Contents
1. ClamAV (antivirus software) implementation
1.1 Install ClamAV
|
1 |
# zypper -n install clamav |
1.2 Definition File Update
①Virus Definition File Update Settings
|
1 2 3 4 |
# vi /etc/freshclam.conf # Line 74: Comment out and add below #DatabaseMirror database.clamav.net DatabaseMirror db.jp.clamav.net |
②Virus definition file update
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# freshclam ClamAV update process started at Sun Oct 5 10:23:21 2025 daily database available for download (remote version: 27780) Time: 3.9s, ETA: 0.0s [========================>] 61.73MiB/61.73MiB Testing database: '/var/lib/clamav/tmp.629dfccf45/clamav-7d79d7b2241f28eefe31b518405bede7.tmp-daily.cvd' ... Database test passed. daily.cvd updated (version: 27780, sigs: 2076928, f-level: 90, builder: tomjudge) main database available for download (remote version: 62) Time: 11.2s, ETA: 0.0s [========================>] 162.58MiB/162.58MiB Testing database: '/var/lib/clamav/tmp.629dfccf45/clamav-a426626c2ce5f5e99a2b8fae52cd589c.tmp-main.cvd' ... Database test passed. main.cvd updated (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) bytecode database available for download (remote version: 339) Time: 0.1s, ETA: 0.0s [========================>] 275.10KiB/275.10KiB Testing database: '/var/lib/clamav/tmp.629dfccf45/clamav-06919a851161eb9f47743f136b8a4d16.tmp-bytecode.cvd' ... Database test passed. bytecode.cvd updated (version: 339, sigs: 80, f-level: 90, builder: nrandolp) WARNING: Clamd was NOT notified: Can't connect to clamd through /run/clamav/clamd.sock: No such file or directory |
Finally, the message "WARNING: Clamd was NOT notified: Can't connect to clamd through /run/clamav/clamd-socket: No such file or directory" appears, but this is not a problem.
1.3 Functionality Verification
①If no virus is detected
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
# cd # clamscan --infected --remove --recursive ----------- SCAN SUMMARY ----------- Known viruses: 8708646 Engine version: 1.4.3 Scanned directories: 6 Scanned files: 5 Infected files: 0 Data scanned: 0.02 MB Data read: 0.01 MB (ratio 2.00:1) Time: 15.437 sec (0 m 15 s) Start Date: 2025:10:05 10:25:19 End Date: 2025:10:05 10:25:34 |
➁When a virus is detected
Download the test virus and scan it
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# wget https://secure.eicar.org/eicar.com.txt # clamscan --infected --remove --recursive /root/eicar.com.txt: Win.Test.EICAR_HDB-1 FOUND /root/eicar.com.txt: Removed. ----------- SCAN SUMMARY ----------- Known viruses: 8708646 Engine version: 1.4.3 Scanned directories: 6 Scanned files: 7 Infected files: 1 Data scanned: 0.02 MB Data read: 0.01 MB (ratio 2.00:1) Time: 15.611 sec (0 m 15 s) Start Date: 2025:10:05 10:27:37 End Date: 2025:10:05 10:27:52 |
1.4 Implementation of an Automatic Virus Scan Script
①Creating the Script Storage Directory
|
1 |
# mkdir -p /srv/www/system |
②Automatic Script Creation
# cd /srv/www/system
Create clamscan.sh in /srv/www/system with the following content:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
# vi clamscan.sh #!/bin/bash PATH=/usr/bin:/bin # excludeopt setup excludelist=/srv/www/system/clamscan.exclude if [ -s $excludelist ]; then for i in `cat $excludelist` do if [ $(echo "$i"|grep \/$) ]; then i=`echo $i|sed -e 's/^\([^ ]*\)\/$/\1/p' -e d` excludeopt="${excludeopt} --exclude-dir=$i" else excludeopt="${excludeopt} --exclude=$i" fi done fi # signature update freshclam # virus scan clamscan --recursive --remove ${excludeopt} / |
Grant execution permissions to the script
|
1 |
# chmod 700 clamscan.sh |
The sys directory and proc directory cannot be scanned per specification, so exclude them.
Also, openSUSE creates a large number of snapshots, so exclude it.
|
1 2 3 |
# echo "/sys/" >> /srv/www/system/clamscan.exclude # echo "/proc/" >> /srv/www/system/clamscan.exclude # echo "/.snapshots/" >> /srv/www/system/clamscan.exclude |
Scheduling Regular Virus Scans
Install cronie
|
1 |
# zypper install cronie |
|
1 2 |
# crontab -e 0 1 * * * /srv/www/system/clamscan.sh > /dev/null 2>& |
Run "/srv/www/system/clamscan.sh" to scan the entire system.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# /srv/www/system/clamscan.sh ----------- SCAN SUMMARY ----------- Known viruses: 8708646 Engine version: 1.4.3 Scanned directories: 9294 Scanned files: 57788 Infected files: 0 Data scanned: 6872.55 MB Data read: 3497.95 MB (ratio 1.96:1) Time: 805.570 sec (13 m 25 s) Start Date: 2025:10:05 10:31:45 End Date: 2025:10:05 10:45:11 |
2. Mail Server Installation
2.1 Postfix Installation
①Install Postfix to build an SMTP server.
