Contents
SSH public key cipher setting
1.Create a key pair
Create a public/private key pair for a user connecting to a Linux server using OpenSSH.
Use ssh-keygen to create the key pair.
The creation of a public/private key pair must be done as a user with remote login privileges.
If you do not specify the destination and file name, id_ed25519 and id_ed25519.pub will be created in /home/(user name)/.ssh/. On the way, enter the password for the key.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
# su – <user name> $ ssh-keygen -t ed25519 Generating public/private ed25519 key pair. Enter file in which to save the key (/home/huong/.ssh/id_ed25519): Created directory '/home/huong/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/huong/.ssh/id_ed25519. Your public key has been saved in /home/huong/.ssh/id_ed25519.pub. The key fingerprint is: SHA256:nIJyadLBDmXJoozL8K2TGA6yXzPSV181nbT3R3+QSVE huong@localhost.localdomain The key's randomart image is: +--[ED25519 256]--+ | .o. o+E| | .+o ..+o| |o...o *o+| |+. + + . . . ++| |ooo.B . S . =| |=..*. o . . o| |++.o= . . | |o.+o + | | ... | +----[SHA256]-----+ |
|
1 2 3 |
$ cat ~/.ssh/id_ed25519.pub >> ~/.ssh/authorized_keys $ chmod 600 ~/.ssh/authorized_keys $ chmod 700 ~/.ssh/ |
2.Private Key Login Settings
|
1 2 3 4 5 6 7 |
$ su - # vi /etc/ssh/sshd_config Delete "#" at the beginning of the line per line 49 Before change) #PubkeyAuthentication yes After the change) PubkeyAuthentication yes |
SSH restart
|
1 |
# systemctl restart sshd.service |
Copy the private key to the client PC (using WinSCP) Configure WinSCP settings
①Start WinSCP, set the following in "New Site", and click "Save".
Host name : Server IP address
Port number : SSH port number
User name : User name
Password : User password
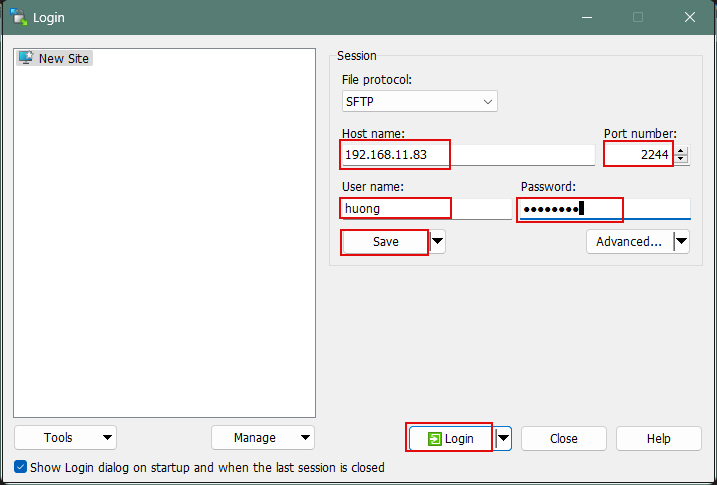
Name the connection with any name.
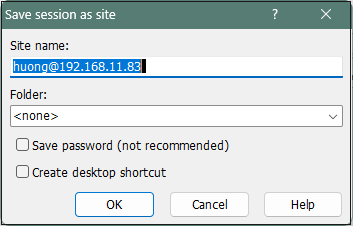
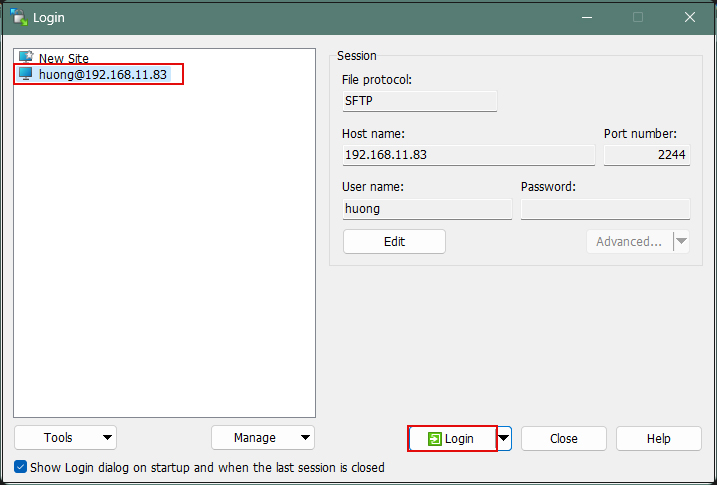
Click "Login" to return to the following screen.
