Create a private key for the client and a public key for the server to allow login with key pair authentication
Contents
1.key pair creation
Create a public/private key pair for a user connecting to the Linux server using OpenSSH.
Use ssh-keygen to create key pairs.
Creation of public/private key pairs is performed with remote login user privileges.
If you do not specify the creation destination and file name, id_ecdsa and id_ecdsa.pub will be created in /home/(user name)/.ssh/.
On the way, also enter the password for the key.
key pair creation
|
1 |
# su - suse |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
suse@Lepard:~> ssh-keygen -t ecdsa Generating public/private ecdsa key pair. Enter file in which to save the key (/home/suse/.ssh/id_ecdsa): Enter Created directory '/home/suse/.ssh'. Enter passphrase (empty for no passphrase): Any password Enter same passphrase again: Same password again Your identification has been saved in /home/suse/.ssh/id_ecdsa Your public key has been saved in /home/suse/.ssh/id_ecdsa.pub The key fingerprint is: SHA256:njRHwWiZLd3e7cmiZDbipHa62zIpWtuNCm0S4pYeAQ4 suse@Lepard The key's randomart image is: +---[ECDSA 256]---+ | B.. | | * +.. | |E . ... . . | |+ . . . .| | + . S . ...| |. + o o * = . o.| | = o + B = o . | |o . =.o*+o . | | . ..o+*Bo | +----[SHA256]-----+ |
