Contents
Install Clamav ( anti-virus software )
1.Install Clam AntiVirus
|
1 |
# dnf -y install clamav clamd clamav-update |
2.Edit Clam AntiVirus configuration file
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# vi /etc/clamd.d/scan.conf ●Line 14. # Default: disabled LogFile /var/log/clamd.scan ← Uncomment ●Line 77. # Default: disabled PidFile /run/clamd.scan/clamd.pid ← Uncomment ●Line 96. # Path to a local socket file the daemon will listen on. # Default: disabled (must be specified by a user) LocalSocket /run/clamd.scan/clamd.sock ← Uncomment ●Line 219. # Run as another user (clamd must be started by root for this option to work) # Default: don't drop privileges #User clamscan ← comment-out |
3.Virus definition file update settings
|
1 2 3 4 5 6 7 8 9 10 11 |
# vi /etc/freshclam.conf ●Line 75. Insert a "#" at the beginning of the line "DatabaseMirror database.clamav.net" and Add "DatabaseMirror db.jp.clamav.net" #DatabaseMirror database.clamav.net DatabaseMirror db.jp.clamav.net ●Per line 151 Add "NotifyClamd /etc/clamd.d/scan.conf" #NotifyClamd /path/to/clamd.conf NotifyClamd /etc/clamd.d/scan.conf |
4.Virus definition file update
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
# freshclam ClamAV update process started at Mon Oct 17 16:28:12 2022 daily database available for download (remote version: 26691) Time: 0.9s, ETA: 0.0s [========================>] 57.27MiB/57.27MiB Testing database: '/var/lib/clamav/tmp.86f3a197d8/clamav-f8e5e9a4e35a43ccb613b710389fd3c0.tmp-daily.cvd' ... Database test passed. daily.cvd updated (version: 26691, sigs: 2008286, f-level: 90, builder: raynman) main database available for download (remote version: 62) Time: 2.0s, ETA: 0.0s [========================>] 162.58MiB/162.58MiB Testing database: '/var/lib/clamav/tmp.86f3a197d8/clamav-89bbce01172ebe46ef30173e4764af5c.tmp-main.cvd' ... Database test passed. main.cvd updated (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) bytecode database available for download (remote version: 333) Time: 0.1s, ETA: 0.0s [========================>] 286.79KiB/286.79KiB Testing database: '/var/lib/clamav/tmp.86f3a197d8/clamav-5ff8858020e095447d90edaeafa70cd8.tmp-bytecode.cvd' ... Database test passed. bytecode.cvd updated (version: 333, sigs: 92, f-level: 63, builder: awillia2) |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
# systemctl start clamd@scan ← clamd start # systemctl enable clamd@scan ← lamd auto-startup setting Created symlink /etc/systemd/system/multi-user.target.wants/clamd@scan.service → /usr/lib/systemd/system/clamd@.service. # systemctl is-enabled clamd@scan enabled # systemctl status clamd@scan ← operation check ● clamd@scan.service - clamd scanner (scan) daemon Loaded: loaded (/usr/lib/systemd/system/clamd@.service; enabled; vendor preset: d> Active: active (running) since Mon 2022-10-17 16:30:49 JST; 44s ago Docs: man:clamd(8) man:clamd.conf(5) https://www.clamav.net/documents/ Main PID: 1433 (clamd) Tasks: 2 (limit: 2274) Memory: 1.2G CPU: 13.851s CGroup: /system.slice/system-clamd.slice/clamd@scan.service mq 1433 /usr/sbin/clamd -c /etc/clamd.d/scan.conf Oct 17 16:30:49 Lepard clamd[1433]: ELF support enabled. Oct 17 16:30:49 Lepard clamd[1433]: Mail files support enabled. Oct 17 16:30:49 Lepard clamd[1433]: OLE2 support enabled. Oct 17 16:30:49 Lepard clamd[1433]: PDF support enabled. Oct 17 16:30:49 Lepard clamd[1433]: SWF support enabled. Oct 17 16:30:49 Lepard clamd[1433]: HTML support enabled. Oct 17 16:30:49 Lepard clamd[1433]: XMLDOCS support enabled. Oct 17 16:30:49 Lepard clamd[1433]: HWP3 support enabled. Oct 17 16:30:49 Lepard clamd[1433]: Self checking every 600 seconds. Oct 17 16:30:49 Lepard systemd[1]: Started clamd@scan.service - clamd scanner (scan) d> |
6.Conducted virus scan
■Download a test virus and perform a virus scan
■Download a test virus and perform a virus scan
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# wget http://www.eicar.org/download/eicar.com # clamscan --infected --remove --recursive /root/eicar.com: Win.Test.EICAR_HDB-1 FOUND /root/eicar.com: Removed. ----------- SCAN SUMMARY ----------- Known viruses: 8640327 Engine version: 0.103.7 Scanned directories: 1 Scanned files: 10 Infected files: 1 Data scanned: 0.02 MB Data read: 0.01 MB (ratio 2.00:1) Time: 18.415 sec (0 m 18 s) Start Date: 2022:10:17 16:32:48 End Date: 2022:10:17 16:33:06 |
7.Deployment of virus scan auto-execution scripts
|
1 |
# mkdir -p /var/www/system |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
# vi /var/www/system/clamscan.sh #!/bin/bash PATH=/usr/bin:/bin # excludeopt setup excludelist=/var/www/system/clamscan.exclude if [ -s $excludelist ]; then for i in `cat $excludelist` do if [ $(echo "$i"|grep \/$) ]; then i=`echo $i|sed -e 's/^\([^ ]*\)\/$/\1/p' -e d` excludeopt="${excludeopt} --exclude-dir=$i" else excludeopt="${excludeopt} --exclude=$i" fi done fi # signature update freshclam # virus scan clamscan --recursive --remove ${excludeopt} / |
|
1 2 3 4 |
# chmod 700 /var/www/system/clamscan.sh # echo "/sys/" >> /var/www/system/clamscan.exclude # echo "/proc/" >> /var/www/system/clamscan.exclude Exclude sys and proc directories. |
9.Scheduled virus scan
|
1 2 3 4 5 6 7 8 9 |
# crontab -e no crontab for root - using an empty one When installing cron # dnf install cronie cronie-anacron again # crontab -e 0 1 * * * /var/www/system/clamscan.sh > /dev/null 2>&1 |
Mail Server Install
1. Install Postfix
1.1 Install
Install Postfix and build an SMTP server
|
1 |
# dnf -y install postfix |
Check if Postfix is installed
|
1 2 |
# rpm -qa | grep postfix postfix-3.6.4-1.fc35.x86_64 |
1.2 Register Postfix to the service
|
1 2 |
# systemctl enable postfix.service Created symlink /etc/systemd/system/multi-user.target.wants/postfix.service → /usr/lib/systemd/system/postfix.service. |
|
1 2 |
# systemctl is-enabled postfix.service enabled |
1.3 Backup postfix configuration files, main.cf and master.cf files
|
1 2 |
# cp -p /etc/postfix/main.cf `date '+/etc/postfix/main.cf.%Y%m%d'` # cp -p /etc/postfix/master.cf `date '+/etc/postfix/master.cf.%Y%m%d'` |
1.4 Edit postfix configuration file
To prevent unauthorized mail relay, configure Postfix to require authentication even for outgoing mail, using Dovecot's SASL function.