|
1 |
# zypper -n install postfix |
②Postfix Configuration
To prevent unauthorized mail relaying, configure Postfix to require authentication for outgoing mail using the SASL feature of Dovecot, described later.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 |
# vi /etc/postfix/main.cf # Line 108: Hostname specification myhostname = mail.[domain] ←Self-hosted name # Line 114: Uncomment and specify the domain name mydomain = [domain] ←Custom domain name # Line 130: Uncomment myorigin = $mydomain # Line 294: Uncomment and append your own network mynetworks = 127.0.0.0/8, 192.168.11.0/24 ←Self-network # Line 451: Uncomment and use Maildir format home_mailbox = Maildir/ # Around line 715: Change inet_interfaces = all # Line 720: Addendum mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain # Lines 734, 735 # Limit mailbox size as needed (example below is 1G) mailbox_size_limit = 1073741824 # Limit the size of sent and received emails as needed (example below: 10MB) message_size_limit = 10485760 # Line 747: Addendum smtpd_recipient_restrictions = permit_mynetworks, permit_auth_destination, permit_sasl_authenticated, reject # Around line 769: Change smtpd_sasl_auth_enable = yes # Around lines 774 and 775: Comment them out and add the following below them. #smtpd_sasl_type = cyrus #smtpd_sasl_path = smtpd smtpd_sasl_type = dovecot smtpd_sasl_path = private/auth smtpd_sasl_security_options = noanonymous smtpd_sasl_local_domain = $myhostname |
|
1 2 |
# systemctl start postfix # systemctl enable postfix |
③If Firewalld is enabled, you must allow the SMTP service. SMTP uses port 25/TCP.
|
1 2 3 4 |
# firewall-cmd --add-service=smtp --permanent success # firewall-cmd --reload success |
2.2 Dovecot Installation
The version of Dovecot being installed this time is 2.4.1, and the configuration has changed significantly from 2.3.x.
There is virtually no information available about Dovecot 2.4.1; the only resource is the official documentation on the website.
I have configured it based on my own judgment, so please point out any errors if you find them.
①Install
|
1 |
# zypper -n install dovecot |
➁Dovecot Configuration
Configure Dovecot to enable SASL functionality for Postfix.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
# vi /etc/dovecot/dovecot.conf # Line 21: Changes and Additions protocols { imap = yes # lmtp = yes pop3 = yes } # Line 34: Comment it out and add below it #protocols = imap pop3 lmtp protocols = imap pop3 # Add around line 40 listen = * # Change the namespace inbox around line 44 as follows: namespace inbox { inbox = yes separator = / mail_driver = maildir # mail_path = ~/Maildir # mail_inbox_path = ~/Maildir/.INBOX mail_path = /home/%{user}/Maildir } Add to the last line service auth { # Postfix smtp-auth unix_listener /var/spool/postfix/private/auth { mode = 0666 user = postfix group = postfix } } |
➂Dovecot Startup and Automatic Execution
|
1 2 3 |
# systemctl start dovecot # systemctl enable dovecot Created symlink /etc/systemd/system/multi-user.target.wants/dovecot.service → /usr/lib/systemd/system/dovecot.service. |
④If Firewalld is enabled, you must allow POP/IMAP services.
POP uses port 110/TCP, and IMAP uses port 143/TCP.
|
1 2 3 4 |
# firewall-cmd --add-service={pop3,imap} --permanent success # firewall-cmd --reload success |
2.3 User Account Registration
This time, we will register the OS user "huong".
① Install the email client
|
1 |
# zypper -n install mailx |
②The mailbox is configured to reference Maildir.
|
1 |
# echo 'export MAIL=$HOME/Maildir' >> /etc/profile.d/mail.sh |
※If a Maildir directory has not been created in the home directory of the existing user (huong), create it manually as follows:
|
1 2 3 4 |
# mkdir -p /home/huong/Maildir/{new,cur,tmp} # chown -R huong:huong /home/huong/Maildir/ # chmod 700 /home/huong/Maildir # chmod 700 /home/huong/Maildir/{new,cur,tmp} |
2.4 Operation Verification
Configure your account in the free email client Thunderbird and verify it works.
However, depending on your provider, the outgoing server may use port 587, so make sure to open port 587 in your firewall settings.
