Install ClamAV on FreeBSD 13 and link it with Amavis against Postfix.
ClamAV is anti-virus software.
We will proceed on the assumption that you have already implemented Postfix.
Before proceeding, update the Ports Collection.
|
1 |
# portsnap fetch update |
1. ClamAV
1.1 Install
|
1 2 |
# cd /usr/ports/security/clamav # make install clean |
Each option is installed by default for now
1.2 Configuration File Editing
①Edit clamd.conf
Run ClamAV as root user
|
1 2 3 4 5 6 7 8 9 10 |
# chmod 640 /usr/local/etc/clamd.conf # vi /usr/local/etc/clamd.conf Line 35 : Uncomment #LogTime yes LogTime yes Line 226 : Comment out User clamav #User clamav |
➁Edit freshclam.conf
Settings about virus pattern files
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# chmod 640 /usr/local/etc/freshclam.conf # vi /usr/local/etc/freshclam.conf Line 59 : change DatabaseOwner clamav ↓ DatabaseOwner root Line 75 : Mirror site added DatabaseMirror database.clamav.net ↓ DatabaseMirror database.clamav.net DatabaseMirror db.local.clamav.net DatabaseMirror db.jp.clamav.net DatabaseMirror db.us.clamav.net Line 121 : Uncomment #Checks 24 Checks 24 |
1.3 Virus database update
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
# freshclam ClamAV update process started at Sun Jul 30 16:24:12 2023 daily database available for download (remote version: 26984) Time: 3.4s, ETA: 0.0s [========================>] 58.80MiB/58.80MiB WARNING: ******* RESULT 200, SIZE: 61651705 ******* Testing database: '/var/db/clamav/tmp.f72e85ffba/clamav-646abc997b2bb3ce93f906a9f4b8a601.tmp-daily.cvd' ... Database test passed. daily.cvd updated (version: 26984, sigs: 2039433, f-level: 90, builder: raynman) main database available for download (remote version: 62) Time: 9.1s, ETA: 0.0s [========================>] 162.58MiB/162.58MiB WARNING: ******* RESULT 200, SIZE: 170479789 ******* Testing database: '/var/db/clamav/tmp.f72e85ffba/clamav-ebbe3d29c4dc3f4a215f27e9a22a1884.tmp-main.cvd' ... Database test passed. main.cvd updated (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) bytecode database available for download (remote version: 334) Time: 0.3s, ETA: 0.0s [========================>] 285.12KiB/285.12KiB WARNING: ******* RESULT 200, SIZE: 291965 ******* Testing database: '/var/db/clamav/tmp.f72e85ffba/clamav-6255c6444f66eec3a9faa4e90a30a0be.tmp-bytecode.cvd' ... Database test passed. bytecode.cvd updated (version: 334, sigs: 91, f-level: 90, builder: anvilleg) WARNING: Clamd was NOT notified: Can't connect to clamd through /var/run/clamav/clamd.sock: No such file or directory |
1.4 ClamAV start
ClamAV auto-start configuration
|
1 2 3 4 |
# vi /etc/rc.conf Add the following clamav_clamd_enable="YES" clamav_freshclam_enable="YES" |
start
|
1 2 3 4 5 |
# /usr/local/etc/rc.d/clamav_clamd start Starting clamav_clamd. # /usr/local/etc/rc.d/clamav_freshclam start Starting clamav_freshclam. |
1.5 manual virus check
To manually check for viruses, do the following
|
1 2 3 4 5 6 7 8 9 10 11 12 |
# clamscan --infected --remove --recursive ----------- SCAN SUMMARY ----------- Known viruses: 8671328 Engine version: 1.1.0 Scanned directories: 1566 Scanned files: 10927 Infected files: 0 Data scanned: 625.51 MB Data read: 305.69 MB (ratio 2.05:1) Time: 177.709 sec (2 m 57 s) Start Date: 2023:07:30 16:29:20 End Date: 2023:07:30 16:32:18 |
1.6 automatic virus scanning
• Scanning range is /home/.
