Contents
前提条件
今回はSuricata IDS と ElasticStack を 次のサーバーにインストールします
・1台目サーバー Suricata IDS & Filebeat : Debian12.8 IPアドレス(192.168.11.83)
・2台目サーバー ElasticStack & kibana : Ubuntu24.04 IPアドレス(192.168.11.200)
root以外のsudoユーザーで実行する
1台目サーバー Suricata インストール
SURICATA IDS/IPSはネットワーク上の通信を監視し、不審なトラフィックを検知するオープンソースのIDSです。基本的な仕組みはシグネチャ型であるため、あらかじめ設定した不正な通信を検知できます。また、Suricataは検知だけでなく防御も行えることが特徴です。
1.Suricata のインストール
①必須パッケージをインストール
|
1 |
# apt install wget curl software-properties-common dirmngr apt-transport-https gnupg2 ca-certificates lsb-release debian-archive-keyring unzip -y |
➁Suricata のインストール
|
1 2 |
# apt update # apt install suricata |
バージョンの確認
|
1 2 |
# suricata -V This is Suricata version 6.0.10 RELEASE |
Suricataサービスを最初に構成する必要があるため、サービスを停止します。
|
1 |
# systemctl stop suricata |
2.Suricataを構成
①Suricataがネットワークパケットを検査するインターフェースとIPアドレスを決定
|
1 2 3 |
# ip --brief add lo UNKNOWN 127.0.0.1/8 ::1/128 ens33 UP 192.168.11.83/24 |
/etc/suricata/suricata.yamlファイル編集
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
# vi /etc/suricata/suricata.yaml # 18行目 : 変更(自ネットワーク) HOME_NET: "[192.168.11.0/24]" # 132行目 : 変更 community-id: false → community-id: true # 589行目 : 変更 af-packet: - interface: eth0 ↓ af-packet: - interface: ens33 ←各自のインターフェース名に変更 |
➁ルールセットを追加
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 |
# suricata-update -o /etc/suricata/rules 19/11/2024 -- 12:26:56 - <Info> -- Using data-directory /var/lib/suricata. 19/11/2024 -- 12:26:56 - <Info> -- Using Suricata configuration /etc/suricata/suricata.yaml 19/11/2024 -- 12:26:56 - <Info> -- Using /etc/suricata/rules for Suricata provided rules. 19/11/2024 -- 12:26:56 - <Info> -- Found Suricata version 6.0.10 at /usr/bin/suricata. 19/11/2024 -- 12:26:56 - <Info> -- Loading /etc/suricata/suricata.yaml 19/11/2024 -- 12:26:56 - <Info> -- Disabling rules for protocol http2 19/11/2024 -- 12:26:56 - <Info> -- Disabling rules for protocol modbus 19/11/2024 -- 12:26:56 - <Info> -- Disabling rules for protocol dnp3 19/11/2024 -- 12:26:56 - <Info> -- Disabling rules for protocol enip 19/11/2024 -- 12:26:56 - <Info> -- No sources configured, will use Emerging Threats Open 19/11/2024 -- 12:26:56 - <Info> -- Fetching https://rules.emergingthreats.net/open/suricata-6.0.10/emerging.rules.tar.gz. 100% - 4599733/4599733 19/11/2024 -- 12:26:59 - <Info> -- Done. 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/app-layer-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/decoder-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/dhcp-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/dnp3-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/dns-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/files.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/http-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/ipsec-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/kerberos-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/modbus-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/nfs-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/ntp-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/smb-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/smtp-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/stream-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Loading distribution rule file /etc/suricata/rules/tls-events.rules 19/11/2024 -- 12:26:59 - <Info> -- Ignoring file rules/emerging-deleted.rules 19/11/2024 -- 12:27:01 - <Info> -- Loaded 54361 rules. 19/11/2024 -- 12:27:01 - <Info> -- Disabled 14 rules. 19/11/2024 -- 12:27:01 - <Info> -- Enabled 0 rules. 19/11/2024 -- 12:27:01 - <Info> -- Modified 0 rules. 19/11/2024 -- 12:27:01 - <Info> -- Dropped 0 rules. 19/11/2024 -- 12:27:02 - <Info> -- Enabled 136 rules for flowbit dependencies. 19/11/2024 -- 12:27:02 - <Info> -- Backing up current rules. 19/11/2024 -- 12:27:02 - <Info> -- Writing rules to /etc/suricata/rules/suricata.rules: total: 54361; enabled: 40645; added: 54361; removed 0; modified: 0 19/11/2024 -- 12:27:02 - <Info> -- Writing /etc/suricata/rules/classification.config 19/11/2024 -- 12:27:02 - <Info> -- Testing with suricata -T. 19/11/2024 -- 12:27:28 - <Info> -- Done. |
suricata-updateが無料のEmerging Threats ET Open Rulesを取得し、Suricataの/etc/suricata/rules/suricata.rulesファイルに保存したことを示しています。また、処理されたルールの数を示し、この例では54361が追加され、そのうち40645が有効になりました。