|
1 2 |
# firewall-cmd --add-port=587/tcp --permanent # firewall-cmd --reload |
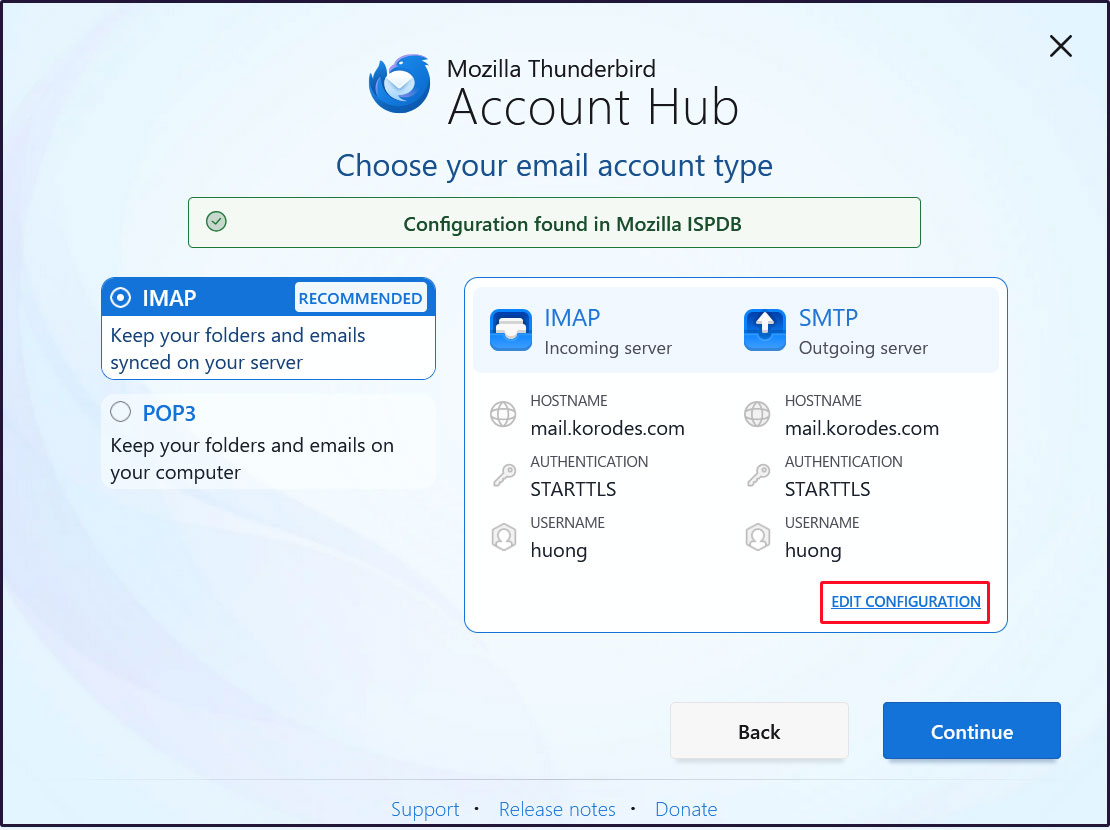
Set up and verify your account in Mozilla Thunderbird (for OS user huong as an email user)
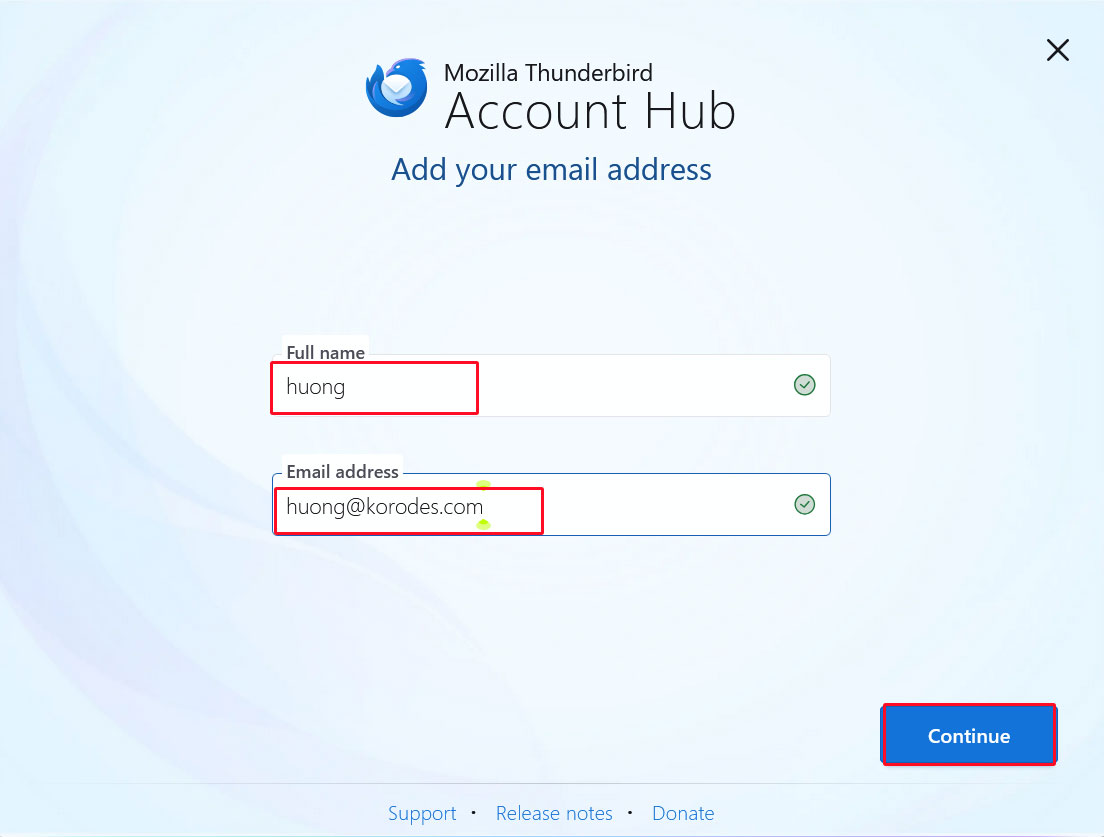
Launch Thunderbird, click [New Account] > [Email] in the [three-bar] menu at the top right
Full name: Any name
Email address: huong@[domain name]
Enter each field and click "Continue".
