Contents
1.Obtain SSL Certificate( Let's Encrypt )
1.1 Advance preparation
Install the latest open ssl
|
1 |
# dnf install openssl-devel |
certbot package install
Install "certbot", Let's Encrypt's SSL certificate issuing tool.
|
1 |
# dnf install certbot |
1.2 Obtaining Certificates
|
1 |
# certbot certonly --webroot -w /var/www/html/[FQDN] -d [FQDN] |
Registration of e-mail address and agreement to terms of use required for the first time only
Specify an email address that you can receive
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
Saving debug log to /var/log/letsencrypt/letsencrypt.log Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [Mail address] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf. You must agree in order to register with the ACME server. Do you agree? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: y - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing, once your first certificate is successfully issued, to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: y Account registered. Requesting a certificate for [FQDN] Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/[FQDN]/fullchain.pem Key is saved at: /etc/letsencrypt/live/[FQDN]/privkey.pem This certificate expires on 2023-05-24. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can try again later by visiting https://act.eff.org. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
The following certificates have been obtained under [/etc/letsencrypt/live//] as described in the message
cert.pem : SSL server certificate (including public key)
chain.pem : Intermediate Certificates
fullchain.pem : File containing cert.pem and chain.pem combined
privkey.pem : private key
1.3 Automatic renewal of certificates
①Pre-registration test
First, test the automatic update using the following --dry-run option.
With this option, certificates are not renewed, only checked, so there is no need to worry about getting stuck with a limit on the number of times a certificate can be obtained.
|
1 |
# certbot renew --dry-run |
➁Automatically renew SSL certificates using cron (run at midnight on the 1st of each month)
|
1 2 |
# crontab -e 0 0 1 * * certbot renew --pre-hook "systemctl stop httpd" --post-hook "systemctl start httpd" |
2. Apache https
Install the following
|
1 |
# dnf -y install mod_ssl |
2.1 Edit ssl.conf file
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# vi /etc/httpd/conf.d/ssl.conf ●Line 43 : Uncomment and change DocumentRoot "/var/www/html/<FQDN>" ●Line 44 : Uncomment and change ServerName <Domain name>:443 ●Line 85 : Make it a comment and add it below # SSLCertificateFile /etc/pki/tls/certs/localhost.crt SSLCertificateFile /etc/letsencrypt/live/<FQDN>/cert.pem ●Line 93 : Make it a comment and add it below # SSLCertificateKeyFile /etc/pki/tls/private/localhost.key SSLCertificateKeyFile /etc/letsencrypt/live/<FQDN>/privkey.pem ●Line 103 : Add SSLCertificateChainFile /etc/letsencrypt/live/<FQDN>/chain.pem |
