1.Anti-virus software Clamav installed
1.1 Install
|
1 |
# apt install clamav clamav-daemon |
The clamav-related configuration files are installed in the "/etc/clamav/" folder.
1.2 Virus definition updates
|
1 2 |
# systemctl stop clamav-freshclam # freshclam |
|
1 2 3 4 |
ClamAV update process started at Wed May 1 10:15:19 2024 Wed May 1 10:15:19 2024 -> daily.cvd database is up-to-date (version: 27261, sigs: 2060256, f-level: 90, builder: raynman) Wed May 1 10:15:19 2024 -> main.cvd database is up-to-date (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) Wed May 1 10:15:19 2024 -> bytecode.cvd database is up-to-date (version: 335, sigs: 86, f-level: 90, builder: raynman) |
|
1 |
# systemctl start clamav-freshclam |
Change configuration file
|
1 2 3 4 5 6 |
# vi /etc/logrotate.d/clamav-freshclam Line 7 create 640 clamav adm ↓ create 640 clamav clamav |
1.3 Virus Check Confirmation
①Running manual virus checks
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# clamscan --infected --remove --recursive /home ----------- SCAN SUMMARY ----------- Known viruses: 8692086 Engine version: 1.0.5 Scanned directories: 5 Scanned files: 7 Infected files: 0 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 20.596 sec (0 m 20 s) Start Date: 2024:05:01 10:17:27 End Date: 2024:05:01 10:17:48 |
Infected files: 0, so no virus
②Download a test virus to detect viruses
Download a trial harmless virus to test detection
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# cd # wget https://secure.eicar.org/eicar.com.txt # clamscan --infected --remove --recursive /root/eicar.com.txt: Win.Test.EICAR_HDB-1 FOUND /root/eicar.com.txt: Removed. ----------- SCAN SUMMARY ----------- Known viruses: 8692086 Engine version: 1.0.5 Scanned directories: 2 Scanned files: 8 Infected files: 1 Data scanned: 0.02 MB Data read: 0.01 MB (ratio 2.00:1) Time: 13.444 sec (0 m 13 s) Start Date: 2024:05:01 10:20:34 End Date: 2024:05:01 10:20:47 |
The virus is notified with the message "FOUND" and "Infected files: 1". Also, since the "--remove" option is attached, the test virus has been removed.
1.4 Create a script file to do a full scan
|
1 2 3 |
# mkdir /opt/script # cd /opt/script # vi clam-full.sh |
①Contents of clam-full.sh (new)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
#!/bin/sh echo ========================================= date hostname clamscan / \ --infected \ --recursive \ --log=/var/log/clamav/clamscan.log \ --move=/var/log/clamav/virus \ --exclude-dir=^/boot \ --exclude-dir=^/sys \ --exclude-dir=^/proc \ --exclude-dir=^/dev \ --exclude-dir=^/var/log/clamav/virus if [ $? = 0 ]; then echo "virus undetected" else echo "Virus detected!!" fi |
②grant execution authority
|
1 |
# chmod +x /opt/script/clam-full.sh |
③Create a folder for virus quarantine (if it already exists, it is OK, but if it does not, a runtime error will occur because it is specified as an excluded directory in the above script).
|
1 |
# mkdir /var/log/clamav/virus |
④try and run it.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# /opt/script/clam-full.sh ========================================= Wed 1 May 10:23:41 JST 2024 Lepard LibClamAV Warning: cli_scanxz: decompress file size exceeds limits - only scanning 105906176 bytes ----------- SCAN SUMMARY ----------- Known viruses: 8692086 Engine version: 1.0.5 Scanned directories: 10218 Scanned files: 69859 Infected files: 0 Data scanned: 3674.69 MB Data read: 5454.82 MB (ratio 0.67:1) Time: 602.188 sec (10 m 2 s) Start Date: 2024:05:01 10:23:41 End Date: 2024:05:01 10:33:43 virus undetected |
LibClamAV Warning: cli_scanxz: decompress file size exceeds limits - only scanning 27262976 bytes
If the above message is displayed, run with the "--max-filesize=200M" and "--max-scansize=200M" options.
⑤Scheduled virus scan execution with cron
|
1 2 |
# crontab -e 0 2 * * mon /opt/script/clam-full.sh >> /var/log/clamav/clamascan.log |
2. Email software installation
2.1 Postfix : Installation/Configuration
Install Postfix and build an SMTP server. 25/TCP is used for SMTP.
To prevent unauthorized mail relay, use the SASL function of Dovecot (see below), and configure Postfix so that authentication is required even for outgoing mail.
①Install
|
1 |
# apt -y install postfix sasl2-bin |
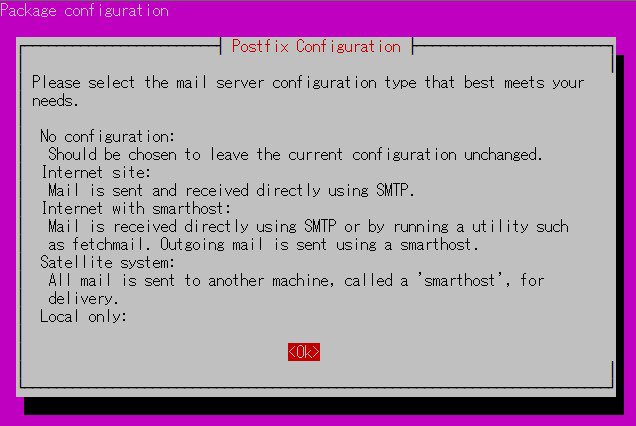
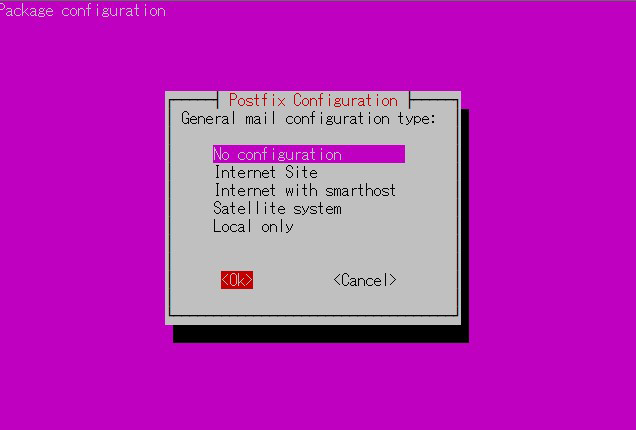
Installation Status Screen
You will be asked to select a general configuration setting, select "No Configuration" to set it manually later.