➂ルール・セット・プロバイダーの追加
既定のプロバイダー リストを一覧表示
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 |
# suricata-update list-sources Name: et/open Vendor: Proofpoint Summary: Emerging Threats Open Ruleset License: MIT Name: et/pro Vendor: Proofpoint Summary: Emerging Threats Pro Ruleset License: Commercial Replaces: et/open Parameters: secret-code Subscription: https://www.proofpoint.com/us/threat-insight/et-pro-ruleset Name: oisf/trafficid Vendor: OISF Summary: Suricata Traffic ID ruleset License: MIT Name: scwx/enhanced Vendor: Secureworks Summary: Secureworks suricata-enhanced ruleset License: Commercial Parameters: secret-code Subscription: https://www.secureworks.com/contact/ (Please reference CTU Countermeasures) Name: scwx/malware Vendor: Secureworks Summary: Secureworks suricata-malware ruleset License: Commercial Parameters: secret-code Subscription: https://www.secureworks.com/contact/ (Please reference CTU Countermeasures) Name: scwx/security Vendor: Secureworks Summary: Secureworks suricata-security ruleset License: Commercial Parameters: secret-code Subscription: https://www.secureworks.com/contact/ (Please reference CTU Countermeasures) Name: abuse.ch/sslbl-blacklist Vendor: Abuse.ch Summary: Abuse.ch SSL Blacklist License: CC0-1.0 Replaces: sslbl/ssl-fp-blacklist Name: abuse.ch/sslbl-ja3 Vendor: Abuse.ch Summary: Abuse.ch Suricata JA3 Fingerprint Ruleset License: CC0-1.0 Replaces: sslbl/ja3-fingerprints Name: abuse.ch/sslbl-c2 Vendor: Abuse.ch Summary: Abuse.ch Suricata Botnet C2 IP Ruleset License: CC0-1.0 Name: abuse.ch/feodotracker Vendor: Abuse.ch Summary: Abuse.ch Feodo Tracker Botnet C2 IP ruleset License: CC0-1.0 Name: abuse.ch/urlhaus Vendor: abuse.ch Summary: Abuse.ch URLhaus Suricata Rules License: CC0-1.0 Name: etnetera/aggressive Vendor: Etnetera a.s. Summary: Etnetera aggressive IP blacklist License: MIT Name: tgreen/hunting Vendor: tgreen Summary: Threat hunting rules License: GPLv3 Name: malsilo/win-malware Vendor: malsilo Summary: Commodity malware rules License: MIT Name: stamus/lateral Vendor: Stamus Networks Summary: Lateral movement rules License: GPL-3.0-only Name: stamus/nrd-30-open Vendor: Stamus Networks Summary: Newly Registered Domains Open only - 30 day list, complete License: Commercial Parameters: secret-code Subscription: https://www.stamus-networks.com/stamus-labs/subscribe-to-threat-intel-feed Name: stamus/nrd-14-open Vendor: Stamus Networks Summary: Newly Registered Domains Open only - 14 day list, complete License: Commercial Parameters: secret-code Subscription: https://www.stamus-networks.com/stamus-labs/subscribe-to-threat-intel-feed Name: stamus/nrd-entropy-30-open Vendor: Stamus Networks Summary: Newly Registered Domains Open only - 30 day list, high entropy License: Commercial Parameters: secret-code Subscription: https://www.stamus-networks.com/stamus-labs/subscribe-to-threat-intel-feed Name: stamus/nrd-entropy-14-open Vendor: Stamus Networks Summary: Newly Registered Domains Open only - 14 day list, high entropy License: Commercial Parameters: secret-code Subscription: https://www.stamus-networks.com/stamus-labs/subscribe-to-threat-intel-feed Name: stamus/nrd-phishing-30-open Vendor: Stamus Networks Summary: Newly Registered Domains Open only - 30 day list, phishing License: Commercial Parameters: secret-code Subscription: https://www.stamus-networks.com/stamus-labs/subscribe-to-threat-intel-feed Name: stamus/nrd-phishing-14-open Vendor: Stamus Networks Summary: Newly Registered Domains Open only - 14 day list, phishing License: Commercial Parameters: secret-code Subscription: https://www.stamus-networks.com/stamus-labs/subscribe-to-threat-intel-feed Name: pawpatrules Vendor: pawpatrules Summary: PAW Patrules is a collection of rules for IDPS / NSM Suricata engine License: CC-BY-SA-4.0 Name: ptrules/open Vendor: Positive Technologies Summary: Positive Technologies Open Ruleset License: Custom Name: aleksibovellan/nmap Vendor: aleksibovellan Summary: Suricata IDS/IPS Detection Rules Against NMAP Scans License: MIT |
例としてtgreen/hunting ルールセットを含める場合
