Clamav
1.Clamav Install
|
1 |
# dnf -y install clamav clamd clamav-update |
2.Clam AntiVirus Configuration File Edit
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# vi /etc/clamd.d/scan.conf ●Line 14 # Default: disabled LogFile /var/log/clamd.scan ← Uncomment ●Line 77 # Default: disabled PidFile /run/clamd.scan/clamd.pid ← Uncomment ●Line 103 : add #LocalSocket /run/clamd.scan/clamd.sock LocalSocket /var/run/clamd.scan/clamd.sock ●Line 233 # Run as another user (clamd must be started by root for this option to work) # Default: don't drop privileges #User clamscan ← Add # at the beginning of the line and comment it out (to make it work with root privileges) |
3.virus definition file update settings
|
1 2 3 4 5 6 7 8 9 |
# vi /etc/freshclam.conf ● Line 78 Insert a "#" at the beginning of the line "DatabaseMirror database.clamav.net" and Add "DatabaseMirror db.jp.clamav.net" #DatabaseMirror database.clamav.net DatabaseMirror db.jp.clamav.net ● Per Line 154 Add "NotifyClamd /etc/clamd.d/scan.conf" #NotifyClamd /path/to/clamd.conf NotifyClamd /etc/clamd.d/scan.conf |
4.Virus definition file update
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
# freshclam ClamAV update process started at Tue Jun 24 13:05:45 2025 daily database available for download (remote version: 27678) Time: 1.6s, ETA: 0.0s [========================>] 61.68MiB/61.68MiB Testing database: '/var/lib/clamav/tmp.882483b2b5/clamav-9121d7196371c359eebdb34814d97656.tmp-daily.cvd' ... Database test passed. daily.cvd updated (version: 27678, sigs: 2075789, f-level: 90, builder: raynman) main database available for download (remote version: 62) Time: 2.5s, ETA: 0.0s [========================>] 162.58MiB/162.58MiB Testing database: '/var/lib/clamav/tmp.882483b2b5/clamav-b6ac47570c69d0f3522777b9690b9104.tmp-main.cvd' ... Database test passed. main.cvd updated (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) bytecode database available for download (remote version: 336) Time: 0.1s, ETA: 0.0s [========================>] 277.52KiB/277.52KiB Testing database: '/var/lib/clamav/tmp.882483b2b5/clamav-b5981c2608acd1813dabffc12b9fa02a.tmp-bytecode.cvd' ... Database test passed. bytecode.cvd updated (version: 336, sigs: 83, f-level: 90, builder: nrandolp) WARNING: Clamd was NOT notified: Can't connect to clamd through /var/run/clamd.scan/clamd.sock: No such file or directory |
5.Clam AntiVirus start
clamd startup
|
1 |
# systemctl start clamd@scan |
clamd automatic startup settings
|
1 |
# systemctl enable clamd@scan |
operation check
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
# systemctl status clamd@scan ● clamd@scan.service - clamd scanner (scan) daemon Loaded: loaded (/usr/lib/systemd/system/clamd@.service; enabled; preset: d> Active: active (running) since Tue 2025-06-24 13:07:01 JST; 19s ago Invocation: 0ded23a363a841a5b376f2b28a74bdc0 Docs: man:clamd(8) man:clamd.conf(5) https://www.clamav.net/documents/ Main PID: 49752 (clamd) Tasks: 2 (limit: 46857) Memory: 1.2G (peak: 1.2G) CPU: 16.995s CGroup: /system.slice/system-clamd.slice/clamd@scan.service mq49752 /usr/sbin/clamd -c /etc/clamd.d/scan.conf Jun 24 13:07:01 Lepard clamd[49752]: ELF support enabled. Jun 24 13:07:01 Lepard clamd[49752]: Mail files support enabled. Jun 24 13:07:01 Lepard clamd[49752]: OLE2 support enabled. Jun 24 13:07:01 Lepard clamd[49752]: PDF support enabled. Jun 24 13:07:01 Lepard clamd[49752]: SWF support enabled. Jun 24 13:07:01 Lepard clamd[49752]: HTML support enabled. Jun 24 13:07:01 Lepard clamd[49752]: XMLDOCS support enabled. Jun 24 13:07:01 Lepard clamd[49752]: HWP3 support enabled. Jun 24 13:07:01 Lepard clamd[49752]: OneNote support enabled. |
6.Conducted virus scan
■Download a test virus and perform a virus scan
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# wget https://secure.eicar.org/eicar.com.txt # clamscan --infected --remove --recursive /root/eicar.com.txt: Win.Test.EICAR_HDB-1 FOUND /root/eicar.com.txt: Removed. ----------- SCAN SUMMARY ----------- Known viruses: 8707556 Engine version: 1.4.2 Scanned directories: 2 Scanned files: 11 Infected files: 1 Data scanned: 0.02 MB Data read: 0.01 MB (ratio 1.67:1) Time: 18.453 sec (0 m 18 s) Start Date: 2025:06:24 13:11:14 End Date: 2025:06:24 13:11:33 |
/root/eicar.com.txt: Win.Test.EICAR_HDB-1 FOUND
/root/eicar.com.txt: Removed.
