Contents
1. Obtain a certificate (Let's Encrypt)
1.1 advance preparation
①Enable mod_ssl
|
1 |
# a2enmod ssl |
②Install client tool to obtain Let's Encrypt certificate
|
1 |
# apt -y install certbot |
1.2 Obtaining a Let's Encrypt Certificate
It is assumed that a web server such as Apache httpd or Nginx is running.
If the Web server is not running on the server where the work is to be performed, follow the steps ※ below.
It is also assumed that the server on which the work is to be performed (the server with the FQDN from which you want to obtain the certificate) is accessible from the Internet at port 80.
|
1 |
# certbot certonly --webroot -w /var/www/html/<FQDN> -d <FQDN> |
#Use the directory under the public directory of the running Web server as a temporary area for authentication by specifying [--webroot].
# -w [document root] -d [FQDN from which you want to obtain a certificate] # FQDN (Fully Qualified Domain Name) : Hostname. Domain name without abbreviation
#Document root is the one for the appropriate host definition if there are multiple host definitions in the virtual host
# Registration of e-mail address and agreement to terms of use are required for the first time only.
# Specify an email address to receive
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
Saving debug log to /var/log/letsencrypt/letsencrypt.log Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [Mail address] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf. You must agree in order to register with the ACME server. Do you agree? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: y - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing, once your first certificate is successfully issued, to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: y Account registered. Requesting a certificate for <FQDN> Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/<FQDN>/fullchain.pem Key is saved at: /etc/letsencrypt/live/<FQDN>/privkey.pem This certificate expires on 2024-05-12. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can try again later by visiting https://act.eff.org. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
Success when displaye "Congratulations! Your certificate and chain have been saved."
# The following certificate is obtained under [/etc/letsencrypt/live/<FQDN>/] as described in the message
# cert.pem ⇒ SSL server certificate (including public key)
# chain.pem ⇒ intermediate certificate
# fullchain.pem ⇒ File containing cert.pem and chain.pem combined
# privkey.pem ⇒ private key
※ Obtaining a Let's Encrypt certificate when the web server is not running
# Renew all certificates with an expiration date of less than 30 days
# If you want to renew regardless of the number of days remaining on the expiration date, specify [--force-renewal] as well
|
1 |
# certbot certonly --standalone -d <FQDN> |
Renewing certificates already obtained
# Renew all certificates with an expiration date of less than 30 days
# If you want to renew regardless of the number of days remaining on the expiration date, specify [--force-renewal] as well
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# certbot [--force-renewal] renew Saving debug log to /var/log/letsencrypt/letsencrypt.log - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Processing /etc/letsencrypt/renewal/[FQDN].conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Renewing an existing certificate for [FQDN] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations, all renewals succeeded: /etc/letsencrypt/live/[FQDN]/fullchain.pem (success) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
2. SSL/TLS (Let's Encrypt) configuration for Apache2
①Edit Apache2 SSL-related configuration files
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# cd /etc/apache2/sites-available/ # cp default-ssl.conf hoge.com-ssl.conf ← hoge.com-ssl(May be any name) # vi hoge.com-ssl.conf # Line 2:Administrator address change ServerAdmin <Administrator address>> # Line 4:change DocumentRoot /var/www/html/<FQDN>/ # Line 12,13:change ErrorLog ${APACHE_LOG_DIR}/<FQDN>.error.log CustomLog ${APACHE_LOG_DIR}/<FQDN>.access.log combined # Linne 31,32:Change to the certificate obtained in [1]. SSLCertificateFile /etc/letsencrypt/live/<FQDN>/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/<FQDN>/privkey.pem # Per Line43:change to the chain file obtained in [1]. SSLCertificateChainFile /etc/letsencrypt/live/<FQDN>/chain.pem |
②Reflecting and activating the configuration file
|
1 2 3 4 5 6 7 8 |
# a2ensite hoge.com-ssl.conf Enabling site hoge.com-ssl.conf. To activate the new configuration, you need to run: systemctl reload apache2 # Default Disable # a2dissite default-ssl.conf # systemctl restart apache2 |
③http to https redirect
|
1 |
# a2enmod rewrite |
One of the following methods
|
1 2 3 4 5 6 7 8 9 10 |
1. How to create .htaccess files Create .htaccess in /var/www/html/<FQDN>/ and fill in the following RewriteEngine on RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L] 2.vHow to fill in vhost-yourdomain.conf RewriteEngine on RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L] |
④Reflection of settings and startup
|
1 |
# a2ensite vhost-yourdomain.conf |
|
1 |
# a2enmod ssl |
|
1 2 |
Restart Apache # systemctl restart apache2 |
3. SSL/TLS (Let's Encrypt) settings on the mail server
3.1 Obtaining a certificate for the mail server
Obtain a certificate for the mail server, but it cannot be obtained in the same way as above, so the following with the "--standalone" option fails.