To prevent unauthorized mail relay, configure Postfix to require authentication even for outgoing mail, using Dovecot's SASL function.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 |
# vi /etc/postfix/main.cf ●Per line 96: add #myhostname = virtual.domain.tld myhostname = mail.<domain name> ●Per line 103: Add your domain name #mydomain = domain.tld mydomain = <domain name> ●Per line 118: Uncomment myorigin = $mydomain ●Per line 135: change inet_interfaces = all ●Per line 138: change inet_protocols = ipv4 ●Per line 183: add Comment out around line 183 and add to line 184. #mydestination = $myhostname, localhost.$mydomain, localhost mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain ●Per line 287: add #mynetworks = 168.100.189.0/28, 127.0.0.0/8 #mynetworks = $config_directory/mynetworks #mynetworks = hash:/etc/postfix/network_table mynetworks = 192.168.11.0/24, 127.0.0.0/8 ←192.168.11.0/24 to suit your environment ●Per line 440: Uncomment Mail storage format #home_mailbox = Mailbox home_mailbox = Maildir/ ●Per line 447: add #mail_spool_directory = /var/mail mail_spool_directory = /var/spool/mail ●Per line 593: add #smtpd_banner = $myhostname ESMTP $mail_name #smtpd_banner = $myhostname ESMTP $mail_name ($mail_version) smtpd_banner = $myhostname ESMTP unknown ●Add the following to the last line # Limit send/receive mail size to 10M message_size_limit = 10485760 # Limit mailbox size to 1G mailbox_size_limit = 1073741824 # SMTP-Auth Settings smtpd_sasl_type = dovecot smtpd_sasl_path = private/auth smtpd_sasl_auth_enable = yes smtpd_sasl_security_options = noanonymous smtpd_sasl_local_domain = $mydomain smtpd_recipient_restrictions = permit_mynetworks, permit_auth_destination, permit_sasl_authenticated, reject |
Release SMTP port (port 25)
|
1 2 3 4 |
# firewall-cmd --add-service=smtp --permanent success # firewall-cmd --reload success |
1.5 Start Postfix
|
1 |
# systemctl enable --now postfix |
2.Dovecot Installation
2.1 Install
|
1 |
# dnf -y install dovecot |
2.2 Edit dovecot.conf file
|
1 2 3 4 5 6 7 8 |
# cp -p /etc/dovecot/dovecot.conf `date '+ /etc/dovecot/dovecot.conf.%Y%m%d'` # vi /etc/dovecot/dovecot.conf ●Per line 25: add # protocols = imap pop3 lmtp protocols = imap pop3 ●Line 30 : Uncomment # Remove [::] if listening for IPv4 only listen = * |
2.3 Edit 10-auth.conf file
|
1 2 3 4 5 6 |
# vi /etc/dovecot/conf.d/10-auth.conf ●Line 10 : Uncomment change If plain text authentication is also allowed disable_plaintext_auth = no ●Line 100 : add auth_mechanisms = plain login |
2.3 Edit 10-mail.conf file
|
1 2 3 |
# vi /etc/dovecot/conf.d/10-mail.conf ●Line 31 : add mail_location = maildir:~/Maildir |
2.4 Edit 10-master.conf file
|
1 2 3 4 5 6 7 8 |
# vi /etc/dovecot/conf.d/10-master.conf ●Line 107-109 : Uncommented and added # Postfix smtp-auth unix_listener /var/spool/postfix/private/auth { mode = 0666 user = postfix group = postfix } |
2.5 Edit 10-ssl.conf file
|
1 2 3 4 |
# vi /etc/dovecot/conf.d/10-ssl.conf ●Per line 8 Change "ssl = required" to "ssl = yes" ssl = yes |
2.6 Register dovecot as a service and start
|
1 2 |
# systemctl enable dovecot.service Created symlink /etc/systemd/system/multi-user.target.wants/dovecot.service → /usr/lib/systemd/system/dovecot.service. |
|
1 2 |
# systemctl is-enabled dovecot.service Enabled |
|
1 |
# systemctl start dovecot.service |
2.7 Permission port opening for POP/IMAP service with firewalld
POP is [110/TCP], IMAP is [143/TCP].
|
1 2 3 |
# firewall-cmd --permanent --add-service=pop3 # firewall-cmd --permanent --add-service=imap # firewall-cmd --reload |
3.Create mail user and check operation
3.1 User Account Creation
Mail client installation
|
1 |
# dnf -y install mailx |
Mailboxes are set to refer to Maildir
|
1 |
# echo 'export MAIL=$HOME/Maildir' >> /etc/profile.d/mail.sh |
Add user "linux"
|
1 2 3 4 5 6 |
# useradd linux # passwd linux Changing password for user root. New password: Retype new password: passwd: all authentication tokens updated successfully. |
3.2 operation check ①
Log in as an email user and send a test email.