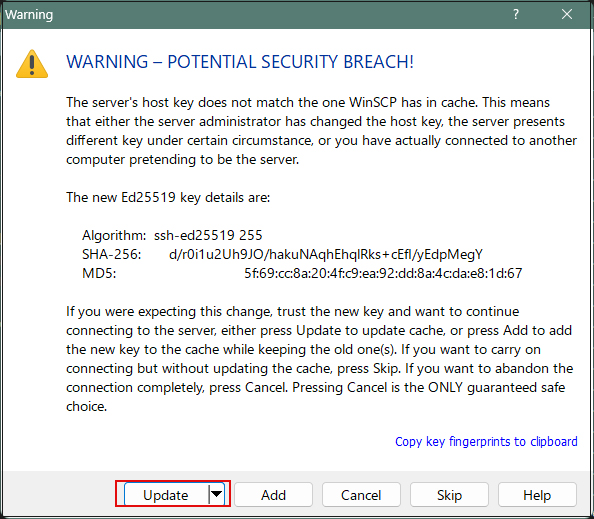
If the following screen appears, click "Update".
In the following screen, enter the user's password in the "Pasword" field.
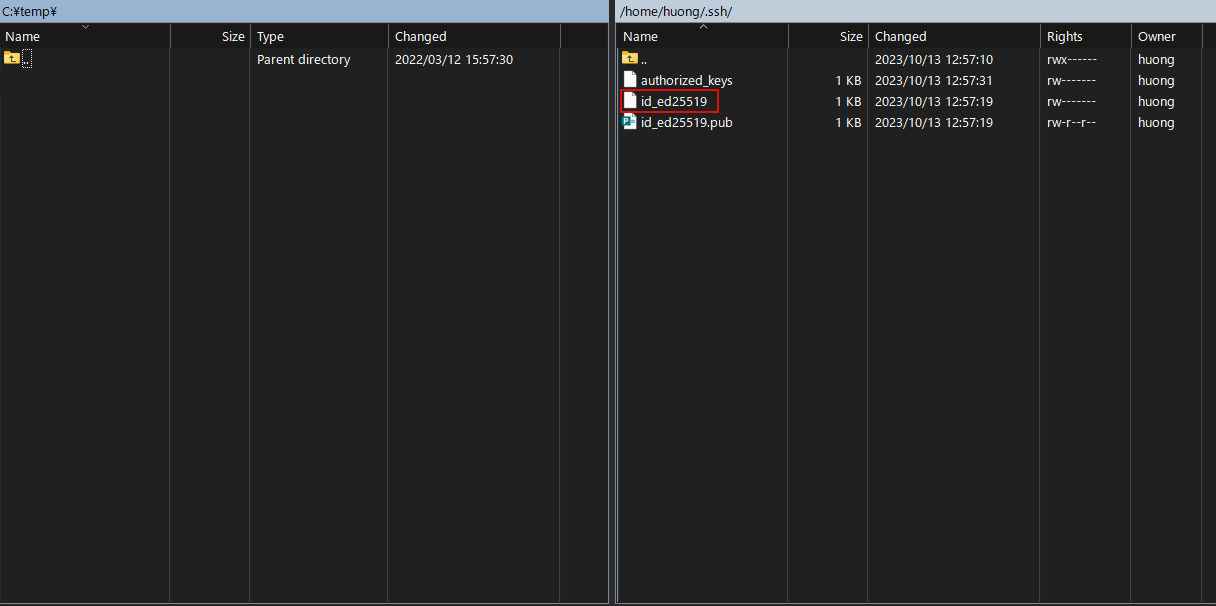
The following screen will appear. Copy id_ed25519 in the /home/user/.ssh directory to any location on the windows side (select id_ed25519 and drag & copy it to the left side).