• Output scan results to /var/log/clamav.log
• Automatic deletion of detected viruses
• Executed daily
Create an execution script with the above conditions
①Creation of virus storage directory
|
1 |
# mkdir -p /var/lib/clamav/virus |
➁Shell Script Creation
|
1 2 3 4 5 6 7 8 |
# vi /etc/clamscan.sh Describe the following information #!/bin/sh # clamscan script CLAMSCAN='/usr/local/bin/clamscan' echo "clamscan start "`date '+%Y%m%d'` $CLAMSCAN --log=/var/log/clamav/clamav.log -i --move=/var/lib/clamav/virus/ -r /home |
Grant execution permissions to scripts
|
1 |
# chmod 755 /etc/clamscan.sh |
Register in cron to be executed at 0:00 AM
|
1 2 3 |
# crontab -e Description of the following contents 0 0 * * * /etc/clamscan.sh > /dev/null 2>&1 |
Run the following as a test
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
# /etc/clamscan.sh clamscan start 20230730 ----------- SCAN SUMMARY ----------- Known viruses: 8671328 Engine version: 1.1.0 Scanned directories: 21 Scanned files: 63 Infected files: 0 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 23.208 sec (0 m 23 s) Start Date: 2023:07:30 17:13:26 End Date: 2023:07:30 17:13:49 |
If you look at /var/log/clamav/clamav.log, you will see the same log as above
2. Amavis
Install Amavis, which links ClamAV and Postfix
2.1 Install
|
1 2 |
# cd /usr/ports/security/amavisd-new # make config |
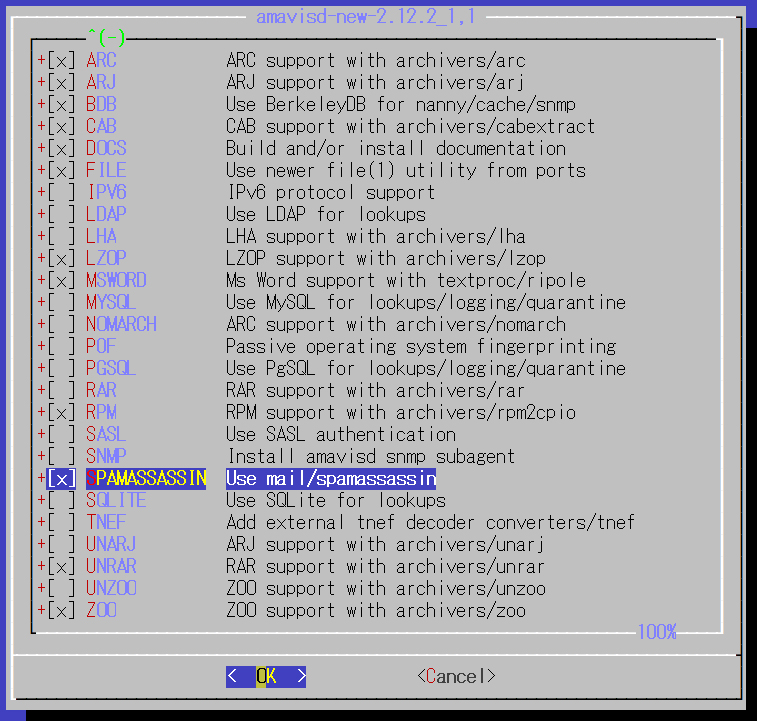
The option settings are as follows
SPAMASSASIN should be included.
IPv6 is not required, so remove the item.
Otherwise, proceed with defaults.
|
1 |
# make install clean |
2.2 Configuration File Editing
Edit amavisd.conf
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
# vi /usr/local/etc/amavisd.conf Line 13 : Uncomment # @bypass_spam_checks_maps = (1); @bypass_spam_checks_maps = (1); Line 23: Change to your own domain name $mydomain = '<domain name>'; Line 155 : Change to own host name # $myhostname = 'host.example.com'; $myhostname = 'mail.<domain name>'; Line 157-158 : Uncomment # $notify_method = 'smtp:[127.0.0.1]:10025'; # $forward_method = 'smtp:[127.0.0.1]:10025'; ↓ $notify_method = 'smtp:[127.0.0.1]:10025'; $forward_method = 'smtp:[127.0.0.1]:10025'; Line 386-389 : Uncomment # ### http://www.clamav.net/ # ['ClamAV-clamd', # \&ask_daemon, ["CONTSCAN {}\n", "/var/run/clamav/clamd.sock"], # qr/\bOK$/m, qr/\bFOUND$/m, # qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ], ↓ ### http://www.clamav.net/ ['ClamAV-clamd', \&ask_daemon, ["CONTSCAN {}\n", "/var/run/clamav/clamd.sock"], qr/\bOK$/m, qr/\bFOUND$/m, qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ], |
2.3 Amavis Auto-Startup Configuration
|
1 2 3 |
# vi /etc/rc.conf Add the following description amavisd_enable="YES" |
Amavis start
|
1 |
# /usr/local/etc/rc.d/amavisd start |
2.4 Postfix Configuration
①Edit main.cf
|
1 2 3 4 |
# vi /usr/local/etc/postfix/main.cf #Add to the last line # Filter configuration content_filter = smtp-amavis:[127.0.0.1]:10024 |
➁Edit master.cf
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