Infected files: 1
The above is displayed and the virus file has been detected and deleted
7.Deployment of virus scan auto-execution scripts
Create script storage directory
|
1 |
# mkdir -p /var/www/system |
Create clamscan.sh in /var/www/system with the following contents
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
# vi /var/www/system/clamscan.sh #!/bin/bash PATH=/usr/bin:/bin # excludeopt setup excludelist=/var/www/system/clamscan.exclude if [ -s $excludelist ]; then for i in `cat $excludelist` do if [ $(echo "$i"|grep \/$) ]; then i=`echo $i|sed -e 's/^\([^ ]*\)\/$/\1/p' -e d` excludeopt="${excludeopt} --exclude-dir=$i" else excludeopt="${excludeopt} --exclude=$i" fi done fi # signature update freshclam # virus scan clamscan --recursive --remove ${excludeopt} / |
Execution authority for scripts
|
1 |
# chmod 700 /var/www/system/clamscan.sh |
8.Virus scan exclusion directory settings
Exclude sys and proc directories.
|
1 2 |
# echo "/sys/" >> /var/www/system/clamscan.exclude # echo "/proc/" >> /var/www/system/clamscan.exclude |
Try to implement a trial script
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# /var/www/system/clamscan.sh ----------- SCAN SUMMARY ----------- Known viruses: 8707556 Engine version: 1.4.2 Scanned directories: 18099 Scanned files: 105319 Infected files: 0 Data scanned: 8032.83 MB Data read: 4197.75 MB (ratio 1.91:1) Time: 1277.069 sec (21 m 17 s) Start Date: 2025:06:24 13:15:44 End Date: 2025:06:24 13:37:01 |
9.Scheduled virus scan execution
|
1 2 |
# crontab -e 0 1 * * * /var/www/system/clamscan.sh > /dev/null 2>&1 |
Mail Server Install
1. Postfix
1.1 Install
Install Postfix and build an SMTP server
|
1 |
# dnf -y install postfix |
Confirm Postfix is installed
|
1 2 3 4 5 |
# rpm -qa | grep postfix postfix-lmdb-3.8.5-8.el10.x86_64 postfix-3.8.5-8.el10.x86_64 postfix-perl-scripts-3.8.5-8.el10.x86_64 pcp-pmda-postfix-6.3.7-1.el10_0.x86_64 |
1.2 Register Postfix to the service
|
1 2 3 4 |
# systemctl enable postfix.service Created symlink /etc/systemd/system/multi-user.target.wants/postfix.service → /usr/lib/systemd/system/postfix.service. # systemctl is-enabled postfix.service enabled |
1.3 Backup postfix configuration files, main.cf and master.cf files
|
1 2 |
# cp -p /etc/postfix/main.cf `date '+/etc/postfix/main.cf.%Y%m%d'` # cp -p /etc/postfix/master.cf `date '+/etc/postfix/master.cf.%Y%m%d'` |
1.4 Edit postfix configuration file
To prevent unauthorized mail relay, configure Postfix to require authentication for outgoing mail as well, using Dovecot's SASL function.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 |
# vi /etc/postfix/main.cf ●Per Line 100 : Add #myhostname = virtual.domain.tld myhostname = mail.<domain> ●Per Line 107 : Add #mydomain = domain.tld mydomain = <domain> ●Per Line 122 : Delete comment out myorigin = $mydomain ●Per Line 139 : Change inet_interfaces = all ●Per Line 187 : Comment out and uncomment line 188 #mydestination = $myhostname, localhost.$mydomain, localhost mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain ●Per Line 293 : Add #mynetworks = 168.100.3.0/28, 127.0.0.0/8 #mynetworks = $config_directory/mynetworks #mynetworks = hash:/etc/postfix/network_table mynetworks = 192.168.11.0/24, 127.0.0.0/8 ←192.168.11.0/24 to suit your environment ●Delete comment per line 447 Set mail storage format. #home_mailbox = Mailbox home_mailbox = Maildir/ ●Per Line 454 : Delete comment #mail_spool_directory = /var/mail mail_spool_directory = /var/spool/mail ●Per Line 602 : Add #smtpd_banner = $myhostname ESMTP $mail_name #smtpd_banner = $myhostname ESMTP $mail_name ($mail_version) smtpd_banner = $myhostname ESMTP unknown ●Add the following to the last line # Limit send/receive mail size to 10M message_size_limit = 10485760 # Limit mailbox size to 1G mailbox_size_limit = 1073741824 # SMTP-Auth Settings smtpd_sasl_type = dovecot smtpd_sasl_path = private/auth smtpd_sasl_auth_enable = yes smtpd_sasl_security_options = noanonymous smtpd_sasl_local_domain = $mydomain smtpd_recipient_restrictions = permit_mynetworks, permit_auth_destination, permit_sasl_authenticated, reject |
1.5 Allow SMTP port (port 25)
|
1 2 3 4 |
# firewall-cmd --add-service=smtp --permanent success # firewall-cmd --reload success |
1.6 Start Postfix
|
1 |
# systemctl restart --now postfix |
2.Dovecot
2.1 dovecot Install
|
1 |
# dnf -y install dovecot |
2.2 Edit dovecot.conf file
|
1 2 3 4 5 6 7 8 9 |
# cp -p /etc/dovecot/dovecot.conf `date '+ /etc/dovecot/dovecot.conf.%Y%m%d'` # vi /etc/dovecot/dovecot.conf ●Add per line 25 # protocols = imap pop3 lmtp protocols = imap pop3 ●Line 30 : Uncomment # Remove [::] if listening for IPv4 only listen = * |
2.3 Edit 10-auth.conf file
|
1 2 3 4 5 6 |
# vi /etc/dovecot/conf.d/10-auth.conf ●Line 10 : Uncomment and change Plain text authentication is also allowed disable_plaintext_auth = no ●Line 100 : Add auth_mechanisms = plain login |
2.3 Edit 10-mail.conf file
|
1 2 3 |
# vi /etc/dovecot/conf.d/10-mail.conf ●Line 31 : Add mail_location = maildir:~/Maildir |
2.4 Edit 10-master.conf file
|
1 2 3 4 5 6 7 8 |
# vi /etc/dovecot/conf.d/10-master.conf ● Line 110-112 : Uncommented and added # Postfix smtp-auth unix_listener /var/spool/postfix/private/auth { mode = 0666 user = postfix group = postfix } |
2.5 Edit 10-ssl.conf file
|
1 2 3 4 |
# vi /etc/dovecot/conf.d/10-ssl.conf ●Per line 8 Change "ssl = required" to "ssl = yes" ssl = yes |
2.6 Register dovecot as a service and start it
|
1 2 3 4 5 |
# systemctl enable dovecot.service Created symlink /etc/systemd/system/multi-user.target.wants/dovecot.service → /usr/lib/systemd/system/dovecot.service. # systemctl is-enabled dovecot.service Enabled # systemctl start dovecot.service |
2.7 Allow POP/IMAP services in Firewalld Port Allow
POP is [110/TCP], IMAP is [143/TCP].