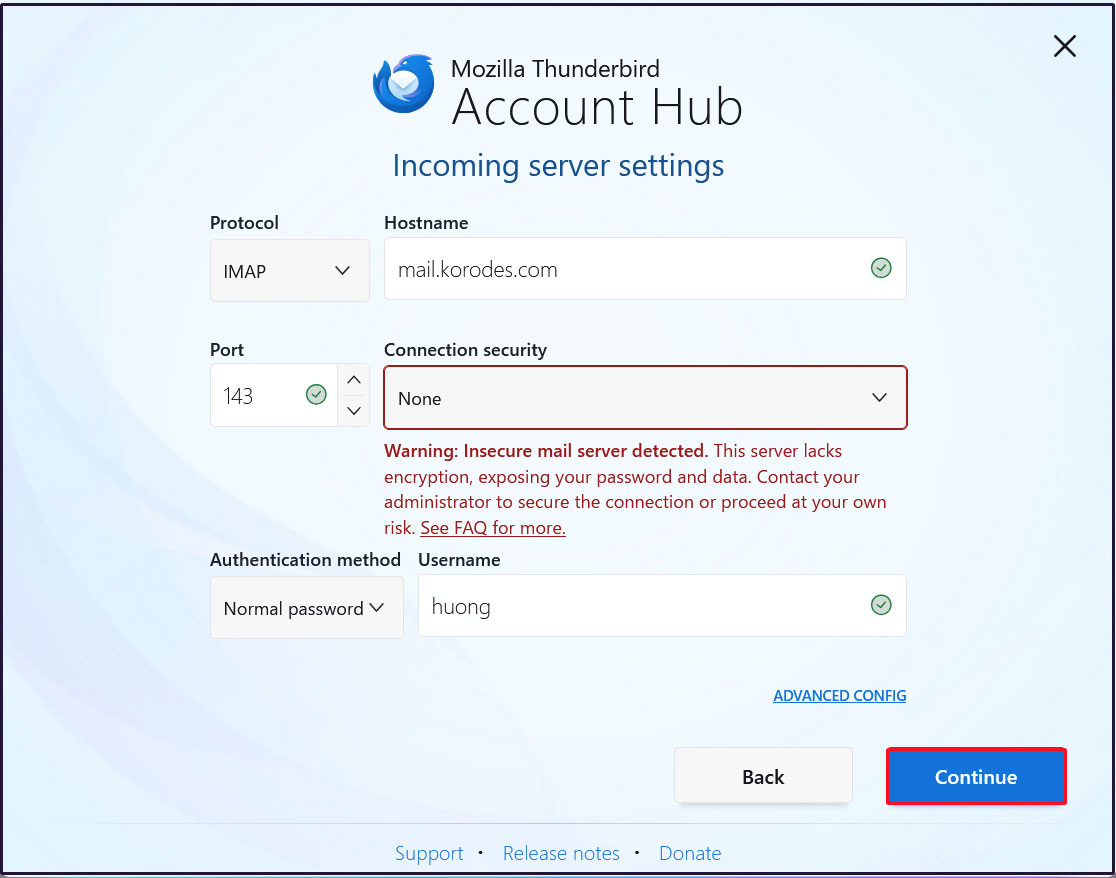
Incoming Server Settings
Set [Connection security] to [None] and click [Continue]
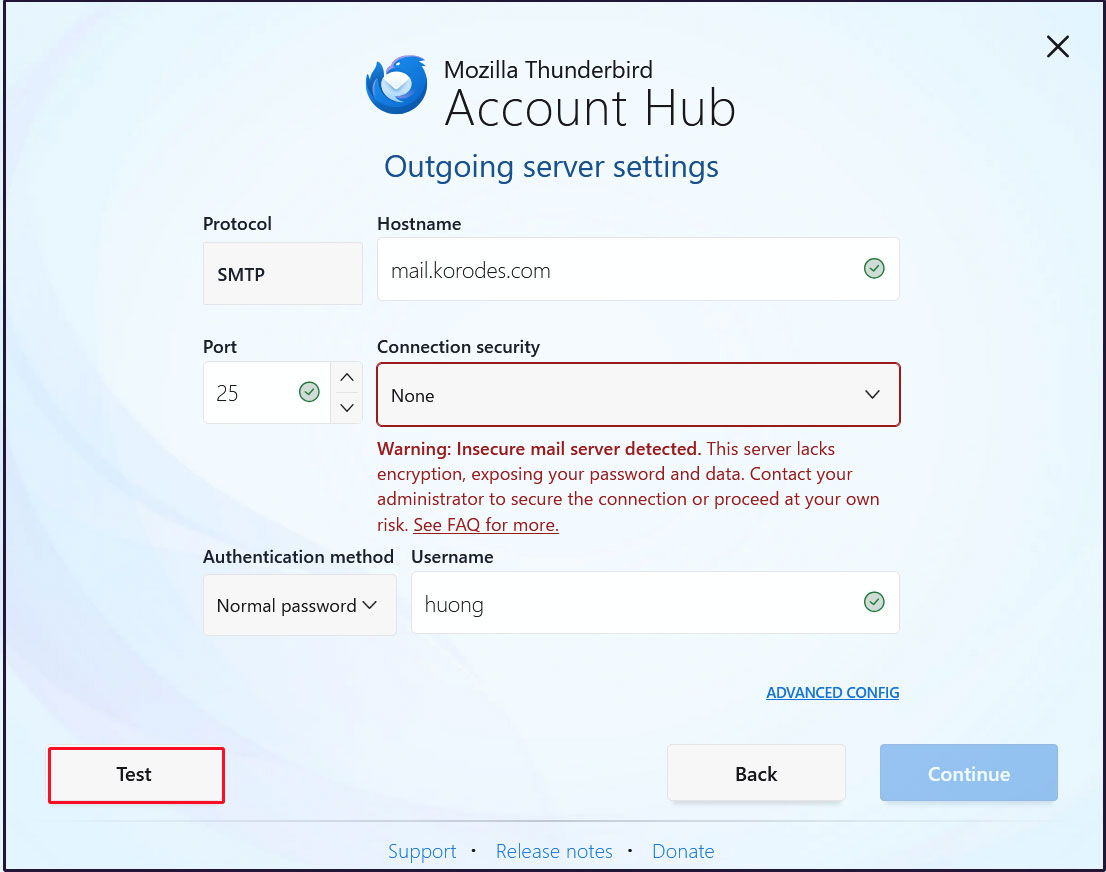
Outgoing Server Settings