3.Change to log in only with private key
|
1 2 3 4 5 |
# vi /etc/ssh/sshd_config ■Per Line 69 Add "PasswordAuthentication no" under "#PasswordAuthentication yes" #PasswordAuthentication yes PasswordAuthentication no |
SSH restart
|
1 |
# systemctl restart sshd.service |
4.Creating a private key using PuTTYgen
Launch Winscp and start run PuTTYgen from Tools
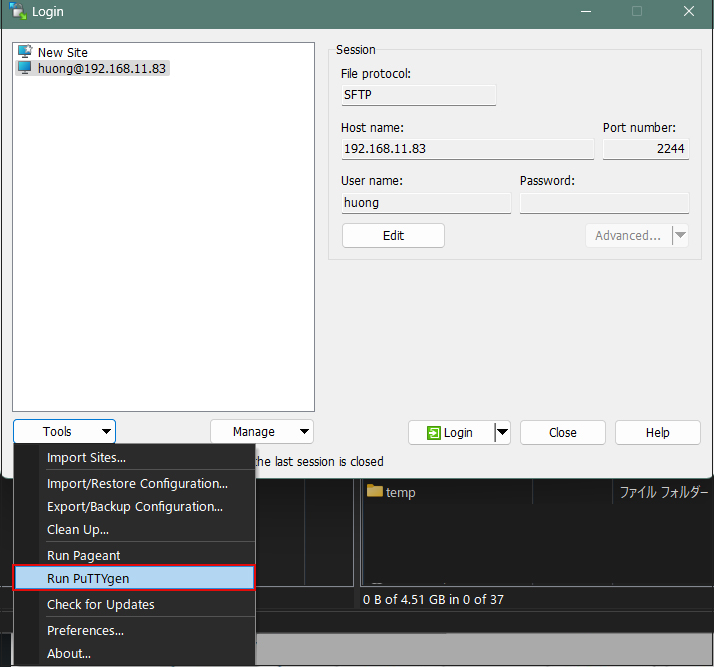