|
1 2 3 |
# firewall-cmd --permanent --add-service=pop3 # firewall-cmd --permanent --add-service=imap # firewall-cmd --reload |
3.Create mail user and check operation
3.1 advance preparation
①new user
When a new user is added, set up the system to automatically send and receive e-mail.
|
1 2 3 4 |
# mkdir -p /etc/skel/Maildir/{new,cur,tmp} # chmod -R 700 /etc/skel/Maildir/ # echo "~/Maildir/"> /etc/skel/.forward # chmod 600 /etc/skel/.forward |
②Existing users
Configure the already created users to be able to send and receive e-mail.
|
1 2 3 4 |
# mkdir -p /home/huong/Maildir/{new,cur,tmp} # chown -R huong:huong /home/huong/Maildir/ # chmod 700 /home/huong/Maildir # chmod 700 /home/huong/Maildir/{new,cur,tmp} |
3.2 User Account Creation
|
1 2 3 4 5 6 7 8 9 10 11 |
Mail Client Install # dnf -y install s-nail # echo 'export MAIL=$HOME/Maildir' >> /etc/profile.d/mail.sh Add user [linux] # useradd linux # passwd linux Changing password for user linux. New password: Retype new password: passwd: password updated successfully |
3.3 operation check ①
①Log in as an email user and send a test email.
|
1 2 3 4 5 6 7 8 9 10 11 |
# su - linux $ mail linux@localhost Subject: Test Mail To: linux@localhost mail test ^D ------- (Preliminary) Envelope contains: To: linux@localhost Subject: Test Mail Send this message [yes/no, empty: recompose]? y |
②Email Confirmation
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
$ mail s-nail version v14.9.24. Type `?' for help /home/linux/Maildir: 1 message 1 new ▸N 1 linux@korodes.com 2025-06-24 13:58 14/408 "Test Mail " & 1 [-- Message 1 -- 14 lines, 408 bytes --]: Date: Tue, 24 Jun 2025 13:58:05 +0900 To: linux@localhost Subject: Test Mail Message-Id: <20250624045805.74E2C41F88E7@mail.korodes.com> From: linux@korodes.com mail test & q Held 1 message in /home/linux/Maildir |
3.4 operation check ②
Set up and confirm your account in Mozilla Thunderbird (for OS user huong as mail user)
①Start Thunderbird
Your full name : Any name
Email address : huong@<domain-name>
Password : Password for huong
Enter each and click "Configure manually".
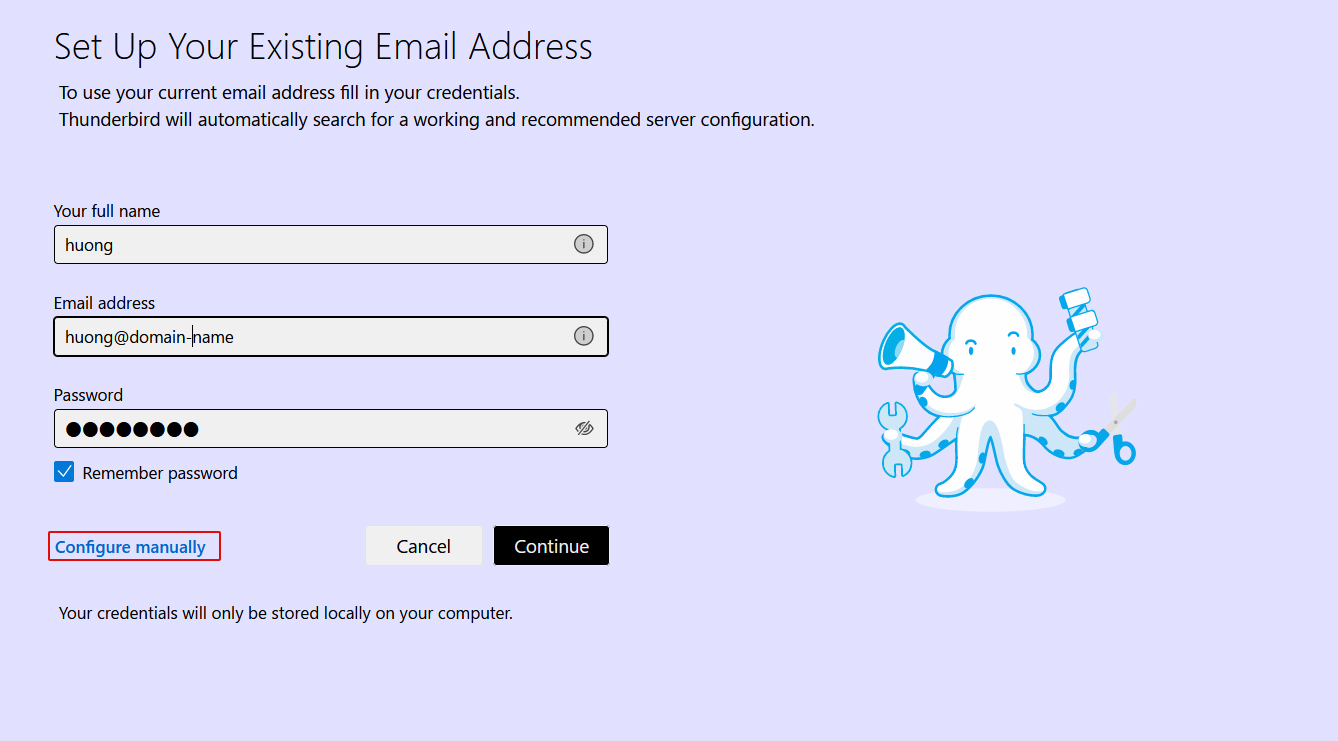
➁Set "INCOMMING SERVER" and "OUTGOING SERVER" as shown below and click "Re-test".
