Contents
1.SSL証明書を取得する ( Let's Encrypt )
最新のopen sslをインストールしておく
# yum install openssl-devel
1.1 証明書のインストール
# yum -y install certbot # certbot certonly --webroot -w /var/www/html/[FQDN] -d [FQDN]
# 受信可能なメールアドレスを指定
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator webroot, Installer None
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel):[E-mail address]
Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf. You must
agree in order to register with the ACME server. Do you agree?
(Y)es/(N)o: y
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
(Y)es/(N)o: y
Account registered.
Requesting a certificate for cent.korodes.com
Performing the following challenges:
http-01 challenge for cent.korodes.com
Using the webroot path /var/www/html/cent.korodes.com for all unmatched domains.
Waiting for verification…
Cleaning up challenges
Subscribe to the EFF mailing list (email: mhori@hera.eonet.ne.jp).
Starting new HTTPS connection (1): supporters.eff.org
We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can try again later by visiting https://act.eff.org.
IMPORTANT NOTES:
-Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/cent.korodes.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/cent.korodes.com/privkey.pem
Your certificate will expire on 2023-05-18. To obtain a new or
tweaked version of this certificate in the future, simply run
certbot again. To non-interactively renew all of your
certificates, run "certbot renew"
-If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
1.2 証明書を自動更新 (Let's Encrypt)
①登録前のテスト
まず以下の--dry-runオプションを使って自動更新をテストしてみる。このオプションでは、証明書は更新されずに動作確認のみ実施されるため、証明書の取得回数制限に引っかかる心配もない
# certbot renew --dry-run
②Systemd Timerを利用する
# systemctl cat certbot-renew.timer # /usr/lib/systemd/system/certbot-renew.timer [Unit] Description=This is the timer to set the schedule for automated renewals [Timer] OnCalendar=*-*-* 00/12:00:00 RandomizedDelaySec=12hours Persistent=true [Install] WantedBy=timers.target
# systemctl enable --now certbot-renew.timer Created symlink from /etc/systemd/system/timers.target.wants/certbot-renew.timer to /usr/lib/systemd/system/certbot-renew.timer.
# systemctl list-timers certbot-renew.timer NEXT LEFT LAST PASSED UNIT ACTIVATES Sat 2023-02-18 11:01:38 JST 13h left n/a n/a certbot-renew.timer certbot-re 1 timers listed. Pass --all to see loaded but inactive timers, too.
2. Apache のhttps 化
念のため、下記をインストールしておく
# yum -y install mod_ssl
2.1 ssl.conf ファイルの編集
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# vi /etc/httpd/conf.d/ssl.conf ●59 行目 コメント解除して変更 DocumentRoot "/var/www/html/<FQDN>" ●60 行目 コメント解除して変更 ServerName <ドメイン名>:443 ●100行目 コメントにしてその下に追加 # SSLCertificateFile /etc/pki/tls/certs/localhost.crt SSLCertificateFile /etc/letsencrypt/live/<FQDN>/cert.pem ●107行目 コメントにしてその下に追加 # SSLCertificateKeyFile /etc/pki/tls/private/localhost.key SSLCertificateKeyFile /etc/letsencrypt/live/<FQDN>/privkey.pem ●117行目 追加 SSLCertificateChainFile /etc/letsencrypt/live/<FQDN>/chain.pem |