②Configuration File Edit
|
1 2 |
# cp /usr/share/postfix/main.cf.dist /etc/postfix/main.cf # vi /etc/postfix/main.cf |
Editing Contents
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 |
# Line 82:Uncomment mail_owner = postfix # Line 100:Add hostname specification myhostname = mail.[domain name] # Line 107:Add domain name specification mydomain = [domain name] # Line127:Uncomment myorigin = $mydomain # Line 141:Uncomment inet_interfaces = all # Line 189:Uncomment mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain # Line 232:Uncomment local_recipient_maps = unix:passwd.byname $alias_maps # Line 277:Uncomment mynetworks_style = subnet # Line 294:self-networking addition mynetworks = 127.0.0.0/8, 192.168.11.0/24 # Line 416:Uncomment alias_maps = hash:/etc/aliases # Line 427:Uncomment alias_database = hash:/etc/aliases # Line 449:Uncomment home_mailbox = Maildir/ # Line 585:Make it a comment and add below it #smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu) smtpd_banner = $myhostname ESMTP # Line 659:add sendmail_path = /usr/sbin/postfix # Line 664:add newaliases_path = /usr/bin/newaliases # Line 669:add mailq_path = /usr/bin/mailq # Line 675:add setgid_group = postdrop # Line 679:comment #html_directory = # Line 683:comment #manpage_directory = # Line 688:comment #sample_directory = # Line 692:comment #readme_directory = # Add to last line: message_size_limit = 10485760 # Limit mailbox size to 1G mailbox_size_limit = 1073741824 # SMTP-Auth Settings smtpd_sasl_type = dovecot smtpd_sasl_path = private/auth smtpd_sasl_auth_enable = yes smtpd_sasl_security_options = noanonymous smtpd_sasl_local_domain = $myhostname smtpd_recipient_restrictions = permit_mynetworks, permit_auth_destination, permit_sasl_authenticated, reject |
③master.cf edit
|
1 |
# vi /etc/postfix/master.cf |
Editing Contents
|
1 2 3 4 5 6 7 8 9 10 11 12 |
smtp inet n - y - - smtpd Line 19,22 Uncomment #smtp inet n - y - 1 postscreen #smtpd pass - - y - - smtpd #dnsblog unix - - y - 0 dnsblog #tlsproxy unix - - y - 0 tlsproxy submission inet n - y - - smtpd # -o syslog_name=postfix/submission # -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes # -o smtpd_tls_auth_only=yes |
④Reflecting settings
|
1 2 |
# newaliases # systemctl restart postfix |
2.2 Dovecot : Installation/Configuration
Install Dovecot and build a POP/IMAP server, using 110/TCP for POP and 143/TCP for IMAP
|
1 |
# apt -y install dovecot-core dovecot-pop3d dovecot-imapd |
①Configure Dovecot to provide SASL functionality for Postfix
|
1 2 3 4 |
# vi /etc/dovecot/dovecot.conf Line 30:Uncomment listen = *, :: |
|
1 2 3 4 5 6 7 |
# vi /etc/dovecot/conf.d/10-auth.conf Line 10:Uncomment and change (also allow plain text authentication) disable_plaintext_auth = no Line 100:add auth_mechanisms = plain login |
|
1 2 3 4 |
# vi /etc/dovecot/conf.d/10-mail.conf Line 30:Change to Maildir format mail_location = maildir:~/Maildir |
|
1 2 3 4 5 6 7 8 9 |
# vi /etc/dovecot/conf.d/10-master.conf Line 110-112:Uncommented and added # Postfix smtp-authi unix_listener /var/spool/postfix/private/auth { mode = 0666 user = postfix group = postfix } |
②Configuration Reflection
|
1 |
# systemctl restart dovecot |
2.3 Port Open
|
1 2 3 4 |
# ufw allow pop3 # ufw allow imap # ufw allow smtp # ufw reload |
2.4 Email User Account Registration
Register a user account for e-mail.
This setting is for when a user account on the OS is also used for e-mail.
If you want to use mail with a user account on the OS, you do not need to make any additional settings, only register an OS user.
①Mail Client Install
|
1 |
# apt -y install mailutils |
②Mailboxes are set to refer to Maildir
|
1 |
# echo 'export MAIL=$HOME/Maildir/' >> /etc/profile.d/mail.sh |
2.5 operation check ①
①Test sending mail
Send test mail to yourself [mail (user name)@(host name)].