|
1 |
# certbot certonly --standalone -d mail.<domain name> |
If I stop the web server once and then do it, it succeeds as follows
|
1 2 |
# systemctl stop apache2.service # certbot certonly --standalone -d mail.<domain name> |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
Saving debug log to /var/log/letsencrypt/letsencrypt.log Requesting a certificate for mail.[Domain name] Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/mail.[Domain name]/fullchain.pem Key is saved at: /etc/letsencrypt/live/mail.[Domain name]/privkey.pem This certificate expires on 2024-05-12. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
3.2 Postfix Configuration
|
1 2 3 4 5 6 7 8 |
# vi /etc/postfix/main.cf # Add to the last line smtpd_use_tls = yes smtp_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_cert_file = /etc/letsencrypt/live/mail.<domain name>/fullchain.pem smtpd_tls_key_file = /etc/letsencrypt/live/mail.<domain name>/privkey.pem smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache |
|
1 2 3 4 5 6 7 8 9 10 11 12 |
# vi /etc/postfix/master.cf # Per Line 21-24 : Uncomment submission inet n - y - - smtpd -o syslog_name=postfix/submission #-o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes # Add to last line smtps inet n - y - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes |
3.3 Dovecot Settings
|
1 2 3 4 5 6 |
# vi /etc/dovecot/conf.d/10-ssl.conf # Line 6:change ssl = yes # Line 12,13:Uncomment and specify certificate/key file ssl_cert = </etc/letsencrypt/live/mail.<domain name>/fullchain.pem ssl_key = </etc/letsencrypt/live/mail.<domain name>/privkey.pem |
Allow Port 587 in UFW
|
1 2 |
# ufw allow 587/tcp # ufw reload |
|
1 |
# systemctl restart postfix dovecot |
3.4 Thunderbird Settings
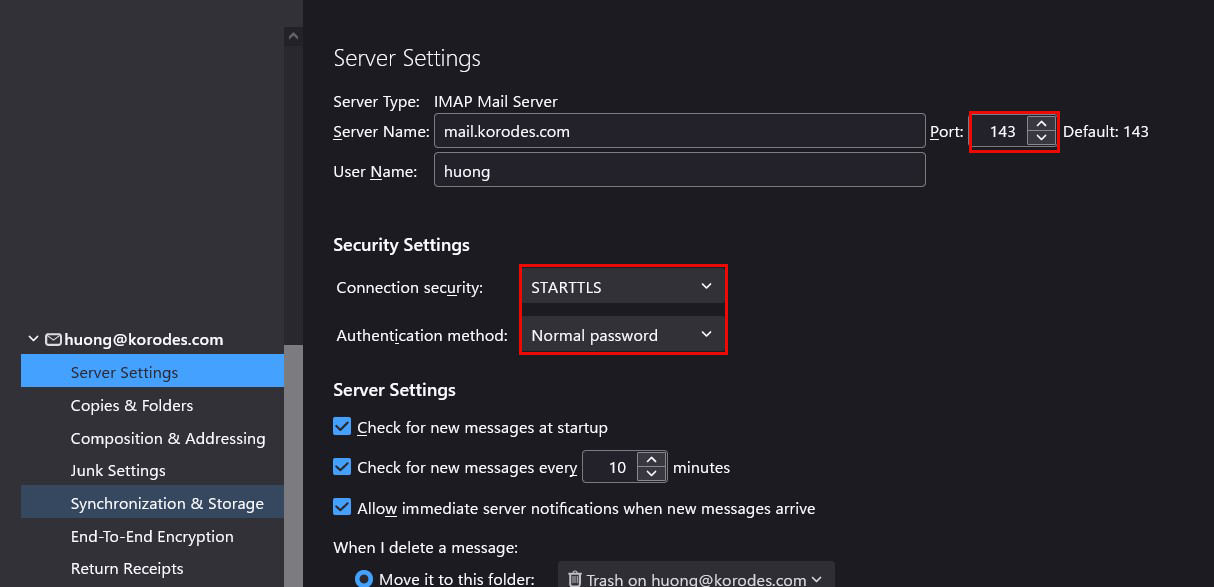
Receiving server
Port : 143
Connection security : STARTTLS
Authentication method : Normal password
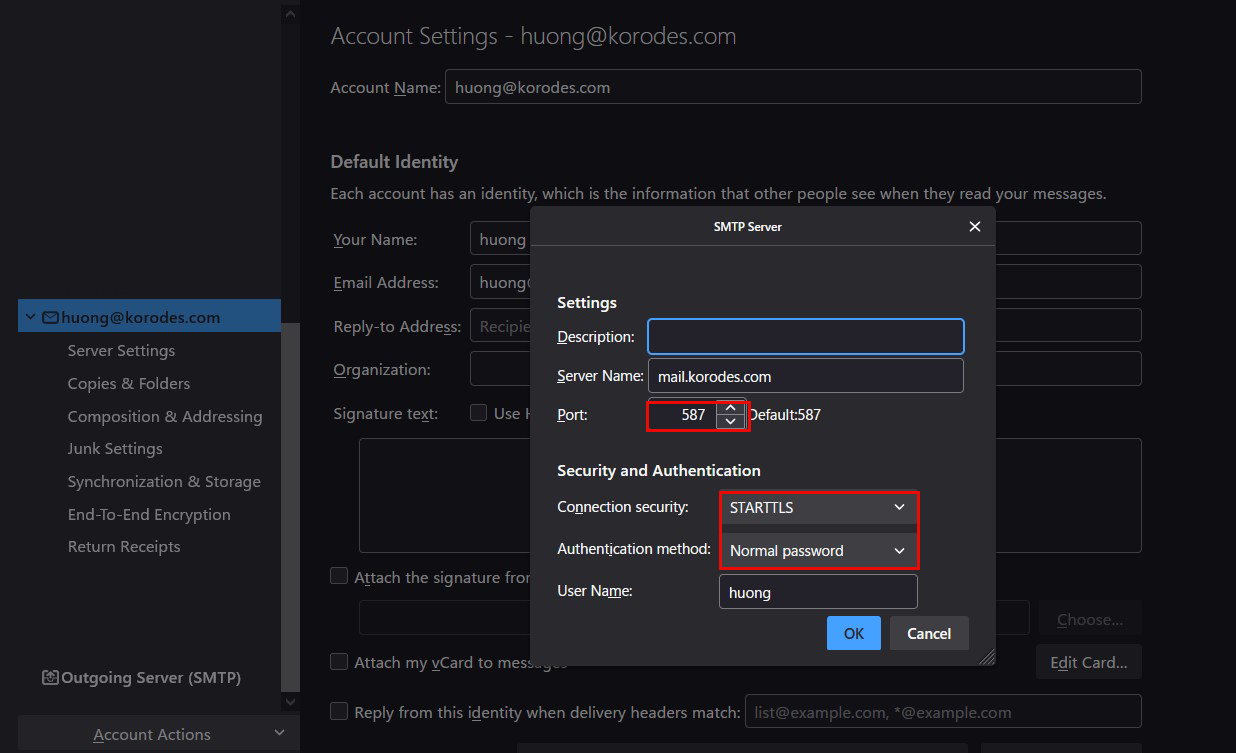
Sending server
Port : 587
Connection security : STARTTLS
Authentication method : Normal password