Set [Connection security] to [None] and click [Test]
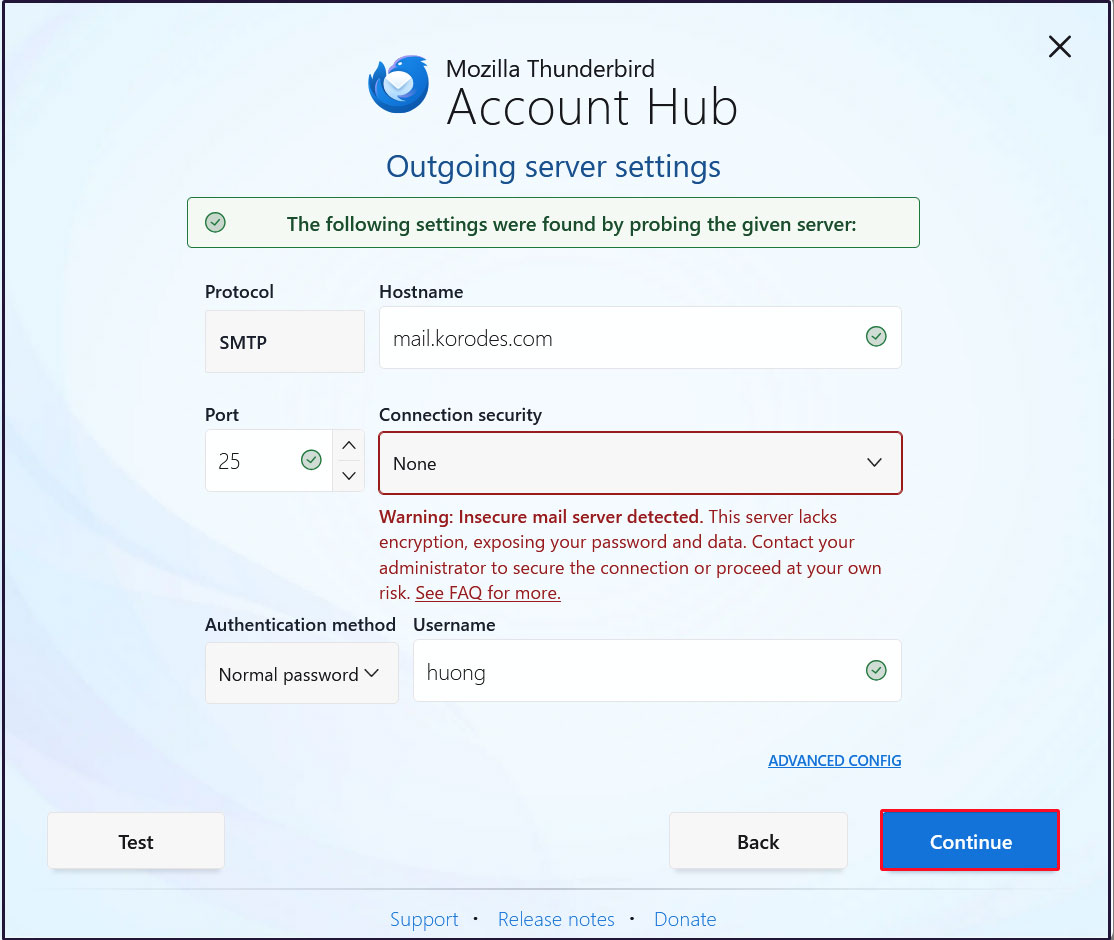
Click [Continue]
Enter the user's password in the [Password] field and click [Continue].