|
1 2 3 4 5 6 7 8 |
# su - [user name] $ mail [user name]@localhost # Cc Cc: # subject Subject: Test Mail # body This is the first mail. |
Ctrl + D key to exit the main text
➁Check incoming mail
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
$ mail "/home/[user name]/Maildir/": 1 message 1 new >N 1 [user name] Wed May 1 02:15 13/427 Test Mail ? 1 Return-Path: <user name@lepard> X-Original-To:[user name]g@localhost Delivered-To: [user name]@localhost Received: by mail.korodes.com (Postfix, from userid 1000) id BC62C61755; Wed, 1 May 2024 11:15:57 +0900 (JST) To: <user name@localhost> Subject: Test Mail User-Agent: mail (GNU Mailutils 3.15) Date: Wed, 1 May 2024 11:15:57 +0900 Message-Id: <20231004012407.41F6CB326@mail.domain> From: [user name] <user name@lepard> This is the first mail. |
2.6 operation check ②
Set up and confirm your account in Mozilla Thunderbird
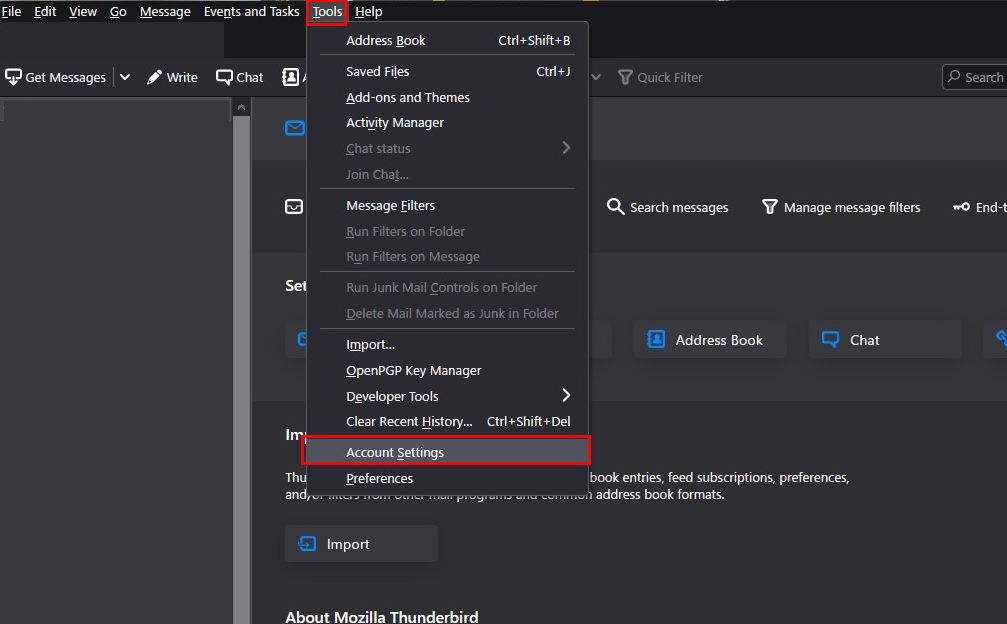
①Start Thunderbird, and click "Tools", "Account Settings".
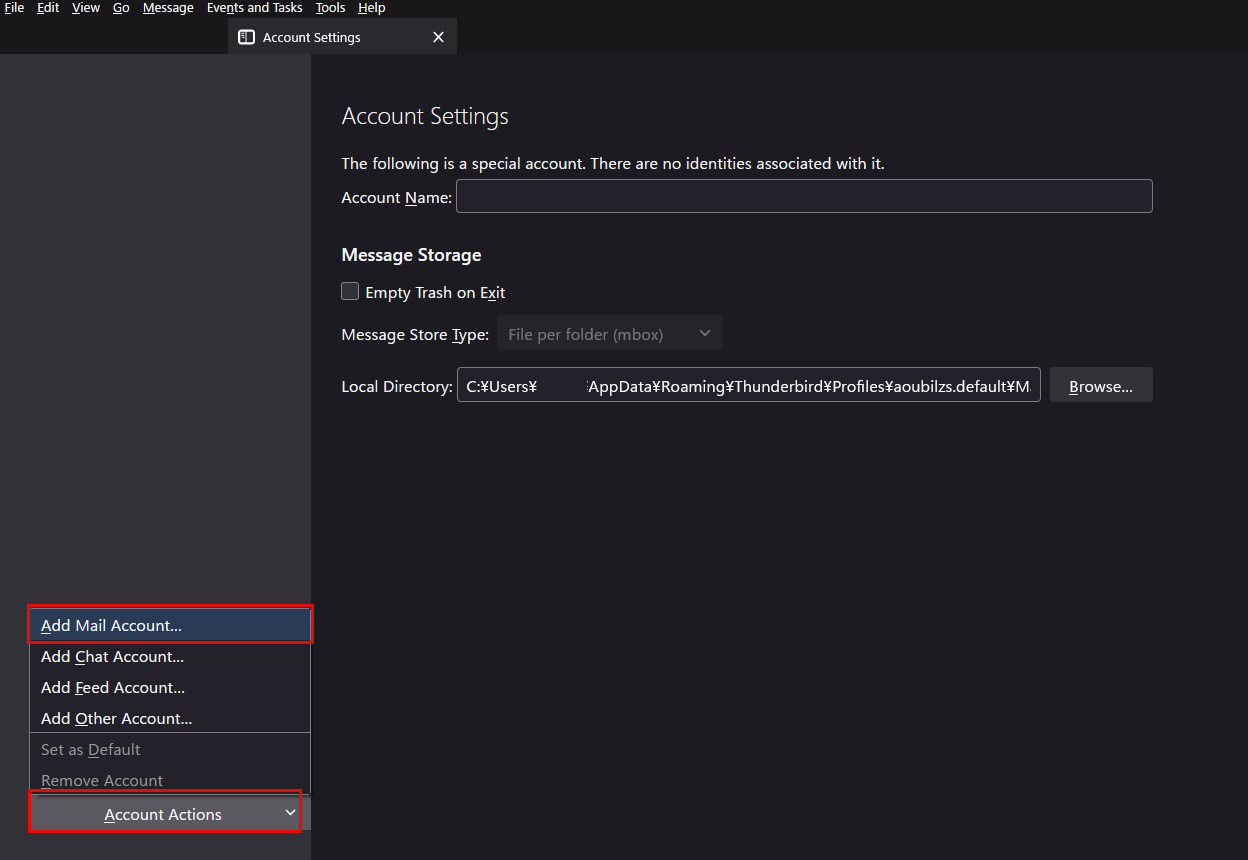
②「Account Actions」「Add Mail Account」
③Your full name : any name
Email addtess : huong@korodes.com" that I just added.