# vi /usr/local/etc/postfix/master.cf #Add to the last line # Amavis configuration smtp-amavis unix - - n - 2 smtp -o smtp_data_done_timeout=1200 -o smtp_send_xforward_command=yes -o disable_dns_lookups=yes -o max_use=20 127.0.0.1:10025 inet n - n - - smtpd -o content_filter= -o local_recipient_maps= -o relay_recipient_maps= -o smtpd_restriction_classes= -o smtpd_delay_reject=no -o smtpd_client_restrictions=permit_mynetworks,reject -o smtpd_helo_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o smtpd_data_restrictions=reject_unauth_pipelining -o smtpd_end_of_data_restrictions= -o mynetworks=127.0.0.0/8 -o smtpd_error_sleep_time=0 -o smtpd_soft_error_limit=1001 -o smtpd_hard_error_limit=1000 -o smtpd_client_connection_count_limit=0 -o smtpd_client_connection_rate_limit=0 -o receive_override_options=no_header_body_checks,no_unknown_recipient_checks |
3. Anti-Spam with SpamAssassin
3.1 SpamAssassin Install
If you did not select spamassassin as an option when you installed Amavis, install it as follows
|
1 2 |
# cd /usr/ports/mail/spamassassin # make install clean |
|
1 |
# chmod 644 /usr/local/etc/mail/spamassassin/v310.pre |
3.2 Configuration File Editing
|
1 2 3 4 |
# vi /usr/local/etc/mail/spamassassin/v310.pre Line 24 : Uncomment (enable TextCat) loadplugin Mail::SpamAssassin::Plugin::DCC |
3.3 Spamassassin start
|
1 2 3 4 |
# vi /etc/rc.conf Additional description below spamd_enable="YES" |
|
1 2 3 |
# sa-update # /usr/local/etc/rc.d/sa-spamd start Starting spamd. |
3.4 SpamassAssin Update
Create an update script
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
# vi /etc/periodic/daily/620.spamassassin Fill in the following information #!/bin/sh PATH=/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/sbin:/usr/local/bin cd /usr/local/etc/mail/spamassassin wget -q https://github.com/kittyfreak/spamassassin_user_prefs/archive/refs/heads/main.zip [ $? -ne 0 ] && exit unzip main.zip >/dev/null 2>&1 [ $? -ne 0 ] && exit rm -f main.zip mv spamassassin_user_prefs-main/user_prefs . rm -rf spamassassin_user_prefs-main cp user_prefs local.cf cat << EOF >> local.cf report_safe 0 rewrite_header Subject ***SPAM*** EOF /usr/local/etc/rc.d/sa-spamd restart > /dev/null |
Grant execution rights to scripts
|
1 |
# chmod 755 /etc/periodic/daily/620.spamassassin |
When the script is executed, a local.cff is created for the date and time of execution
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
# /etc/periodic/daily/620.spamassassin # ll /usr/local/etc/mail/spamassassin total 520 -rw-r--r-- 1 root wheel 1649 Jul 31 19:08 init.pre -rw-r--r-- 1 root wheel 1649 Jul 31 19:08 init.pre.sample -rw-r--r-- 1 root wheel 500636 Aug 2 11:08 local.cf -rw-r--r-- 1 root wheel 3218 Jul 31 19:08 local.cf.sample drwx------ 2 root wheel 6 Jul 31 19:11 sa-update-keys/ -rw-r--r-- 1 root wheel 500588 Apr 30 10:24 user_prefs -rw-r--r-- 1 root wheel 2266 Jul 31 19:11 v310.pre -rw-r--r-- 1 root wheel 2267 Jul 31 19:08 v310.pre.sample -rw-r--r-- 1 root wheel 1168 Jul 31 19:08 v312.pre -rw-r--r-- 1 root wheel 1168 Jul 31 19:08 v312.pre.sample -rw-r--r-- 1 root wheel 2416 Jul 31 19:08 v320.pre -rw-r--r-- 1 root wheel 2416 Jul 31 19:08 v320.pre.sample -rw-r--r-- 1 root wheel 1237 Jul 31 19:08 v330.pre -rw-r--r-- 1 root wheel 1237 Jul 31 19:08 v330.pre.sample -rw-r--r-- 1 root wheel 1020 Jul 31 19:08 v340.pre -rw-r--r-- 1 root wheel 1020 Jul 31 19:08 v340.pre.sample -rw-r--r-- 1 root wheel 1315 Jul 31 19:08 v341.pre -rw-r--r-- 1 root wheel 1315 Jul 31 19:08 v341.pre.sample -rw-r--r-- 1 root wheel 1475 Jul 31 19:08 v342.pre -rw-r--r-- 1 root wheel 1475 Jul 31 19:08 v342.pre.sample -rw-r--r-- 1 root wheel 1266 Jul 31 19:08 v343.pre -rw-r--r-- 1 root wheel 1266 Jul 31 19:08 v343.pre.sample -rw-r--r-- 1 root wheel 1482 Jul 31 19:08 v400.pre -rw-r--r-- 1 root wheel 1482 Jul 31 19:08 v400.pre.sample |
3.5 postfix restart
