Contents
1. clamav ( anti-virus software )
1.1 Clamav Install
|
1 |
# zypper -n install clamav |
1.2 virus definition file update
①Configuration File Editing
|
1 2 3 4 |
# vi /etc/freshclam.conf 〇Line 71 : Comment out and add below #DatabaseMirror database.clamav.net DatabaseMirror db.jp.clamav.net |
②virus definition file update
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# freshclam ClamAV update process started at Sun Jun 16 15:04:51 2024 daily database available for download (remote version: 27307) Time: 0.8s, ETA: 0.0s [========================>] 60.81MiB/60.81MiB Testing database: '/var/lib/clamav/tmp.246c380401/clamav-52aed66ac330b66854486579bd02daee.tmp-daily.cvd' ... Database test passed. daily.cvd updated (version: 27307, sigs: 2063014, f-level: 90, builder: raynman) main database available for download (remote version: 62) Time: 1.6s, ETA: 0.0s [========================>] 162.58MiB/162.58MiB Testing database: '/var/lib/clamav/tmp.246c380401/clamav-b71ee05771cd6a38b5f7c6371d6cb2ec.tmp-main.cvd' ... Database test passed. main.cvd updated (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) bytecode database available for download (remote version: 335) Time: 0.2s, ETA: 0.0s [========================>] 282.94KiB/282.94KiB Testing database: '/var/lib/clamav/tmp.246c380401/clamav-717e25953f9087ce3d269a183663db24.tmp-bytecode.cvd' ... Database test passed. bytecode.cvd updated (version: 335, sigs: 86, f-level: 90, builder: raynman) WARNING: Clamd was NOT notified: Can't connect to clamd through /run/clamav/clamd-socket: No such file or directory |
1.3 operation check
①Scan entire system
■If no virus is detected
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# cd # clamscan --infected --remove --recursive ----------- SCAN SUMMARY ----------- Known viruses: 8694597 Engine version: 0.103.11 Scanned directories: 8 Scanned files: 8 Infected files: 0 Data scanned: 0.05 MB Data read: 0.03 MB (ratio 1.71:1) Time: 21.971 sec (0 m 21 s) Start Date: 2024:06:16 15:05:53 End Date: 2024:06:16 15:06:15 |
■If a virus is detected
Download and scan for test viruses
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# wget https://secure.eicar.org/eicar.com.txt # clamscan --infected --remove --recursive /root/eicar.com: Win.Test.EICAR_HDB-1 FOUND ←Virus detection /root/eicar.com: Removed. ← virus removal ----------- SCAN SUMMARY ----------- Known viruses: 8694597 Engine version: 0.103.11 Scanned directories: 8 Scanned files: 10 Infected files: 1 Data scanned: 0.05 MB Data read: 0.03 MB (ratio 1.71:1) Time: 14.340 sec (0 m 14 s) Start Date: 2024:06:16 15:08:40 End Date: 2024:06:16 15:08:55 |
1.4 Deployment of virus scan auto-execution scripts
①Create script storage directory
|
1 |
# mkdir -p /srv/www/system |
②Creation of auto-execution scripts
# cd /srv/www/system
Create clamscan.sh in /srv/www/system with the following contents
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
# vi /srv/www/system/clamscan.sh #!/bin/bash PATH=/usr/bin:/bin # excludeopt setup excludelist=/srv/www/system/clamscan.exclude if [ -s $excludelist ]; then for i in `cat $excludelist` do if [ $(echo "$i"|grep \/$) ]; then i=`echo $i|sed -e 's/^\([^ ]*\)\/$/\1/p' -e d` excludeopt="${excludeopt} --exclude-dir=$i" else excludeopt="${excludeopt} --exclude=$i" fi done fi # signature update freshclam # virus scan clamscan --recursive --remove ${excludeopt} / |
Grant execute permissions to scripts
|
1 |
# chmod 700 clamscan.sh |
The sys and proc directories are excluded from the scan because they cannot be scanned due to the specification.