Password : Password for user huong
Click on "Configure manually"
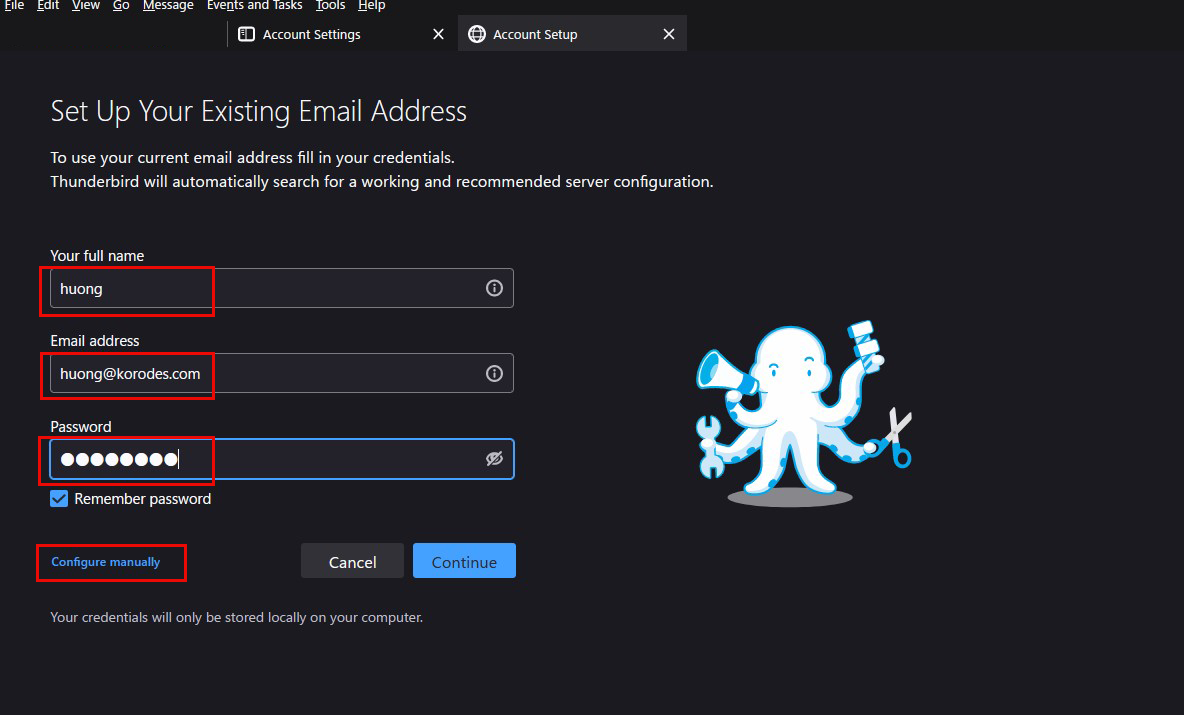
④Set "INCOMMING SERVER" and "OUTGOING SERVER" as shown below and click "Re-test".
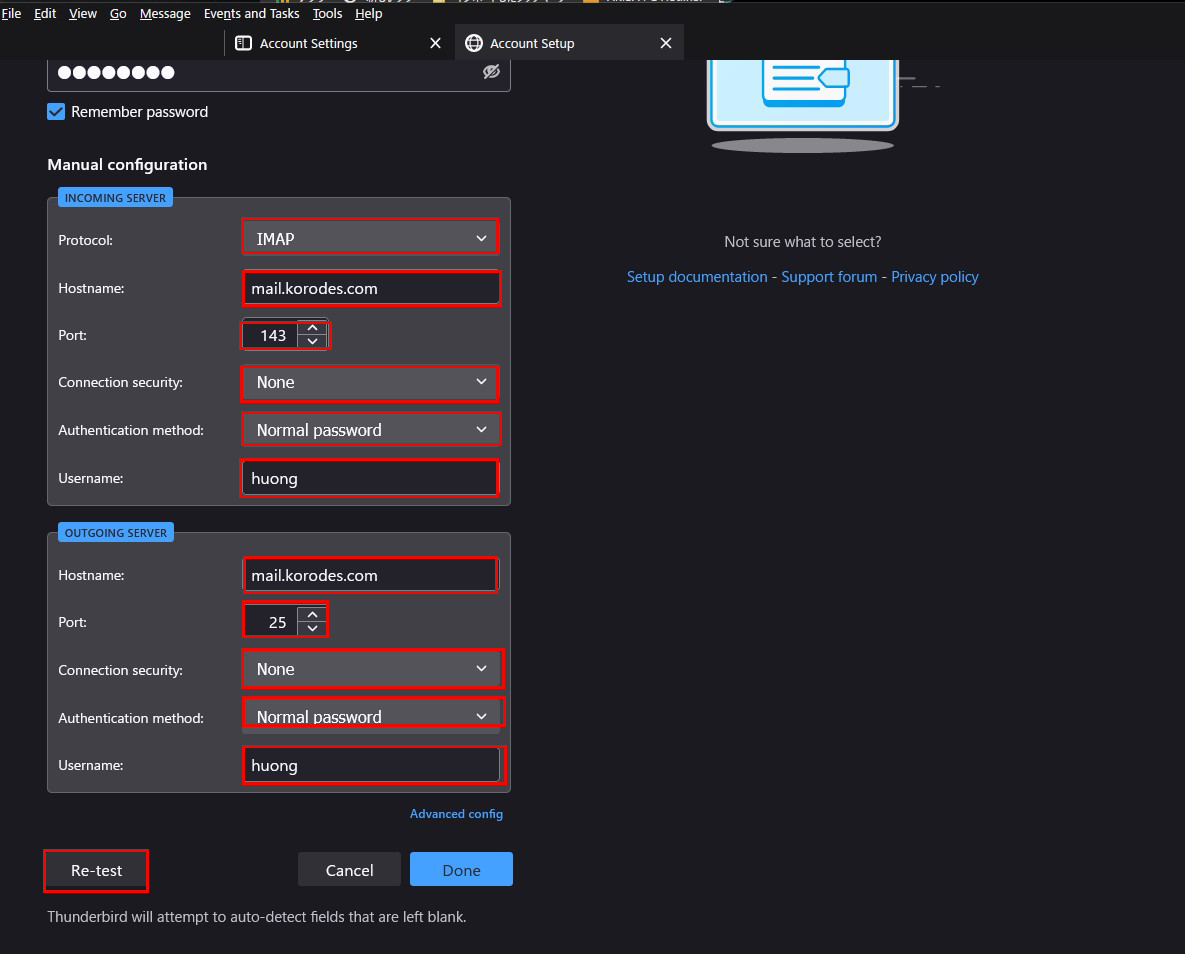