Click Load [ Open File Dialog ], change the file type to [ All Files (. Change the file type to [ All Files (. *) ] and load the private key id_ed25519 transferred from the Linux server.
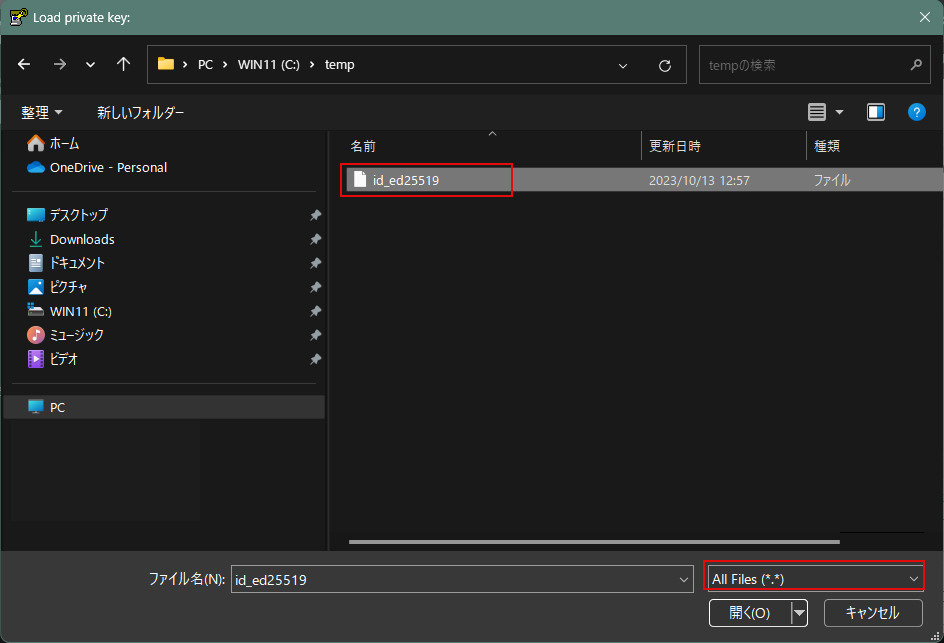
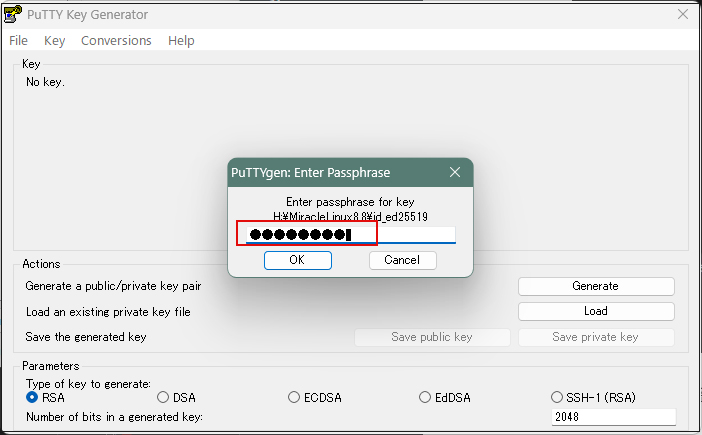
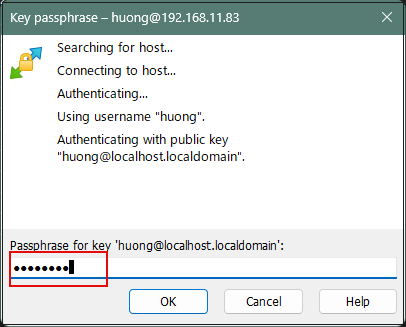
Enter the passphrase you entered when you created the private key on the server side