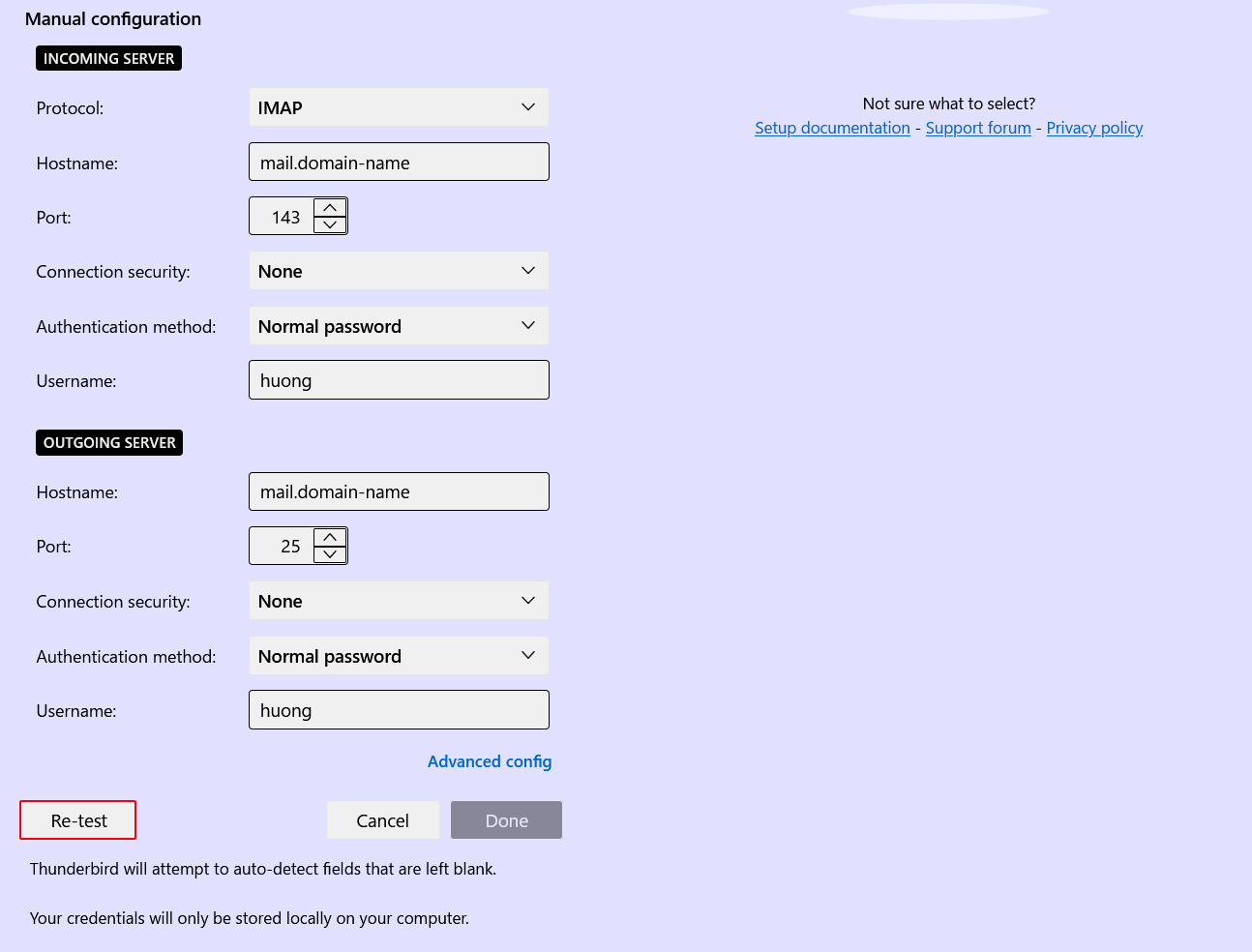
➂The following settings were found by probinfg the given server
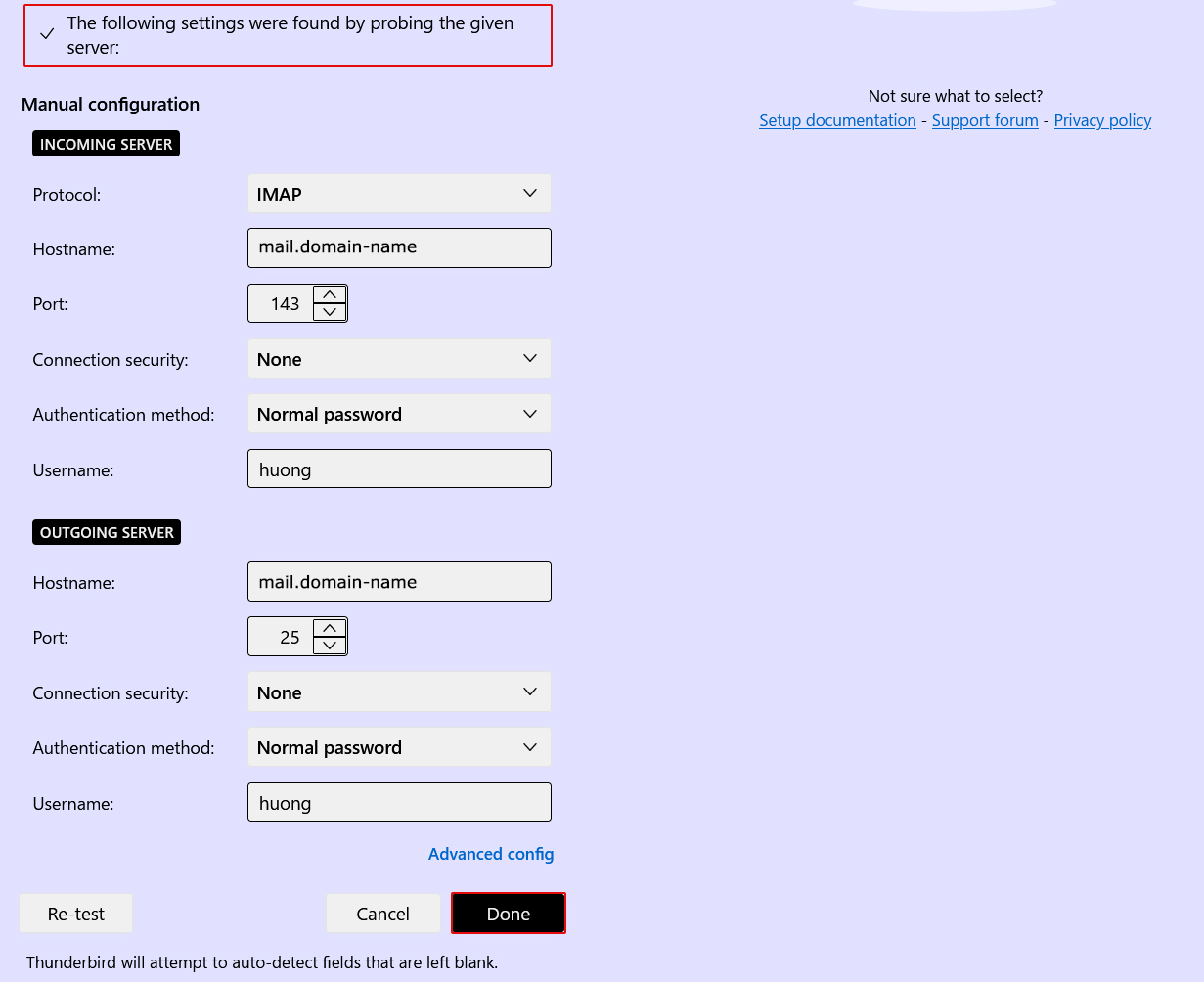
After clicking "Done," the