|
1 2 3 4 |
suse@Lepard:~> ll ~/.ssh total 8 -rw------- 1 suse users 557 Sep 9 21:58 id_ecdsa -rw-r--r-- 1 suse users 173 Sep 9 21:58 id_ecdsa.pub |
|
1 2 |
suse@Lepard:~>cat ~/.ssh/id_ecdsa.pub >> ~/.ssh/authorized_keys suse@Lepard:~>chmod 600 ~/.ssh/authorized_keys |
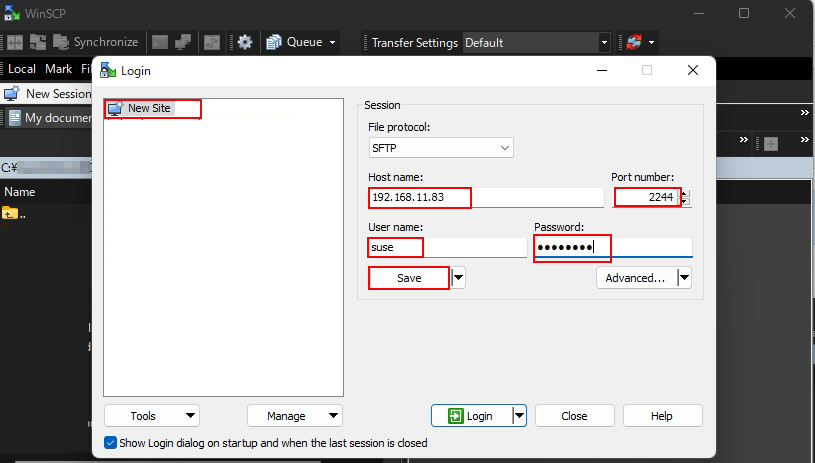
Start winSCP
New Site click
Host name : server IP address
Port number : SSH port number
User name : login user name
Password : Password for the above user
Save click
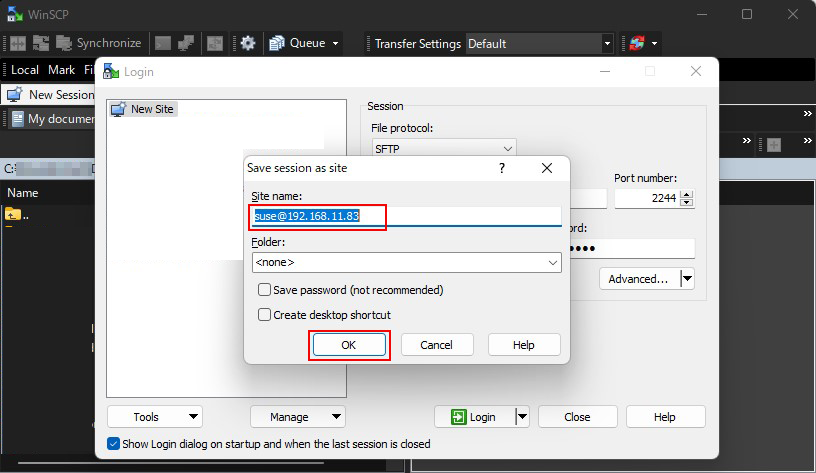
OK click
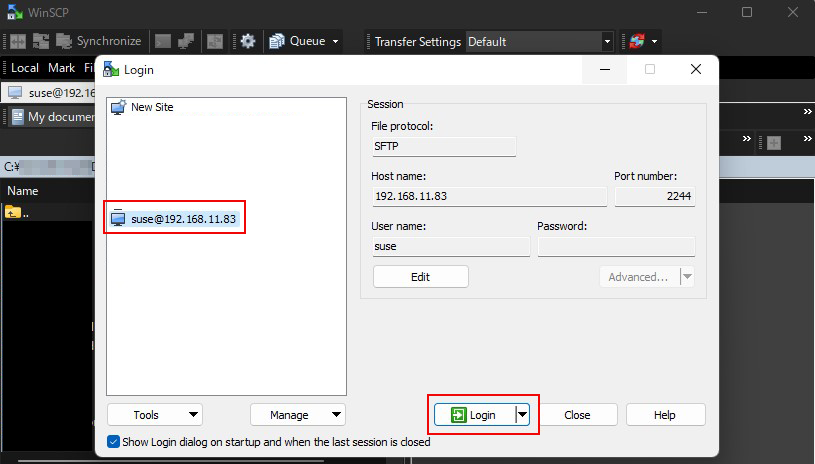
OK click
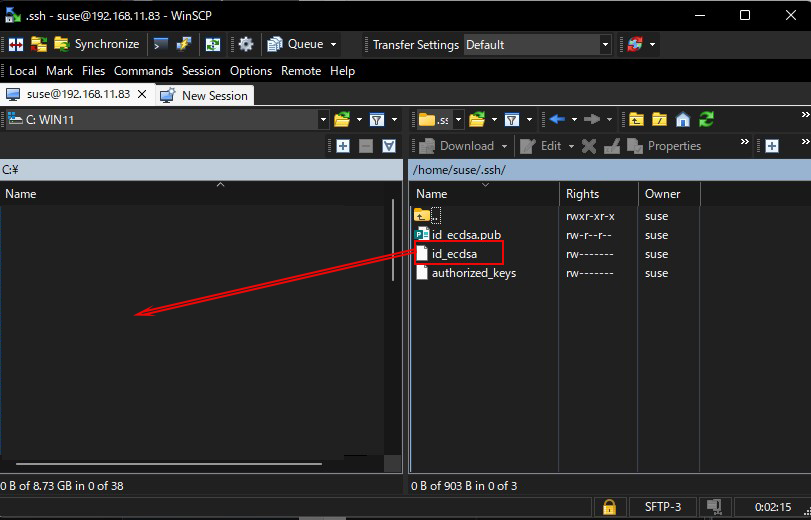
2. Edit SSH settings
2.1 Editing Configuration Files
If you use key authentication, you can make the environment more secure by disabling password authentication on the SSH server side as follows. This time, use su - to become root instead of a general user.
|
1 2 3 4 5 |
# vi /etc/ssh/sshd_config # Line 58,62:Uncomment and change to password verification disabled. PasswordAuthentication no ChallengeResponseAuthentication no |
|
1 |
# systemctl restart sshd.service |
2.2 How to connect with Tera Term
Open TeraTerm and click "New Connection" from the "File" menu.