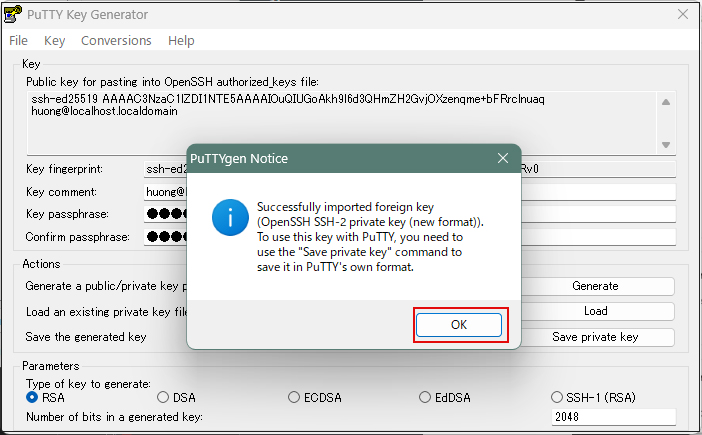
Click the [ OK ] button when the following appears
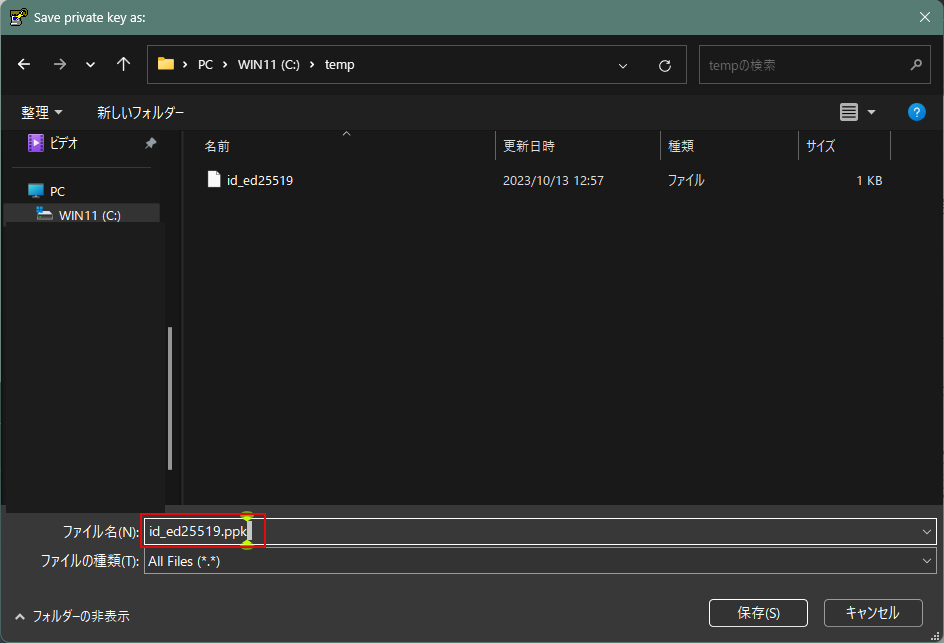
Click the [ Save private key ] button to save the private key.
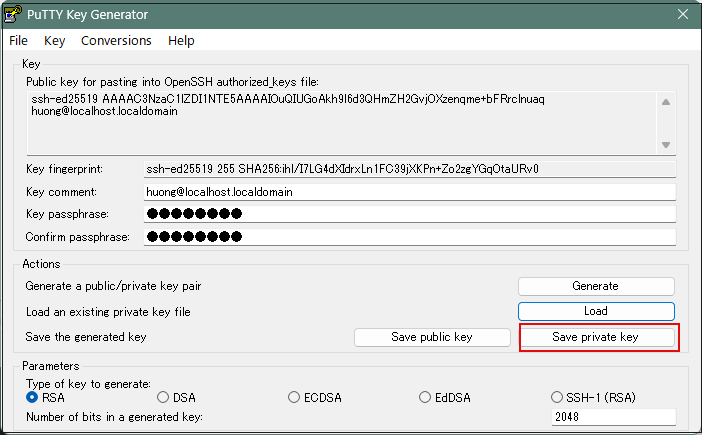
Save it here as id_ed25519.ppk (in Windows).
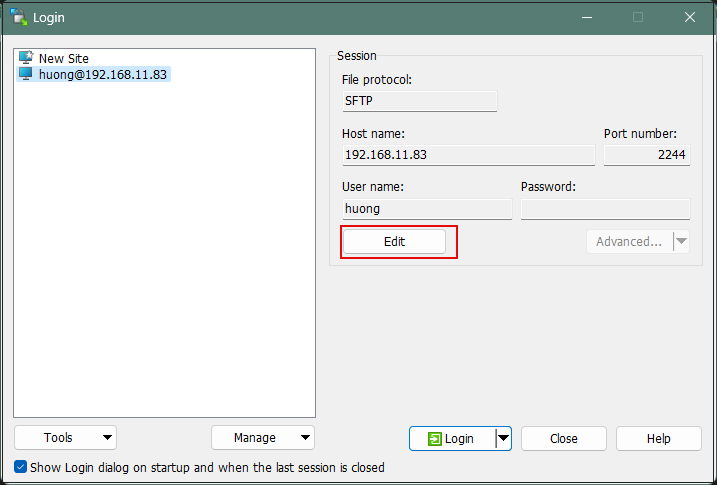
Select the appropriate server and click "Edit"