|
1 2 3 4 5 6 7 8 9 |
# suricata-update enable-source tgreen/hunting 19/11/2024 -- 12:31:11 - <Info> -- Using data-directory /var/lib/suricata. 19/11/2024 -- 12:31:11 - <Info> -- Using Suricata configuration /etc/suricata/suricata.yaml 19/11/2024 -- 12:31:11 - <Info> -- Using /etc/suricata/rules for Suricata provided rules. 19/11/2024 -- 12:31:11 - <Info> -- Found Suricata version 6.0.10 at /usr/bin/suricata. 19/11/2024 -- 12:31:11 - <Info> -- Creating directory /var/lib/suricata/update/sources 19/11/2024 -- 12:31:11 - <Info> -- Enabling default source et/open 19/11/2024 -- 12:31:11 - <Info> -- Source tgreen/hunting enabled |
アップデートを実行
|
1 |
# suricata-update -o /etc/suricata/rules |
3.Suricata 構成のテスト
①検証ツールを実行
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# suricata -T -c /etc/suricata/suricata.yaml -v 19/11/2024 -- 12:32:15 - <Info> - Running suricata under test mode 19/11/2024 -- 12:32:15 - <Notice> - This is Suricata version 6.0.10 RELEASE running in SYSTEM mode 19/11/2024 -- 12:32:15 - <Info> - CPUs/cores online: 2 19/11/2024 -- 12:32:15 - <Info> - fast output device (regular) initialized: fast.log 19/11/2024 -- 12:32:15 - <Info> - eve-log output device (regular) initialized: eve.json 19/11/2024 -- 12:32:15 - <Info> - stats output device (regular) initialized: stats.log 19/11/2024 -- 12:32:28 - <Info> - 1 rule files processed. 40896 rules successfully loaded, 0 rules failed 19/11/2024 -- 12:32:29 - <Info> - Threshold config parsed: 0 rule(s) found 19/11/2024 -- 12:32:29 - <Info> - 40899 signatures processed. 1191 are IP-only rules, 5120 are inspecting packet payload, 34385 inspect application layer, 108 are decoder event only 19/11/2024 -- 12:32:40 - <Notice> - Configuration provided was successfully loaded. Exiting. 19/11/2024 -- 12:32:40 - <Info> - cleaning up signature grouping structure... complete |
Suricata service再起動
|
1 |
# systemctl start suricata |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# systemctl status suricata ● suricata.service - Suricata IDS/IDP daemon Loaded: loaded (/lib/systemd/system/suricata.service; enabled; preset: enabled) Active: active (running) since Tue 2024-11-19 12:33:13 JST; 6s ago Docs: man:suricata(8) man:suricatasc(8) https://suricata-ids.org/docs/ Process: 3009 ExecStart=/usr/bin/suricata -D --af-packet -c /etc/suricata/suricata.yaml --pidfile /run/suricata.pid (code=exited, status=0/SUCCESS) Main PID: 3010 (Suricata-Main) Tasks: 1 (limit: 2264) Memory: 187.4M CPU: 6.568s CGroup: /system.slice/suricata.service └─3010 /usr/bin/suricata -D --af-packet -c /etc/suricata/suricata.yaml --pidfile /run/suricata.pid Nov 19 12:33:13 Lepard systemd[1]: Starting suricata.service - Suricata IDS/IDP daemon... Nov 19 12:33:13 Lepard suricata[3009]: 19/11/2024 -- 12:33:13 - <Notice> - This is Suricata version 6.0.10 RELEASE running in SYSTEM mode Nov 19 12:33:13 Lepard systemd[1]: Started suricata.service - Suricata IDS/IDP daemon. |
ログファイルを確認
|
1 2 3 4 5 6 7 8 9 10 11 12 |
# tail -f /var/log/suricata/suricata.log 19/11/2024 -- 12:33:13 - <Info> - fast output device (regular) initialized: fast.log 19/11/2024 -- 12:33:13 - <Info> - eve-log output device (regular) initialized: eve.json 19/11/2024 -- 12:33:13 - <Info> - stats output device (regular) initialized: stats.log 19/11/2024 -- 12:33:27 - <Info> - 1 rule files processed. 40896 rules successfully loaded, 0 rules failed 19/11/2024 -- 12:33:27 - <Info> - Threshold config parsed: 0 rule(s) found 19/11/2024 -- 12:33:28 - <Info> - 40899 signatures processed. 1191 are IP-only rules, 5120 are inspecting packet payload, 34385 inspect application layer, 108 are decoder event only 19/11/2024 -- 12:33:39 - <Info> - Going to use 2 thread(s) 19/11/2024 -- 12:33:39 - <Info> - Using unix socket file '/var/run/suricata-command.socket' 19/11/2024 -- 12:33:39 - <Notice> - all 2 packet processing threads, 4 management threads initialized, engine started. 19/11/2024 -- 12:33:39 - <Info> - All AFP capture threads are running. |
4.Suricataルールのテスト