following "Warning" appears, but there is no problem, so click "Confirm."
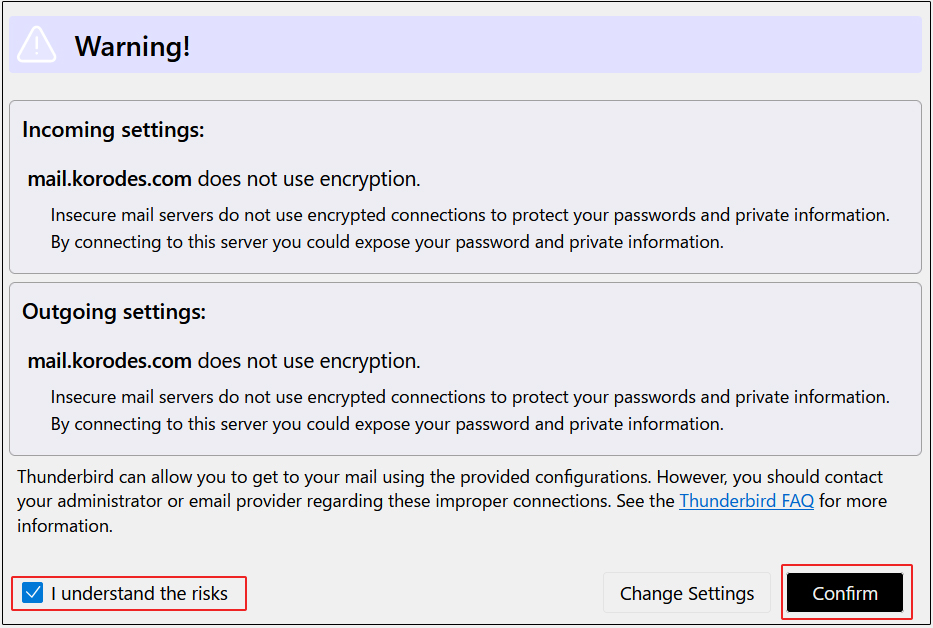
④Click "Finish" when "Account syccessfuly created" is displayed.