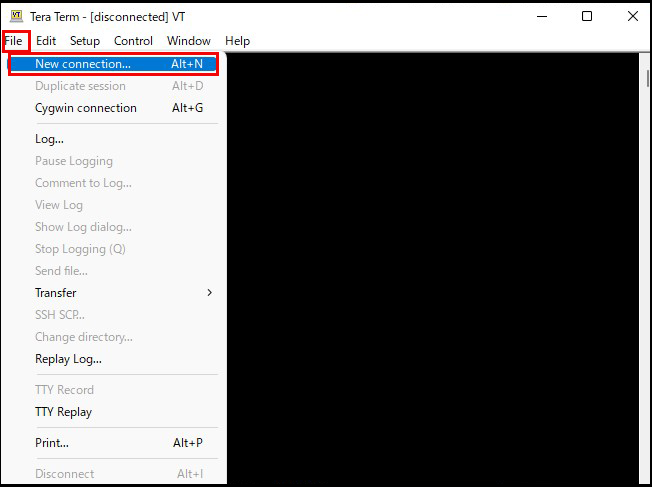
Host : server IP address TCP port : SSH Port number
OK Click
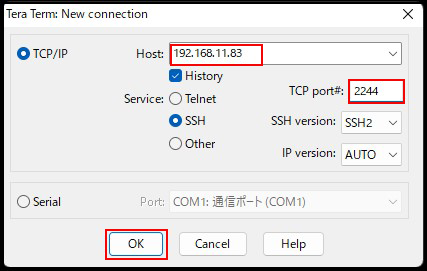
User name : login user name
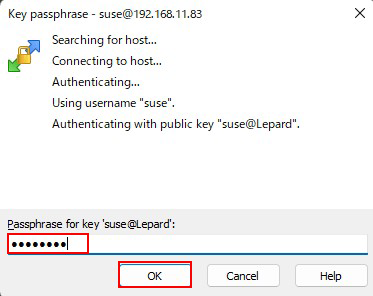
Passphrase : Password set when creating private key id_ecdsa
Use RSA/DSA/ECDSA/ED25519 key to log in : check
Private key file: Set "id_ecdsa" saved in Windows