Log in as an email user and send a test email.
|
1 2 3 4 5 6 |
# su - linux $ mail linux@localhost Subject: Test Mail mail test ← To end the text, type "." EOT |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
$ mail Heirloom Mail version 12.5 7/5/10. Type ? for help. "/home/linux/Maildir": 1 message 1 new >N 1 linux@korodes.com Wed May 11 13:05 17/506 "Test Mail" & 1 Message 1: From linux@korodes.com Wed May 11 13:05:10 2022 Return-Path: <linux@korodes.com> X-Original-To: linux@localhost Delivered-To: linux@localhost Date: Wed, 11 May 2022 13:05:10 +0900 To: linux@localhost Subject: test User-Agent: Heirloom mailx 12.5 7/5/10 Content-Type: text/plain; charset=us-ascii From: linux@korodes.com Status: Rmail test& q Held 1 message in /home/linux/Maildir |
3.3 operation check ②
Set up and confirm your account in Mozilla Thunderbird
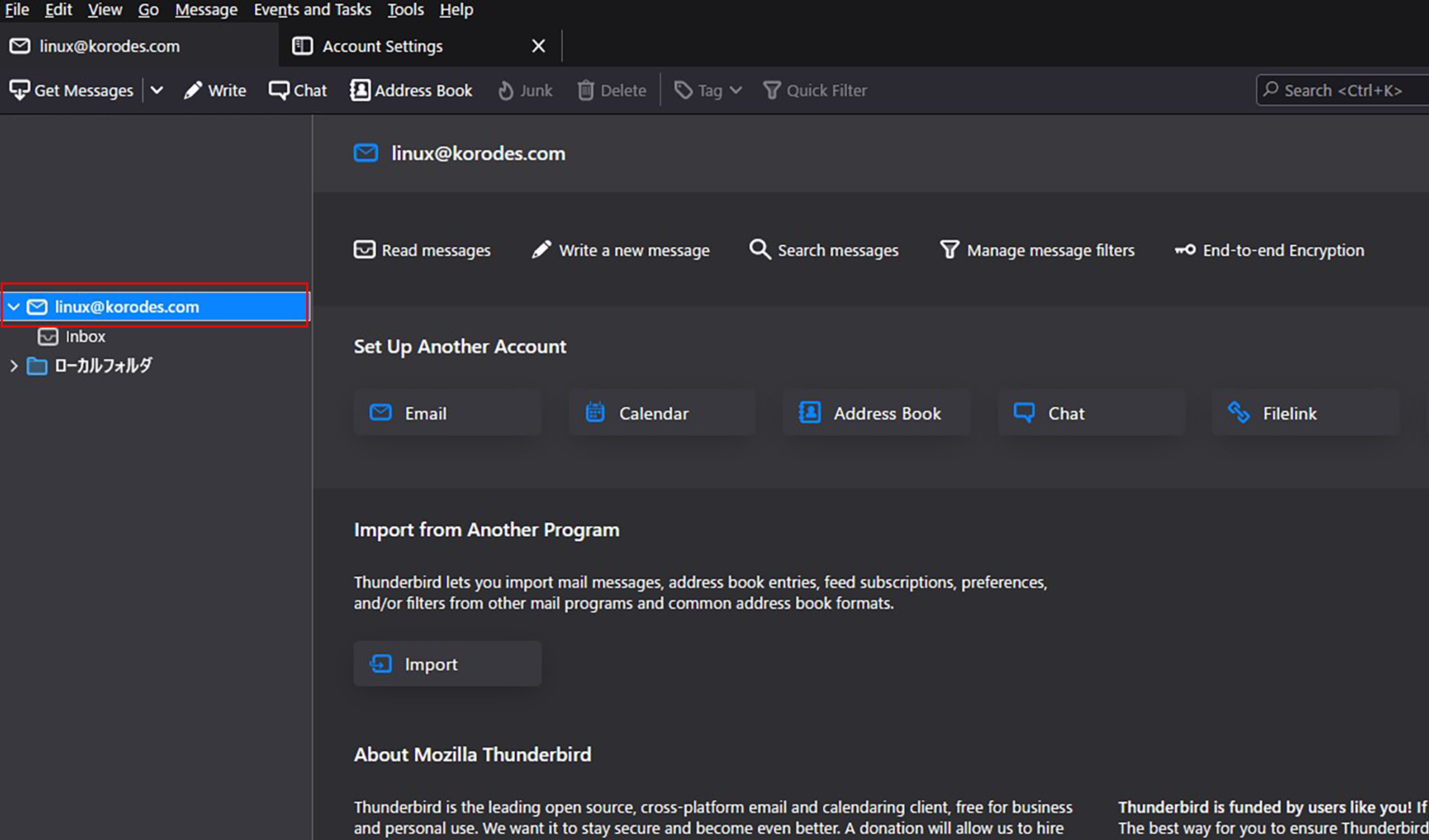
①Start Thunderbird, "Tools", "Account Settings".