①次のコマンドを使用してET Openルール番号2100498をテストする
|
1 2 |
# curl http://testmynids.org/uid/index.html uid=0(root) gid=0(root) groups=0(root) |
②指定されたルール番号を使用してログファイルを確認する
|
1 2 3 |
# grep 2100498 /var/log/suricata/fast.log 11/19/2024-12:35:06.340641 [**] [1:2100498:7] GPL ATTACK_RESPONSE id check returned root [**] [Classification: Potentially Bad Traffic] [Priority: 2] {TCP} 18.65.159.75:80 -> 192.168.11.83:45552 |
③/var/log/suricata/eve.log のイベント確認
jq をインストール
|
1 |
# apt install jq |
2100498シグネチャを検索して、EVEログのイベントをフィルタリング
2100498の値と一致するsignature_idキーを持つalertオブジェクトを表示
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
# jq 'select(.alert .signature_id==2100498)' /var/log/suricata/eve.json { "timestamp": "2024-11-19T12:35:06.340641+0900", "flow_id": 1085739939590100, "in_iface": "ens33", "event_type": "alert", "src_ip": "18.65.159.75", "src_port": 80, "dest_ip": "192.168.11.83", "dest_port": 45552, "proto": "TCP", "community_id": "1:xYwYl5+l5Grb9PM/cjkqvNDYva0=", "alert": { "action": "allowed", "gid": 1, "signature_id": 2100498, "rev": 7, "signature": "GPL ATTACK_RESPONSE id check returned root", "category": "Potentially Bad Traffic", "severity": 2, "metadata": { "created_at": [ "2010_09_23" ], "updated_at": [ "2019_07_26" ] } }, |
④Custom Rulesの作成と適用
非SSHポートへのSSHトラフィックをスキャンするための以下のカスタム署名を作成し、/etc/suricata/rules/local.rulesというファイルにインクルードする(今回はIPv4のみ)
|
1 2 |
# vi /etc/suricata/rules/local.rules alert ssh any any -> 203.0.113.5 !22 (msg:"SSH TRAFFIC on non-SSH port"; flow:to_client, not_established; classtype: misc-attack; target: dest_ip; sid:1000000;) |
suricata.yamlの編集
|
1 2 3 4 5 6 |
# vi /etc/suricata/suricata.yaml 1923行目にlocal.rulesを追加 rule-files: - suricata.rules - local.rules |
SURICATAの設定を検証
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# suricata -T -c /etc/suricata/suricata.yaml -v 19/11/2024 -- 12:39:04 - <Info> - Running suricata under test mode 19/11/2024 -- 12:39:04 - <Notice> - This is Suricata version 6.0.10 RELEASE running in SYSTEM mode 19/11/2024 -- 12:39:04 - <Info> - CPUs/cores online: 2 19/11/2024 -- 12:39:05 - <Info> - fast output device (regular) initialized: fast.log 19/11/2024 -- 12:39:05 - <Info> - eve-log output device (regular) initialized: eve.json 19/11/2024 -- 12:39:05 - <Info> - stats output device (regular) initialized: stats.log 19/11/2024 -- 12:40:29 - <Info> - 2 rule files processed. 40897 rules successfully loaded, 0 rules failed 19/11/2024 -- 12:40:29 - <Info> - Threshold config parsed: 0 rule(s) found 19/11/2024 -- 12:40:30 - <Info> - 40900 signatures processed. 1191 are IP-only rules, 5120 are inspecting packet payload, 34386 inspect application layer, 108 are decoder event only 19/11/2024 -- 12:40:40 - <Notice> - Configuration provided was successfully loaded. Exiting. 19/11/2024 -- 12:40:40 - <Info> - cleaning up signature grouping structure... complete |
先ほどのカスタム署名を編集し、ドロップアクションを使うように変換する
|
1 2 3 |
# vi /etc/suricata/rules/local.rules drop ssh any any -> 192.168.11.83 !22 (msg:"SSH TRAFFIC on non-SSH port"; flow:to_client, not_established; classtype: misc-attack; target: dest_ip; sid:1000000;) |
⑤SURICATAを再設定し、IPSモードで再起動する
|
1 2 3 4 |
# vi /etc/default/suricata 13行目 LISTENMODE=nfqueue |
systemdをリロードして、新しいSuricataの設定を検出するようにする
|
1 |
# systemctl daemon-reload |
|
1 |
# systemctl restart suricata.service |
⑥suricataに必要なルールをUFWに追加
/etc/ufw/before.rulesと/etc/ufw/before6.rulesのファイアウォールファイルを直接編集する
|
1 2 3 4 5 6 7 8 9 10 |
# vi /etc/ufw/before.rules 19行目当たりに下記追加 ## Start Suricata NFQUEUE rules -I INPUT 1 -p tcp --dport 2244 -j NFQUEUE --queue-bypass -I OUTPUT 1 -p tcp --sport 2244 -j NFQUEUE --queue-bypass -I FORWARD -j NFQUEUE -I INPUT 2 -j NFQUEUE -I OUTPUT 2 -j NFQUEUE ## End Suricata NFQUEUE rules |
同様に/etc/ufw/before6.rulesも変更する
UFWを再起動
|
1 |
# systemctl restart ufw.service |
前述のシグネチャsid:2100498に一致するパケットをドロップするようにする
|
1 2 3 4 5 |
