 return @arr->[($first-1)..$end]; 「->」削除 return @arr[($first-1)..$end]; |
|
1 2 3 |
# vi /usr/local/snortsnarf/include/SnortSnarf/HTMLAnomMemStorage.pm 266行目 return @arr->[($first-1)..$end]; 「->」削除 return @arr[($first-1)..$end]; |
④解析結果出力ディレクトリ作成
|
1 2 |
# mkdir /var/www/html/snortsnarf # chown apache:apache /var/www/html/snortsnarf |
⑤解析結果へのアクセス制御
|
1 2 3 4 5 6 7 8 |
# vi /etc/httpd/conf/httpd.conf Apache 2.4の場合161行目当たりに追加 <Directory "/var/www/html/snortsnarf"> DirectoryIndex index.html Options +ExecCGI require ip 127.0.0.1 192.168.11.0/24 </Directory> |
⑥実行と確認
|
1 |
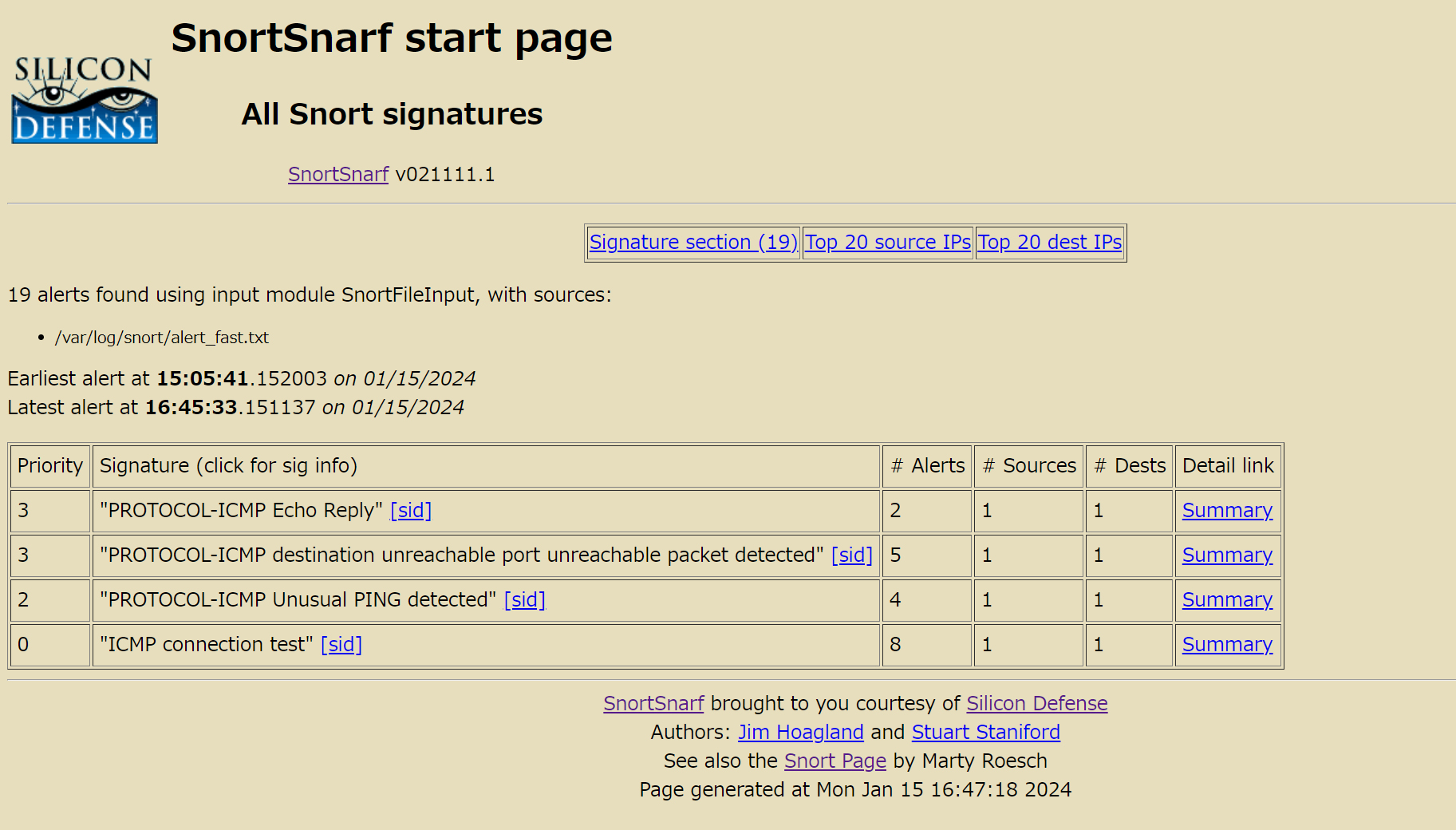
# /usr/local/snortsnarf/snortsnarf.pl /var/log/snort/alert_fast.txt -d /var/www/html/snortsnarf |
ブラウザにて、http://[server IP]/snortsnarf/にアクセスすると下記の画面になればOK