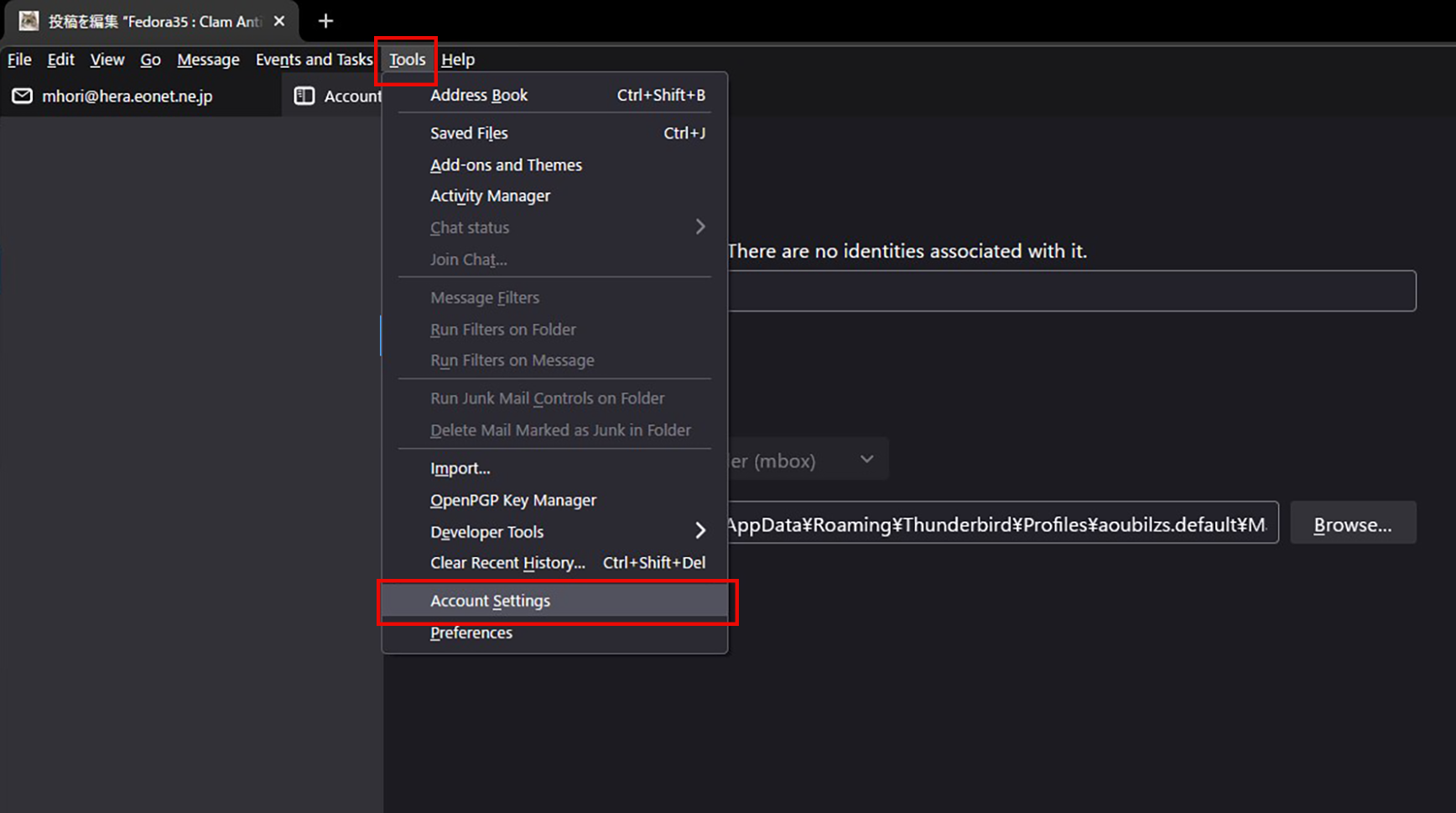
Set up and confirm your account in Mozilla Thunderbird
①Start Thunderbird, "Tools", "Account Settings".

②"Account Actions," "Add Email Account."
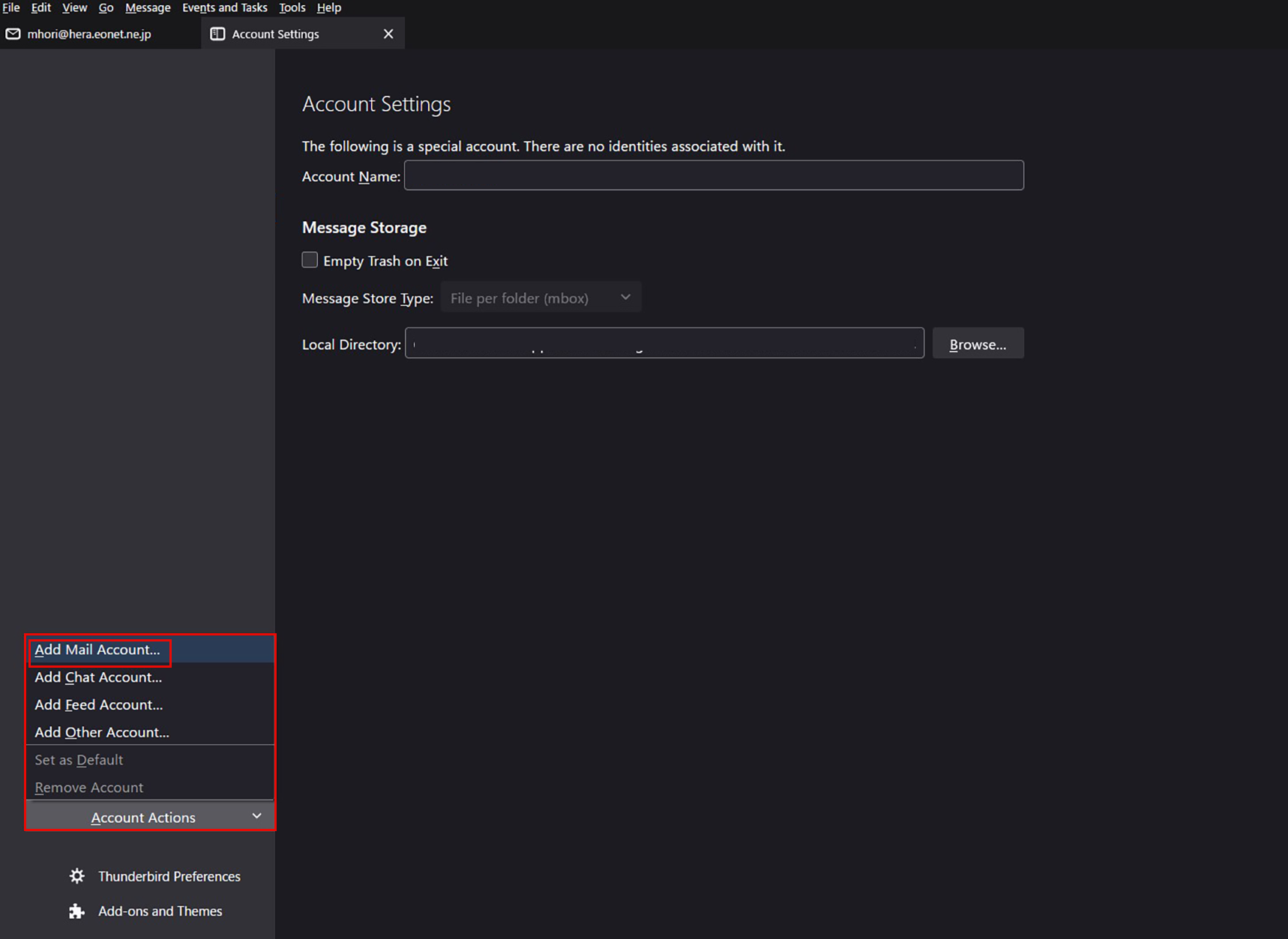

③"Your full name" is an arbitrary name
The "Email address" is "linux@korodes.com," which I just added.