# vi /etc/suricata/rules/suricata.rules sid:2100498に一致する行を見つけalertをdropに変更 drop ip any any -> any any (msg:"GPL ATTACK_RESPONSE id check returned root"; content:"uid=0|28|root|29|"; classtype:bad-unknown; sid:2100498; rev:7; metadata:created_at 2010_09_23, updated_at 2019_07_26;) |
シグネチャをリロード
|
1 |
# kill -usr2 $(pidof suricata) |
curlを使ってこのルールをテストする
|
1 2 |
# curl --max-time 5 http://testmynids.org/uid/index.html curl: (28) Operation timed out after 5000 milliseconds with 0 out of 39 bytes received |
jqを使ってeve.log確認 "action": "blocked"になっている
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 |
# jq 'select(.alert .signature_id==2100498)' /var/log/suricata/eve.json { "timestamp": "2024-11-19T12:56:44.447219+0900", "flow_id": 1561530059235987, "event_type": "alert", "src_ip": "18.65.159.75", "src_port": 80, "dest_ip": "192.168.11.83", "dest_port": 37592, "proto": "TCP", "community_id": "1:SQuT4qYsqwmMzchc9if4AnDNNQ0=", "alert": { "action": "blocked", "gid": 1, "signature_id": 2100498, "rev": 7, "signature": "GPL ATTACK_RESPONSE id check returned root", "category": "Potentially Bad Traffic", "severity": 2, "metadata": { "created_at": [ "2010_09_23" ], "updated_at": [ "2019_07_26" ] } }, |
ELK StackとSURICATAの統合
Elastic Stackをインストール&設定して、SURICATAのログを可視化&検索できるようにする
本セクションは基本的には2台目のUbuntu22.04サーバーで行います
1. Elasticsearchのインストール
1.1 公開署名キーをダウンロードしてインストール
|
1 |
# wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | gpg --dearmor -o /usr/share/keyrings/elasticsearch-keyring.gpg |
1.2 リポジトリ定義を/etc/apt/sources.list.d/elastic-8.x.listに保存
|
1 |
# echo "deb [signed-by=/usr/share/keyrings/elasticsearch-keyring.gpg] https://artifacts.elastic.co/packages/8.x/apt stable main" | tee /etc/apt/sources.list.d/elastic-8.x.list |
1.3 Elasticsearch パッケージをインストール
|
1 |
# apt update && apt install elasticsearch |
2. Elasticsearch 設定
2.1 Elasticsearch 設定ファイルを編集
|
1 2 3 4 5 6 7 8 9 10 11 12 |
# vi /etc/elasticsearch/elasticsearch.yml 57行目追加 : Elastic Stackサーバーのipアドレスを入力 network.host: 192.168.11.200 62行目コメント解除 http.port: 9200 xpack.security.enabledとxpack.security.enrollment.enabledを一時無効にする 93行目変更 xpack.security.enabled: false 95行目変更 xpack.security.enrollment.enabled: false |
ファイルを保存する
2.2 9200/tcp ホートを開放
|
1 2 |
# ufw allow 9200/tcp # ufw reload |
2.3 Elasticsearchサービスを有効にして確認
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
# systemctl start elasticsearch.service Elasticsearch Hostにcurlリクエストを送る # curl -X GET "192.168.11.200:9200" { "name" : "Lion", "cluster_name" : "elasticsearch", "cluster_uuid" : "rCXdMlLVTRiTl3xmX33IwA", "version" : { "number" : "8.16.0", "build_flavor" : "default", "build_type" : "deb", "build_hash" : "12ff76a92922609df4aba61a368e7adf65589749", "build_date" : "2024-11-08T10:05:56.292914697Z", "build_snapshot" : false, "lucene_version" : "9.12.0", "minimum_wire_compatibility_version" : "7.17.0", "minimum_index_compatibility_version" : "7.0.0" }, "tagline" : "You Know, for Search" } |
Elasticsearch バージョン8.16.0が稼働している
2.4 Elasticsearch 設定ファイルを再度編集
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
# vi /etc/elasticsearch/elasticsearch.yml xpack.securityを有効に戻す 93行目変更 xpack.security.enabled: true 95行目変更 xpack.security.enrollment.enabled: true 101行目に"verification_mode: none"追加 xpack.security.http.ssl: enabled: true keystore.path: certs/http.p12 verification_mode: none 106行目に"verification_mode: none"追加 xpack.security.transport.ssl: enabled: true verification_mode: none keystore.path: certs/transport.p12 truststore.path: certs/transport.p12 |
ファイルを保存し、 elasticsearch.serviceを再起動
|
1 |
# systemctl restart elasticsearch.service |
2.4 elasticとkibana_systemのパスワードを作成
elasticユーザとkibana_systemユーザのパスワードは後で使用するので必ずコピーしておく
kibana_systemユーザはKibanaの設定に使用する
elasticユーザはFilebeatの設定およびKibanaへのログインに使用する
[elastic] userのパスワード作成
|
1 2 3 4 5 6 7 8 9 |
# cd /usr/share/elasticsearch/bin # ./elasticsearch-reset-password -u elastic This tool will reset the password of the [elastic] user to an autogenerated value. The password will be printed in the console. Please confirm that you would like to continue [y/N]y Password for the [elastic] user successfully reset. New value: 1y6En9+QRA+BduUbrSYJ |
[kibana_system]userのパスワード作成