⑤"The following settings were found by probinfg the given server" Displayed
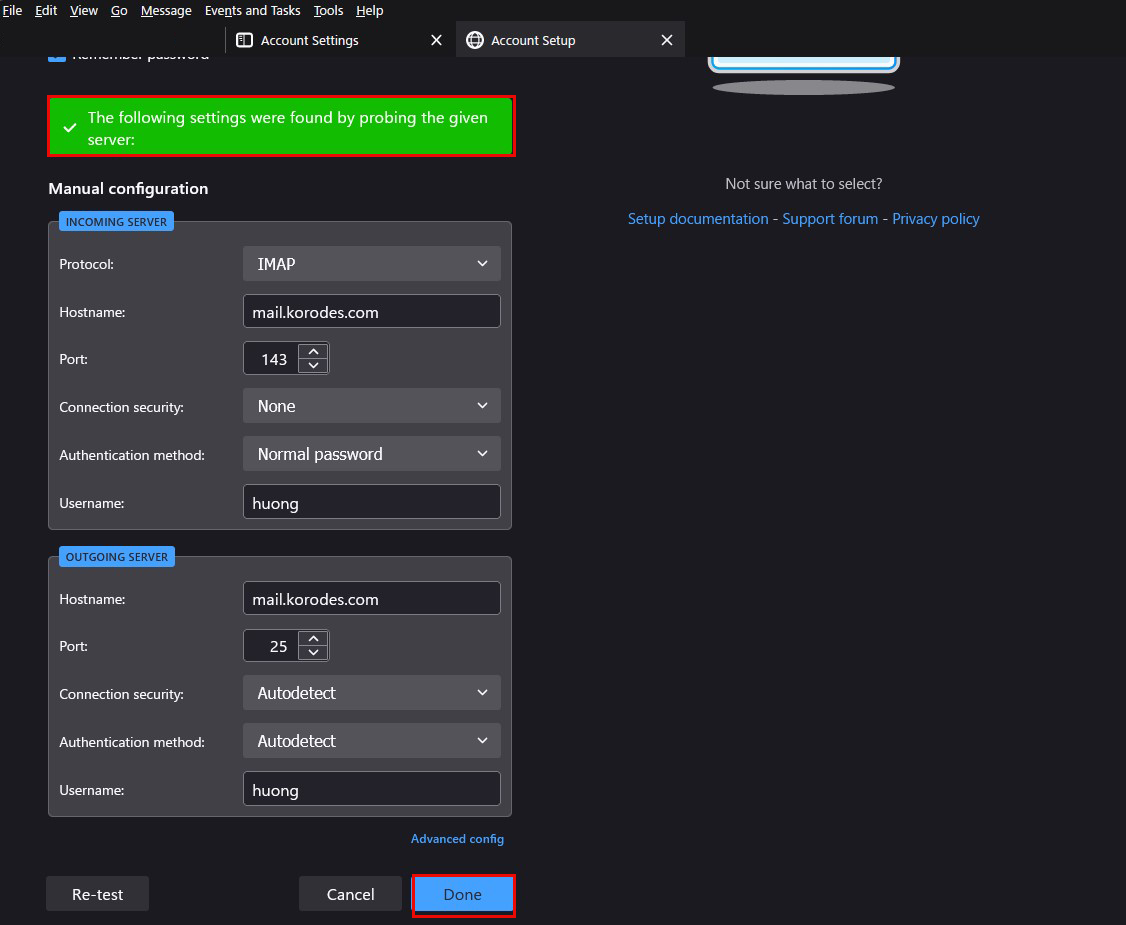
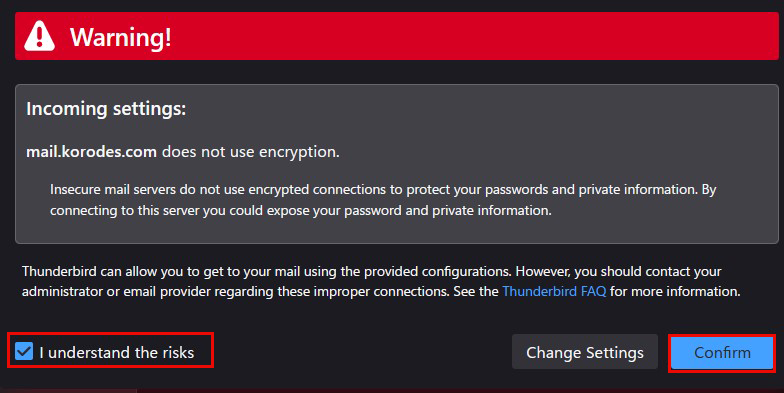
After clicking "Done," the following "Warning" appears, but there is no problem, so click "Confirm.