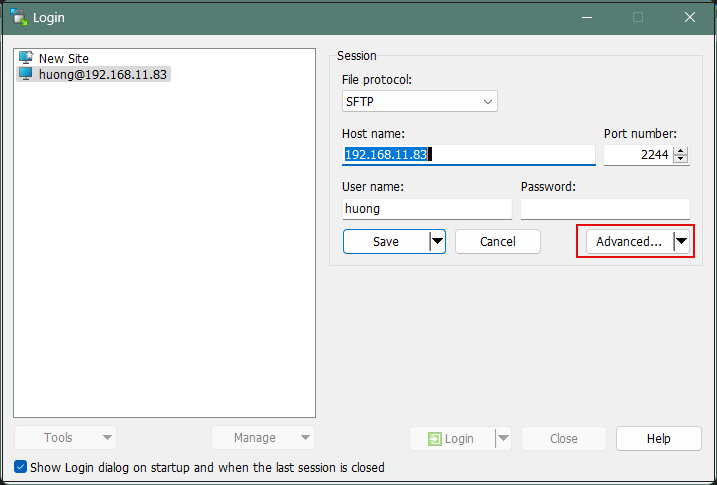
Click on "Advanced"
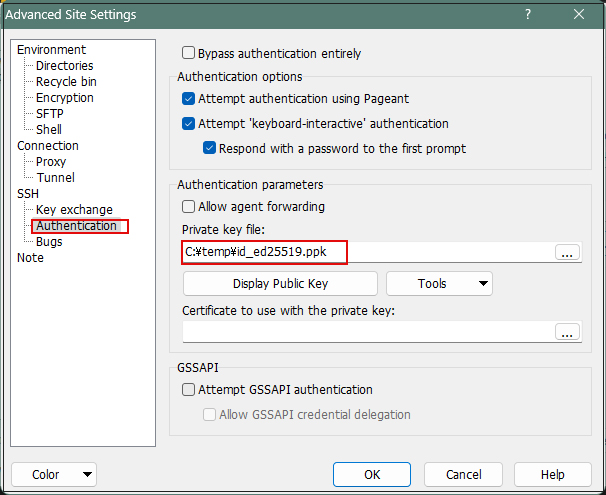
Open the "Authentication" menu and specify "id_ed25519.ppk" saved in Windows for "Private key file
Click "Save"
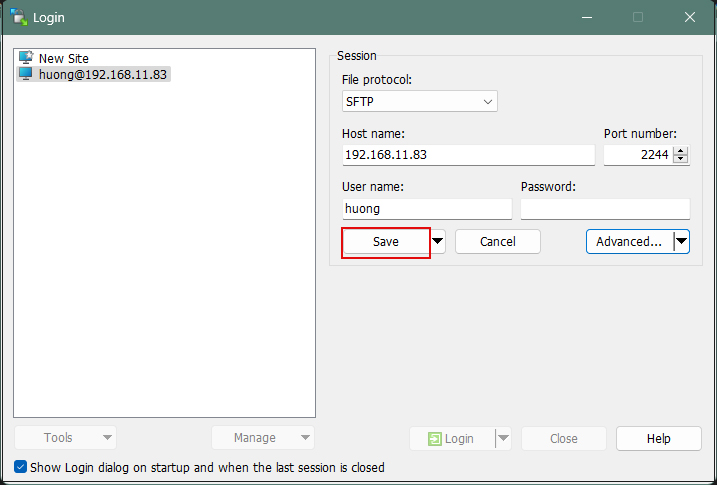
Click on "Login"
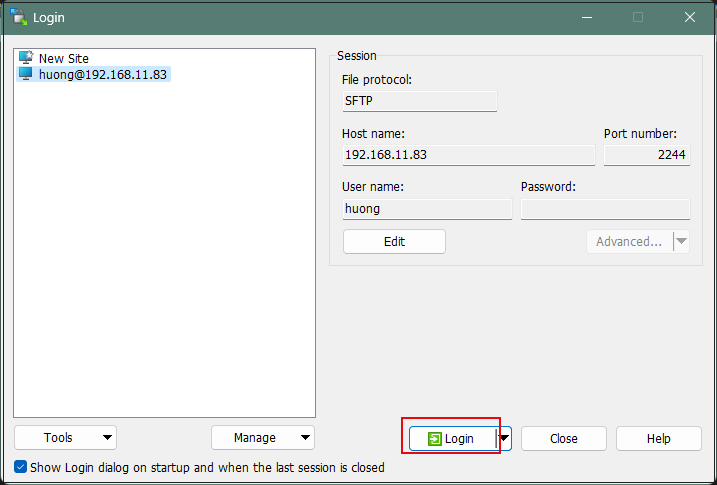
The password is the password set in "Creating a public and private key pair" above