|
1 2 3 4 5 6 7 8 9 |
# cd /usr/share/elasticsearch/bin # ./elasticsearch-reset-password -u kibana_system This tool will reset the password of the [kibana_system] user to an autogenerated value. The password will be printed in the console. Please confirm that you would like to continue [y/N]y Password for the [kibana_system] user successfully reset. New value: PKZfJ9uAnMsPB5c8xdAz |
3. Kibana の設定
Kibana は Elasticsearch をインストールした後にインストールする。
Kibana は Elasticsearch と同じマシンにインストールする
3.1 Kibanaインストール
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
# apt install kibana Reading package lists... Done Building dependency tree... Done Reading state information... Done The following NEW packages will be installed: kibana 0 upgraded, 1 newly installed, 0 to remove and 2 not upgraded. Need to get 345 MB of archives. After this operation, 1,038 MB of additional disk space will be used. Get:1 https://artifacts.elastic.co/packages/8.x/apt stable/main amd64 kibana amd64 8.16.0 [345 MB] Fetched 345 MB in 5s (63.2 MB/s) Selecting previously unselected package kibana. (Reading database ... 88571 files and directories currently installed.) Preparing to unpack .../kibana_8.16.0_amd64.deb ... Unpacking kibana (8.16.0) ... Setting up kibana (8.16.0) ... Creating kibana group... OK Creating kibana user... OK Kibana is currently running with legacy OpenSSL providers enabled! For details and instructions on how to disable see https://www.elastic.co/guide/en/kibana/8.16/production.html#openssl-legacy-provider Created Kibana keystore in /etc/kibana/kibana.keystore Scanning processes... |
3.2 xpack.security設定と暗号化キーを作成
暗号化キーをコピーしておく
|
1 2 3 4 5 6 7 |
# cd /usr/share/kibana/bin/ # ./kibana-encryption-keys generate -q xpack.encryptedSavedObjects.encryptionKey: 02ed1d28734acc1a28875504ebe005d9 xpack.reporting.encryptionKey: e2dbb6668a6a67ffc58129f272d1bca6 xpack.security.encryptionKey: cc4e87c2d357b53a35d4e6f133a1e876 |
kibana.yml設定ファイルに暗号化キーを追加する
|
1 2 3 4 5 6 7 8 9 10 |
# vi /etc/kibana/kibana.yml 最終行に暗号化キーを追加 # Maximum number of documents loaded by each shard to generate autocomplete suggestions. # This value must be a whole number greater than zero. Defaults to 100_000 #unifiedSearch.autocomplete.valueSuggestions.terminateAfter: 100000 xpack.encryptedSavedObjects.encryptionKey: 02ed1d28734acc1a28875504ebe005d9 xpack.reporting.encryptionKey: e2dbb6668a6a67ffc58129f272d1bca6 xpack.security.encryptionKey: cc4e87c2d357b53a35d4e6f133a1e876 |
3.3 その他kibana.yml設定ファイル編集
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# vi /etc/kibana/kibana.yml 6行目コメント解除 server.port: 5601 12行目 Elastic StackのIPアドレス(192.168.11.200)に置き換え server.host: "192.168.11.200" 44行目に追加 elasticsearch.hosts: ["https://192.168.11.200:9200"] 49,50行目コメント解除し、elasticsearch.username はデフォルト(kibana_system)のままで、elasticsearch.password を作成したkibana_systemのパスワードに変更 elasticsearch.username: "kibana_system" elasticsearch.password: "PKZfJ9uAnMsPB5c8xdAz" 96行目に追加 Kibana が Elasticsearch にアウトバウンド SSL/TSL 接続を行う際にホスト名の検証がスキップされる #elasticsearch.ssl.verificationMode: full elasticsearch.ssl.verificationMode: 'none' |
ファイル保存
3.4 Kibanaサービスを開始
|
1 |
# systemctl start kibana.service |
Kibana.serviceのステータスを確認
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# systemctl status kibana.service ● kibana.service - Kibana Loaded: loaded (/usr/lib/systemd/system/kibana.service; disabled; preset: enabled) Active: active (running) since Tue 2024-11-19 14:17:35 JST; 6s ago Docs: https://www.elastic.co Main PID: 15123 (node) Tasks: 11 (limit: 4556) Memory: 343.8M (peak: 343.8M) CPU: 6.422s CGroup: /system.slice/kibana.service mq15123 /usr/share/kibana/bin/../node/glibc-217/bin/node /usr/share/kibana/bin/../src/cli/dist Nov 19 14:17:35 Lion systemd[1]: Started kibana.service - Kibana. Nov 19 14:17:35 Lion kibana[15123]: Kibana is currently running with legacy OpenSSL providers enabled! For details and instructions on how to disable see htt> Nov 19 14:17:36 Lion kibana[15123]: {"log.level":"info","@timestamp":"2024-11-19T05:17:36.111Z","log.logger":"elastic-apm-node","ecs.version":"8.10.0","agent> Nov 19 14:17:36 Lion kibana[15123]: Native global console methods have been overridden in production environment. Nov 19 14:17:37 Lion kibana[15123]: [2024-11-19T14:17:37.353+09:00][INFO ][root] Kibana is starting Nov 19 14:17:37 Lion kibana[15123]: [2024-11-19T14:17:37.383+09:00][INFO ][node] Kibana process configured with roles: [background_tasks, ui] |