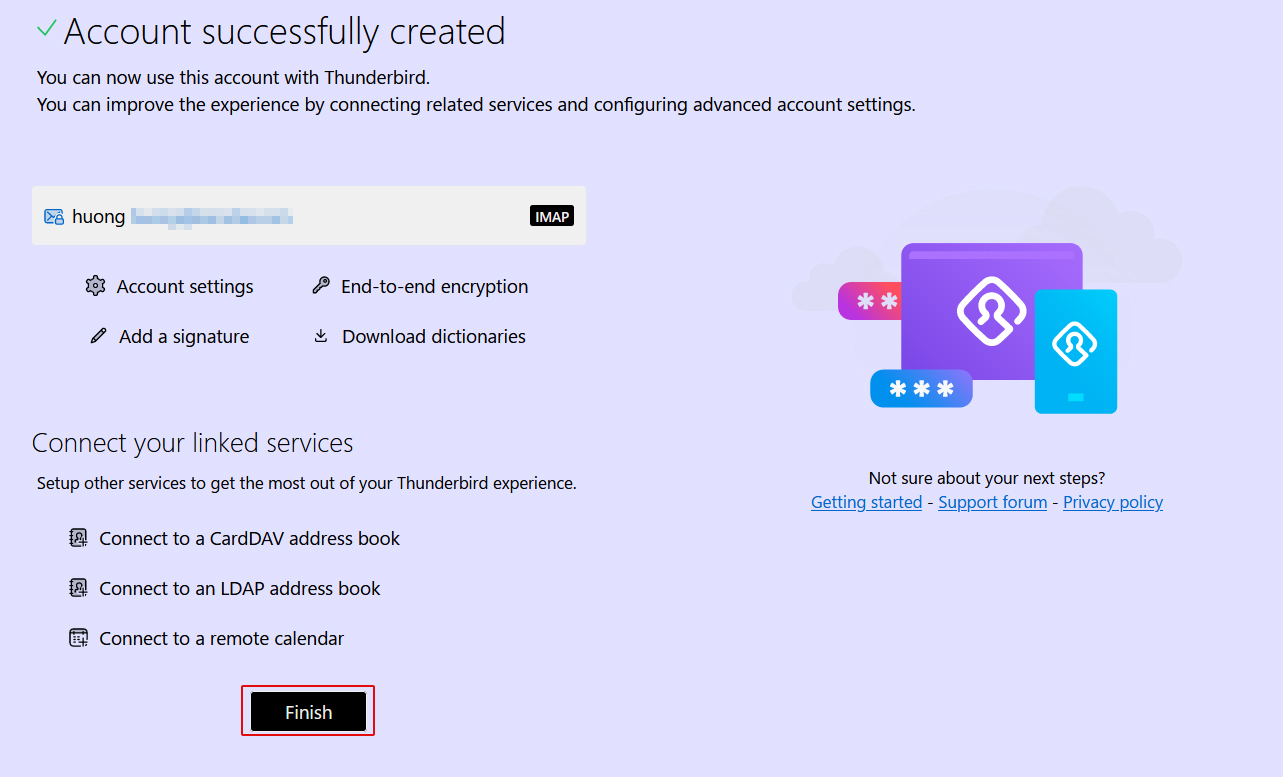
Mail : Postfix + Clamav + clamav-milter+SpamAssassin
1.Real-time scanning of e-mails
①clamav-milter Install
Virus checks are performed on the mail server side using Clam AntiVirus.
The mail server and Clam AntiVirus are linked using clamav-milter.