OK click
2.3 Creating a private key using PuTTYgen
Start Winscp and launch Run PuTTYgen from Tools
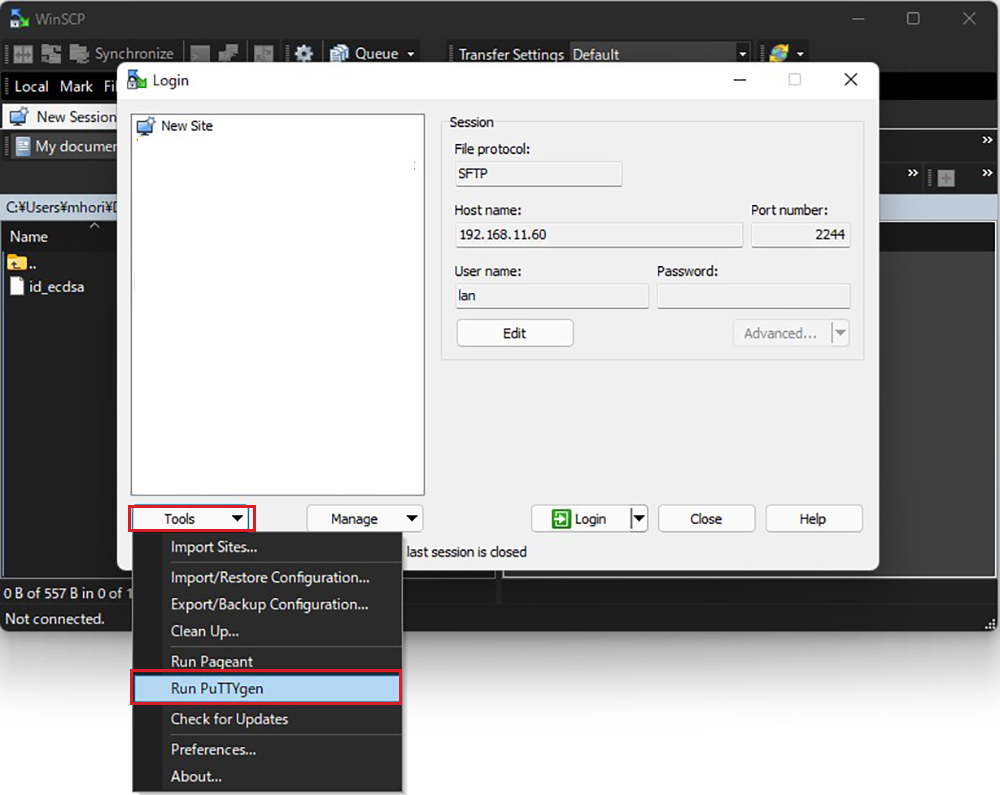
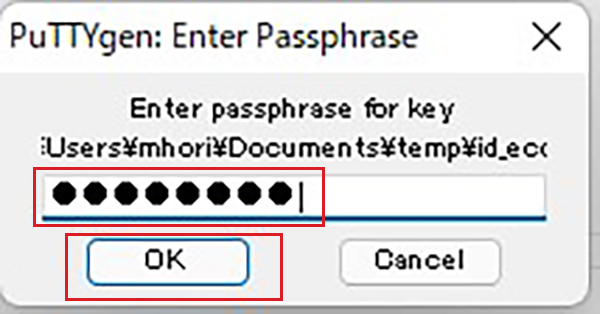
Click Load [ Open File Dialog ], change the file type to [ All Files (*. *) ] and load the private key id_ecdsa transferred from the Linux server.
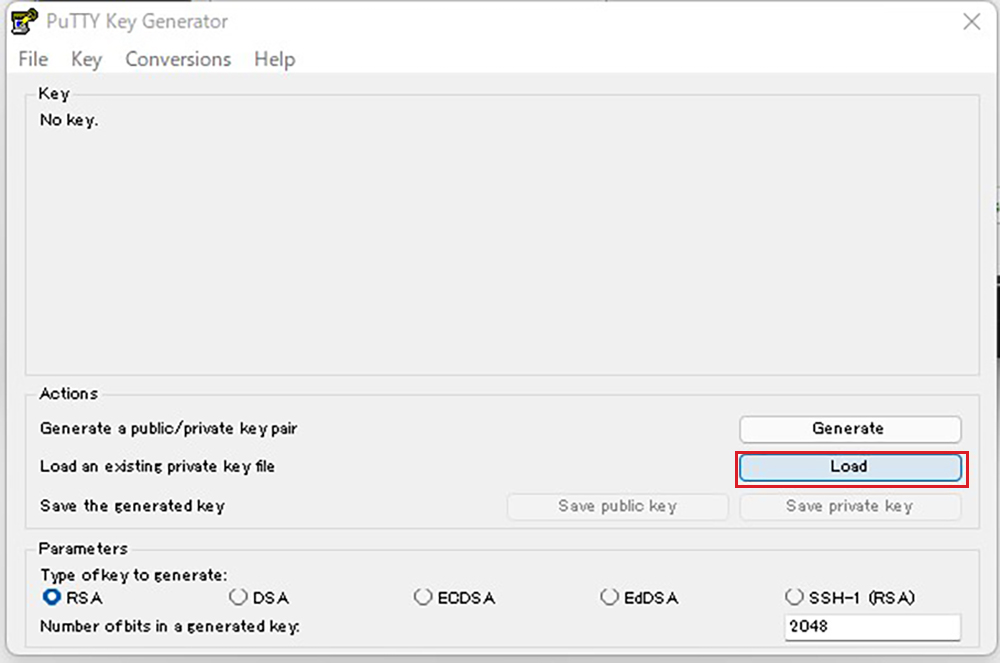