Password is user (linux) password
Click on "Configure Manually"
The "Email address" is "linux@korodes.com," which I just added.
Password is user (linux) password
Click on "Configure Manually"
④Set "Incoming Server" and "Outgoing Server" as shown below and click "Re-test".
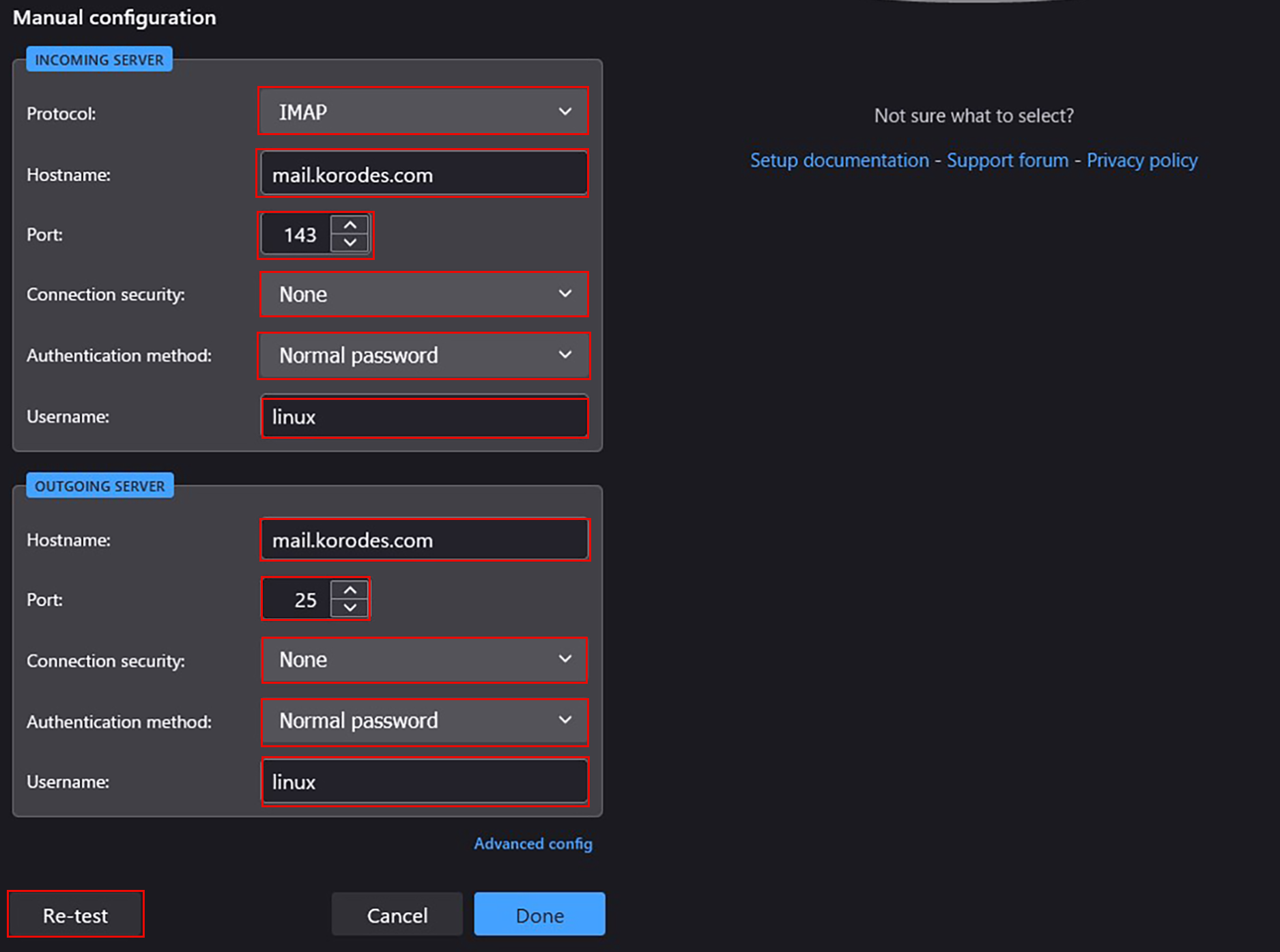

⑤The "Server Found" message appears.