3.5 http,httpsポート開放
|
1 2 3 |
# ufw allow http # ufw allow https # ufw reload |
4. Kibanaのウェブページ起動確認
ウェブ・ブラウザにアクセスし、Kibanaが正しく起動していることを確認する。"http://192.168.11.200:5601"と入力してKibanaにアクセスしてみる。ただし、5601ポートを開放しておく
|
1 2 |
# ufw allow 5601/tcp # ufw reload |
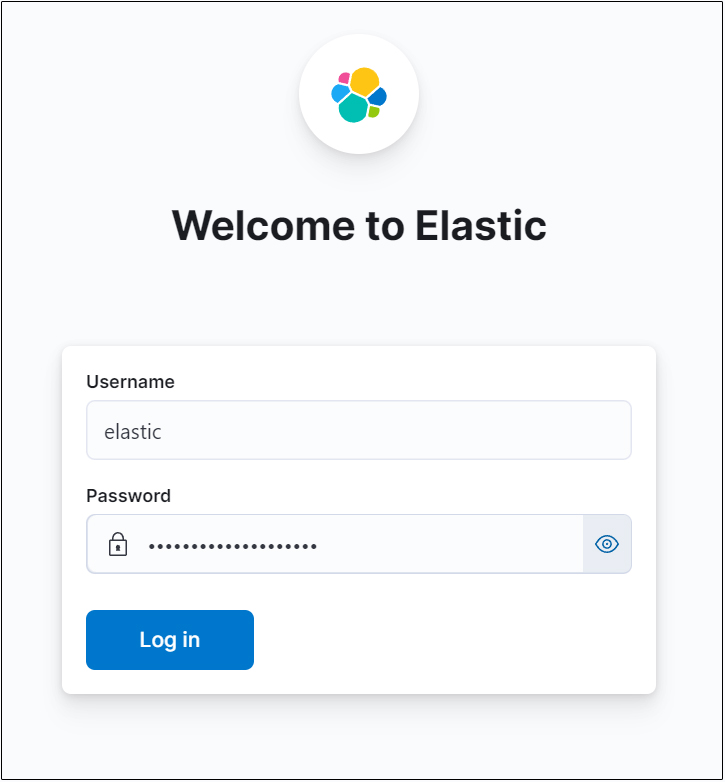
Usernameはelastic、Passwordはelastic用に作成したものでログイン
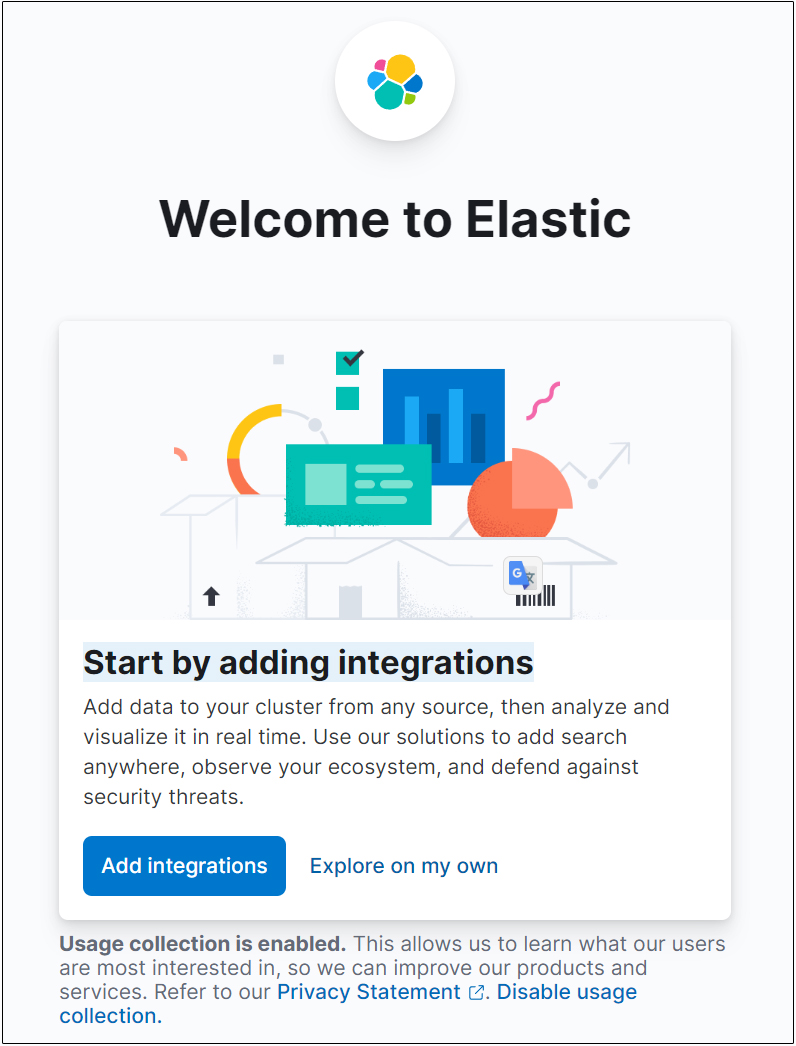
"Add integrations"選択しEnter
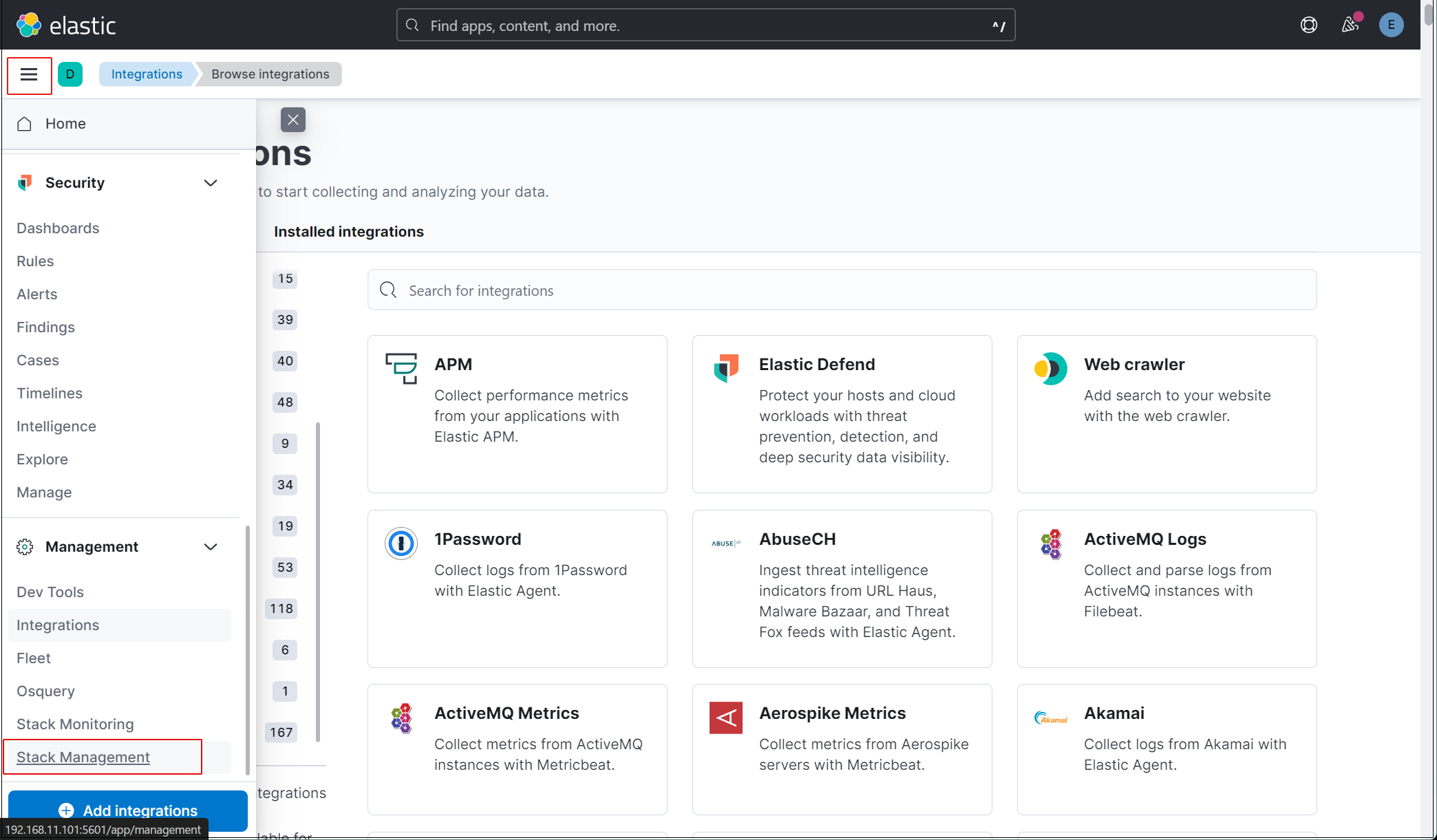
elasticスーパーユーザーアカウントを使う必要がないように、新しいユーザーアカウントを作成します。
左上三本線マークをクリックし、Stack Management を選択
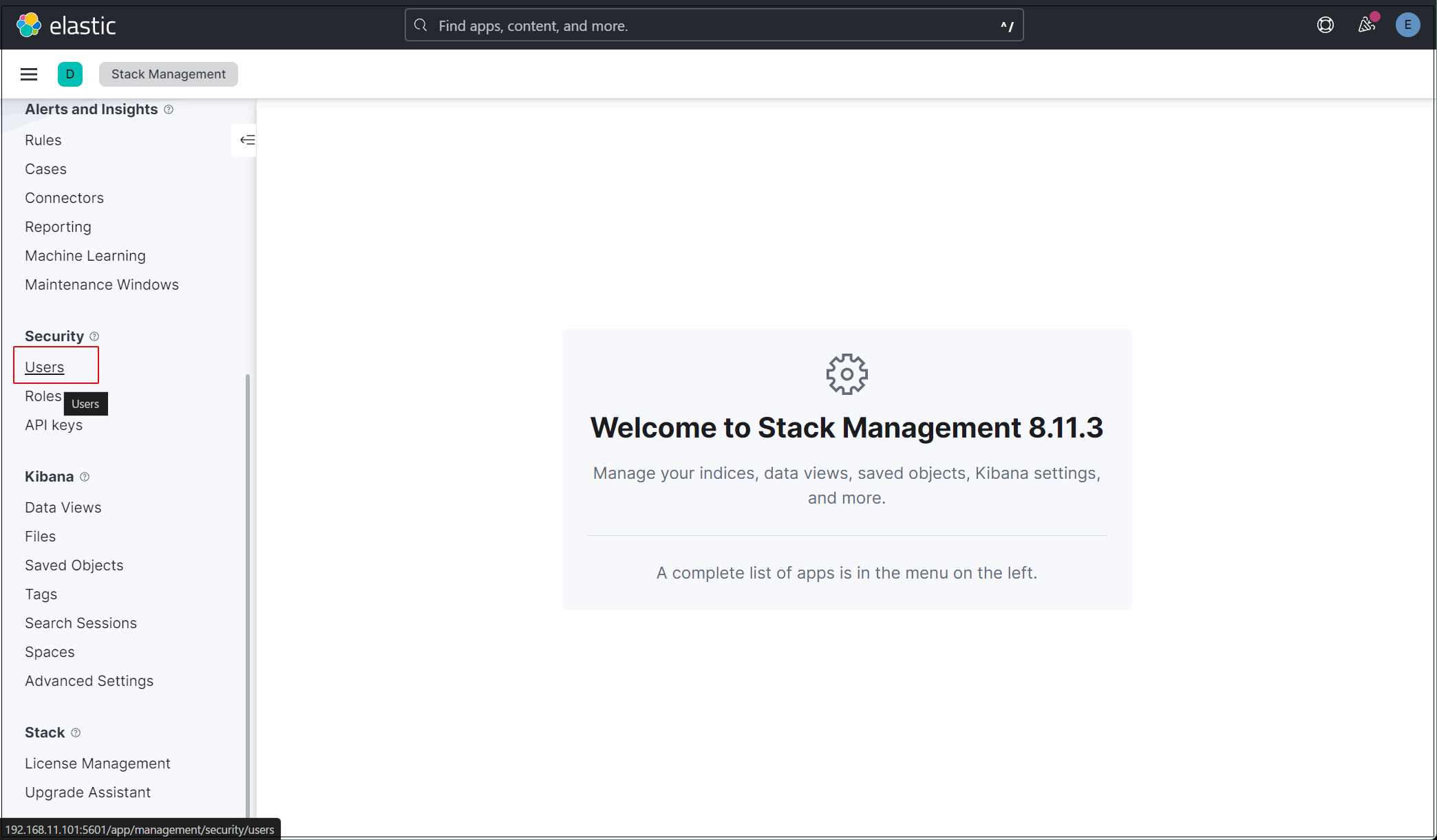
「security」「Users」選択
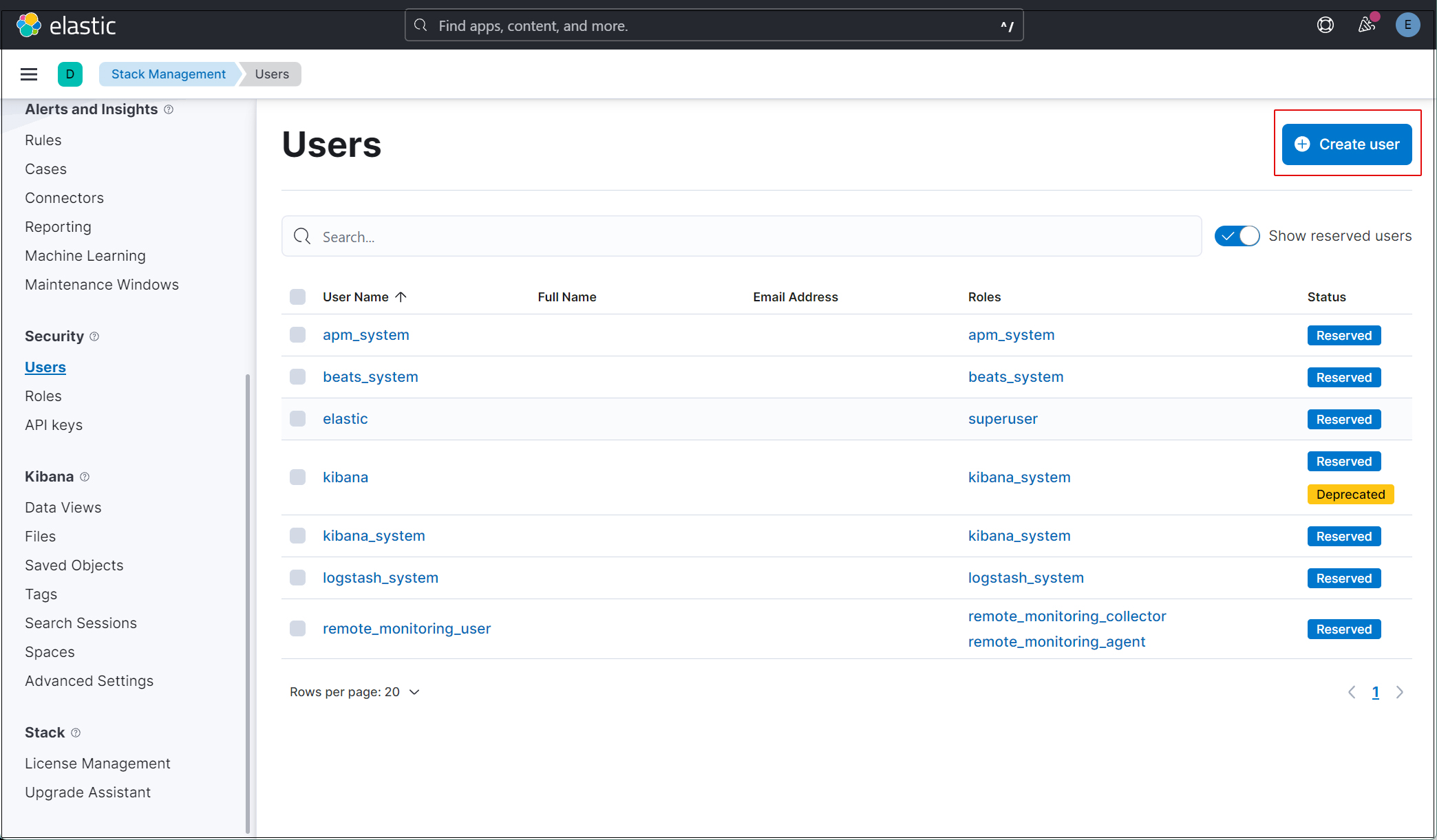
右上の"Create user"ボタンをクリック
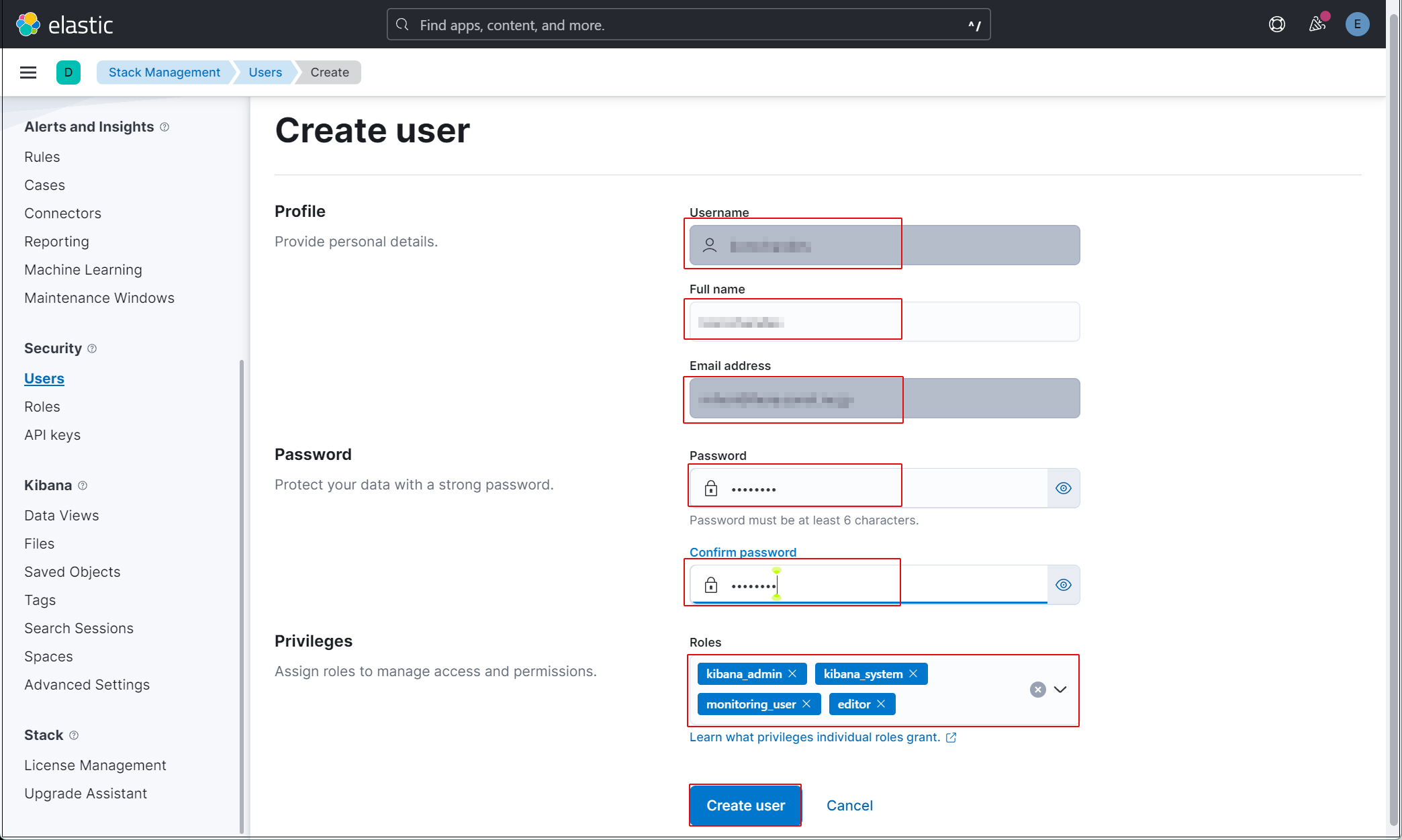
新規ユーザー情報を入力し、Privilegesでkibana_admin、kibana_system、monitoring_user、editorのロールを割り当てる
現在のプロファイルからログアウトし、新しく作成したユーザーアカウントでログインできることを確認する。現在、SURICATAのホストでFilebeatを設定していないため、Kibanaで表示できるデータがありません。
Filebeat インストールと設定
本作業はSuricataをインストールした1台目のDebian12.8サーバーで作業する
1. Filebeat インストール
1.1 パブリック署名キーをダウンロード
|
1 |
# wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | apt-key add - |
1.2 リポジトリ定義を/etc/apt/sources.list.d/elastic-8.x.listに保存
|
1 |
# echo "deb https://artifacts.elastic.co/packages/8.x/apt stable main" | tee -a /etc/apt/sources.list.d/elastic-8.x.list |
1.3 Filebeatをインストール
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
# apt update && apt install filebeat Get:1 http://security.debian.org/debian-security bookworm-security InRelease [48.0 kB] Get:2 http://deb.debian.org/debian bookworm-backports InRelease [59.0 kB] Hit:3 http://ftp.jp.debian.org/debian bookworm InRelease Get:4 http://ftp.jp.debian.org/debian bookworm-updates InRelease [55.4 kB] Get:5 http://security.debian.org/debian-security bookworm-security/main Sources [125 kB] Get:6 http://security.debian.org/debian-security bookworm-security/main amd64 Packages [204 kB] Get:7 https://artifacts.elastic.co/packages/8.x/apt stable InRelease [10.4 kB] Get:8 http://deb.debian.org/debian bookworm-backports/main amd64 Packages.diff/Index [63.3 kB] Get:9 http://deb.debian.org/debian bookworm-backports/main Translation-en.diff/Index [63.3 kB] Get:10 http://ftp.jp.debian.org/debian bookworm/main amd64 DEP-11 Metadata [4,492 kB] Get:11 http://deb.debian.org/debian bookworm-backports/main amd64 Packages T-2024-11-19-0205.28-F-2024-11-14-0805.11.pdiff [17.6 kB] Get:11 http://deb.debian.org/debian bookworm-backports/main amd64 Packages T-2024-11-19-0205.28-F-2024-11-14-0805.11.pdiff [17.6 kB] Get:12 https://artifacts.elastic.co/packages/8.x/apt stable/main amd64 Packages [120 kB] Get:13 http://deb.debian.org/debian bookworm-backports/main Translation-en T-2024-11-18-1408.37-F-2024-11-14-0805.11.pdiff [7,803 B] Get:13 http://deb.debian.org/debian bookworm-backports/main Translation-en T-2024-11-18-1408.37-F-2024-11-14-0805.11.pdiff [7,803 B] Get:14 http://ftp.jp.debian.org/debian bookworm/non-free-firmware amd64 DEP-11 Metadata [15.5 kB] Fetched 5,281 kB in 3s (2,032 kB/s) Reading package lists... Done Building dependency tree... Done Reading state information... Done 7 packages can be upgraded. Run 'apt list --upgradable' to see them. W: https://artifacts.elastic.co/packages/8.x/apt/dists/stable/InRelease: Key is stored in legacy trusted.gpg keyring (/etc/apt/trusted.gpg), see the DEPRECATION section in apt-key(8) for details. Reading package lists... Done Building dependency tree... Done Reading state information... Done The following NEW packages will be installed: filebeat 0 upgraded, 1 newly installed, 0 to remove and 7 not upgraded. Need to get 55.9 MB of archives. After this operation, 206 MB of additional disk space will be used. Get:1 https://artifacts.elastic.co/packages/8.x/apt stable/main amd64 filebeat amd64 8.16.0 [55.9 MB] Fetched 55.9 MB in 3s (21.4 MB/s) Selecting previously unselected package filebeat. (Reading database ... 53274 files and directories currently installed.) Preparing to unpack .../filebeat_8.16.0_amd64.deb ... Unpacking filebeat (8.16.0) ... Setting up filebeat (8.16.0) ... |
1.4 FilebeatをElasticsearchとKibanaに接続するように設定