|
1 |
# dnf -y install clamav-milter clamav-milter-systemd |
➁clamav-milter configuration
Edit clamav-milter configuration file
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 |
# vi /etc/mail/clamav-milter.conf Line 6 # Comment or remove the line below. #Example ← Add # at the beginning of the line and comment out Per Line 23-24: Add # Default: no default #MilterSocket /run/clamav-milter/clamav-milter.socket #MilterSocket /tmp/clamav-milter.sock #MilterSocket inet:7357 MilterSocket /var/run/clamav-milter/clamav-milter.socket ← Specify the UNIX socket name for clamav-milter MilterSocketMode 660 ← Specify UNIX socket access rights for clamav-milter Per Line 98: Add # Default: no default #ClamdSocket tcp:scanner.mydomain:7357 #ClamdSocket unix:/run/clamav/clamd.sock ClamdSocket unix:/var/run/clamd.scan/clamd.sock ←Specify the UNIX socket name for Clam AntiVirus (match the LocalSocket option in /etc/clamd.d/scan.conf) Per Line171 : Add # Action to be performed on infected messages # Default: Quarantine #OnInfected Quarantine OnInfected Blackhole ← Destroy virus-infected e-mails. Per Line 193 : Add # Note that while "Replace" can potentially break DKIM signatures, "Add" may # confuse procmail and similar filters. # Default: no #AddHeader Replace AddHeader Yes ← Outputs a message in the mail header stating that a virus check has been performed. Per Line 253 : Delete comment # Default: LOG_LOCAL6 LogFacility LOG_MAIL ← Log output destination to mail log |
➂clamav-milter startup and auto-startup settings
|
1 2 3 4 |
# systemctl start clamav-milter # systemctl enable clamav-milter Created symlink /etc/systemd/system/multi-user.target.wants/clamav-milter.service → /usr/lib/systemd/system/clamav-milter.service. |
④Postfix and clamav-milter integration settings
Edit Postfix configuration file
|
1 2 3 4 5 |
# vi /etc/postfix/main.cf Add the following to the last line milter_default_action = tempfail smtpd_milters = unix:/var/run/clamav-milter/clamav-milter.socket non_smtpd_milters = unix:/var/run/clamav-milter/clamav-milter.socket |
⑤Add postfix user to clamilt group
|
1 |
# usermod -G clamilt -a postfix |
⑥Postfix Settings Reflected
|
1 |
# systemctl restart postfix |
⑦Check with Thunderbird
I sent a blank email to myself in Thunderbird, and in the header display of the received email, I see the following
X-Virus-Scanned: clamav-milter 1.4.2 at Lepard
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
Return-Path: xxxxx@xxxxxx.com
X-Original-To: xxxxx@xxxxxx.com
Delivered-To: xxxxx@xxxxxx.com
Received: from [192.168.11.8] (buffalo.setup [192.168.11.1])
by mail.xxxxxx.com (Postfix) with ESMTPA id 255F241F87D8
for xxxxx@xxxxxx.com; Tue, 24 Jun 2025 14:11:50 +0900 (JST)
Message-ID: 1b3aace1-204d-497f-abdf-ba46c9229e8d@xxxxxx.com
Date: Tue, 24 Jun 2025 14:11:48 +0900
MIME-Version: 1.0
User-Agent: Mozilla Thunderbird
From: xxxxx xxxxx@xxxxxx.com
Content-Language: en-US
To: xxxxx xxxxx@xxxxxx.com
Content-Type: text/plain; charset=UTF-8; format=flowed
Content-Transfer-Encoding: 7bit
X-Virus-Scanned: clamav-milter 1.4.2 at Lepard
X-Virus-Status: Clean
Try sending yourself an email with the body of the email "X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*" and confirm that the email is discarded and never received
2.Email spam protection
2.1 SpamAssassin・procmail・postfix settings
①SpamAssassin・procmail Install
|
1 |
# dnf -y install spamassassin procmail |
➁procmail settings
Create /etc/procmailrc if you want to apply the settings to all users
To configure for each individual, create
~/.procmailrc in each user's home directory
Create /etc/procmailrc this time
|
1 |
# vi /etc/procmailrc |
Contents of procmailrc
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
SHELL=/bin/bash PATH=/usr/bin:/bin:/usr/local/bin DROPPRIVS=yes MAILDIR=$HOME/Maildir DEFAULT=$MAILDIR/ SPAM=$MAILDIR/.Spam/ LOGFILE=$HOME/.procmail.log # Log output destination VERBOSE=ON # If there is no “X-Spam-***” in the mail header, spamassassassin will be started. :0fw *!^X-Spam.* |spamassassin # If there is an “X-Spam-Status: Yes” in the mail header, the mail is stored in the “.Spam” directory :0 * ^X-Spam-Status: Yes $SPAM |
➂Edit postfix configuration file
with root privileges
|
1 2 3 4 |
# vi /etc/postfix/main.cf Per Line 478 : Add mailbox_command = /usr/bin/procmail -a "$EXTENSION" |
④Edit spamassassin configuration file
|
1 2 3 4 |
# vi /etc/mail/spamassassin/v310.pre Delete # at the beginning of the line per line 24 loadplugin Mail::SpamAssassin::Plugin::DCC |
⑤postfix、spamassassin restart
|
1 2 |
# systemctl restart postfix spamassassin # systemctl enable spamassassin |
⑥Check with Thudrtbird
If you send a blank email to yourself and the header looks like this, it is normal
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
Return-Path: xxxxx@xxxxxx.com
X-Spam-Checker-Version: SpamAssassin 4.0.1 (2024-03-26) on Lepard
X-Spam-Level: ***
X-Spam-Status: No, score=3.1 required=5.0 tests=ALL_TRUSTED,EMPTY_MESSAGE,
MISSING_SUBJECT autolearn=no autolearn_force=no version=4.0.1
--------------------------------------------------
⑦Create script to update SpamAssassin configuration file