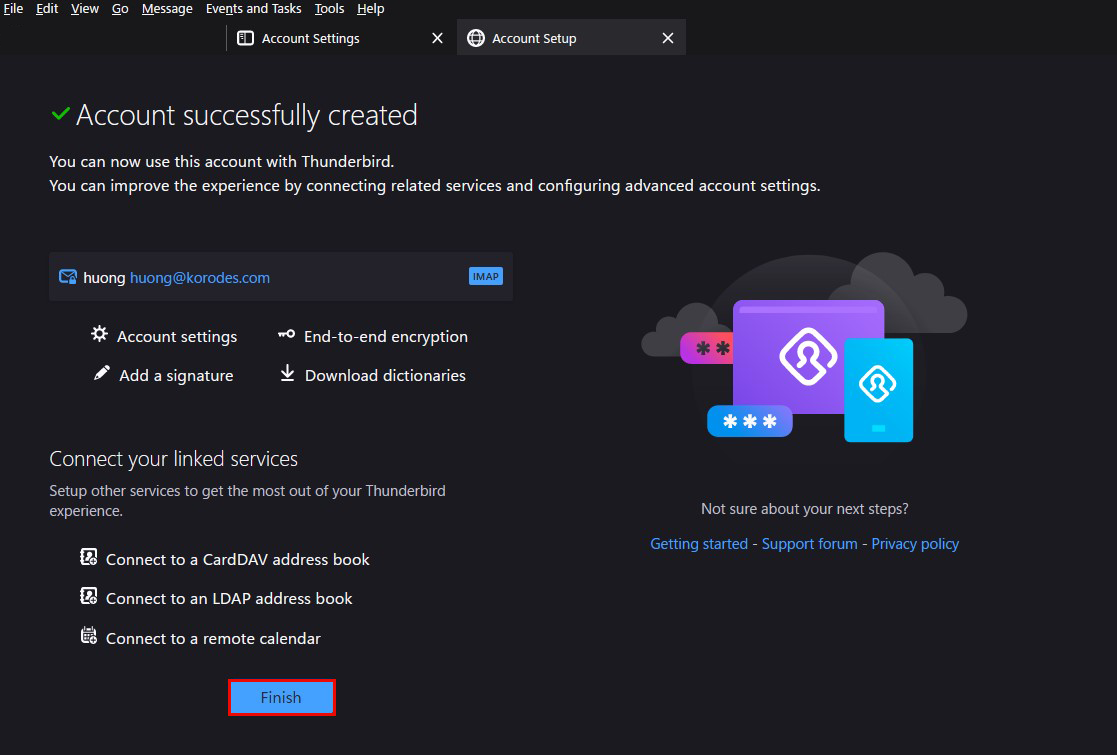
⑥Click "Finish" when "Account syccessfuly created" is displayed.
2.7 Applied ClamAV to mail server Postfix
Set up Postfix and Clamav to work together to scan incoming and outgoing mail in real time.
①Install Amavisd and Clamav Daemon and start Clamav Daemon
|
1 2 3 |
$ su - Password: # apt -y install clamav-daemon amavisd-new |
If the server is not using a fully qualified domain name (FQDN) as the hostname, Amavis may fail to start.
Also, since the OS hostname may change, set a valid hostname directly in the Amavis configuration file
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# vi /etc/amavis/conf.d/05-node_id Line 11 : Uncomment and change use strict; # $myhostname is used by amavisd-new for node identification, and it is # important to get it right (e.g. for ESMTP EHLO, loop detection, and so on). chomp($myhostname = `hostname --fqdn`); # To manually set $myhostname, edit the following line with the correct Fully # Qualified Domain Name (FQDN) and remove the # at the beginning of the line. # $myhostname = "mail.[domain name]"; 1; # ensure a defined return |
②"15-content_filter_mode" editing
|
1 2 3 4 |
# vi /etc/amavis/conf.d/15-content_filter_mode Line 13,14 : Uncomment and enable virus scan @bypass_virus_checks_maps = ( \%bypass_virus_checks, \@bypass_virus_checks_acl, \$bypass_virus_checks_re); |
③Register your own domain name
|
1 |
# echo '<yourDomain>' > /etc/mailname |
④"main.cf" editing
|
1 2 3 4 |
# vi /etc/postfix/main.cf Add to last line content_filter=smtp-amavis:[127.0.0.1]:10024 |
⑤"master.cf" editing
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
# vi /etc/postfix/master.cf # Add all the following lines to the last line smtp-amavis unix - - n - 2 smtp -o smtp_data_done_timeout=1200 -o smtp_send_xforward_command=yes -o disable_dns_lookups=yes 127.0.0.1:10025 inet n - n - - smtpd -o content_filter= -o local_recipient_maps= -o relay_recipient_maps= -o smtpd_restriction_classes= -o smtpd_client_restrictions= -o smtpd_helo_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o mynetworks=127.0.0.0/8 -o strict_rfc821_envelopes=yes -o smtpd_error_sleep_time=0 -o smtpd_soft_error_limit=1001 -o smtpd_hard_error_limit=1000 |
⑥Configuration Reflection
|
1 2 3 |
# usermod -G clamav amavis # usermod -G amavis clamav # systemctl restart clamav-daemon amavis postfix |
⑦When you send an e-mail to yourself on Thuderbird, etc., it is successful if you see the following message in the header of the incoming e-mail.
