Contents
1.Obtain an SSL Certificate (Let's Encrypt)
1.1 Preparation
①Enable mod_ssl
If mod_ssl is not enabled, enable it.
|
1 |
# a2enmod ssl |
Installing the Snappy Package Management System
Since the Let's Encrypt SSL certificate issuance tool "certbot" has recommended installation via "snap" since 2021, we will first install Snapd.
Add the snap repository for openSUSE 16
|
1 2 3 |
# zypper addrepo --refresh \ https://download.opensuse.org/repositories/system:/snappy/openSUSE_Leap_16.0 \ snappy |
After adding the repository, import its GPG key.
|
1 |
# zypper --gpg-auto-import-keys refresh |
Upgrade the package cache to include the new Snappy repository:
|
1 |
# zypper dup --from snappy |
Install snapd
|
1 |
# zypper install snapd |
Restart the system and add /snap/bin to the PATH.
Enable and start the snapd.apparmor service.
|
1 |
# systemctl enable --now snapd.apparmor |
Enable and start snapd
|
1 2 |
# systemctl enable --now snapd # systemctl start snapd |
Check the version of snapd and the snap command-line tool
|
1 2 3 4 5 6 7 |
# snap version snap 2.71 snapd 2.71 series 16 opensuse-leap 16.0 kernel 6.12.0-160000.5-default |
1.2 Certbot installation
|
1 2 3 4 |
# snap install --classic certbot 2025-10-08T19:13:06+09:00 INFO Waiting for automatic snapd restart... certbot 5.1.0 from Certbot Project (certbot-eff**) installed |
1.3 Certificate Acquisition
|
1 |
# certbot certonly --webroot -w /srv/www/htdocs/[FQDN] -d <FQDN> |
# First-time users must register an email address and agree to the terms of use.
# Specify a valid email address
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): [mail address]
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.4-April-3-2024.pdf. You must agree in
order to register with the ACME server. Do you agree?
(Y)es/(N)o: y
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
(Y)es/(N)o: y
Account registered.
Requesting a certificate for [FQDN]
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/[FQDN]/fullchain.pem
Key is saved at: /etc/letsencrypt/live/[FQDN]/privkey.pem
This certificate expires on 2026-01-06.
These files will be updated when the certificate renews.
NEXT STEPS:
- The certificate will need to be renewed before it expires. Certbot can automatically renew the certificate in the background, but you may need to take steps to enable that functionality. See https://certbot.org/renewal-setup for instructions.
We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can try again later by visiting https://act.eff.org.
If you like Certbot, please consider supporting our work by:
- Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
- Donating to EFF: https://eff.org/donate-le
If "Successfully received certificate." is displayed, it was successful.
# As stated in the message, the following certificates have been obtained under [/etc/letsencrypt/live/[FQDN]/]
# cert.pem ⇒ SSL server certificate (including public key)
# chain.pem ⇒ Interim Certificate
# fullchain.pem ⇒ A file combining cert.pem and chain.pem
# privkey.pem ⇒ Private key corresponding to the public key
2. Web Server SSL Implementation
2.1 SSL Configuration
|
1 2 |
# a2enmod -l actions alias auth_basic authn_core authn_file authz_host authz_groupfile authz_core authz_user autoindex cgi dir env expires include log_config mime negotiation setenvif ssl socache_shmcb userdir reqtimeout cgid php8 |
|
1 2 3 |
# vi /etc/apache2/listen.conf ● Line 17: Uncomment Listen 443 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# vi /etc/apache2/vhosts.d/default-ssl.conf # New Creation <VirtualHost *:443> DocumentRoot "/srv/www/htdocs/[FQDN]" SSLEngine on SSLProtocol all -SSLv2 -SSLv3 SSLCertificateFile /etc/letsencrypt/live/[FQDN]/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/[FQDN]/privkey.pem SSLCertificateChainFile /etc/letsencrypt/live/[FQDN]/chain.pem <FilesMatch "\.(cgi|shtml|phtml|php)$"> SSLOptions +StdEnvVars </FilesMatch> <Directory "/srv/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> </VirtualHost> |
|
1 |
# systemctl restart apache2 |
2.2 Redirect HTTP traffic to HTTPS
To redirect all HTTP traffic to HTTPS, add the following to virtual_host.conf:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# vi /etc/apache2/vhosts.d/virtual_host.conf <VirtualHost *:80> RewriteEngine On RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L] ServerName [FQDN] ServerAdmin Email address DocumentRoot /srv/www/htdocs/[FQDN] ErrorLog /var/log/apache2/[FQDN].error.log CustomLog /var/log/apache2/[FQDN].access.log combined LogLevel warn RewriteEngine On RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L] </VirtualHost> |
|
1 2 3 |
# a2enmod rewrite # a2enmod -l actions alias auth_basic authn_core authn_file authz_host authz_groupfile authz_core authz_user autoindex cgi dir env expires include log_config mime negotiation setenvif ssl socache_shmcb userdir reqtimeout cgid php8 rewrite |
|
1 |
# systemctl restart apache2 |
If Firewalld is enabled, you must allow HTTPS services. HTTPS uses port 443/TCP.