Apache restart
|
1 |
# systemctl restart httpd |
Allow https in Firewall
|
1 2 3 4 |
# firewall-cmd --add-service=https --permanent success # firewall-cmd --reload success |
2.2 Redirect HTTP communications to HTTPS
Create .htaccess under /var/www/html/[FQDN]/.
Contents of .htaccess
|
1 2 3 4 5 |
# vi /var/www/html/[FQDN]/.htaccess RewriteEngine On RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L] |
3. SSL/TLS (Let's Encrypt) settings on the mail server
3.1 Obtaining a Certificate for Mail Server
Obtain a certificate for the mail server, but it cannot be obtained in the same way as above, so the following with the "--standalone" option fails.
|
1 |
# certbot certonly --standalone -d mail.<domain name> |
If I stop the web server once and then do it, it succeeds as follows
|
1 2 |
# systemctl stop httpd.service # certbot certonly --standalone -d mail.<domain name> |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
Saving debug log to /var/log/letsencrypt/letsencrypt.log Requesting a certificate for mail.<domain name> Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/mail.<domain name>/fullchain.pem Key is saved at: /etc/letsencrypt/live/mail.<domain name>/privkey.pem This certificate expires on 2023-05-24. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
3.2 Postfix Configuration
|
1 2 3 4 5 6 7 8 9 10 11 |
# vi /etc/postfix/main.cf ●Per line 709, 715 : Comment #smtpd_tls_cert_file = /etc/pki/tls/certs/postfix.pem #smtpd_tls_key_file = /etc/pki/tls/private/postfix.key ● Add to the last line smtpd_use_tls = yes smtp_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_cert_file = /etc/letsencrypt/live/mail.<domain name>/fullchain.pem smtpd_tls_key_file = /etc/letsencrypt/live/mail.<domain name>/privkey.pem smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache |
|
1 2 3 4 5 6 7 8 9 10 11 |
# vi /etc/postfix/master.cf ●Line 19-22 : Uncomment submission inet n - n - - smtpd -o syslog_name=postfix/submission -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes ●Line 31-34 : Uncomment smtps inet n - n - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes |
3.3 Dovecot Configuration
|
1 2 3 4 5 6 |
# vi /etc/dovecot/conf.d/10-ssl.conf ●Line 8:Confirmation ssl = yes ●Line 14,15:Comment and add the following certificate/key file specification ssl_cert = </etc/letsencrypt/live/mail.<domain name>/fullchain.pem ssl_key = </etc/letsencrypt/live/mail.<domain name>/privkey.pem |
Allow Port 587 in firewall
|
1 2 |
# firewall-cmd --add-port=587/tcp --permanent # firewall-cmd --reload |
|
1 |
# systemctl restart postfix dovecot |
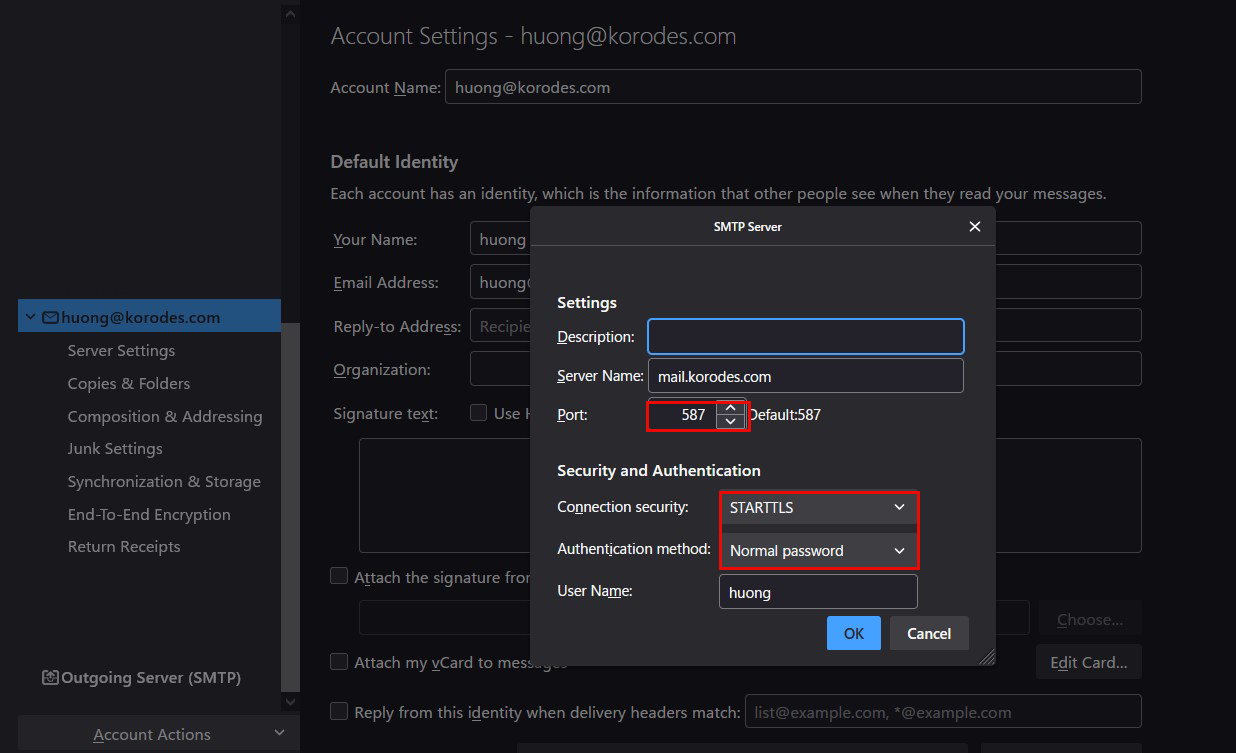
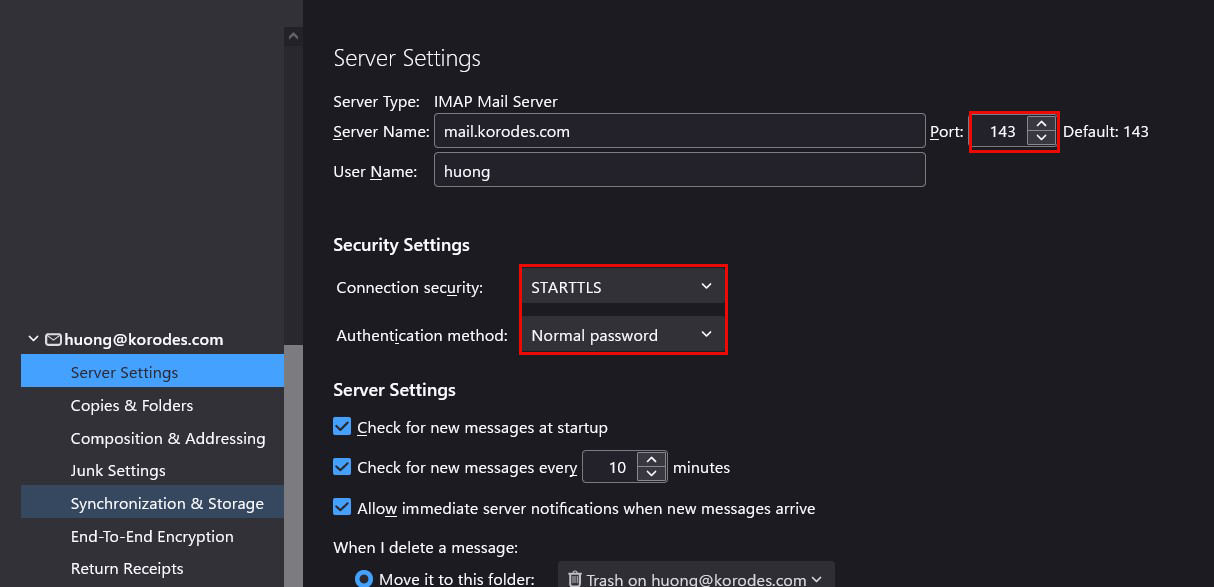
3.4 Thunderbird Settings
Receiving server
Port : 143
Connection security : STARTTLS
Authentication method : Normal password
Sending server
Port : 587
Connection security : STARTTLS
Authentication method : Normal password