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# vi /etc/filebeat/filebeat.yml 114行目あたりに追加、Elastic StackのIPアドレスとKibanaのポート番号(5601)を入力 host: "192.168.11.200:5601" 141行目あたりコメント解除し Elastic Stack のipアドレスとelasticsearchのポート番号を入力 hosts: ["https://192.168.11.200:9200"] 148行目あたりコメント解除 protocol: "https" 152,153行目あたりコメント解除し、[username]はデフォルトのままにし、[password]は[elastic]ユーザーのパスワードを入力する username: "elastic" password: “Ma6sJuSBGPnP+vav9K_P" 154行目あたりに追加 ssl.verification_mode: 'none' |
FilebeatのSuricataモジュールを有効にしますが、Elasticsearch 8.xでは、モジュールのインポートにバグがあるため、.ymlファイルからSuricataモジュールをインポートします
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# vi /etc/filebeat/filebeat.yml 57行目当たりのFilebeatモジュールのセクションをすべてコメントアウトし、reload.periodの下に以下の行を追加する: # ============================== Filebeat modules ============================== #filebeat.config.modules: # Glob pattern for configuration loading #path: ${path.config}/modules.d/*.yml # Set to true to enable config reloading #reload.enabled: false # Period on which files under path should be checked for changes #reload.period: 10s filebeat.modules: - module: suricata eve: enabled: true var.paths: ["/var/log/suricata/eve.json"] |
次に、SURICATAモジュールを強制的に実行
|
1 2 |
# filebeat setup --pipelines --modules suricata -M "suricata.eve.enabled=true" -c /etc/filebeat/filebeat.yml Loaded Ingest pipelines |
1.5 初期環境をセットアップ
SIEMダッシュボードとパイプラインをElasticsearchにロードします
filebeat setupコマンドを実行
suricata-eve-* が表示されていることを確認
|
1 2 3 4 5 6 7 8 |
# filebeat setup -e {"log.level":"info","@timestamp":"2024-11-21T17:29:07.984+0900","log.logger":"modules","log.origin":{"function":"github.com/elastic/beats/v7/filebeat/fileset.LoadPipeline","file.name":"fileset/pipelines.go","file.line":135},"message":"Elasticsearch pipeline loaded.","service.name":"filebeat","pipeline":"filebeat-8.16.0-suricata-eve-dns","ecs.version":"1.6.0"} {"log.level":"info","@timestamp":"2024-11-21T17:29:07.986+0900","log.logger":"modules","log.origin":{"function":"github.com/elastic/beats/v7/filebeat/fileset.LoadPipeline","file.name":"fileset/pipelines.go","file.line":135},"message":"Elasticsearch pipeline loaded.","service.name":"filebeat","pipeline":"filebeat-8.16.0-suricata-eve-dns-answer-v1","ecs.version":"1.6.0"} {"log.level":"info","@timestamp":"2024-11-21T17:29:07.988+0900","log.logger":"modules","log.origin":{"function":"github.com/elastic/beats/v7/filebeat/fileset.LoadPipeline","file.name":"fileset/pipelines.go","file.line":135},"message":"Elasticsearch pipeline loaded.","service.name":"filebeat","pipeline":"filebeat-8.16.0-suricata-eve-dns-answer-v2","ecs.version":"1.6.0"} {"log.level":"info","@timestamp":"2024-11-21T17:29:07.990+0900","log.logger":"modules","log.origin":{"function":"github.com/elastic/beats/v7/filebeat/fileset.LoadPipeline","file.name":"fileset/pipelines.go","file.line":135},"message":"Elasticsearch pipeline loaded.","service.name":"filebeat","pipeline":"filebeat-8.16.0-suricata-eve-tls","ecs.version":"1.6.0"} {"log.level":"info","@timestamp":"2024-11-21T17:29:07.992+0900","log.logger":"modules","log.origin":{"function":"github.com/elastic/beats/v7/filebeat/fileset.LoadPipeline","file.name":"fileset/pipelines.go","file.line":135},"message":"Elasticsearch pipeline loaded.","service.name":"filebeat","pipeline":"filebeat-8.16.0-suricata-eve-http","ecs.version":"1.6.0"} Loaded Ingest pipelines |
1.6 Filebeatサービスを開始
|
1 |
# systemctl start filebeat.service |
Kibanaで確認
作成したユーザーでKibanaにログインし直します。http://192.168.11.200:5601にアクセスします。
一番上の検索フィールドに「Suricata Events Overview」と入力し、Events Overviewをクリック
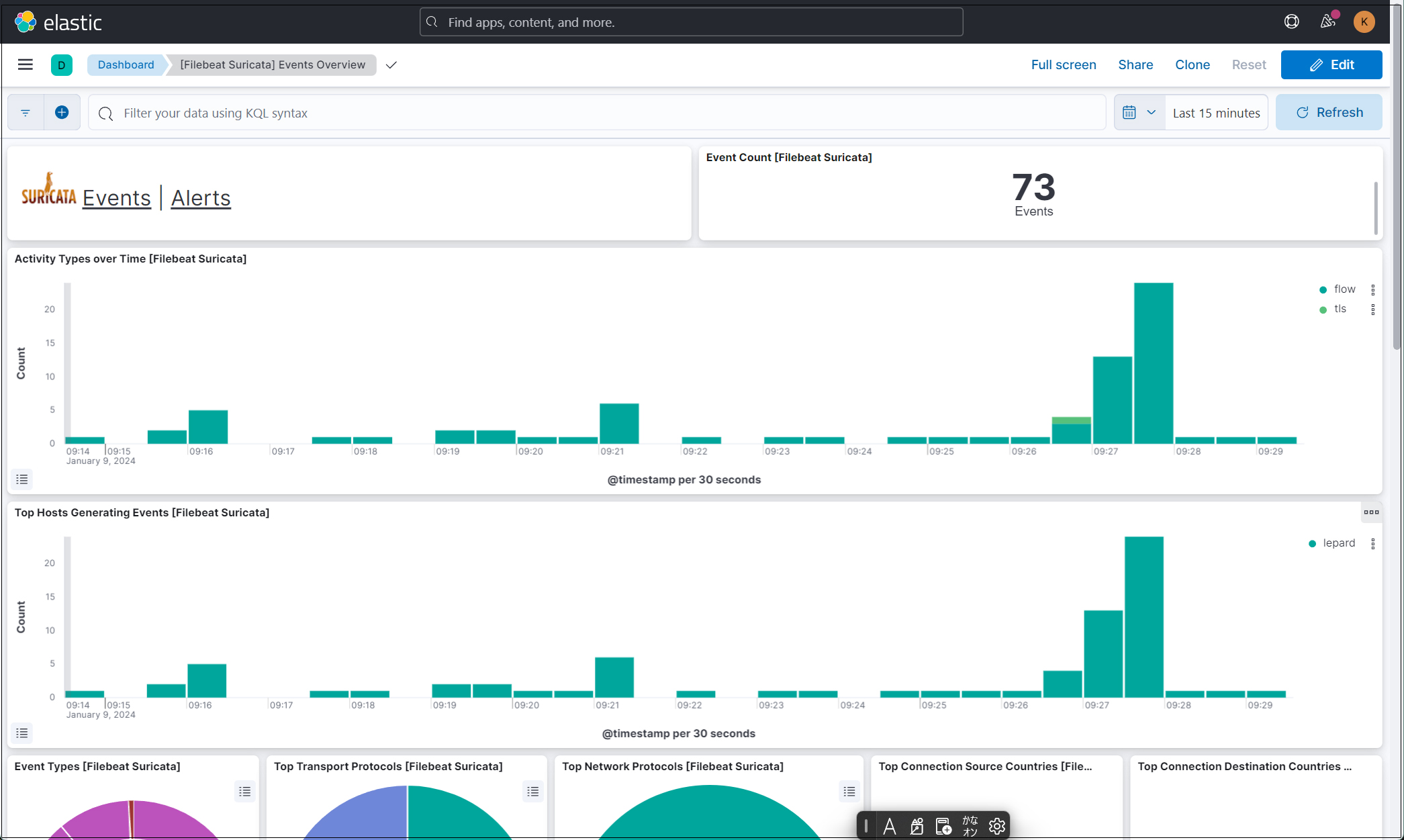
過去 15 分間のすべての Suricata イベントが表示されます
悪質なトラフィックのアラートを表示するにはSuricataロゴの横にあるAlertsテキストをクリック