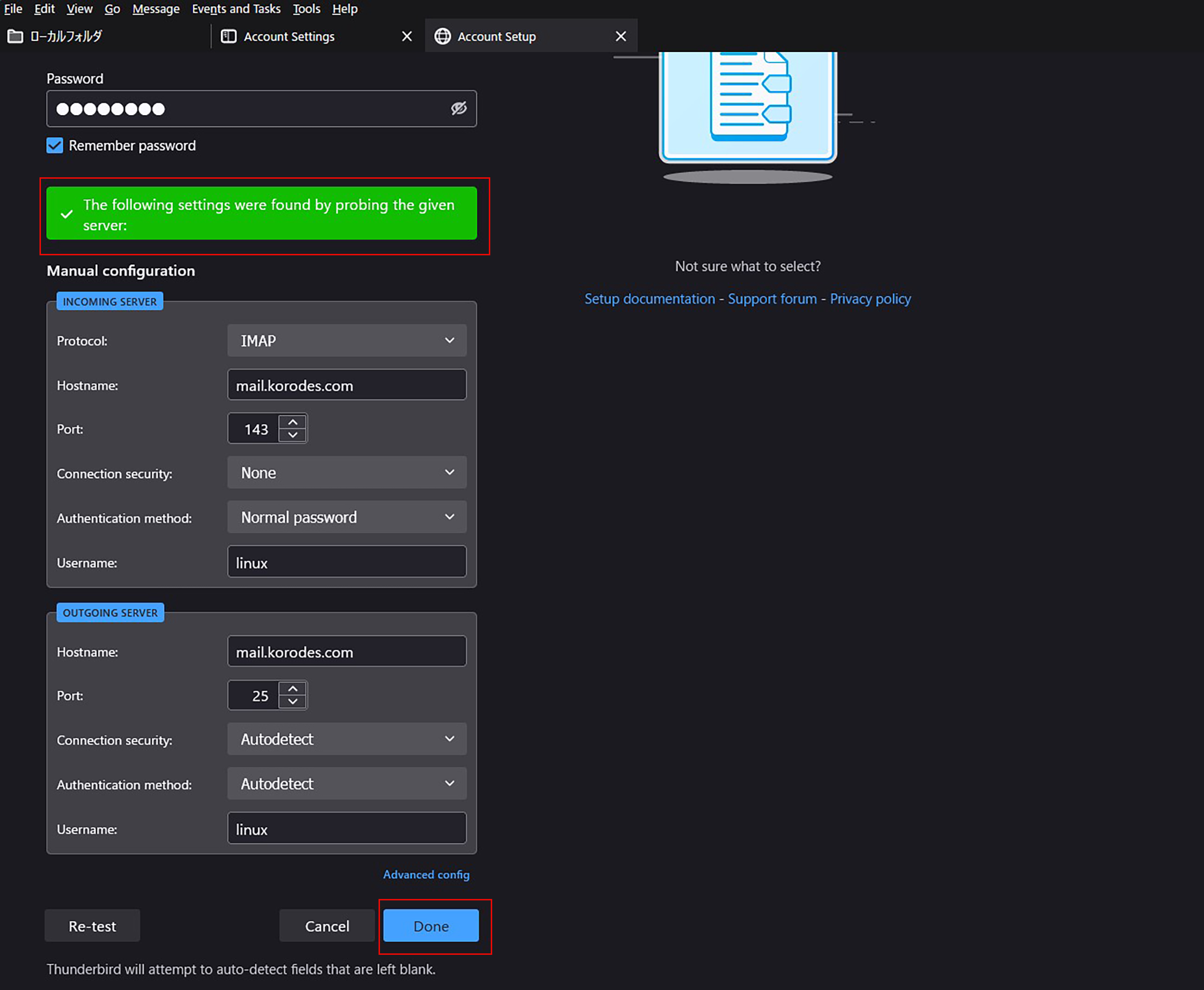
After clicking "Done" the following "Warning" appears, but there is no problem, so click "Confirm.