Click [Continue]
Your email account has been successfully created. Click [Finish].
3. Mail Server : Postfix + Clamav + clamav-milter+SpamAssassin
3.1 Real-time email scanning
①clamav-milter Installation
Perform virus checks on emails at the mail server side using Clam AntiVirus.
Integration between the mail server and Clam AntiVirus is achieved using clamav-milter.
|
1 |
# zypper -n install clamav-milter |
➁clclamav-milter configuration
Editing the clamav-milter configuration file
Regarding the UNIX socket permissions for clamav-milter, most sources recommend setting them to "660". However, in my environment, this caused it to fail to start. Although it poses a security risk, I set them to "666".
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# vi /etc/clamav-milter.conf Line 26: Change MilterSocketMode 666 ← Specify the access permissions for the UNIX socket of clamav-milter Around line 166: Add # Action to be performed on infected messages # Default: Quarantine #OnInfected Quarantine OnInfected Blackhole ← Delete virus-infected emails Around line 188: Add # Note that while "Replace" can potentially break DKIM signatures, "Add" may # confuse procmail and similar filters. # Default: no #AddHeader Replace AddHeader Yes ← Output a message in the email header indicating that a virus check has been performed. |
➂clamav-milter startup and automatic startup configuration
|
1 2 3 4 |
# systemctl start clamav-milter # systemctl enable clamav-milter Created symlink /etc/systemd/system/multi-user.target.wants/clamav-milter.service → /usr/lib/systemd/system/clamav-milter.service. |
④Postfix and ClamAV-Milter Integration Configuration
Editing the Postfix Configuration File
|
1 2 3 4 5 |
# vi /etc/postfix/main.cf Add the following milter_default_action = tempfail smtpd_milters = unix:/run/clamav/clamav-milter.sock non_smtpd_milters = unix:/run/clamav/clamav-milter.sock |
⑤Add the postfix user to the clamilt group
For some reason, the clamilt group user wasn't created during installation, so I'll create it now.
|
1 2 |
# groupadd clamilt # useradd -g clamilt clamilt |
Add the postfix user to the clamilt group
|
1 |
# usermod -G clamilt -a postfix |
⑥Postfix Configuration Update
|
1 |
# systemctl restart postfix |
⑦Check in Thunderbird
Send an empty email to yourself in Thunderbird. In the header display section of the received email, the following should appear:
X-Virus-Scanned: clamav-milter 1.4.3 at lepard
X-Virus-Status: Clean
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
Return-Path: <xxxxx@xxxxxxx.com>
X-Original-To: xxxxx@xxxxxxx.com
Delivered-To: xxxxx@xxxxxxx.com
Received: from [192.168.11.6] (buffalo.setup [192.168.11.1])
by mail.xxxxxxx.com (Postfix) with ESMTPA id 4B4E6D2D1
for <xxxxx@xxxxxxx.com>; Mon, 06 Oct 2025 19:05:40 +0900 (JST)
Message-ID: <62b016f4-f943-4d28-a0db-80fca430dd70@xxxxxxx.com>
Date: Mon, 6 Oct 2025 19:05:40 +0900
MIME-Version: 1.0
User-Agent: Mozilla Thunderbird
From: xxxxx <xxxxx@xxxxxxx.com>
Content-Language: en-US
To: xxxxx <xxxxx@xxxxxxx.com>
Content-Type: text/plain; charset=UTF-8; format=flowed
Content-Transfer-Encoding: 7bit
X-Virus-Scanned: clamav-milter 1.4.3 at lepard
X-Virus-Status: Clean
Send yourself an email with the body text "X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*" and verify that the email is discarded and does not arrive.
3.2 Email Spam Prevention
3.2.1 SpamAssassin・spamass-milter・postfix Settings
①SpamAssassin・spamass-milter install
|
1 |
# zypper -n install spamassassin |
spamass-milter was not found in the official repository, so we have added an experimental one to the repository and installed it.
|
1 2 3 |
# zypper addrepo https://download.opensuse.org/repositories/server:mail/16.0/server:mail.repo # zypper refresh # zypper install spamass-milter |
➁SpamAssassin startup
|
1 |
# systemctl start spamd |
➂SpamAssassin Configuration
|
1 2 3 4 |
# vi /etc/mail/spamassassin/v310.pre Remove the # at the beginning of line 24. loadplugin Mail::SpamAssassin::Plugin::DCC |
④SpamAssassin Configuration File Update Script
Create script under /etc/cron.daily
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
# vi /etc/cron.daily/spamassassin-update.sh #!/bin/bash # Download the latest version of the SpamAssassin configuration file cd /etc/mail/spamassassin wget -q https://github.com/kittyfreak/spamassassin_user_prefs/archive/refs/heads/main.zip [ $? -ne 0 ] && exit unzip main.zip >/dev/null 2>&1 [ $? -ne 0 ] && exit rm -f main.zip mv spamassassin_user_prefs-main/user_prefs . rm -rf spamassassin_user_prefs-main # Restart SpamAssassin only when the configuration file is updated. diff user_prefs user_prefs.org > /dev/null 2>&1 if [ $? -ne 0 ]; then cp user_prefs local.cf # Changing spam detection score※The default value is high, resulting in a large volume of spam emails being received. sed -i 's/required_score .*/required_score 8.0/g' local.cf # Configure settings to prevent emails flagged as spam from being attached. echo "report_safe 0" >> local.cf # Configure to add "***SPAM***" to the subject line of emails identified as spam Only when the incoming mail server is not IMAP lsof -i:143,993 >/dev/null 2>&1 [ $? -ne 0 ] && echo "rewrite_header Subject ***SPAM***" >> local.cf # Restart SpamAssassin systemctl restart spamd > /dev/null fi cp user_prefs user_prefs.org |
Grant the spamassassin-update script execution permissions and run it.