OpenSUSE creates a large number of snapshots, so if necessary, set them in non-target directories.
|
1 2 3 |
# echo "/sys/" >> /srv/www/system/clamscan.exclude # echo "/proc/" >> /srv/www/system/clamscan.exclude # echo "/.snapshots/" >> /srv/www/system/clamscan.exclude |
Set up periodic virus scan
|
1 2 |
# crontab -e 0 1 * * * /srv/www/system/clamscan.sh > /dev/null 2>& |
Execute "/srv/www/system/clamscan.sh" to scan the entire system
|
1 |
# /srv/www/system/clamscan.sh |
2. Mail server Install
2.1 Postfix Install
①Install Postfix and build an SMTP server
|
1 |
# zypper -n install postfix |
②Postfix Settings
To prevent unauthorized mail relay, use the SASL function of Dovecot, described below, and configure Postfix to require authentication for sending as well.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 |
# vi /etc/postfix/main.cf # Line 108:host name specification myhostname = mail.[domain] # Line 114:Uncomment and specify domain name mydomain = [domain] # Line 130:Uncomment myorigin = $mydomain # Line 294:Uncommented and added to my network. mynetworks = 127.0.0.0/8, 192.168.11.0/24 # Line 451:Uncommented Maildir format home_mailbox = Maildir/ # Line 715:Change inet_interfaces = all # Line 720:Add mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain # Line 734,735 # Limit mailbox size as needed (example below is 1G) mailbox_size_limit = 1073741824 # Limit send/receive mail size as needed (10M in the example below) message_size_limit = 10485760 # Line 747:Add smtpd_recipient_restrictions = permit_mynetworks, permit_auth_destination, permit_sasl_authenticated, reject # Per Line762:Change smtpd_sasl_auth_enable = yes # Per Line767,768:Make it commented out and add under it #smtpd_sasl_type = cyrus #smtpd_sasl_path = smtpd smtpd_sasl_type = dovecot smtpd_sasl_path = private/auth smtpd_sasl_security_options = noanonymous smtpd_sasl_local_domain = $myhostname # Line 851,852 : comment-out #myhostname = localhost #mydestination = $myhostname, localhost.$mydomain, localhost |
|
1 2 |
# systemctl start postfix # systemctl enable postfix |
③SMTP service permission is required if Firewalld is enabled; SMTP uses 25/TCP
|
1 2 3 4 |
# firewall-cmd --add-service=smtp --permanent success # firewall-cmd --reload success |
2.3 Dovecot Install
①Install
|
1 |
# zypper -n install dovecot |
②Dovecot Settings
Configure Dovecot to provide SASL functionality for Postfix.
|
1 2 3 |
# vi /etc/dovecot/dovecot.conf # Line 30:Uncomment (remove ", ::" if not listening for IPv6) listen = * |
|
1 2 3 4 5 6 |
# vi /etc/dovecot/conf.d/10-auth.conf # Line 10:Uncomment and change (also allow plain text authentication) disable_plaintext_auth = no # Line 100:add auth_mechanisms = plain login |
|
1 2 3 |
# vi /etc/dovecot/conf.d/10-mail.conf # Line 30:Uncommented and added mail_location = maildir:~/Maildir |
|
1 2 3 4 5 6 7 8 |
# vi /etc/dovecot/conf.d/10-master.conf # Line 107-109:Uncomment and add # Postfix smtp-auth unix_listener /var/spool/postfix/private/auth { mode = 0666 user = postfix group = postfix } |
③Dovecot startup and automatic execution
|
1 2 3 |
# systemctl start dovecot # systemctl enable dovecot Created symlink /etc/systemd/system/multi-user.target.wants/dovecot.service → /usr/lib/systemd/system/dovecot.service. |
④POP/IMAP service permission required if Firewalld is enabled
POP uses 110/TCP, IMAP uses 143/TCP
|
1 2 3 4 |
# firewall-cmd --add-service={pop3,imap} --permanent success # firewall-cmd --reload success |
2.4 User Account Registration
In this case, we will register the OS user "huong".
①Mail client installation
|
1 |
# zypper -n install mailx |
②Mailboxes are set to refer to Maildir
|
1 |
# echo 'export MAIL=$HOME/Maildir' >> /etc/profile.d/mail.sh |
2.5 Confirmation of operation
Set up an account in Thunderbird, a free email client, to check its operation.
However, depending on your provider, port 587 may be used for the outgoing server.
Please free up port 587 in your firewall settings.
|
1 2 |
# firewall-cmd --add-port=587/tcp --permanent # firewall-cmd --reload |
Start Thunderbird and select "Account Settings" from the "Tools" menu.