|
1 2 3 |
# /usr/local/etc/rc.d/postfix restart postfix/postfix-script: stopping the Postfix mail system postfix/postfix-script: starting the Postfix mail system |
3.6 Spam mailbox creation
When using IMAP in this case
①Create spam mailboxes for existing users
Let's assume the existing user is huong
|
1 2 3 |
# mkdir -p /home/huong/Maildir/.spam/{cur,new,tmp} # chmod -R 700 /home/huong/Maildir/.spam # chown -R huong:huong /home/huong/Maildir/.spam |
➁Create spam mailboxes for additional users
|
1 2 |
# mkdir -p /usr/share/skel/Maildir/.spam/{cur,new,tmp} # chmod -R 700 /usr/share/skel/Maildir/.spam |
3.7Edit procmailrc (for IMAP)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
# vi /usr/local/etc/procmailrc Fill in the following SHELL=/bin/sh PATH=/bin:/usr/bin:/usr/local/bin DROPPRIVS=yes MAILDIR=$HOME/Maildir DEFAULT=$MAILDIR/ SPAM=$MAILDIR/.spam/ #LOGFILE=$MAILDIR/procmail.log :0 * ^Subject:.*=\?[Ii][Ss][Oo]-2022-[Jj][Pp]\?[Bb]\?GyRCTCQ\+NUJ6OS05cCIo /dev/null # Start spamassassin if "X-Spam-***" is not in the header :0fw *!^X-Spam.* |spamassassin # If the header has "X-Spam-Status: Yes", it is stored in the ".spam" directory. :0 *^X-Spam-Status: Yes $SPAM |
3.8 Spam Mail Learning
Create spam email learning scripts
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# vi /etc/periodic/daily/620.sa-learn Fill in the following #!/bin/sh # Learning spam folder as spam /usr/local/bin/sa-learn --spam /home/*/Maildir/.spam/cur # Maildir folder learned as normal mail /usr/local/bin/sa-learn --ham /home/*/Maildir/cur # Uncomment the following to delete the spam folder #/bin/rm -f /home/*/Maildir/.spam/cur/* |
3.9 Spam Mail Sending Test
Fill in the following in the body of the message in Thunderbird and send it to yourself.
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X
The following message appears in the header of an incoming e-mail
X-Spam-Checker-Version: SpamAssassin 4.0.0 (2022-12-14) on Lepard
X-Spam-Flag: YES
X-Spam-Level:**************************************************
X-Spam-Status: Yes, score=1002.4 required=13.0 tests=ALL_TRUSTED,
CONTENT_TYPE_PRESENT,GTUBE,HTML_MESSAGE,MIMEQENC,MPART_ALT_DIFF,
MULTIPART_ALTERNATIVE,QENCPTR1,QENCPTR2,T_SCC_BODY_TEXT_LINE
autolearn=no autolearn_force=no version=4.0.0
X-Spam-Report:
* 0.1 ALL_TRUSTED Passed through trusted hosts only via SMTP
* -0.1 CONTENT_TYPE_PRESENT exists:Content-Type
* 0.1 MULTIPART_ALTERNATIVE Multipart/alternative
* 1000 GTUBE BODY: Generic Test for Unsolicited Bulk Email
* 1.0 HTML_MESSAGE BODY: HTML included in message
* 0.7 MPART_ALT_DIFF BODY: HTML and text parts are different
* 0.2 QENCPTR2 FULL: Quoted-Printable mime pattern
* 0.2 MIMEQENC FULL: Quoted-Printable mime definition
* 0.2 QENCPTR1 FULL: Quoted-Printable mime pattern
* -0.0 T_SCC_BODY_TEXT_LINE No description available.