|
1 2 |
# chmod +x /etc/cron.daily/spamassassin-update.sh # /etc/cron.daily/spamassassin-update.sh |
Verify that the SpamAssassin configuration file (local.cf) has been created with the current date in the /etc/mail/spamassassin directory.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# ls -l /etc/mail/spamassassin total 1520 -rw-r--r-- 1 root root 1649 Apr 10 2024 init.pre -rw-r--r-- 1 root root 500601 Oct 7 09:18 local.cf drwx------ 1 root root 102 Oct 6 15:10 sa-update-keys -rw-r--r-- 1 root root 500588 Apr 30 2023 user_prefs -rw-r--r-- 1 root root 500588 Oct 7 09:18 user_prefs.org -rw-r--r-- 1 root root 2262 Oct 7 08:52 v310.pre -rw-r--r-- 1 root root 1168 Apr 10 2024 v312.pre -rw-r--r-- 1 root root 2416 Apr 10 2024 v320.pre -rw-r--r-- 1 root root 1237 Apr 10 2024 v330.pre -rw-r--r-- 1 root root 1020 Apr 10 2024 v340.pre -rw-r--r-- 1 root root 1315 Apr 10 2024 v341.pre -rw-r--r-- 1 root root 1519 Apr 10 2024 v342.pre -rw-r--r-- 1 root root 1266 Apr 10 2024 v343.pre -rw-r--r-- 1 root root 1482 Apr 10 2024 v400.pre -rw-r--r-- 1 root root 1118 Apr 10 2024 v401.pre |
⑤SpamAssassin Milter Startup and Automatic Startup Configuration
|
1 2 3 4 |
# systemctl start spamass-milter # systemctl enable spamass-milter Created symlink /etc/systemd/system/multi-user.target.wants/spamass-milter.service → /usr/lib/systemd/system/spamass-milter.service. |
⑥Postfix and SpamAssassin Milter Integration Configuration
|
1 2 3 4 5 6 |
# vi /etc/postfix/main.cf Add the following milter_default_action = tempfail smtpd_milters = unix:/var/run/clamav-milter/clamav-milter.socket,unix:/run/spamass-milter/socket ※If clamav-milter is already defined non_smtpd_milters = unix:/var/run/clamav-milter/clamav-milter.socket,unix:/run/spamass-milter/socket ※If clamav-milter is already defined |
⑧Restart postfix
|
1 |
# systemctl restart postfix |
⑨Procmail Configuration
Creating a Procmail Configuration File
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# vi /etc/procmailrc SHELL=/bin/bash PATH=/usr/bin:/bin DROPPRIVS=yes MAILDIR=$HOME/Maildir DEFAULT=$MAILDIR/ # Log output destination LOGFILE=$HOME/.procmail.log # Detailed Log Output VERBOSE=ON # If the Spam-Level determined by SpamAssassin is equal to or greater than a specified value (20 in this case), delete the message. # ※Be aware that important emails may be deleted. :0 * ^X-Spam-Level: \*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\* /dev/null |
Creating the Procmail Log Rotation Configuration File
|
1 2 3 4 5 6 |
# vi /etc/logrotate.d/procmail /home/*/.procmail.log { missingok nocreate notifempty } |
⑩Postfix and Procmail Integration Configuration
|
1 2 3 4 5 6 |
# vi /etc/postfix/main.cf Line 481: Addition #mailbox_command = /some/where/procmail #mailbox_command = /some/where/procmail -a "$EXTENSION" mailbox_command = /usr/bin/procmail ← Add (to enable integration with Procmail) |
Postfix Configuration Update
|
1 |
# systemctl restart postfix |
3.2.2 Spam Email Filtering Settings
Emails marked as spam by SpamAssassin in their headers should be delivered to the spam-specific mailbox, while other emails should be delivered to the regular mailbox.
①Creating a Dedicated Spam Mailbox
For existing users, add a dedicated spam mailbox to their mailbox.
For new users, automatically create a dedicated spam mailbox when adding the user.