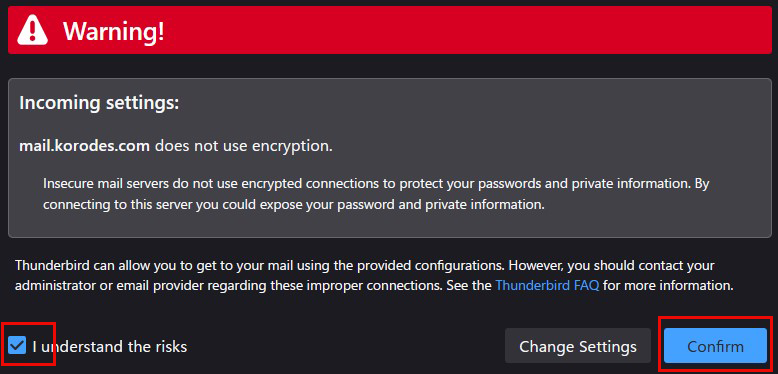

⑥Click "Finish"
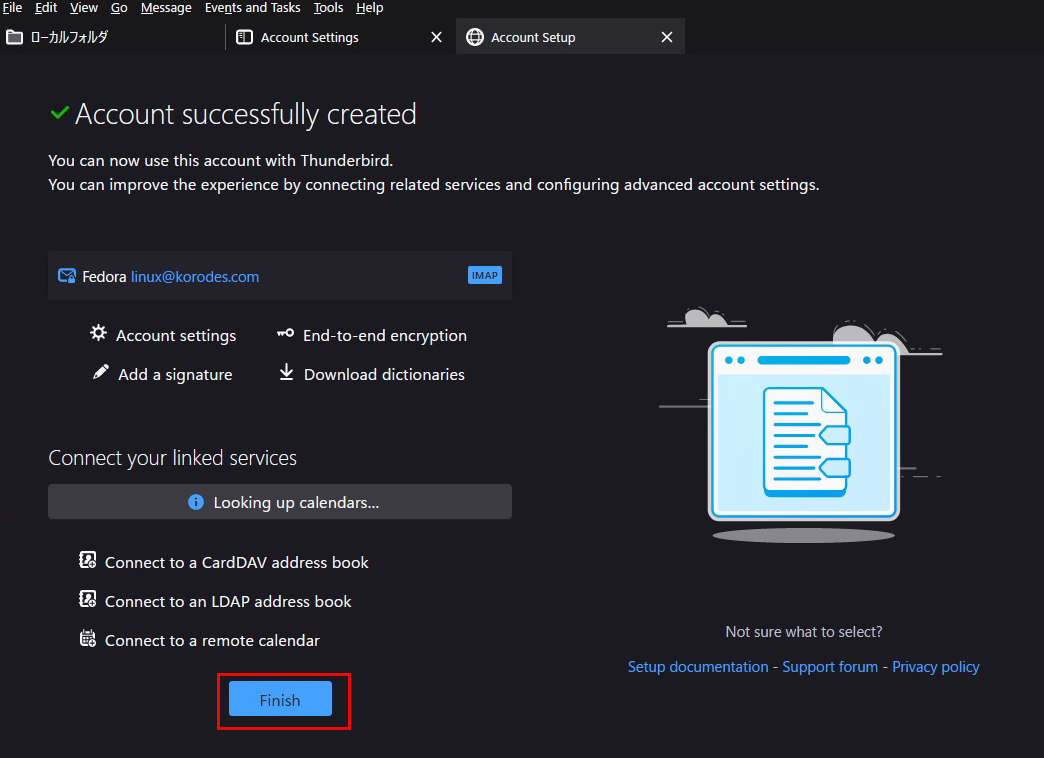
⑦Your account has been created.

Mail Server : Postfix + Clamav + Amavisd+SpamAssassin
1.Real-time scanning of E-mails
①Install Amavisd and Clamav Server
|
1 |
# dnf -y install amavisd-new clamd perl-Digest-SHA1 perl-IO-stringy |
➁Configuration File Edit
|
1 2 3 4 5 6 7 |
# vi /etc/clamd.d/scan.conf ●Line 77:change PidFile /var/run/clamd.scan/clamd.pid ●Line 81:Uncomment TemporaryDirectory /var/tmp ●Line 96:change LocalSocket /var/run/clamd.scan/clamd.sock |
|
1 2 3 |
# touch /var/log/clamd.scan # chown clamscan. /var/log/clamd.scan # systemctl enable clamd@scan |
➂Setup and start Amavisd
|
1 2 3 4 5 6 7 8 9 10 11 |
# vi /etc/amavisd/amavisd.conf ●Delete # at the beginning of the line per line 13 @bypass_spam_checks_maps = (1); # controls running of anti-spam code ●Line 23:Change to your domain name $mydomain = 'Domain name'; ●Per Line 28 : Comment out #$QUARANTINEDIR = undef; # -Q ●Per Line 125 : Comment out # $virus_admin = undef; # notifications recip ●Line 158:Uncomment and change to your own host name $myhostname = 'mail.<domain>'; |
|
1 2 |
# systemctl enable amavisd Created symlink /etc/systemd/system/multi-user.target.wants/amavisd.service → /usr/lib/systemd/system/amavisd.service. |
④Postfix Configuration
|
1 2 3 |
# vi /etc/postfix/main.cf # Add to the last line content_filter=smtp-amavis:[127.0.0.1]:10024 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
# vi /etc/postfix/master.cf # Add to the last line smtp-amavis unix - - n - 2 smtp -o smtp_data_done_timeout=1200 -o smtp_send_xforward_command=yes -o disable_dns_lookups=yes 127.0.0.1:10025 inet n - n - - smtpd -o content_filter= -o local_recipient_maps= -o relay_recipient_maps= -o smtpd_restriction_classes= -o smtpd_client_restrictions= -o smtpd_helo_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o mynetworks=127.0.0.0/8 -o strict_rfc821_envelopes=yes -o smtpd_error_sleep_time=0 -o smtpd_soft_error_limit=1001 -o smtpd_hard_error_limit=1000 |
|
1 |
# systemctl restart postfix |
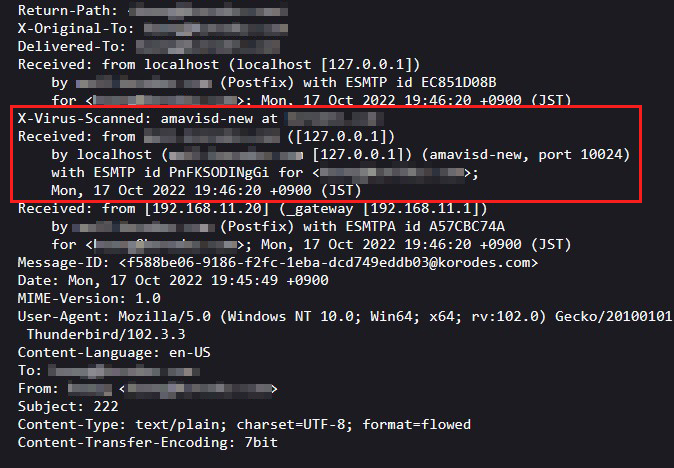
⑤I sent a test email to myself in Thunderbird, and in the header display section of the received email, I see the following
X-Virus-Scanned: amavisd-new at
X-Virus-Scanned: amavisd-new at
2.Email spam protection
①SpamAssassin installed to prevent spam
|
1 2 3 4 |
# dnf -y install spamassassin spamass-milter-postfix # systemctl start spamassassin # systemctl enable spamassassin Created symlink /etc/systemd/system/multi-user.target.wants/spamassassin.service → /usr/lib/systemd/system/spamassassin.service. |
②SpamAssassin Settings
|
1 2 3 |
# vi /etc/mail/spamassassin/v310.pre ●Delete # at the beginning of the line per line 24 loadplugin Mail::SpamAssassin::Plugin::DCC |
③SpamAssassin configuration file modernization script
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