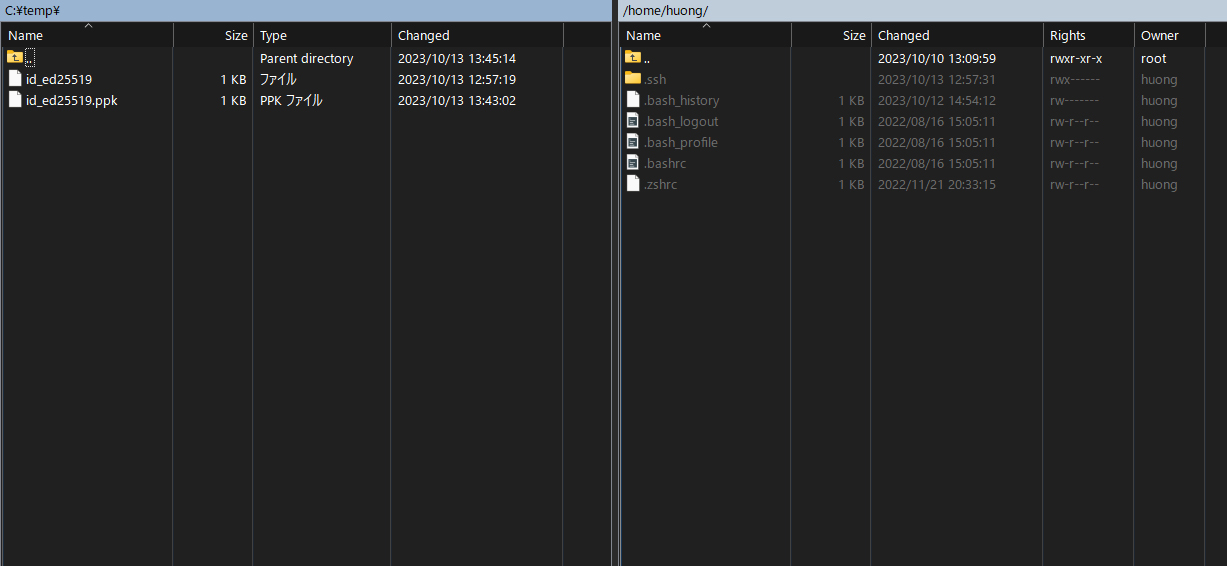
When successfully connected, the server side is displayed on the right and the Windows side on the left as shown below.
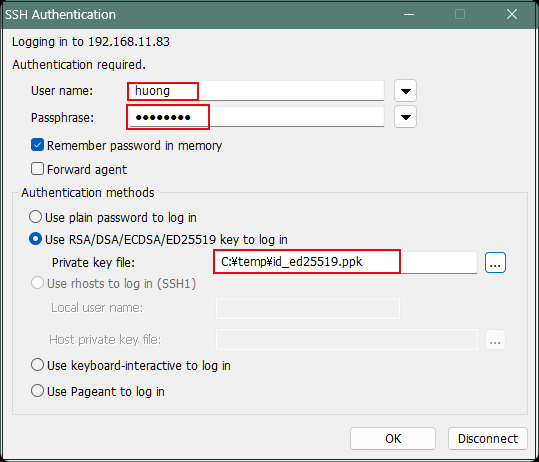
When connecting with Tera Term
"Use RSA/DSA/ECDSA/…"
Specify "id_ed25519.ppk" saved in windows
This completes the security configuration for the SSH service.