|
1 2 3 4 |
# firewall-cmd --add-service=https --permanent success # firewall-cmd --reload success |
3. Configuring SSL/TLS (Let's Encrypt) on the Mail Server
3.1 Obtaining a Certificate for the Mail Server
Obtaining a certificate for the mail server fails even when using the "--standalone" option as shown below, since it cannot be obtained using the same method as above.
|
1 |
# certbot certonly --standalone -d mail.[domain name] |
After stopping the web server once, it succeeds as follows:
|
1 2 |
# systemctl stop httpd.service # certbot certonly --standalone -d mail.[domain name] |
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Requesting a certificate for mail.[Domain]
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/mail.[Domain]/fullchain.pem
Key is saved at: /etc/letsencrypt/live/mail.[Domain]/privkey.pem
This certificate expires on 2026-01-06.
These files will be updated when the certificate renews.
Certbot has set up a scheduled task to automatically renew this certificate in the background.
----------------------------------------------------------------------------------------------------------
If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
----------------------------------------------------------------------------------------------------------
Restart Apache
|
1 |
# systemctl restart apache2 |
3.2 Postfix Configuration
|
1 2 3 4 5 6 7 8 9 10 11 |
# vi /etc/postfix/main.cf Around lines 802 and 803: Change smtpd_tls_cert_file = /etc/letsencrypt/live/mail.[domain name]/fullchain.pem smtpd_tls_key_file = /etc/letsencrypt/live/mail.[domain name]/privkey.pem Add to the last line smtpd_use_tls = yes smtp_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_session_cache_database = btree:/var/lib/postfix/smtpd_scache |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
# vi /etc/postfix/master.cf Lines 24-29: Change as follows submission inet n - n - - smtpd -o syslog_name=postfix/submission # -o smtpd_forbid_unauth_pipelining=no -o smtpd_tls_security_level=encrypt # -o content_filter=smtp:[127.0.0.1]:10024 -o smtpd_sasl_auth_enable=yes Lines 46-51: Change as follows submissions inet n - n - - smtpd -o syslog_name=postfix/submissions # -o smtpd_forbid_unauth_pipelining=no -o smtpd_tls_wrappermode=yes # -o content_filter=smtp:[127.0.0.1]:10024 -o smtpd_sasl_auth_enable=yes Around line 70: Cancel contract tlsmgr unix - - n 1000? 1 tlsmgr |
3.3 Dovecot Configuration
|
1 2 3 4 5 6 7 |
# vi /etc/dovecot/dovecot.conf Add to the last line ssl = yes ssl_server_cert_file = /etc/letsencrypt/live/mail.[domain name]/fullchain.pem ssl_server_key_file = /etc/letsencrypt/live/mail.[domain name]/privkey.pem |
Allow port 587 through the firewall
|
1 2 |
# firewall-cmd --add-port=587/tcp --permanent # firewall-cmd --reload |
Restart
|
1 |
# systemctl restart postfix dovecot |
3.4 Thunderbird Settings
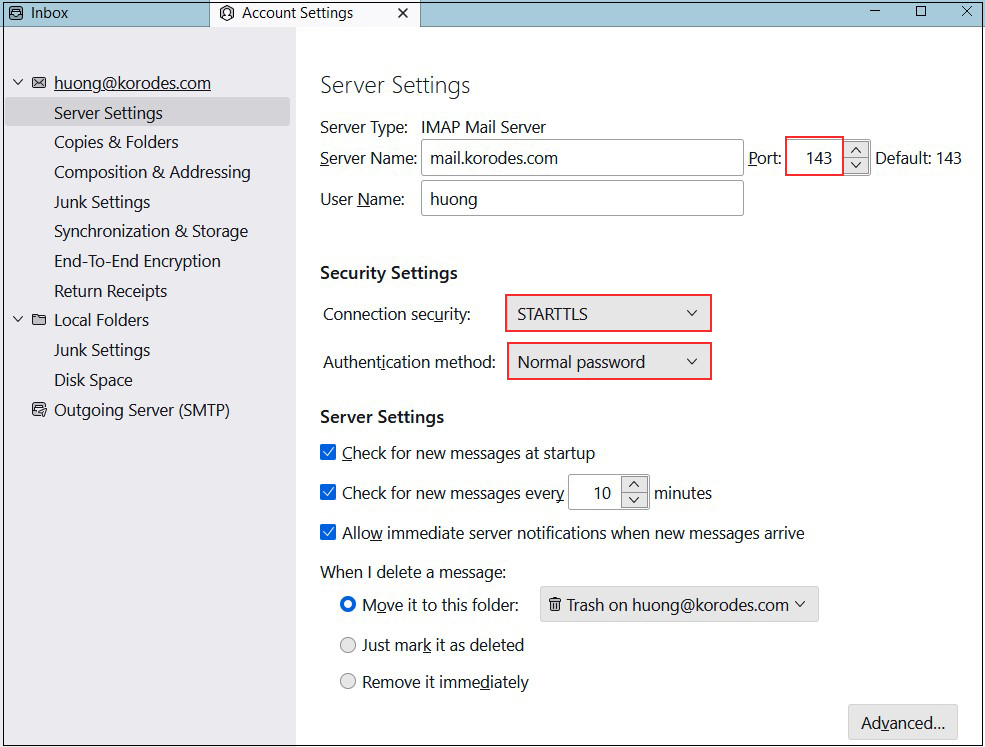
Incoming mail server
Port : 143
Connection security : STARTTLS
Authentication method : Normal password
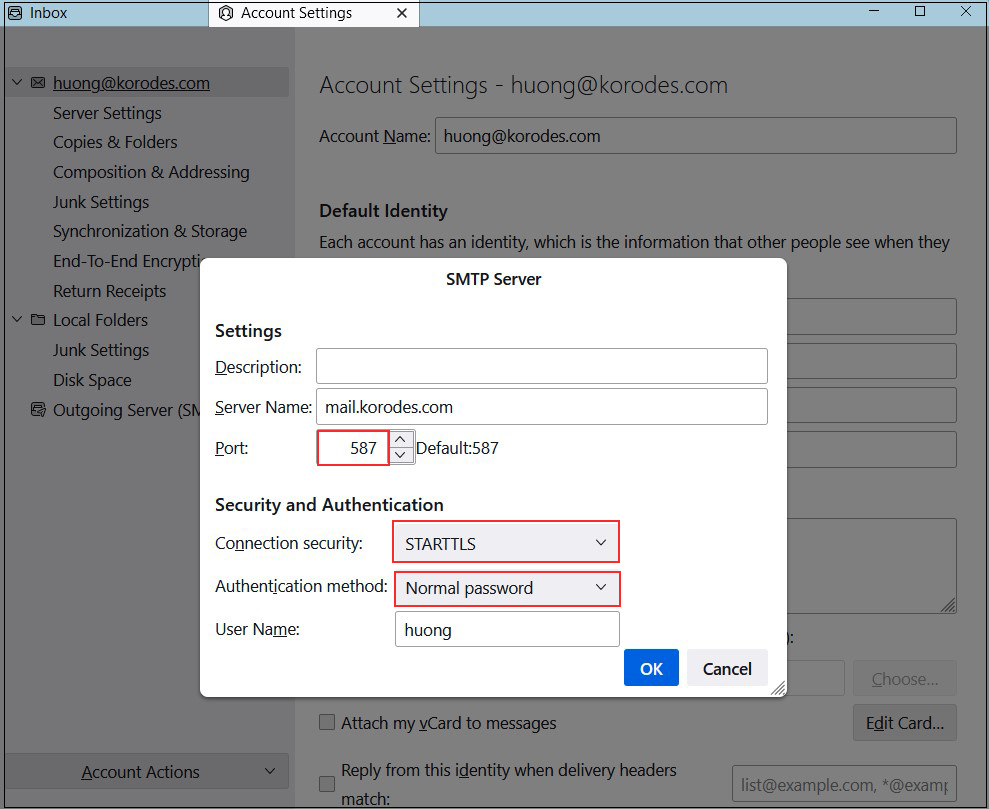
Outgoing mail server
Port : 587
Connection security : STARTTLS
Authentication method : Normal password