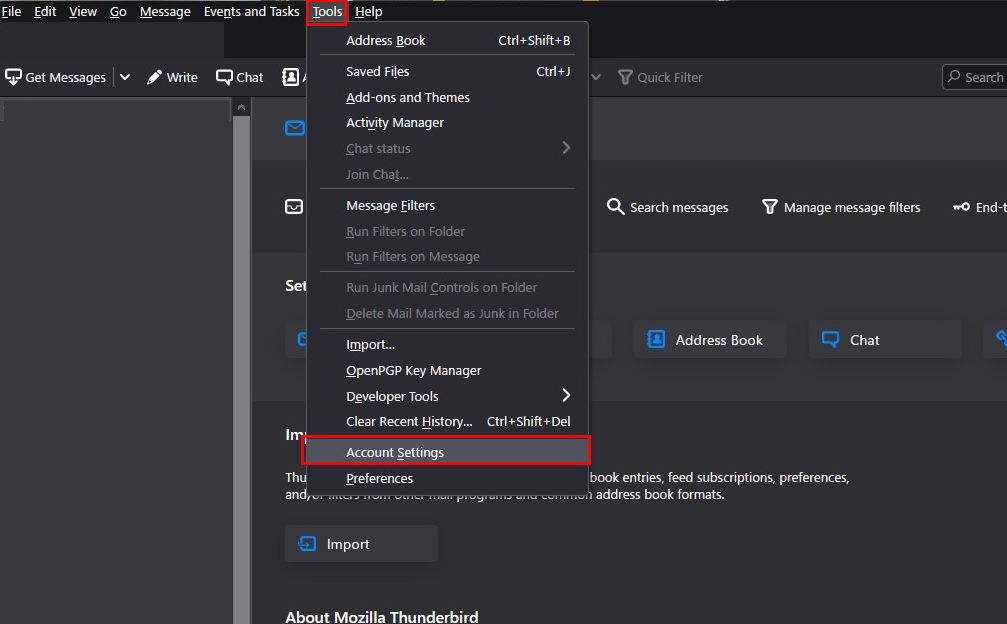
"Add Mail Account..." in "Account Actions" Select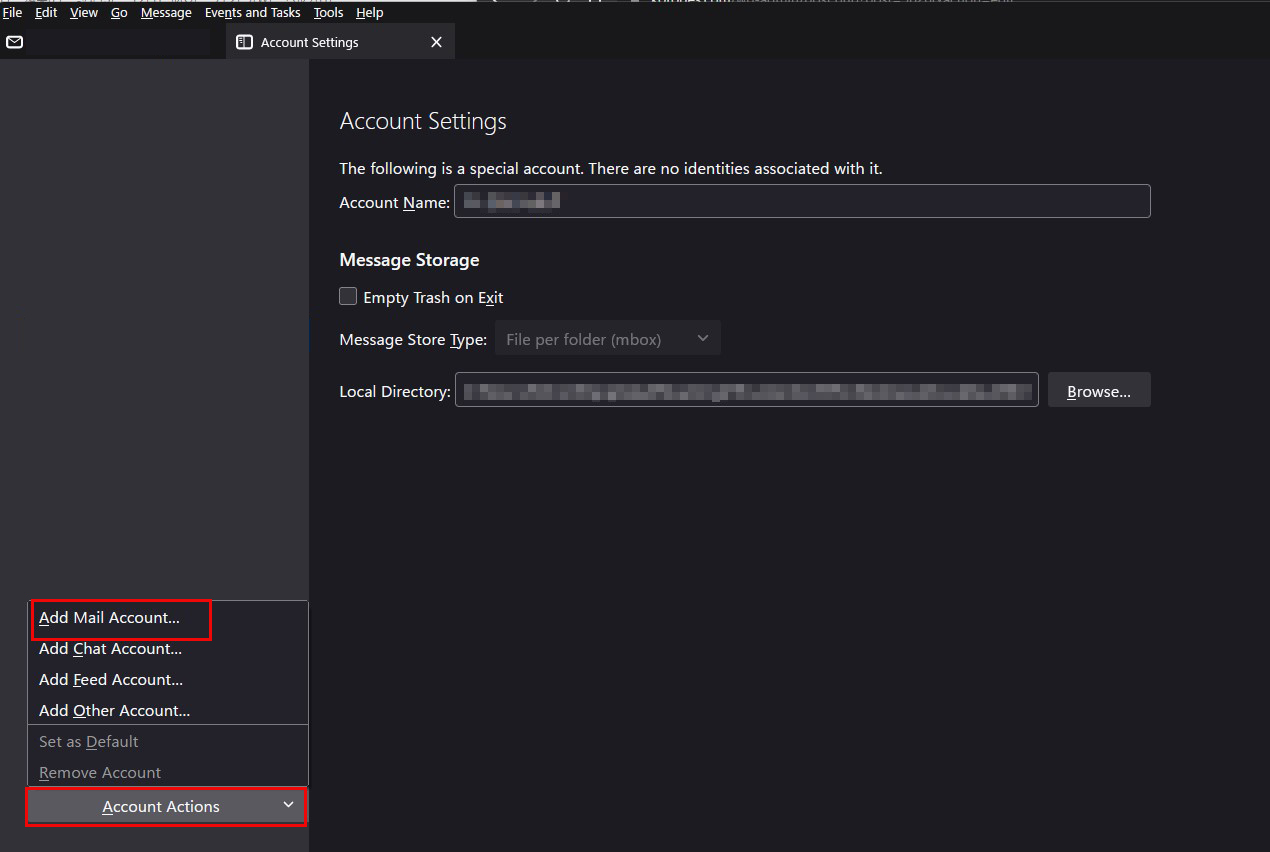
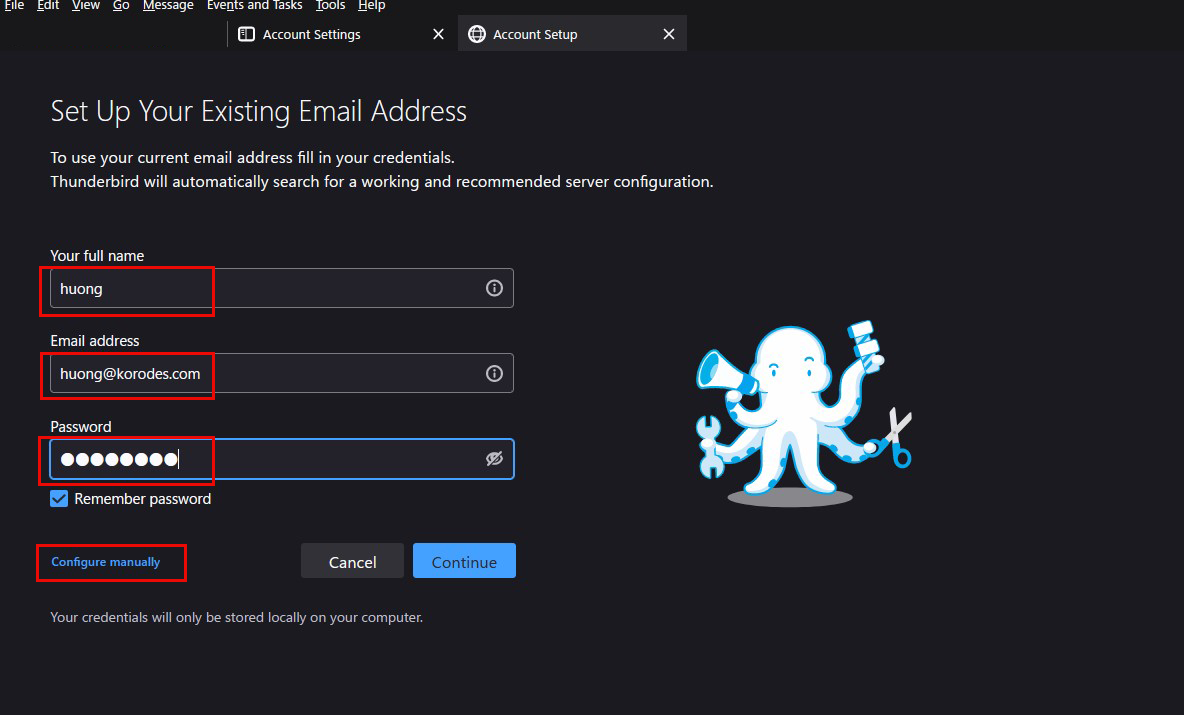
Fill in each field as follows and click "Configure manually"
Your full name : Any name
Email address : <Mail server user name>@<Domain name>
Password : Password for the mail server user
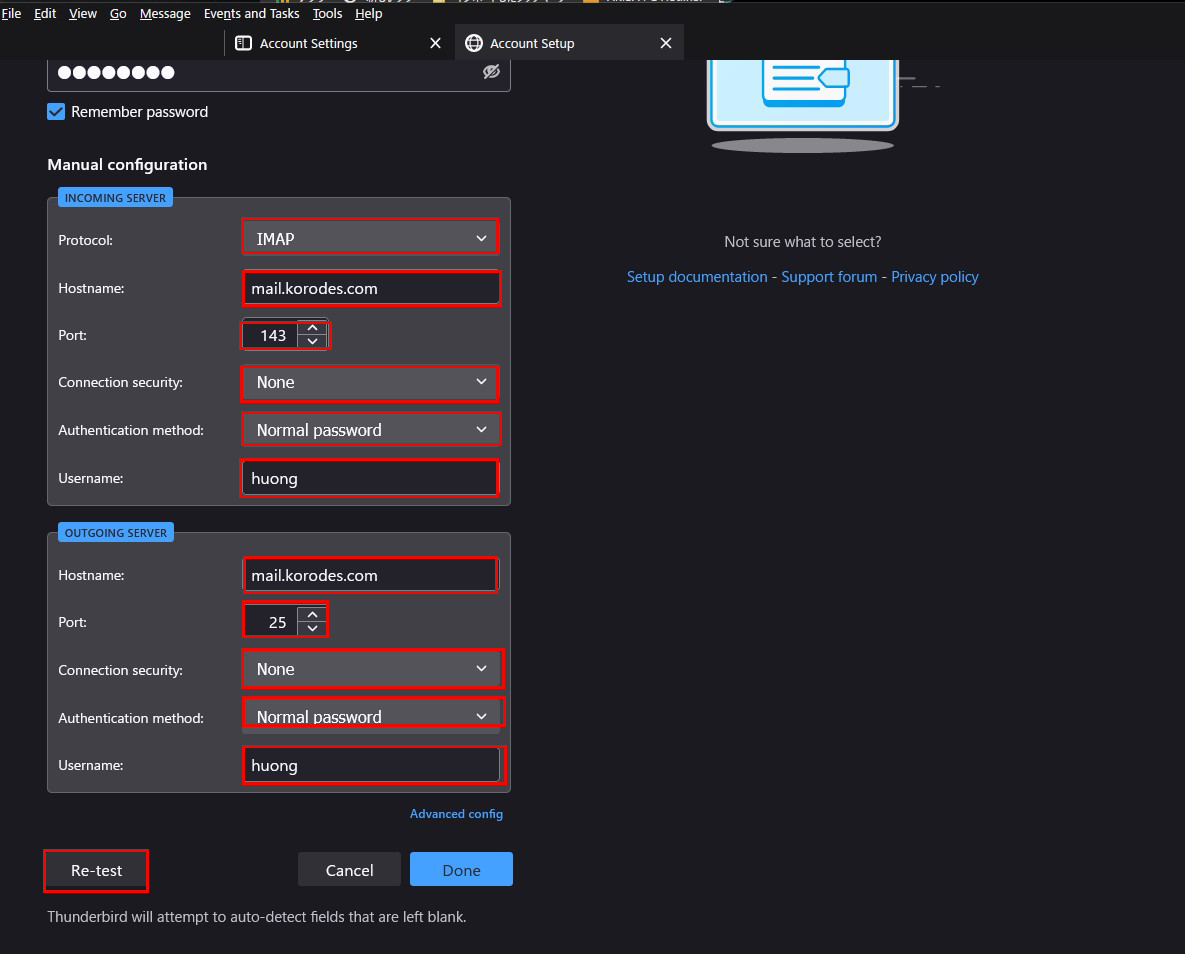
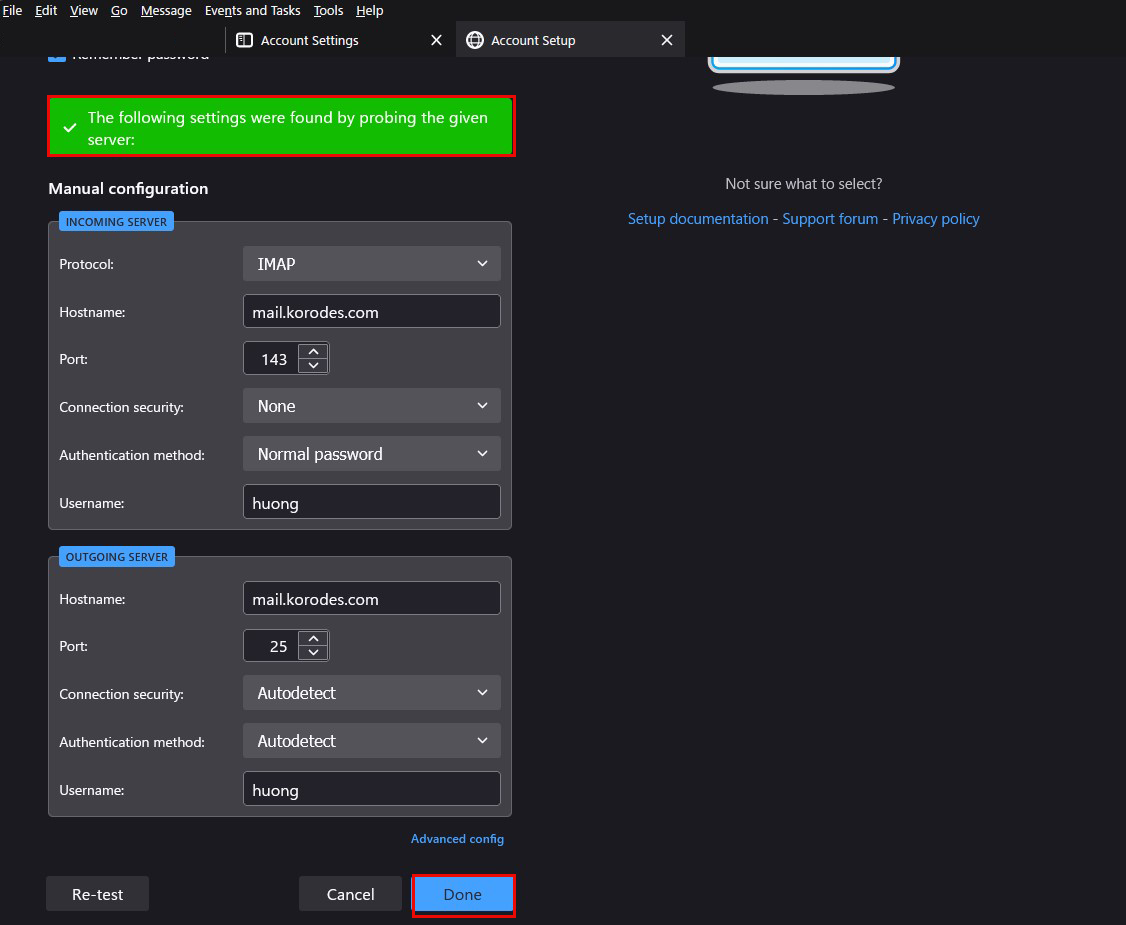
Set as shown below, but if your provider allows port 25 for outbound servers, you may use "25" instead of "587". Click "Re-test"
Click "Done" when you see "Mail server found, account is valid.
A warning screen will appear. Check the box as shown below and click "Confirm.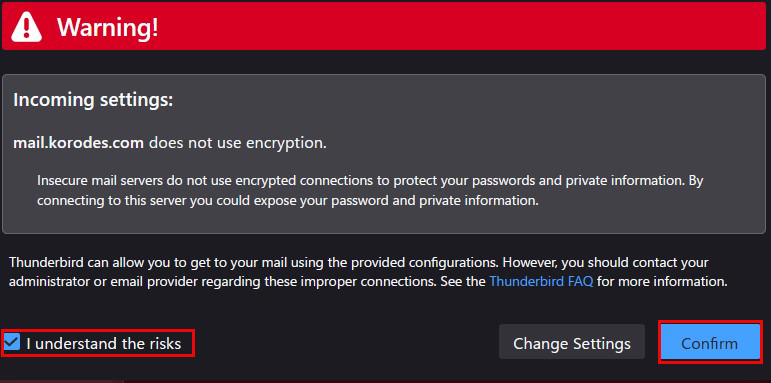