Passphrase : Password set when creating private key id_ecdsa
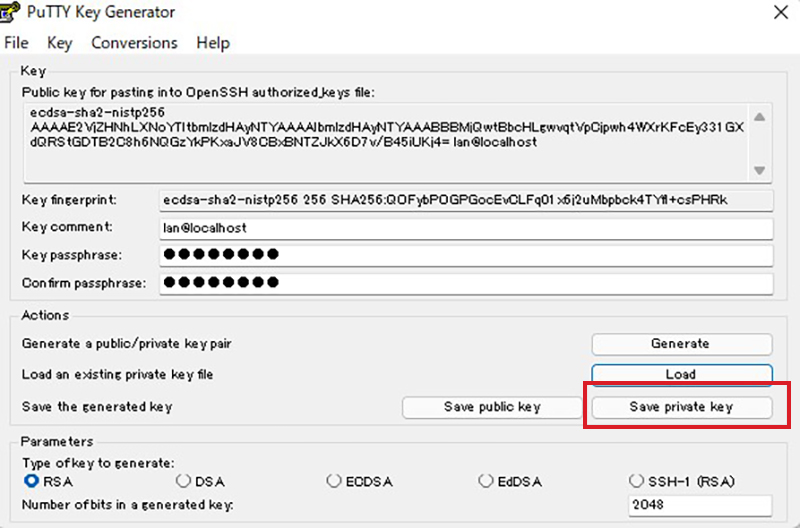
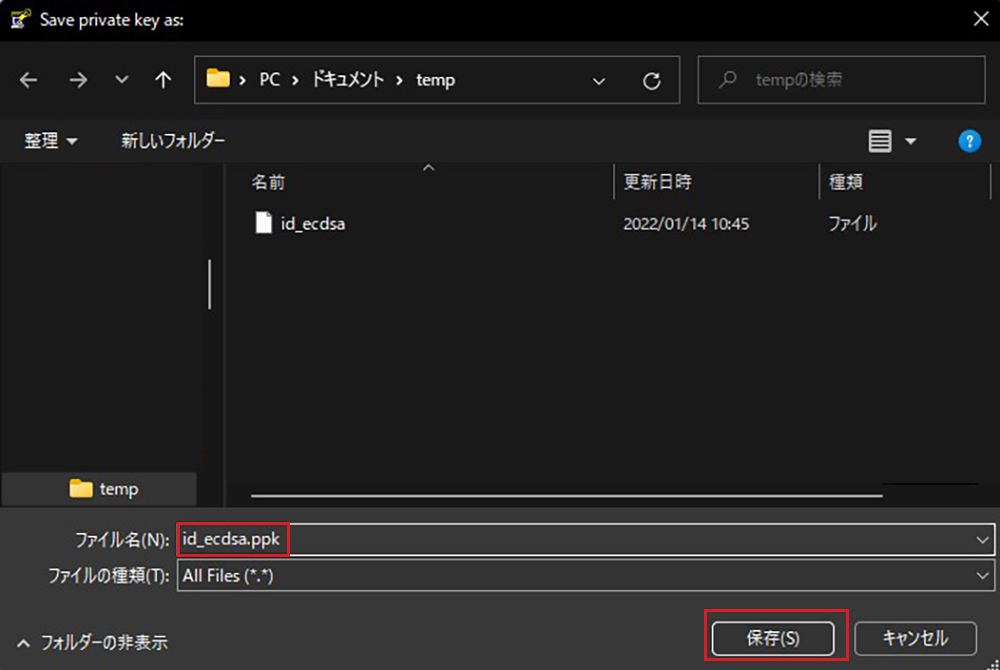
Click on "Save private key"
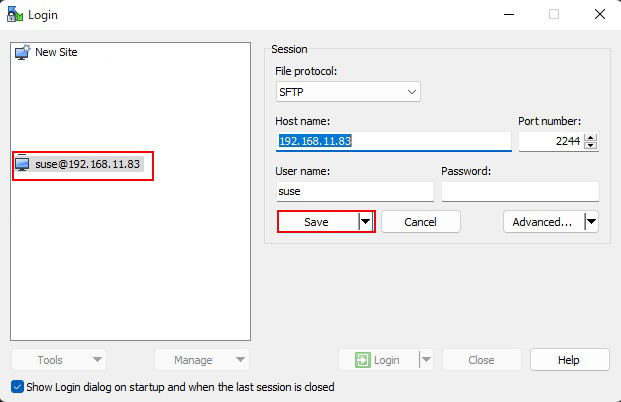
Save the file as ".ppk" extension with the name "id_ecdsa.ppk" in the same place as "id_ecdsa" saved earlier on the Windows side.