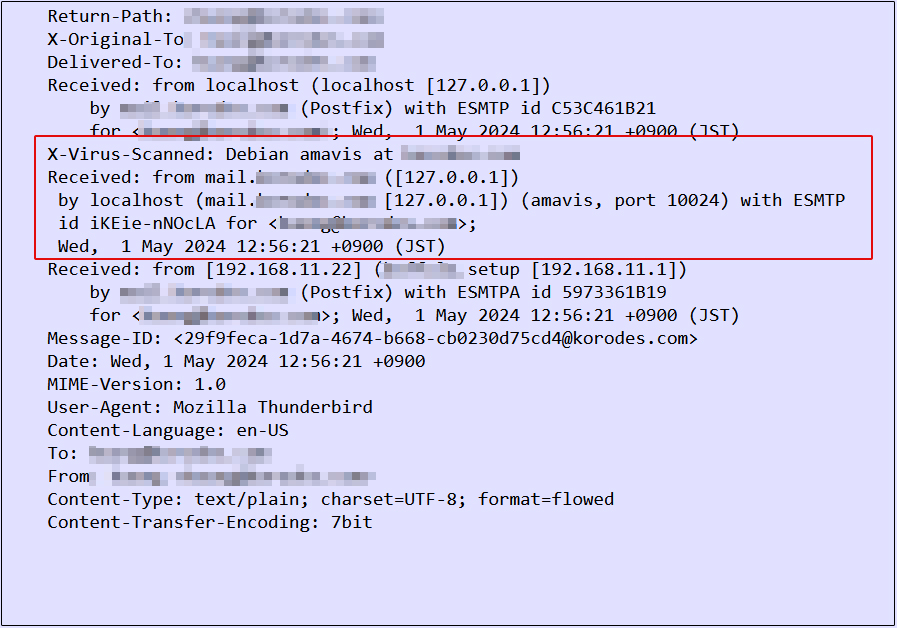
Try sending yourself an email with the body of the email "X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*" and confirm that the email is discarded and never received
2.8 Applied spamassassin to mail server Postfix
2.5.1 spamassassin install
①Install
|
1 2 3 |
# apt update # apt upgrade # apt -y install spamassassin spamass-milter |
②SpamAssassin Settings
|
1 2 3 4 |
# vi /etc/mail/spamassassin/v310.pre Delete # at the beginning of the line per line 24 loadplugin Mail::SpamAssassin::Plugin::DCC |
➂SpamAssassin configuration file modernization script
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
# vi /opt/script/spamassassin-update.sh #!/bin/bash cd /etc/mail/spamassassin wget -q https://github.com/kittyfreak/spamassassin_user_prefs/archive/refs/heads/main.zip [ $? -ne 0 ] && exit unzip main.zip >/dev/null 2>&1 [ $? -ne 0 ] && exit rm -f main.zip mv spamassassin_user_prefs-main/user_prefs . rm -rf spamassassin_user_prefs-main diff user_prefs user_prefs.org > /dev/null 2>&1 if [ $? -ne 0 ]; then cp user_prefs local.cf echo "report_safe 0" >> local.cf echo "rewrite_header Subject ***SPAM***" >> local.cf if [ -f /etc/init.d/spamd ]; then /etc/init.d/spamd restart > /dev/null else systemctl restart spamd > /dev/null fi fi cp user_prefs user_prefs.org |
Grant execute permission to the spamassassin-update script and run it
|
1 2 |
# chmod 700 /opt/script/spamassassin-update.sh # /opt/script/spamassassin-update.sh |
Check that the SpamAssassin configuration file (local.cf) is created in the /etc/mail/spamassassin directory with the date of the day
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# ls -l /etc/mail/spamassassin/ total 1528 -rw-r--r-- 1 root root 1292 Aug 31 2023 65_debian.cf -rw-r--r-- 1 root root 1644 Apr 12 21:53 init.pre -rw-r--r-- 1 root root 500636 May 1 14:02 local.cf -rw-r--r-- 1 root root 118 Aug 31 2023 sa-compile.pre drwxr-xr-x 2 root root 4096 May 1 12:47 sa-update-hooks.d -rw-r--r-- 1 root root 500588 Apr 30 2023 user_prefs -rw-r--r-- 1 root root 500588 May 1 14:17 user_prefs.org -rw-r--r-- 1 root root 2257 May 1 14:12 v310.pre -rw-r--r-- 1 root root 1163 Apr 12 21:53 v312.pre -rw-r--r-- 1 root root 2411 Apr 12 21:53 v320.pre -rw-r--r-- 1 root root 1232 Apr 12 21:53 v330.pre -rw-r--r-- 1 root root 1015 Apr 12 21:53 v340.pre -rw-r--r-- 1 root root 1310 Apr 12 21:53 v341.pre -rw-r--r-- 1 root root 1470 Apr 12 21:53 v342.pre -rw-r--r-- 1 root root 1261 Apr 12 21:53 v343.pre -rw-r--r-- 1 root root 1477 Apr 12 21:53 v400.pre |
Set up cron to automatically run a script daily that updates the SpamAssassin configuration file
|
1 2 |
# crontab -e 0 2 * * * /opt/script/spamassassin-update.sh > /dev/null 2>&1 |
④spamass-milter startup and automatic startup settings
|
1 2 3 4 5 |
# systemctl start spamass-milter # systemctl enable spamass-milter spamass-milter.service is not a native service, redirecting to systemd-sysv-install. Executing: /usr/lib/systemd/systemd-sysv-install enable spamass-milter |
- Create a directory ".Spam" in Maildir format for storing spam mails.
- Creation is done by the target user.
|
1 2 3 4 5 6 7 |
# su - <user name> $ cd ~ Create a directory named ".Spam" $ cd Maildir $ /usr/bin/maildirmake.dovecot .Spam $ su - Password: |
2.5.2 Procmail
①Procmail Install
|
1 |
# apt -y install procmail |
If installed, the following results are returned
|
1 2 |
# which procmail /usr/bin/procmail |
②Procmail Settings
If you put the filter in "/etc/procmailrc", which is in charge of the entire mail filter, the filter will be applied to all users.
If you put it in "/home/username/.procmailrc", which is the mail filter file for each user, the filter will be applied only to that user.
In this case, to apply the filter to all users, we will put it in "/etc/procmailrc".
|
1 |
# vi /etc/procmailrc |
procmailrc description (newly created)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# Set path PATH=/bin:/usr/bin:/usr/local/bin # Mailbox Settings MAILDIR=$HOME/Maildir DEFAULT=$MAILDIR/ # Specify log file output destination for Procmail LOGFILE=$MAILDIR/procmaillog # Specify lock file path LOCKFILE=$HOME/.lockmail # If there is no "X-Spam-***" in the mail header, spamassassassin will be started. :0fw *!^X-Spam.* |spamassassin # If the mail header contains "X-Spam-Status: Yes", the mail will be stored in the ".Spam" directory. :0 * ^X-Spam-Status: Yes $MAILDIR/.Spam/ |
2.5.3 Postfix Configuration
① "main.cf" editing
|
1 2 3 4 |
# vi /etc/postfix/main.cf Uncomment line 477 mailbox_command = /usr/bin/procmail |
②Reflecting and activating settings
|
1 2 |
# systemctl start spamd # systemctl restart postfix |
2.5.4 Spam Email Learning
Learning all the contents of all users' ".Spam" directories as spam mail
①Learning of spam mail
|
1 2 |
# /usr/bin/sa-learn --spam /home/*/Maildir/.Spam/cur Learned tokens from 0 message(s) (0 message(s) examined). <--Learned 0 emails as spam mails |
②Normal mail learning
|
1 2 |
# /usr/bin/sa-learn --ham /home/*/Maildir/cur Learned tokens from 4 message(s) (4 message(s) examined). <-- Learned 4 emails as normal emails |
③Create a script and register it with Cron
Name the file "spam-learns.sh" and place it under /opt/script/.