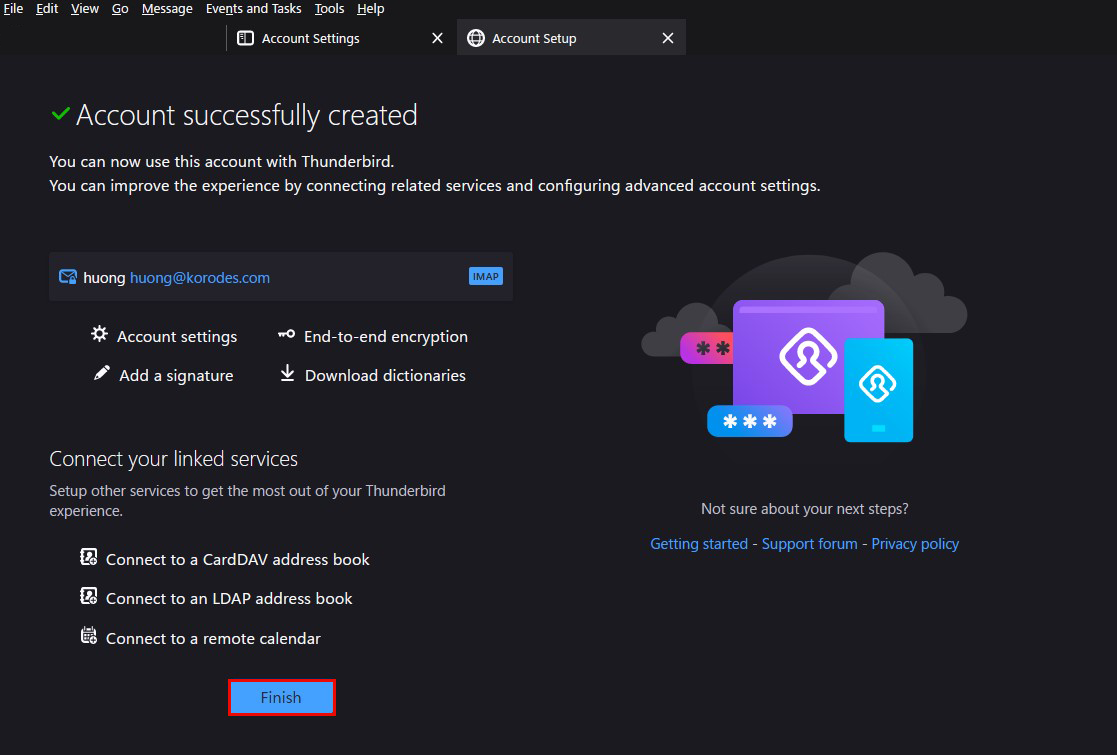
If the next screen appears, success!
3. Mail Server : Postfix + Clamav + Amavisd
Set up Postfix and Clamav to work together to scan incoming and outgoing mail in real time.
3.1 Amavisd & Clamav Server Install
|
1 2 3 4 |
# zypper -n install amavisd-new spamassassin # systemctl start clamd # systemctl enable clamd Created symlink /etc/systemd/system/multi-user.target.wants/clamd.service → /usr/lib/systemd/system/clamd.service. |
3.2 Configure Amavisd
①Configuration File Editing
|
1 2 3 4 5 6 7 8 |
# vi /etc/amavisd.conf # Line 23:Change to your domain name $mydomain = 'korodes.com'; # Line 155:Uncomment and change to own host name $myhostname = 'mail.korodes.com'; # Line 157,158:Uncomment $notify_method = 'smtp:[127.0.0.1]:10025'; $forward_method = 'smtp:[127.0.0.1]:10025'; |
②Startup and Auto-Run Settings
|
1 2 3 4 5 |
# sa-update # systemctl start amavis spamd # systemctl enable amavis spamd Created symlink /etc/systemd/system/multi-user.target.wants/amavis.service → /usr/lib/systemd/system/amavis.service. Created symlink /etc/systemd/system/multi-user.target.wants/spamd.service → /usr/lib/systemd/system/spamd.service. |
3.3 Postfix Configuration
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
# vi /etc/postfix/master.cf # Add the following to the last line smtp-amavis unix - - n - 2 smtp -o smtp_data_done_timeout=1200 -o smtp_send_xforward_command=yes -o disable_dns_lookups=yes 127.0.0.1:10025 inet n - n - - smtpd -o content_filter= -o local_recipient_maps= -o relay_recipient_maps= -o smtpd_restriction_classes= -o smtpd_client_restrictions= -o smtpd_helo_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o mynetworks=127.0.0.0/8 -o strict_rfc821_envelopes=yes -o smtpd_error_sleep_time=0 -o smtpd_soft_error_limit=1001 -o smtpd_hard_error_limit=1000 |
|
1 2 3 |
# vi /etc/postfix/main.cf # Add the following to the last line content_filter=smtp-amavis:[127.0.0.1]:10024 |
|
1 |
# systemctl restart postfix |
3.4 Check with Thunderbird
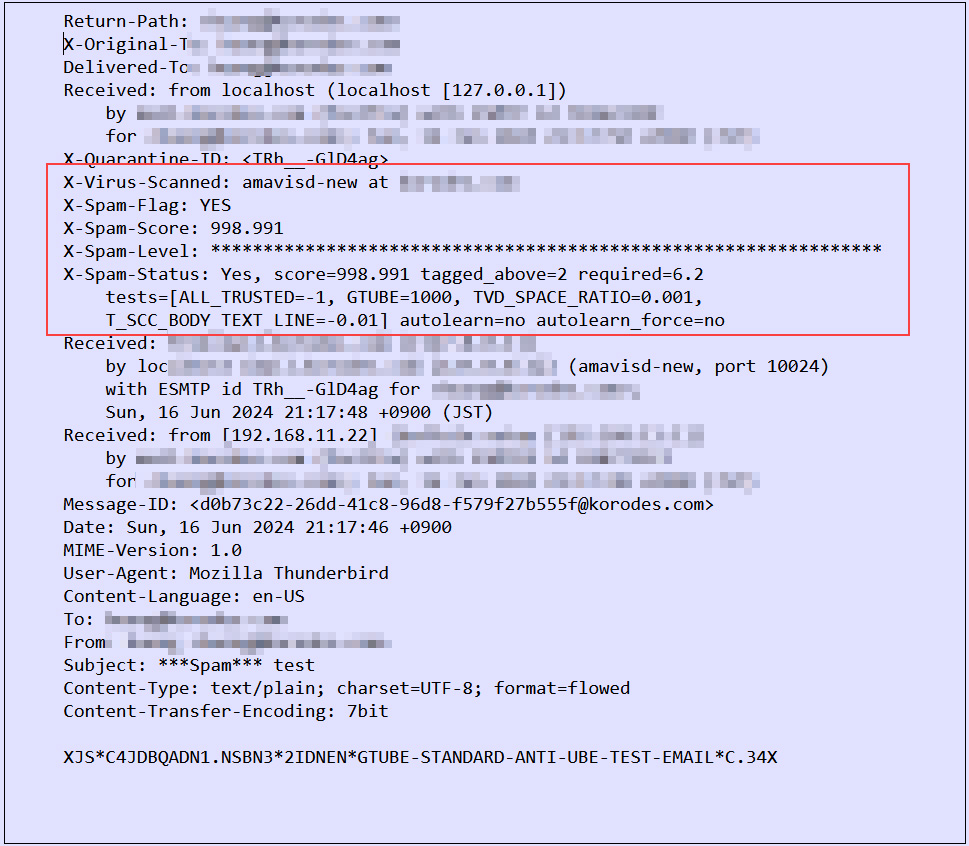
When you send an e-mail to yourself with the following contents in the body, if you see "spam" in the list of received e-mails and the following message in the header of the e-mail, you have succeeded.