Check the appropriate server and click Save.
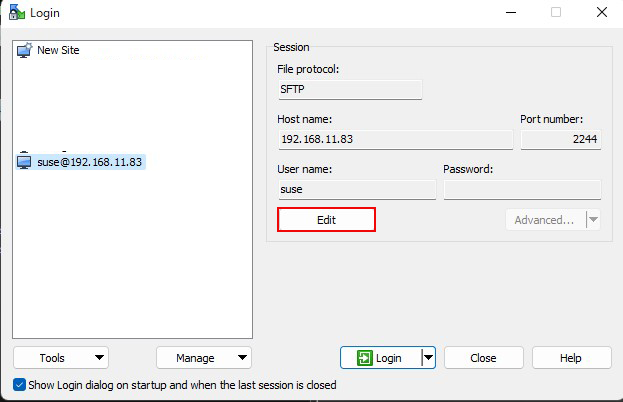
Click "Edit"
Click "Advabced..."
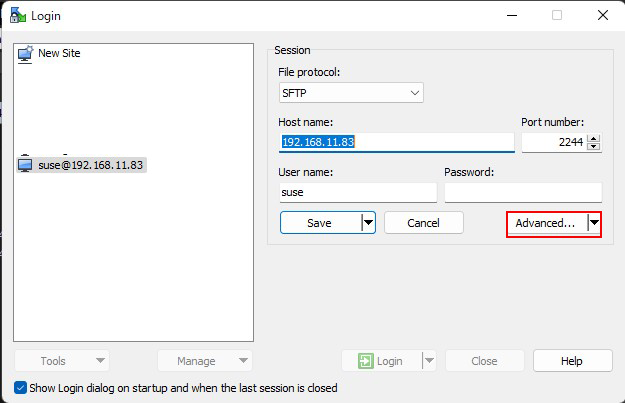
Open the "Authentication" menu and specify "id_ecdsa.ppk" saved in Windows for "Private key file"
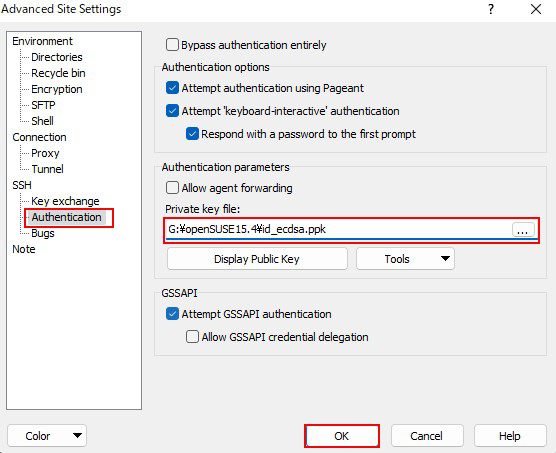
Click "Login" after "Save"

In the Password field, enter the password defined in the first public key course you created.