After saving the script, give it executable access as "chmod 750 spam-learns.sh".
|
1 |
# vi /opt/script/spam-learns.sh |
spam-learns.sh Contents
|
1 2 3 4 5 6 7 |
#! /bin/sh # Spam Email Learning /usr/bin/sa-learn --spam /home/*/Maildir/.Spam/cur # Learning normal mail /usr/bin/sa-learn --ham /home/*/Maildir/cur # If you want to force the deletion of the contents of the spam mail storage directory, add the following statement /bin/rm -f /home/*/Maildir/.Spam/cur |
|
1 |
# chmod 750 /opt/script/spam-learns.sh |
After spam-learns.sh is created, create a definition file directly under /lib/systemd/system.
The name should end in .service, like spam-learns.service.
Define the Type as simple.
|
1 2 |
# cd /lib/systemd/system # vi spam-learns.service |
Contents of spam-learns.service
|
1 2 3 4 5 6 7 8 9 10 |
[Unit] Description=demo sample node.js program [Service] Type=simple ExecStart= /opt/script/spam-learns.sh Restart=always [Install] WantedBy=multi-user.target |
|
1 2 |
# crontab -e 0 4 * * * /opt/script/spam-learns.sh |
|
1 2 |
# systemctl enable spam-learns Created symlink /etc/systemd/system/multi-user.target.wants/spam-learns.service → /lib/systemd/system/spam-learns.service. |
④Send a blank email to yourself in Thunderbird, etc., and if you see the following message in the header of the received email, you have succeeded.
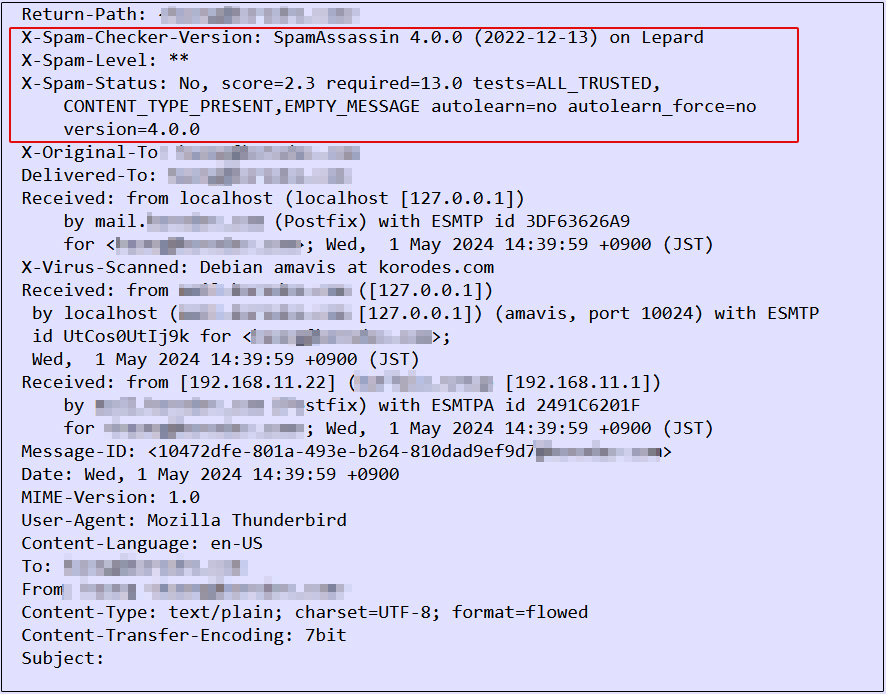
⑤Spam check confirmation
Send yourself an email with the body of the email "XJSC4JDBQADN1.NSBN32IDNENGTUBE-STANDARD-ANTI-UBE-TEST-EMAILC.34X" and make sure the email is not delivered and is sorted into the Spam folder
The header shows the following
Check mail under /home/[user]/Maildir/.Spam/new/.
| X-Spam-Checker-Version: SpamAssassin 4.0.0 (2022-12-13) on Lepard X-Spam-Flag: YES X-Spam-Level: ************************************************** X-Spam-Status: Yes, score=1002.4 required=13.0 tests=ALL_TRUSTED, CONTENT_TYPE_PRESENT,GTUBE,HTML_MESSAGE,MIMEQENC,MPART_ALT_DIFF, MULTIPART_ALTERNATIVE,QENCPTR1,QENCPTR2 autolearn=no autolearn_force=no version=4.0.0 X-Spam-Report: * 0.1 ALL_TRUSTED Passed through trusted hosts only via SMTP * 1000 GTUBE BODY: Generic Test for Unsolicited Bulk Email * -0.1 CONTENT_TYPE_PRESENT exists:Content-Type * 0.1 MULTIPART_ALTERNATIVE Multipart/alternative * 1.0 HTML_MESSAGE BODY: HTML included in message * 0.7 MPART_ALT_DIFF BODY: HTML and text parts are different * 0.2 MIMEQENC FULL: Quoted-Printable mime definition * 0.2 QENCPTR1 FULL: Quoted-Printable mime pattern * 0.2 QENCPTR2 FULL: Quoted-Printable mime pattern |