# vi /var/www/system/spamassassin-update.sh #!/bin/bash cd /etc/mail/spamassassin wget -q https://github.com/kittyfreak/spamassassin_user_prefs/archive/refs/heads/main.zip [ $? -ne 0 ] && exit unzip main.zip >/dev/null 2>&1 [ $? -ne 0 ] && exit rm -f main.zip mv spamassassin_user_prefs-main/user_prefs . rm -rf spamassassin_user_prefs-main diff user_prefs user_prefs.org > /dev/null 2>&1 if [ $? -ne 0 ]; then cp user_prefs local.cf echo "report_safe 0" >> local.cf echo "rewrite_header Subject ***SPAM***" >> local.cf # SpamAssassin restart if [ -f /etc/rc.d/init.d/spamassassin ]; then /etc/rc.d/init.d/spamassassin restart > /dev/null else systemctl restart spamassassin > /dev/null fi fi cp user_prefs user_prefs.org |
Grant execute permission to the spamassassin-update script and run it
|
1 2 |
# chmod +x /var/www/system/spamassassin-update.sh # /var/www/system/spamassassin-update.sh |
Make sure that the SpamAssassin configuration file in the /etc/mail/spamassassin directory is created with the current day's date.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# ls -l /etc/mail/spamassassin total 1612 drwxr-xr-x 2 root root 40 Oct 17 19:20 channel.d -rw-r--r-- 1 root root 1194 Jan 22 2022 init.pre -rw-r--r-- 1 root root 499337 Oct 17 20:09 local.cf drwx------ 2 root root 6 Jan 22 2022 sa-update-keys -rw-r--r-- 1 root root 62 Jan 22 2022 spamassassin-default.rc -rwxr-xr-x 1 root root 39 Jan 22 2022 spamassassin-helper.sh -rw-r--r-- 1 root root 55 Jan 22 2022 spamassassin-spamc.rc -rw-r--r-- 1 root root 499289 Dec 29 2021 user_prefs -rw-r--r-- 1 root root 499289 Oct 17 20:09 user_prefs.org -rw-r--r-- 1 root root 2523 Oct 17 20:07 v310.pre -rw-r--r-- 1 root root 1194 Jan 22 2022 v312.pre -rw-r--r-- 1 root root 2416 Jan 22 2022 v320.pre -rw-r--r-- 1 root root 1237 Jan 22 2022 v330.pre -rw-r--r-- 1 root root 1020 Jan 22 2022 v340.pre -rw-r--r-- 1 root root 1309 Jan 22 2022 v341.pre -rw-r--r-- 1 root root 1469 Jan 22 2022 v342.pre -rw-r--r-- 1 root root 1264 Jan 22 2022 v343.pre |
Set up cron to automatically run a script daily that updates the SpamAssassin configuration file
|
1 2 |
# crontab -e 0 2 * * * /var/www/system/spamassassin-update.sh > /dev/null 2>&1 |
④Integrate SpamAssassin into Postfix
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 |
# vi /etc/postfix/master.cf ●Add "#" to the beginning of line 11 and add SpamAssassin setting to line 12 # smtp inet n - n - - smtpd smtp inet n - n - - smtpd -o content_filter=spamassassin ●Add to last line smtp-amavis unix - - n - 2 smtp -o smtp_data_done_timeout=1200 -o smtp_send_xforward_command=yes -o disable_dns_lookups=yes 127.0.0.1:10025 inet n - n - - smtpd -o content_filter= -o local_recipient_maps= -o relay_recipient_maps= -o smtpd_restriction_classes= -o smtpd_client_restrictions= -o smtpd_helo_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o mynetworks=127.0.0.0/8 -o strict_rfc821_envelopes=yes -o smtpd_error_sleep_time=0 -o smtpd_soft_error_limit=1001 -o smtpd_hard_error_limit=1000 spamassassin unix - n n - - pipe user=nobody argv=/usr/bin/spamc -e /usr/sbin/sendmail.postfix -oi -f ${sender} ${recipient} |
⑤Restart postfix
|
1 |
# systemctl restart postfix |
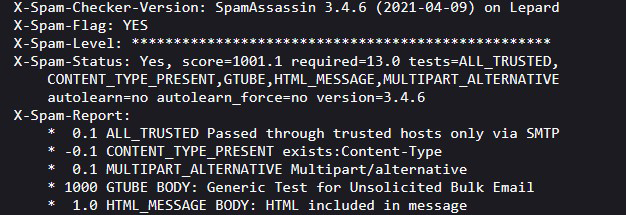
⑥If you send an e-mail to yourself in Thunderbird with the following information in the body, the following will appear in the header.
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X