# systemctl restart httpd
# firewall-cmd --add-service=https --permanent success # firewall-cmd --reload success
2.2 HTTP 通信を HTTPS へリダイレクト
.htaccessを/var/www/html/[FQDN]/ 配下に作成
.htaccessの内容
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
3. Mail サーバーにSSL/TLS(Let's Encrypt) の設定
3.1 メールサーバー用証明書の取得
メールサーバー用の証明書を取得するが上記と同様の方法では取得できないので「--standalone」オプションをつけて下記のようにしても失敗する。
|
1 |
# certbot certonly --standalone -d mail.<domain name> |
一度web サーバーを止めてから行うと下記のとおり成功する
|
1 2 |
# systemctl stop httpd.service # certbot certonly --standalone -d mail.<domain name> |
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator standalone, Installer None
Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
Requesting a certificate for mail.korodes.com
Performing the following challenges:
http-01 challenge for mail.korodes.com
Waiting for verification…
Cleaning up challenges
IMPORTANT NOTES:
-Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/mail.korodes.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/mail.korodes.com/privkey.pem
Your certificate will expire on 2023-05-18. To obtain a new or
tweaked version of this certificate in the future, simply run
certbot again. To non-interactively renew all of your
certificates, run "certbot renew"
-If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
3.2 Postfixの設定
# vi /etc/postfix/main.cf
● 最終行に追記
smtpd_use_tls = yes
smtp_tls_mandatory_protocols = !SSLv2, !SSLv3
smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3
smtpd_tls_cert_file = /etc/letsencrypt/live/mail.<domain name>/fullchain.pem
smtpd_tls_key_file = /etc/letsencrypt/live/mail.<domain name>/privkey.pem
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
# vi /etc/postfix/master.cf
● 16-19行目 : コメント解除
submission inet n - n - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
● 26-29行目 : コメント解除
smtps inet n - n - - smtpd
-o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
postfix 再起動
# systemctl restart postfix
3.3 Dovecotの設定
# vi /etc/dovecot/conf.d/10-ssl.conf 9行目 : 変更 ssl = yes
dovecot再起動
# systemctl restart dovecot
3.4 Firewalldの設定
サブミッションポート(587番ポート)を許可する
# firewall-cmd --add-port=587/tcp --permanent # firewall-cmd --reload
3.5 Thunderbirdの設定
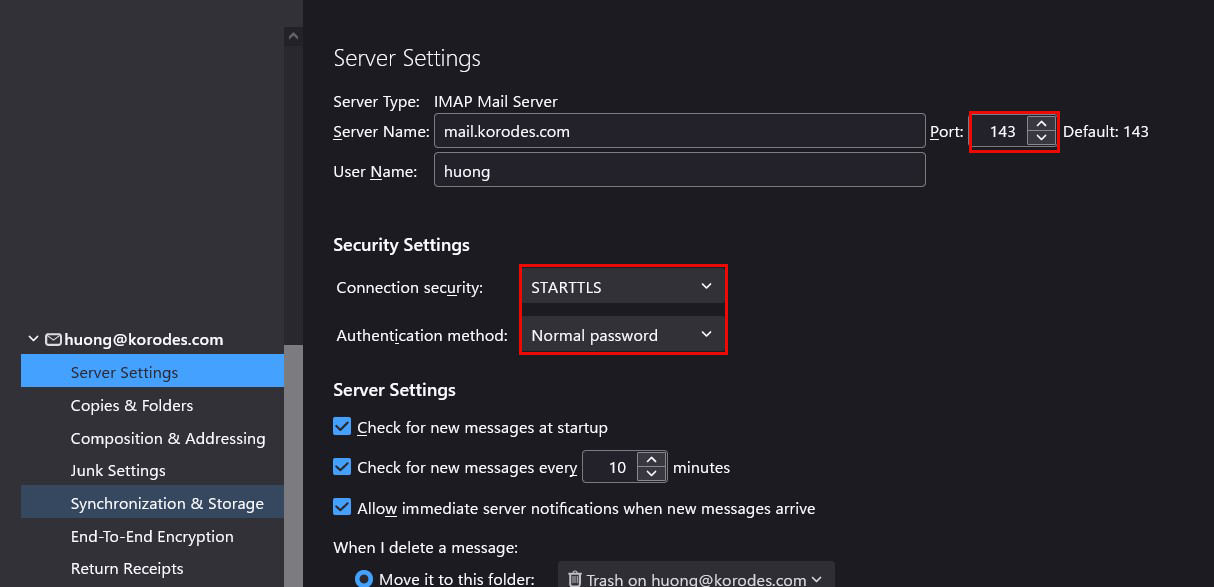
受信サーバー
Port : 143
Connection security : STARTTLS
Authentication method : Normal password
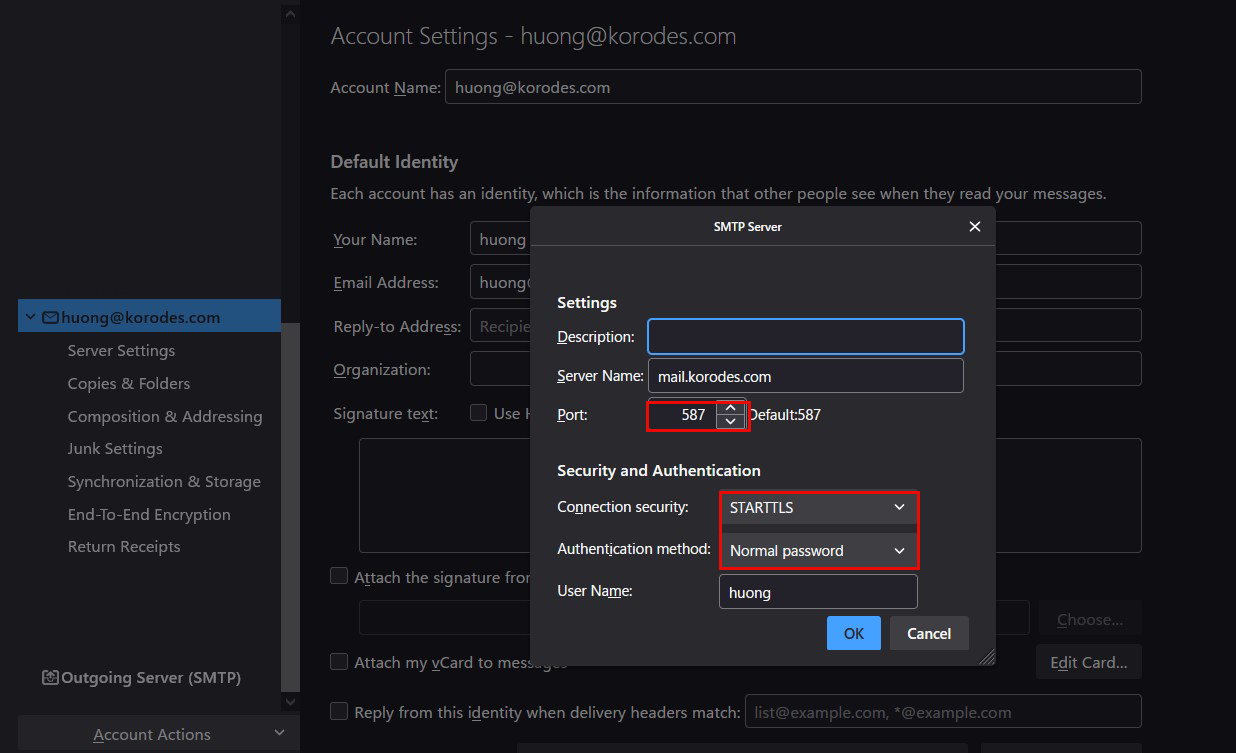
送信サーバー
Port : 587
Connection security : STARTTLS
Authentication method : Normal password