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X
4.virus scan script substitution
Set up a notification to a specified e-mail address after virus check scan.
① Create virus scan exclusion directory list
|
1 2 3 4 5 |
# cd /srv/www/system/ # vi clamscan.exclude /sys/ /proc/ /.snapshots ← openSUSE is configured to take a large number of snapshots, so if you don't need them, set |
②Disable existing script and create new virus scan script
|
1 2 3 |
# cd /srv/www/system/ # mv clamscan.sh clamscan.sh_bak # vi clamscan.sh |
Contents of new "clamscan.sh"
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
#!/bin/bash PATH=/usr/bin:/bin MAILTO="<Any email address>" # excludeopt setup excludelist=/srv/www/system/clamscan.exclude if [ -s $excludelist ]; then for i in `cat $excludelist` do if [ $(echo "$i"|grep \/$) ]; then i=`echo $i|sed -e 's/^\([^ ]*\)\/$/\1/p' -e d` excludeopt="${excludeopt} --exclude-dir=^$i" else excludeopt="${excludeopt} --exclude=^$i" fi done fi # signature update freshclam 2>&1 > /dev/null # virus scan CLAMSCANTMP=`mktemp` #clamscan --recursive --remove ${excludeopt} / > $CLAMSCANTMP 2>&1 clamscan --recursive ${excludeopt} / > $CLAMSCANTMP 2>&1 [ ! -z "$(grep FOUND$ $CLAMSCANTMP)" ] && \ # report mail send grep FOUND$ $CLAMSCANTMP | mail -s "Virus Found in `hostname`" $MAILTO rm -f $CLAMSCANTMP |
|
1 |
# chmod 700 clamscan.sh |
You will now be notified by email if there is a virus. If there is no virus, you will not be notified.