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
# cd /var/www/system # vi spamassassin-update.sh Describe the following information #!/bin/bash cd /etc/mail/spamassassin wget -q https://github.com/kittyfreak/spamassassin_user_prefs/archive/refs/heads/main.zip [ $? -ne 0 ] && exit unzip main.zip >/dev/null 2>&1 [ $? -ne 0 ] && exit rm -f main.zip mv spamassassin_user_prefs-main/user_prefs . rm -rf spamassassin_user_prefs-main diff user_prefs user_prefs.org > /dev/null 2>&1 if [ $? -ne 0 ]; then cp user_prefs local.cf echo "report_safe 0" >> local.cf echo "rewrite_header Subject ***SPAM***" >> local.cf # SpamAssassin restart if [ -f /etc/rc.d/init.d/spamassassin ]; then /etc/rc.d/init.d/spamassassin restart > /dev/null else systemctl restart spamassassin > /dev/null fi fi cp user_prefs user_prefs.org |
Grant execute permission to the spamassassin-update script and run it
|
1 2 |
# chmod 700 /var/www/system/spamassassin-update.sh # /var/www/system/spamassassin-update.sh |
Confirm that the SpamAssassin configuration file (local.cf) is created in the /etc/mail/spamassassin directory with the date of the day
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
# ls -l /etc/mail/spamassassin total 1656 drwxr-xr-x 2 root root 40 Jun 24 14:32 channel.d -rw-r--r-- 1 root root 1649 Nov 29 2024 init.pre -rw-r--r-- 1 root root 500636 Jun 24 14:59 local.cf drwx------ 2 root root 6 Nov 29 2024 sa-update-keys -rw-r--r-- 1 root root 62 Nov 29 2024 spamassassin-default.rc -rwxr-xr-x 1 root root 39 Nov 29 2024 spamassassin-helper.sh -rw-r--r-- 1 root root 55 Nov 29 2024 spamassassin-spamc.rc -rw-r--r-- 1 root root 500588 Apr 30 2023 user_prefs -rw-r--r-- 1 root root 500588 Jun 24 14:59 user_prefs.org -rw-r--r-- 1 root root 2262 Jun 24 14:50 v310.pre -rw-r--r-- 1 root root 1168 Nov 29 2024 v312.pre -rw-r--r-- 1 root root 2416 Nov 29 2024 v320.pre -rw-r--r-- 1 root root 1237 Nov 29 2024 v330.pre -rw-r--r-- 1 root root 1020 Nov 29 2024 v340.pre -rw-r--r-- 1 root root 1315 Nov 29 2024 v341.pre -rw-r--r-- 1 root root 1519 Nov 29 2024 v342.pre -rw-r--r-- 1 root root 1266 Nov 29 2024 v343.pre -rw-r--r-- 1 root root 1482 Nov 29 2024 v400.pre -rw-r--r-- 1 root root 1118 Nov 29 2024 v401.pre |
Set up cron to automatically run a script daily that updates the SpamAssassin configuration file
|
1 2 |
# crontab -e 0 2 * * * /var/www/system/spamassassin-update.sh > /dev/null 2>&1 |
2.2 Spam mail sorting settings
Mail marked as spam in the mail header by SpamAssassin will be delivered to a spam-only mailbox, while other mail will be delivered to a normal mailbox.
Create a dedicated spam mailbox
For existing users, add a spam-only mailbox to their mailboxes.
For new users, a spam-only mailbox will be automatically created when a user is added.
①Created script to create spam-only mailboxes
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# vi spamfolder-create #!/bin/bash for user in `ls /home` do id -u $user > /dev/null 2>&1 if [ $? -eq 0 ] && [ ! -d /home/$user/Maildir/.Spam/new ]; then mkdir -p /home/$user/Maildir/.Spam/new mkdir -p /home/$user/Maildir/.Spam/cur mkdir -p /home/$user/Maildir/.Spam/tmp chmod -R 700 /home/$user/Maildir/.Spam chown -R $user:$user /home/$user/Maildir/.Spam echo $user fi done |
Run script to create spam-only mailboxes
|
1 2 3 |
# bash spamfolder-create huong linux |
New user countermeasure
Automatically creates a spam-only mailbox when a new user is added.
|
1 2 |
# mkdir -p /etc/skel/Maildir/.Spam/{new,cur,tmp} # chmod -R 700 /etc/skel/Maildir/.Spam |
➁Spam Mail Sorting
Emails identified as spam by SpamAssassin are delivered to a spam-only mailbox.
|
1 2 3 4 5 6 |
# vi /etc/procmailrc Add the following to the end # SpamAssassin will deliver spam emails to a spam-only mailbox. :0 *^X-Spam-Flag: YES $HOME/Maildir/.Spam/ |
➂confirmation
When you send a blank email to yourself, the following message is appended to the header of the received email
X-Spam-Checker-Version: SpamAssassin 4.0.1 (2024-03-26) on Lepard
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
Return-Path: xxxxx@xxxxxx.com
X-Spam-Checker-Version: SpamAssassin 4.0.1 (2024-03-26) on Lepard
X-Spam-Level: **
X-Spam-Status: No, score=2.3 required=13.0 tests=ALL_TRUSTED,
CONTENT_TYPE_PRESENT,EMPTY_MESSAGE autolearn=no autolearn_force=no
version=4.0.1
④Spam check confirmation
Send yourself an email with the body of the email “XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X” and make sure the email is not delivered and sorted into the Spam folder
The header should include The header should read something like
X-Spam-Checker-Version: SpamAssassin 4.0.1 (2024-03-26) on Lepard
X-Spam-Flag: YES
X-Spam-Level:
X-Spam-Status: Yes, score=1001.8 required=13.0 tests=ALL_TRUSTED,
CONTENT_TYPE_PRESENT,GTUBE,HTML_MESSAGE,MPART_ALT_DIFF,
MULTIPART_ALTERNATIVE autolearn=no autolearn_force=no version=4.0.1
X-Spam-Report:
* 0.1 ALL_TRUSTED Passed through trusted hosts only via SMTP
* -0.1 CONTENT_TYPE_PRESENT exists:Content-Type
* 0.1 MULTIPART_ALTERNATIVE Multipart/alternative
* 1000 GTUBE BODY: Generic Test for Unsolicited Bulk Email
* 1.0 HTML_MESSAGE BODY: HTML included in message
* 0.7 MPART_ALT_DIFF BODY: HTML and text parts are different