Create a script for creating dedicated spam mailboxes.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# vi spamfolder-create #!/bin/bash for user in `ls /home` do id -u $user > /dev/null 2>&1 if [ $? -eq 0 ] && [ ! -d /home/$user/Maildir/.Spam/new ]; then mkdir -p /home/$user/Maildir/.Spam/new mkdir -p /home/$user/Maildir/.Spam/cur mkdir -p /home/$user/Maildir/.Spam/tmp chmod -R 700 /home/$user/Maildir/.Spam chown -R $user:$user /home/$user/Maildir/.Spam echo $user fi done |
Execute the spam-dedicated mailbox creation script
|
1 2 |
# bash spamfolder-create huong |
New User Countermeasures
Automatically create a dedicated spam mailbox when adding new users
|
1 2 |
# mkdir -p /etc/skel/Maildir/.Spam/{new,cur,tmp} # chmod -R 700 /etc/skel/Maildir/.Spam |
➁Spam Email Filtering
Emails flagged as spam by SpamAssassin are delivered to a dedicated spam mailbox.
|
1 2 3 4 5 6 |
# vi /etc/procmailrc Add the following to the end # Emails flagged as spam by SpamAssassin are delivered to the spam-specific mailbox. :0 *^X-Spam-Flag: YES $HOME/Maildir/.Spam/ |
➂SpamAssassin Milter Verification
When sending an empty email to yourself, the following message is appended to the header of the received email:
X-Spam-Status: No, score=2.2 required=8.0 tests=ALL_TRUSTED,
CONTENT_TYPE_PRESENT,EMPTY_MESSAGE autolearn=no autolearn_force=no
version=4.0.1
X-Spam-Level: **
X-Spam-Checker-Version: SpamAssassin 4.0.1 (2024-03-26) on lepard
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
Return-Path: <xxxxx@xxxxxxx.com>
X-Original-To: xxxxx@xxxxxxx.com
Delivered-To: xxxxx@xxxxxxx.com
Received: from [192.168.11.6] (buffalo.setup [192.168.11.1])
by mail.xxxxxxx.com (Postfix) with ESMTPA id 05DF5D432
for <xxxxx@xxxxxxx.com>; Tue, 07 Oct 2025 09:49:00 +0900 (JST)
Message-ID: <87078198-4413-4907-a72a-0dd7500d1c00@korodes.com>
Date: Tue, 7 Oct 2025 09:48:59 +0900
MIME-Version: 1.0
User-Agent: Mozilla Thunderbird
From: huong <xxxxx@xxxxxxx.com>
Content-Language: en-US
To: huong <xxxxx@xxxxxxx.com>
Content-Type: text/plain; charset=UTF-8; format=flowed
Content-Transfer-Encoding: 7bit
X-Virus-Scanned: clamav-milter 1.4.3 at lepard
X-Virus-Status: Clean
X-Spam-Status: No, score=2.2 required=8.0 tests=ALL_TRUSTED,
CONTENT_TYPE_PRESENT,EMPTY_MESSAGE autolearn=no autolearn_force=no
version=4.0.1
X-Spam-Level: **
X-Spam-Checker-Version: SpamAssassin 4.0.1 (2024-03-26) on Lepard
④Spam Check Verification
Confirm that an email with the body text "XJSC4JDBQADN1.NSBN32IDNENGTUBE-STANDARD-ANTI-UBE-TEST-EMAILC.34X" sent to yourself is not delivered and is instead routed to the Spam folder.
The email header displays as follows:
| Return-Path: xxxxx@xxxxxxx.com X-Original-To: xxxxx@xxxxxxx.com Delivered-To: xxxxx@xxxxxxx.com Received: from [192.168.11.6] (buffalo.setup [192.168.11.1]) by mail.xxxxxx.com (Postfix) with ESMTPA id A8698D433 for xxxxx@xxxxxxx.com; Tue, 07 Oct 2025 09:53:05 +0900 (JST) Content-Type: multipart/alternative; boundary="------------bXIP72VG7BUq5TDt8w65TTDf" Message-ID: 25095fa1-94da-4024-a2a2-eca90c5d91f9@korodes.com Date: Tue, 7 Oct 2025 09:53:05 +0900 MIME-Version: 1.0 User-Agent: Mozilla Thunderbird From: xxxxx xxxxx@xxxxxxx.com Content-Language: en-US To: xxxxx xxxxx@xxxxxxx.com Subject: Spam Test X-Virus-Scanned: clamav-milter 1.4.3 at lepard X-Virus-Status: Clean X-Spam-Flag: YES X-Spam-Status: Yes, score=1003.3 required=8.0 tests=ALL_TRUSTED, CONTENT_TYPE_PRESENT,GTUBE,HTML_MESSAGE,MPART_ALT_DIFF, MULTIPART_ALTERNATIVE autolearn=no autolearn_force=no version=4.0.1 X-Spam-Report: * 0.1 ALL_TRUSTED Passed through trusted hosts only via SMTP * 0.1 MULTIPART_ALTERNATIVE Multipart/alternative * -0.1 CONTENT_TYPE_PRESENT exists:Content-Type * 1000 GTUBE BODY: Generic Test for Unsolicited Bulk Email * 2.2 MPART_ALT_DIFF BODY: HTML and text parts are different * 1.0 HTML_MESSAGE BODY: HTML included in message X-Spam-Level: ************************************************ X-Spam-Checker-Version: SpamAssassin 4.0.1 (2024-03-26) on lepard |